During the first half of 2011 we have witnessed a significant growth in malware targeting 64-bit platforms, the most interesting examples of which are bootkits. There are now several malware families in the wild: Win64/Olmarik, an MBR (Master Boot Record) bootkit
Win64/Rovnix, a VBR (Volume Boot Record) bootkit
Win64/TrojanDownloader.Necurs
Win64/Spy.BankerOf course, compared to the volume of families that target x86 platforms, those numbers don’t look much. But the percentage of new x64 families emerging in this year shows a significant increase. Looking at relative detection ratios for x64 platform families, there is an upward trend with a significant spike in the summer of 2010. This is connected with the emergence of a new version of Win64/Olmarik (TDL4) and its active distribution at that time. They all use tricks to bypass the digital signature checks that can be divided into two groups. The first works entirely within user mode, and the second group targets the process of booting the operating system in order to manipulate kernel-mode memory: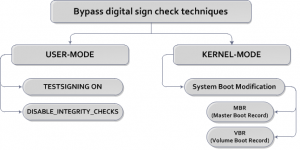
Read more: ESET Threat Blog
QR:
Win64/Rovnix, a VBR (Volume Boot Record) bootkit
Win64/TrojanDownloader.Necurs
Win64/Spy.BankerOf course, compared to the volume of families that target x86 platforms, those numbers don’t look much. But the percentage of new x64 families emerging in this year shows a significant increase. Looking at relative detection ratios for x64 platform families, there is an upward trend with a significant spike in the summer of 2010. This is connected with the emergence of a new version of Win64/Olmarik (TDL4) and its active distribution at that time. They all use tricks to bypass the digital signature checks that can be divided into two groups. The first works entirely within user mode, and the second group targets the process of booting the operating system in order to manipulate kernel-mode memory:

Read more: ESET Threat Blog
QR:



0 comments:
Post a Comment