Top 10 specialty Web browsers you may have missed
These oddly useful alternative browsers offer such advantages as 3-D searching, social networking, easy scriptability, and powerful page manipulationIn the game of technological one-upmanship, the browser used to be an easy place to win. Most people used Internet Explorer, so it was simple to gain the edge by using Firefox. But now Firefox is common, and even Opera and Google Chrome are losing their cachet. Safari ships standard with every Mac, so everyone, the cool and the uncool, have it by default. They're all excellent browsers, but they're still the status quo. Is there anywhere else to turn for a bit of distinction? Finding an even more obscure browser is surprisingly straightforward, and it may offer more than just the feeling of superiority that comes from beating the crowds. Many of the alternative browsers exist to solve particular problems, and the new and better features are useful to us. Sometimes it's because we're part of some niche like Facebook, but often it's because our boss wants us to do something with information on the Web and the specialized browser makes it simpler. [ Learn how to keep your Web surfing secure. Read "The InfoWorld expert guide to Web browser security" and download InfoWorld's Web Browser Security Deep Dive PDF special report. ] Some alternative browsers are just specialized versions of the common open source implementations. The rebels who feel that the world really needs another Web browser are also smart enough to know it doesn't make sense to reinvent the core technology. They just wrap their own features around Chrome or Firefox, Gecko or WebKit. This point is illustrated nicely in this family tree of Web browsers. A purist might object that these hybrids are not much different from a standard browser with extra plug-ins. There's some truth to this, but not always -- some of the unique capabilities can only be done deep inside the software. In any case, the job of parsing the terms and creating an exact definition of the Web browser isn't as much fun as embracing the idea that there are dozens of alternatives. So here's a list of 10 browsers that are not Firefox, Chrome, Opera, Safari, or IE, but that are all the more useful because they're not. They aren't different because they have a different name and some buttons in other spots, but because they offer something that can't be found in the traditional browsers: a more useful representation of Web pages or search results, integration with social networking sites or other services, a lower resource footprint, faster page rendering, or even easy scriptability. Read more: InfoWorld
Asterisk 1.8 Released With Support For Google Voice
Posted by
jasper22
at
16:50
|
Long-standing open-source VoiP software Asterisk has just been updated, and it's packed with more than 200 enhancements, security updates, and new features — including calendar integration and support for Google Voice and Google Talk. Asterisk's fully-featured PBX includes call waiting, hold and transfer, caller ID, and other useful tools so it's a great option for small businesses that need to watch costs. Read more: Slashdot
RDS Protocol Bug Creates a Linux Kernel Hole, Now Fixed
Posted by
jasper22
at
16:49
|
The open-source Linux operating system contains a serious security flaw that can be exploited to gain superuser rights on a target system.The vulnerability, in the Linux implementation of the Reliable Datagram Sockets (RDS) protocol, affects unpatched versions of the Linux kernel, starting from 2.6.30, where the RDS protocol was first included. According to VSR Security, the research outfit that discovered the security hole, Linux installations are only vulnerable if the CONFIG_RDS kernel configuration option is set, and if there are no restrictions on unprivileged users loading packet family modules, as is the case on most stock distributions. Because kernel functions responsible for copying data between kernel and user space failed to verify that a user-provided address actually resided in the user segment, a local attacker could issue specially crafted socket function calls to write arbritrary values into kernel memory. By leveraging this capability, it is possible for unprivileged users to escalate privileges to root. Read more: threat post
Bible.com Investor Sues Company For Lack Of Profit
Posted by
jasper22
at
16:46
|
The board of Bible.com claims that it is easier for a camel to pass through the eye of a needle, than to make money on the domain name, but an angry shareholder disagrees. From the article: "James Solakian filed the lawsuit in Delaware's Chancery Court against the board of Bible.com for breaching their duty by refusing to sell the site or run the company in a profitable way. The lawsuit cites a valuation done by a potential purchaser that estimated bible.com could be worth more than dictionary.com, which recently sold for more than $100 million. Read more: Slashdot
Iranian Cyber Army Moves Into Botnet Renting
Posted by
jasper22
at
14:28
|
A group of malicious hackers who attacked Twitter and the Chinese search engine Baidu are also apparently running a for-rent botnet, according to new research from Seculert. The so-called Iranian Cyber Army also took credit last month for an attack on TechCrunch's European website. In that incident, the group installed a page on TechCrunch's site that redirected visitors to a server that bombarded their PCs with exploits in an attempt to install malicious software Read more: Slashdot
Quantum computing: Cheat Sheet
Posted by
jasper22
at
14:26
|
FEATURE
Time machines - oh, boy!
Steady on Sam, I love science fiction as much as the next geek but I'm not talking about Quantum Leap here. This is even more exciting than time travel.OK, so what is this quantum computing lark then?
Quantum computing and quantum information processing are research efforts that seek to exploit quantum mechanical phenomena to perform tasks such as massively parallel computing. The quantum research field also encompasses quantum cryptography, which utilises quantum phenomena to guarantee secure communications. What are these quantum phenomena you talk of?
Tsk! Clearly weren't paying attention in physics class were you?Quantum mechanics is a branch of physics that describes all manner of weirdness and 'spooky behaviour' - that is, quantum phenomena - taking place at the atomic and sub-atomic levels where electrons, protons and other particles exist. The quantum world's spooky behaviour, for example, sees matter and energy able to behave both like particles and waves simultaneously, and apparently exist in two places at once.My head hurts.
That's to be expected. All of this quantum weirdness is deeply counter-intuitive - if not downright bizarre - to our human brains because it stands in stark contrast to the classical physics we experience in our everyday lives. Thanks for the physics refresher - but what does all this spooky behaviour have to do with computers?
Good question. Instead of having bits, as a classical computer does, which represent either a one or a zero, a quantum computer has quantum bits - qubits - which can represent zero, one, or a superposition of both - that is, any amount of either zero and one simultaneously. As a result, unlike a traditional computer which can only store one number in a single register at any one time, a quantum computer can store more than one. Adding more qubits exponentially increases the size of the number that can be stored - a computer with a 100 qubits would be able to store a massive number in its register, for instance.As well as qubits, another key element of quantum computing is a phenomena known as entanglement. Read more: silicon.com
Time machines - oh, boy!
Steady on Sam, I love science fiction as much as the next geek but I'm not talking about Quantum Leap here. This is even more exciting than time travel.OK, so what is this quantum computing lark then?
Quantum computing and quantum information processing are research efforts that seek to exploit quantum mechanical phenomena to perform tasks such as massively parallel computing. The quantum research field also encompasses quantum cryptography, which utilises quantum phenomena to guarantee secure communications. What are these quantum phenomena you talk of?
Tsk! Clearly weren't paying attention in physics class were you?Quantum mechanics is a branch of physics that describes all manner of weirdness and 'spooky behaviour' - that is, quantum phenomena - taking place at the atomic and sub-atomic levels where electrons, protons and other particles exist. The quantum world's spooky behaviour, for example, sees matter and energy able to behave both like particles and waves simultaneously, and apparently exist in two places at once.My head hurts.
That's to be expected. All of this quantum weirdness is deeply counter-intuitive - if not downright bizarre - to our human brains because it stands in stark contrast to the classical physics we experience in our everyday lives. Thanks for the physics refresher - but what does all this spooky behaviour have to do with computers?
Good question. Instead of having bits, as a classical computer does, which represent either a one or a zero, a quantum computer has quantum bits - qubits - which can represent zero, one, or a superposition of both - that is, any amount of either zero and one simultaneously. As a result, unlike a traditional computer which can only store one number in a single register at any one time, a quantum computer can store more than one. Adding more qubits exponentially increases the size of the number that can be stored - a computer with a 100 qubits would be able to store a massive number in its register, for instance.As well as qubits, another key element of quantum computing is a phenomena known as entanglement. Read more: silicon.com
How Allies Used Math Against German Tanks
Posted by
jasper22
at
14:24
|
This an article about how the allies where able to estimate the number of German tanks produced based on the serial numbers of the tanks. Neat! Godwin does not apply.Read more: Slashdot
Blend Bits 15: The Data Store
Posted by
jasper22
at
12:28
|
There’s lots of data features in Blend to provide food for future posts but this post is about the data store that showed up in Blend 4.This is a fairly simple idea and I suspect that I’d use it more in the realm of a SketchFlow application than I would in a real application as I tend to see it as a way for a designer to store something outside of the underlying object model that they’re data-bound to and I’m not sure I’d want that to happen in a real application. Say I’m sketching a simple login screen and I’ve sketched out this UI;
Read more: Mike Taulty's Blog

Read more: Mike Taulty's Blog
ATTACHED PROPERTY
Posted by
jasper22
at
12:26
|
בפוסט הקודם דיברנו על Dependency property. כעת נדבר על Attached. קודם כל נראה דוגמא קטנה :
<Canvas><Button Canvas.Top="20"
Width="150"
Height="50"
Content="Button in canvas"
Canvas.Left="36"></Button>
</Canvas>
הקוד הבא ימקם Button בתוך הCanvas על בסיס של Top ו Left. אנחנו רואים שהמאפיינים Top ו Left יושבים בתוך ה Canvas ולא בתוך ה Button, למה ? למה אין ל Button מאפיינים של Top ושל Left?! אם נחשוב לרגע נזכור שCanvas הוא רק סוג אחד של Container. Container נוסף שנפוץ בצורה משמעותית יותר מה Canvas הוא ה Grid. ל Grid עצמו אין Top ו Height אלא Column ו Row. אז מה יקרה אם נעבוד בצורה המוצעת כאן ? ל Button יהיה גם top וגםleft ו Column וגם Row. מה יקרה כאשר ירצו להוסיף Container נוסף? האם הגיוני שעל כל Container שנוסיף נצטרך לעבור על כל הControls שרלוונטים ולבצע שינוי גם אצלם ? איך נזכור בכלל איזה Controls רלוונטים. כך שבאמת צריך למצוא פיתרון טוב יותר. ב WPF המציאו את ה Attached Property שמאפשר לנו לשמור נתונים נוספים על פקד בלי שיהיה לא את המאפיין הזה מראש. בואו נראה איך נראה הקוד ב #C ביחס ל XAML למעלה :
Button b = new Button();
b.Content = "Button in canvas";Canvas.SetLeft(b, 36);
Canvas.SetTop(b, 20);
c1.Children.Add(b);
מה הולך פה ? c1 מתייחס כאן ל Canvas עצמו. תיזכרו שוב במילון של ה Dependency Properties מה Post הקודם. באמצעות פונקציה סטטית שיושבת ב Canvas אני שומר על ה Button שה Canvas.Left שלו הוא 36. את מי הערך הזה מעניין ? בטח שלא את ה Button עצמו. כאשר ה Canvas בא לצייר את עצמו הוא עובר על כל ה Childerns שלו ושואל אותם האם יש להם ערכים בשבילו. הערכים הרלוונטים ל Canvas הם left, top, bottom, right, zIndex. הקריאה של הProperty מתבצעת בצורה הבאה :
Canvas.GetTop(b);
ה Canvas מקבל את הערך ולפי זה יודע איך לצייר אותו. שימו לב שהButton לא שומר canvas.Left על אובייקט ספציפי של Canvas אלא ברמה הסטטית.
Read more: SHIMON DAHANUseful, free resources for SQL Server
Posted by
jasper22
at
12:06
|
Recently Dave Ballantyne posted a list of free resources for SQL Server, entitled "The best things in life are free." Now, I'm not trying to upstage Dave, but I know of several resources that aren't on his list. It would be good to have a true community page for this kind of thing, but for now a blog post will have to do. [I also just re-noticed Mladen Prajdic's post on free SQL Server tools, and his list is quite exhaustive.] Please leave a comment if you spot any errors, omissions, broken links, etc. Free Upgrade Advisors / Best Practices AnalyzersThese tools from Microsoft can be instrumental in cleaning up your systems and finding issues *before* the day of the upgrade. I'm including the SQL Server 2005 versions, but if you're just planning your upgrade to 2005 now, I'd suggest re-thinking toward 2008 or 2008 R2. The last service pack for 2005 is due out later this year, and the next major version of SQL Server is probably about a year after that. Note that there is no SQL Server 2008 Best Practices Analyzer, at least that I could find. SQL Server 2005 Upgrade Advisor
SQL Server 2005 Best Practices Analyzer
SQL Server 2008 Upgrade Advisor - download x64 - download x86
SQL Server 2008 R2 Upgrade Advisor - download x64 - download x86
SQL Server 2008 R2 Best Practices Analyzer - download x64 - download x86 (For some advice about the R2 BPA install, see this post from August)
Free DocumentationBooks Online is the official go-to documentation for SQL Server, but you don't have to have a SQL Server license to use it. You can choose to download the application (or install it as part of setup) and keep it up to date, or use the web-based version. SQL Server 2005 Books Online - or download
SQL Server 2008 Books Online - or download
SQL Server 2008 R2 Books Online - or download Free Feature PacksRead more: Aaron Bertrand
SQL Server 2005 Best Practices Analyzer
SQL Server 2008 Upgrade Advisor - download x64 - download x86
SQL Server 2008 R2 Upgrade Advisor - download x64 - download x86
SQL Server 2008 R2 Best Practices Analyzer - download x64 - download x86 (For some advice about the R2 BPA install, see this post from August)
Free DocumentationBooks Online is the official go-to documentation for SQL Server, but you don't have to have a SQL Server license to use it. You can choose to download the application (or install it as part of setup) and keep it up to date, or use the web-based version. SQL Server 2005 Books Online - or download
SQL Server 2008 Books Online - or download
SQL Server 2008 R2 Books Online - or download Free Feature PacksRead more: Aaron Bertrand
Debug Executable Without Using Attach to Process
Posted by
jasper22
at
12:02
|
Okay, so the full title here is "Debug Your Executable Without Using the Traditional 'Attach to Process' Menu Items" but that was way too long for me so I just shortened it up a bit. You probably already know about the Attach to Process menu items on the Debug and Tools menus, but what if, for example, the process fails before you can attach to it? Maybe it fails on startup or it runs too fast for you to catch it. Well we have a solution for you--literally! Did you know you can create a Solution for executables? It's easy to do, just find the executable you want to create a solution for by going to File -> Open Project/Solution:
Or, if you have a Solution open already, File -> Add -> Existing Project:
Now you can run the executable just like any other project by pressing F5. If you have multiple projects make sure to set it as the startup: Read more: Visual Studio Tips and Tricks

Or, if you have a Solution open already, File -> Add -> Existing Project:
Now you can run the executable just like any other project by pressing F5. If you have multiple projects make sure to set it as the startup: Read more: Visual Studio Tips and Tricks
Getting rid of the magic strings in a WCF Data Service Client
Posted by
jasper22
at
11:52
|
One of the common problems that you might find when using the generated DataServiceContext for consuming an existing WCF data service is that you have magic strings everywhere for handling links (expanding, adding, deleting, etc). The problem with all those magic strings is that they make your code to compile correctly, but you might run into some error at runtime because you used a link that does not exist or it was just renamed. To give an example, this is how you expand the items associated to an order using the traditional way with magic strings.context.Orders.Expand(“Items”)If that property is later renamed to “OrderItems” on the service side, and the proxy is updated, that code will still compile but you will receive an error at runtime. Fortunately, you can get rid of those “magic” strings and making the compiler your friend by leveraging Expression trees. The expression trees will make your code easier to maintain, and what’s more important, the compiler will verify the expressions correctness at compilation time. Continuing what Stuart Leeks did for link expansions with expressions, I added a few more methods for managing links. namespace System.Data.Services.Client
{
public static class DataServiceExtensions
{
public static void SetLink<TSource, TPropType>(this DataServiceContext context, TSource source,
Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.SetLink(source, expandString, target);
} public static void AddLink<TSource, TPropType>(this DataServiceContext context,
TSource source, Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.AddLink(source, expandString, target);
} public static void DeleteLink<TSource, TPropType>(this DataServiceContext context,
TSource source, Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.DeleteLink(source, expandString, target);
}Read more: Pablo M. Cibraro (aka Cibrax)
{
public static class DataServiceExtensions
{
public static void SetLink<TSource, TPropType>(this DataServiceContext context, TSource source,
Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.SetLink(source, expandString, target);
} public static void AddLink<TSource, TPropType>(this DataServiceContext context,
TSource source, Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.AddLink(source, expandString, target);
} public static void DeleteLink<TSource, TPropType>(this DataServiceContext context,
TSource source, Expression<Func<TSource, TPropType>> propertySelector, object target)
{
string expandString = BuildString(propertySelector);
context.DeleteLink(source, expandString, target);
}Read more: Pablo M. Cibraro (aka Cibrax)
Mount zip file in application process
Posted by
jasper22
at
11:51
|
Opening a zip package in a program without extracting
IntroductionApplications usually generate some combination of files as output such as xml, pictures, sound and put them in a folder. Packing all of that files and folders into single file and set custom extension for that file is common idea. The new file that includes other files called container. Because of the zip file format is a portable and standard format, many applications use zip file format for containers (usually with a custom extension). This article focus to zip archive as container of files not other containers. For example java programmers use zip file format for create java archive files with jar extension or Microsoft corporative use it for Microsoft Office Word 2007 (with DOCX extension), Microsoft Excel (with XLSX extension) and Microsoft PowerPoint 2007 (with PPTX extension). You can change file’s extension to zip and open those with zip tools applications. This article wants to introduce how to use zip archives in our application? How many solutions exist? And what is the best solution?Why you need to mount the zip file instead using simple zip tools?Packaging data to container as zip archive has some advantage that programmer use it. In this section we want to discuss about opening zip archive and use its files in our application process. Some of the advantages of using containers are hide file structure complexity from the user view and give a single compressed file. After some files put in a zip archive you have an important problem: How can applications work with files in the container? Packaging the output file of an application in zip file or any other format is not complex task, but the application have some problems when it need to open package and access the files inside the package, it may need to extract all of them in temp folder. Even if your zip tools support opening files as “stream” directly from zip archive some component may not support streaming such as “Flash”. Some component like web browser support streaming but what happen to the included file in html such as CSS and pictures? You may find how to give web browser the opened stream but you will need to recalculate all references to files and create other stream for them, all of this make it awesome and you need to extract them to temp folder, it require time, loosing performance and so on. By mounting zip file in your application process this entire problem solved. Your package makes the generated document file as standard zip archive and just mounts them when needed. There are three solutions exist for using zip archive:1. Extracting zip archives in a temporary folder.2. Opening each file or stream in zip archive with API of zip libraries.3. Mounting zip archive in the application process. Now let us see the advantage and disadvantage of each approach.1. Extract all of them into temporary folder and open each required file.First approach for using the application from files inside of zip archive is extract it in a temporary folder and act with files in a standard way. after terminating application this temporary folder can be deleted Read more: Codeproject
IntroductionApplications usually generate some combination of files as output such as xml, pictures, sound and put them in a folder. Packing all of that files and folders into single file and set custom extension for that file is common idea. The new file that includes other files called container. Because of the zip file format is a portable and standard format, many applications use zip file format for containers (usually with a custom extension). This article focus to zip archive as container of files not other containers. For example java programmers use zip file format for create java archive files with jar extension or Microsoft corporative use it for Microsoft Office Word 2007 (with DOCX extension), Microsoft Excel (with XLSX extension) and Microsoft PowerPoint 2007 (with PPTX extension). You can change file’s extension to zip and open those with zip tools applications. This article wants to introduce how to use zip archives in our application? How many solutions exist? And what is the best solution?Why you need to mount the zip file instead using simple zip tools?Packaging data to container as zip archive has some advantage that programmer use it. In this section we want to discuss about opening zip archive and use its files in our application process. Some of the advantages of using containers are hide file structure complexity from the user view and give a single compressed file. After some files put in a zip archive you have an important problem: How can applications work with files in the container? Packaging the output file of an application in zip file or any other format is not complex task, but the application have some problems when it need to open package and access the files inside the package, it may need to extract all of them in temp folder. Even if your zip tools support opening files as “stream” directly from zip archive some component may not support streaming such as “Flash”. Some component like web browser support streaming but what happen to the included file in html such as CSS and pictures? You may find how to give web browser the opened stream but you will need to recalculate all references to files and create other stream for them, all of this make it awesome and you need to extract them to temp folder, it require time, loosing performance and so on. By mounting zip file in your application process this entire problem solved. Your package makes the generated document file as standard zip archive and just mounts them when needed. There are three solutions exist for using zip archive:1. Extracting zip archives in a temporary folder.2. Opening each file or stream in zip archive with API of zip libraries.3. Mounting zip archive in the application process. Now let us see the advantage and disadvantage of each approach.1. Extract all of them into temporary folder and open each required file.First approach for using the application from files inside of zip archive is extract it in a temporary folder and act with files in a standard way. after terminating application this temporary folder can be deleted Read more: Codeproject
Configuring USB Redirection with Microsoft RemoteFX Step-by-Step Guide
Posted by
jasper22
at
11:46
|
Overview
This step-by-step guide walks you through the process of setting up USB redirection with RemoteFX in a test environment.Upon completion of this step-by-step guide, you will have a personal virtual desktop with RemoteFX assigned to a user account that can connect by using RD Web Access. Read more: MS Download
This step-by-step guide walks you through the process of setting up USB redirection with RemoteFX in a test environment.Upon completion of this step-by-step guide, you will have a personal virtual desktop with RemoteFX assigned to a user account that can connect by using RD Web Access. Read more: MS Download
Enterprise JavaScript : Google Launches JavaScript Cloud Scripting Language
Posted by
jasper22
at
11:45
|

Google Apps Script is a new JavaScript enterprise technology to automate tasks across Google products. The new JavaScript cloud scripting language allow to automate repetitive business processes (e.g. expense approvals, time-sheet tracking, ticket management, order fulfillment…), link Google products with third party services (like sending custom emails and a calendar invitation to a list from MySQL database), create customer spreadsheet functions, and even build and collect user inputs through rich graphics interface and menus. Read more: Ajax magazine
Tangible Software Solutions Inc
Posted by
jasper22
at
11:43
|
Convert Between VB, C#, C++, and Java with the Most Accurate & Reliable Source Code Converters
Read more: Tangible Software Solutions
- Instant C# converts VB code to C#
- Instant VB converts C# code to VB
- C++ to C# Converter converts C++ code to C#
- C++ to VB Converter converts C++ code to VB
- C++ to Java Converter converts C++ code to Java
- C# to Java Converter converts C# code to Java
- VB to Java Converter converts VB code to Java
- C# to C++ Converter converts C# code to C++
- VB to C++ Converter converts VB code to C++
- Java to C++ Converter converts Java code to C++
- Java to VB & C# Converter converts Java code to VB or C#
"VB" refers to the .NET implementation of Visual Basic, previously known as "VB.NET".
Read more: Tangible Software Solutions
Creating a carousel with the PathListBox

While the PathListBox control provides an easy way to lay out items along a path, creating a carousel-like effect that appears 3 dimensional and has smooth scrolling requires a fair amount of custom code. Thankfully the Expression team has written this custom code and recently made it available on Codeplex. Enter PathListBoxUtils - this collection of behaviors, controls and extensions makes creating a carousel very easy.Install the PathListBoxUtils
The first step is to install the code samples.
- Go to the Expression Blend Codeplex site.
- Locate the PathBoxUtils section and download and install the latest release.
- Browse around the site and find other cool samples for later.
Create the PathListBox Now we need the PathListBox in place. This should be a familiar process by now, if you’ve been working through the whole series.
- Create a new “Silverlight Application + Website” project and name it “PLBCarousel”.
- Draw a Path with the Pen tool (P).
- Set the Fill to “No Brush”
- Right-click the Path and select the Path > Make Layout Path option.
Read more: .toolbox
ListBox Styling (Part1-ScrollBars) in Expression Blend & Silverlight
Posted by
jasper22
at
14:24
|
Welcome to my fifth Beginners tutorial for Expression Blend & Silverlight. And this time we will be focusing on ScrollBars, which are a core component of a complicated & nested Control like a ListBox. 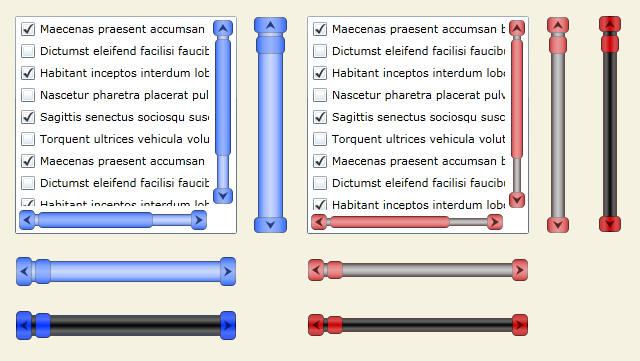
Read more: Codeproject

Read more: Codeproject
20 New jQuery Techniques – October
Posted by
jasper22
at
13:57
|
We don’t do jQuery roundups every month because we prefer to wait a longer period to get a better selection, more to choose from – anyway, this is October months roundup for jQuery techniques. This listing represents new techniques from late August until now. Cashrevelations.com presents a selection of new and fresh jQuery techniques – 20 new jQuery techniques released or updated during the period of August 20 until October 25 this year (2010). All these jQuery techniques are presented with demo. 20 Fresh & New jQuery Techniques – October 20101. Custom Animation Banner with jQuery
In this tutorial you will learn how to create a custom animation banner with jQuery by using the jQuery Easing Plugin and the jQuery 2D Transform Plugin. The idea is to have different elements in a banner that will animate step-wise in a custom way. 2. Quick Feedback Form – jQuery & PHP
In this tutorial by Martin Angelov you will learn how to create a solution for receiving quick feedback from your users – powered by jQuery, PHP and the PHPMailer class, this stylish form sends the users suggestions directly to your mailbox. 3. Wijmo – jQuery UI Widgets
Wijmo is a set of jQuery UI widgets for building web applications – a complete kit of over 30 jQuery UI Widgets. According to the developers, it is a mixture of jQuery, CSS3, SVG, and HTML5. Still in Beta – open to everyone who wants to participate. Read more: CashRevelations
In this tutorial you will learn how to create a custom animation banner with jQuery by using the jQuery Easing Plugin and the jQuery 2D Transform Plugin. The idea is to have different elements in a banner that will animate step-wise in a custom way. 2. Quick Feedback Form – jQuery & PHP
In this tutorial by Martin Angelov you will learn how to create a solution for receiving quick feedback from your users – powered by jQuery, PHP and the PHPMailer class, this stylish form sends the users suggestions directly to your mailbox. 3. Wijmo – jQuery UI Widgets
Wijmo is a set of jQuery UI widgets for building web applications – a complete kit of over 30 jQuery UI Widgets. According to the developers, it is a mixture of jQuery, CSS3, SVG, and HTML5. Still in Beta – open to everyone who wants to participate. Read more: CashRevelations
Microsoft retires Visual Studio Installer projects, replaces with InstallShield
Posted by
jasper22
at
12:24
|
This isn’t breaking or current, but it’s pretty startling to hear the word InstallShield on its own; to hear it will be combined with Visual Studio is just down right scary. Our future is now going to be filled with skinned installers and “Preparing to install” dialogs, even more so than now. Anyway, I originally received this tip via a newsletter from Flextera Software, the current folks handling the InstallShield product. The only official communication from Microsoft I could find on the matter is in the announcement header of the “ClickOnce and Setup & Deployment Projects” MSDN forum, back in July. Very classy. In Visual Studio 2010, we have partnered with Flexera, makers of InstallShield, to create InstallShield Limited Edition 2010 just for Visual Studio 2010 customers. The InstallShield Limited Edition 2010 offers comparable functionality to the Visual Studio Installer projects. In addition, you can build your deployment projects using Team Foundation Server and MSBuild. For more information, see http://blogs.msdn.com/b/deployment_technologies/archive/2010/04/20/installshield-limited-edition-is-available-for-download-in-visual-studio-2010.aspx. With InstallShield available, the Visual Studio Installer project types will not be available in future versions of Visual Studio.Read more: Within Windows
Защита Win32 и .NET приложений: обзор протектора Themida (X-Protector)
Posted by
jasper22
at
12:22
|
Этот обзор посвящен Themida (в прошлом X-Protector), одному из самых мощных и надежных протекторов Win32 приложений. Поскольку Themida совсем недавно понадобилась мне для одного из моих приложений, я решил написать по ней небольшой обзор. Заодно попросил автора ответить на некоторые интересующие меня вопросы. Думаю, ответы будут вам тоже интересны. Результаты этого небольшого интервью ищите в конце статьи. Хочу обратить внимание, что статья написана на базе Themida версии 2.1.3.30, последней на дату написания данного обзора. В ней появилось несколько новых возможностей по части макросов. Демка двухлетней давности с на официального сайта, их лишена. Read more: Habrahabr.ru
Silverlight Developer Guidance Map
Posted by
jasper22
at
12:21
|
If you’re a Silverlight developer or you want to learn Silverlight, this map is for you. Microsoft has an extensive collection of developer guidance available in the form of Code Samples, How Tos, Videos, and Training. The challenge is -- how do you find all of the various content collections? … and part of that challenge is knowing *exactly* where to look. This is where the map comes in. It helps you find your way around the online jungle and gives you short-cuts to the treasure troves of available content. The Silverlight Developer Guidance Map helps you kill a few birds with one stone:
Download the Silverlight Developer Guidance Map
Contents at a Glance
Read more: J.D. Meier's Blog
- It show you the key sources of Silverlight content and where to look (“teach you how to fish”)
- It gives you an index of the main content collections (Code Samples, How Tos, Videos, and Training)
- You can also use the map as a model for creating your own map of developer guidance.
Download the Silverlight Developer Guidance Map
Contents at a Glance
- Introduction
- Sources of Silverlight Developer Guidance
- Topics and Features Map (a “Lens” for Finding Silverlight Content)
- Summary Table of Topics
- How The Map is Organized (Organizing the “Content Collections”)
- Getting Started
- Architecture and Design
- Code Samples
- How Tos
- Videos
- Training
Read more: J.D. Meier's Blog
HTTPS Messaging with Client Side Certificate fails with IIS error 403
Posted by
jasper22
at
12:19
|
Symptoms
We have a Win2k3/Win2k8 Server. We are trying to send HTTPS messages to this Win2k3 Server. The Server Requires Client Side Certificates. The IIS log shows error 403.7 - Client Side Certs Reqd. Also if you enable deadlettering on the messages the messages end up in deadletter queue with HTTP error 403. Cause
If a Win2k8 Server has this problem then the problem is that the Network Service Account under which MSMQ runs does not access to the Private Key in MSMQ Certificate Store. Here is the error logged in the System log on Win2k8 Server. Log Name: System
Source: Schannel
Date: 8/18/2010 3:15:10 PM
Event ID: 36870
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: ComputerName Description:
A fatal error occurred when attempting to access the SSL client credential private key. The error code returned from the cryptographic module is 0x8009030d.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Schannel" />
<EventID Qualifiers="49152">36870</EventID>
<Level>2</Level>
<Task>0</Task>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2010-08-18T19:15:10.000Z" />
<EventRecordID>34419</EventRecordID>
<Channel>System</Channel>
<Computer>Computer Name</Computer>
<Security />
</System>
<EventData>
<Data>client</Data>
<Data>8009030d</Data>
</EventData>
</Event>Resolution
On Windows 2008 Server you need to execute the command at command prompt. The command below gives network service account access to the Private Keys for the Certificates. certutil.exe -service -service -repairstore MSMQ\My "" D:PAI(A;;GAGR;;;BA)(A;;GAGR;;;SY)(A;;GAGR;;;NS) MSMQ\MyRead more: MSMQ Information and Troubleshooting Blog
We have a Win2k3/Win2k8 Server. We are trying to send HTTPS messages to this Win2k3 Server. The Server Requires Client Side Certificates. The IIS log shows error 403.7 - Client Side Certs Reqd. Also if you enable deadlettering on the messages the messages end up in deadletter queue with HTTP error 403. Cause
If a Win2k8 Server has this problem then the problem is that the Network Service Account under which MSMQ runs does not access to the Private Key in MSMQ Certificate Store. Here is the error logged in the System log on Win2k8 Server. Log Name: System
Source: Schannel
Date: 8/18/2010 3:15:10 PM
Event ID: 36870
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: ComputerName Description:
A fatal error occurred when attempting to access the SSL client credential private key. The error code returned from the cryptographic module is 0x8009030d.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Schannel" />
<EventID Qualifiers="49152">36870</EventID>
<Level>2</Level>
<Task>0</Task>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2010-08-18T19:15:10.000Z" />
<EventRecordID>34419</EventRecordID>
<Channel>System</Channel>
<Computer>Computer Name</Computer>
<Security />
</System>
<EventData>
<Data>client</Data>
<Data>8009030d</Data>
</EventData>
</Event>Resolution
On Windows 2008 Server you need to execute the command at command prompt. The command below gives network service account access to the Private Keys for the Certificates. certutil.exe -service -service -repairstore MSMQ\My "" D:PAI(A;;GAGR;;;BA)(A;;GAGR;;;SY)(A;;GAGR;;;NS) MSMQ\MyRead more: MSMQ Information and Troubleshooting Blog
KitKat - The Lazy/Poor Man's Rootkit
Posted by
jasper22
at
12:19
|
IntroductionThis article is about using global hooks and window subclassing to create a pseudo-rootkit capable of hiding files from Explorer, Task Manager, Registry Editor, etc.Background It is assumed that the reader knows basic C++, Windows Programming, Global Hooks (for DLL injection) and of course, knows what a RootKit is.DisclaimerAlthough The program has been well tested, I have to include this disclaimer: The following program attempts to modify your operating system, which may/can make your system unstable. By executing/compiling the program you agree that neither the author nor the site hosting this article shall be held responsible for any damages occured due to this program. This program comes with NO WARRANTY. USE AT YOUR OWN RISK!! If this scares you, you probably shouldn't run this program. The author hereby disclaims himself. This article may not be re-published elsewhere without the permission of the author. Using the codeCompile the VC++ Project to obtain a DLL. You could write your own loader, but i have enclosed a small DLL Tester written in VB just in case. Once loaded, the DLL will establish a CallWnd hook. TheoryBefore I start a flame war or get found out by the Gurus out there, I'd like to state Kitkat is not a "System Roothit". It's more of a "User Rootkit" not to be confused with "UserMode Rootkits (Ring 3)"... There are 2 basic kinds of Rootkits:Kernel Mode Rootkits (Run in Ring0 and filters requests at the highest level)
UserMode Rootkits (Run in UserMode, uses API redirection, IAT hooking to get the job done)
The most powerful rootkits are no doubt the kernel rootkits. Usermode rootkits are less desirable because it is well known[^] that not all API calls can be hooked using IAT patching. (Link to Article)So which of these does KitKat belong to? Actually, its None of the above. Most rootkits have the following model OS ---> RootKit Filter ---> User Every file that is being stealthed is hidden from the system itself, which means even if one programmatically tries to locate a file, you'll not be able to find it since the filter intercepts any such requests. As a result it effectively stealths the files/processes from BOTH the SYSTEM and THE USER. If an AntiVirus (AV) program requests a file that was being stealthed, the AV would get an "INVALID_FILE_HANDLE" response. In contrast, Kitkat is based on the following model: Windows GUI ----> Kitkat RootKit Filter ----> User Read more: Codeproject
UserMode Rootkits (Run in UserMode, uses API redirection, IAT hooking to get the job done)
The most powerful rootkits are no doubt the kernel rootkits. Usermode rootkits are less desirable because it is well known[^] that not all API calls can be hooked using IAT patching. (Link to Article)So which of these does KitKat belong to? Actually, its None of the above. Most rootkits have the following model OS ---> RootKit Filter ---> User Every file that is being stealthed is hidden from the system itself, which means even if one programmatically tries to locate a file, you'll not be able to find it since the filter intercepts any such requests. As a result it effectively stealths the files/processes from BOTH the SYSTEM and THE USER. If an AntiVirus (AV) program requests a file that was being stealthed, the AV would get an "INVALID_FILE_HANDLE" response. In contrast, Kitkat is based on the following model: Windows GUI ----> Kitkat RootKit Filter ----> User Read more: Codeproject
Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate (KB976932)
Posted by
jasper22
at
12:16
|
Overview
Windows 7 and Windows Server 2008 R2 SP1 Release Candidate helps keep your PCs and servers on the latest support level, provides ongoing improvements to the Windows Operating System (OS), by including previous updates delivered over Windows Update as well as continuing incremental updates to the Windows 7 and Windows Server 2008 R2 platforms based on customer and partner feedback, and is easy for organizations to deploy a single set of updates. Windows 7 and Windows Server 2008 R2 SP1 Release Candidate will help you:
Keep your PCs supported and up-to-date
Get ongoing updates to the Windows 7 platform
Easily deploy cumulative updates at a single time
Meet your users' demands for greater business mobility
Provide a comprehensive set of virtualization innovations
Provide an easier Service Pack deployment model for better IT efficiency
In order to download and install the Windows 7 and Windows Server 2008 R2 SP1 Release Candidate you must currently have a Release to Manufacturing (RTM) version of Windows 7 or Windows Server 2008 R2 already installed. If you have previously installed the Windows 7 and Windows Server 2008 R2 SP1 Beta on your machine, you must uninstall the beta before installing the Release Candidate.Windows 7 and Windows Server 2008 R2 SP1 Release Candidate is available for installation in the same languages made available at original launch of Windows 7 and Windows Server 2008 R2. Read more: MS Download
Overview
The following documentation for Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate is provided here: Hotfixes and Security Updates included in Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate
Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate Notable Changes
Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate Test Guidance
For additional information (including how to deploy the service pack and how to join the public beta), please see http://technet.microsoft.com/evalcenter/ff183870.aspx. Support URLs:http://technet.microsoft.com/evalcenter/ff183870.aspxRead more: MS Download
Windows 7 and Windows Server 2008 R2 SP1 Release Candidate helps keep your PCs and servers on the latest support level, provides ongoing improvements to the Windows Operating System (OS), by including previous updates delivered over Windows Update as well as continuing incremental updates to the Windows 7 and Windows Server 2008 R2 platforms based on customer and partner feedback, and is easy for organizations to deploy a single set of updates. Windows 7 and Windows Server 2008 R2 SP1 Release Candidate will help you:
Keep your PCs supported and up-to-date
Get ongoing updates to the Windows 7 platform
Easily deploy cumulative updates at a single time
Meet your users' demands for greater business mobility
Provide a comprehensive set of virtualization innovations
Provide an easier Service Pack deployment model for better IT efficiency
In order to download and install the Windows 7 and Windows Server 2008 R2 SP1 Release Candidate you must currently have a Release to Manufacturing (RTM) version of Windows 7 or Windows Server 2008 R2 already installed. If you have previously installed the Windows 7 and Windows Server 2008 R2 SP1 Beta on your machine, you must uninstall the beta before installing the Release Candidate.Windows 7 and Windows Server 2008 R2 SP1 Release Candidate is available for installation in the same languages made available at original launch of Windows 7 and Windows Server 2008 R2. Read more: MS Download
Overview
The following documentation for Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate is provided here: Hotfixes and Security Updates included in Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate
Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate Notable Changes
Windows 7 and Windows Server 2008 R2 Service Pack 1 Release Candidate Test Guidance
For additional information (including how to deploy the service pack and how to join the public beta), please see http://technet.microsoft.com/evalcenter/ff183870.aspx. Support URLs:http://technet.microsoft.com/evalcenter/ff183870.aspxRead more: MS Download
WP7 Development Tips Part 1
Posted by
jasper22
at
12:15
|
Performance is the area that we probably spend the most time on in all our apps. Building apps on the phone is just way different than building desktop apps. Things that might be really minor optimizations on a desktop Silverlight can really make a difference on desktop Silverlight apps. Developing on the phone is an issue of economics where processing power is a scarce resource. You have to be conscious of the tradeoffs of using things like binding, layout controls, dependency injection, etc with their impact on performance. When I first started building phone apps I was excited to use nRoute and it’s nice features around MVVM/Resource Location/Messaging/Navigation. I wanted to have this really perfect loosely coupled architecture that used biding for everything/minimal code behind, had great designer support and dynamically resolved the proper services and models. In practice, that is not generally high performance code on the phone. If you are using some extra frameworks, really be conscious of the impact on performance and decide if you really need that architecture. What might work wonderfully on a more complicated desktop line of business app might not work as well on the phone. You just have to expect to write more optimization in a mobile app regardless if it’s the iphone, wp7 or android. Silverlight was billed as “same Silverlight, just on the phone”. That is mostly true in terms of the api, but not necessarily true in terms of the actual runtime. It’s really a brand new runtime based on Silverlight 3 with some extra features added, so certain pieces of code might not have the same performance characteristics. I’ve seen a lot of articles from various other people that talk about “buttery smooth scrolling” and other performance tips. At times the tips are a little too generalized. When you try to optimize something for performance on the phone, you really need to take into account your specific circumstances and find the right combination that works for your app. Always test and benchmark. Some things are more difficult to measure without real profiling tools, but do the best you can. Also be aware that scrolling in 3rd party apps on the phone is just not great at the moment. The native OS apps use a different UI framework that is going to make all but the simplest 3rd party apps feel sluggish so don’t feel too bad if your app scrolling seems slower. It’s probably not entirely your fault. Although this guy (around 8:50) seems to disagree. Sure 3rd party apps will get better with more experience and time, but the runtime needs to also get better. It’s the v1 of a new platform for everyone. Finally, most of my thought are based around apps like twitter or facebook or other apps that require lots of live network data and have more complicated/longer list based screens. A 2 screen unit converter app is just going to be faster because it’s a simpler app and you don’t really need to optimize much. So here are some things that you can try think about for your application:
Read more: Clarity Consulting
- Data binding is always going to be slower than just directly setting a value. If you don’t have to databind, try to avoid it. I see lots of people going out of their way to MVVM everything and create bindable app bars. Feel free to just wire up a handler once in awhile or just directly set some text. There are other ways of centralizing code for reuse instead of trying to adhere to a strict pattern. If you are trying to animate in a screen and data bind simultaneously, most of the animations will get chopped. Just directly set enough pieces of data to have something to animate in and then you can do more intensive data binding after the animation is complete.
- As mentioned above – consider the tradeoff of always following the same pattern just for the sake of maintaining the pattern. Sure it might be easier to maintain, but high performance code doesn’t always look pretty. Be flexible, take shortcuts and do what makes sense for a specific part of the application. That’s not to say you should ever write bad code, just don’t focus on creating an architectural masterpiece in lieu of something that is performs well. The end user only sees what you put on screen, not the code behind it. They don’t really care that you used MEF and have an awesome messaging framework. When i see people over-engineer what should be a simple app just to adhere to some theoretical best practices I get sad.
Read more: Clarity Consulting
A Step-by-Step Guide to Building and Deploying your Windows Phone 7 Applications
Posted by
jasper22
at
12:13
|
As of the publication date of this article, Windows Phone 7 devices are becoming available in Europe and will hit North America on November 8th 2010 and Microsoft is gradually opening up the application submission process to registered developers. Microsoft expects as many as 1,000 applications available at launch. Will one of those applications be yours? This article takes you through the process of getting the tools, registering as a developer, building a basic Silverlight application for Windows Phone 7 (©Copyright Colin Melia 2010), and submitting it to the marketplace. Getting Started - Application Platform
The available developer tools allow you to build Silverlight and XNA software for Windows Phone 7. For an introduction to the platform see my previous article. In this article, I’ll be showing you how to build a Silverlight application. The Hub for Applications
Just before device launch Microsoft transformed the Windows Phone 7 developer portal and combined it with the Xbox Creator’s Club, with everything now available in one place called the App Hub.
The available developer tools allow you to build Silverlight and XNA software for Windows Phone 7. For an introduction to the platform see my previous article. In this article, I’ll be showing you how to build a Silverlight application. The Hub for Applications
Just before device launch Microsoft transformed the Windows Phone 7 developer portal and combined it with the Xbox Creator’s Club, with everything now available in one place called the App Hub.
An introduction to Tuple
Posted by
jasper22
at
12:09
|
IntroductionC#4.0 has introduce a new feature call Tuple.Definition
In mathematics and computer science, a tuple is an ordered list of elements. In set theory, an (ordered) n-tuple is a sequence (or ordered list) of n elements, where n is a positive integer. There is also one 0-tuple, an empty sequence. (From Wikipedia) Purpose: Some time we need to return more than one value from a method or function.Using the codeLet us perform a simple experiment for the basic arithmetic operations for the concept to understand. Let us first write our Calculate Function ///
/// Calculate
private void Calculate(out int add, out int sub,out int mul,out int div)
{
int num1 = 5;
int num2 = 4;
add = num1 + num2;
sub = num1 - num2;
mul = num1 * num2;
div = num1 / num2;
}Older approach (Till dotnet 3.5)Approach 1: Using OUT parameterRead more: Codeproject
In mathematics and computer science, a tuple is an ordered list of elements. In set theory, an (ordered) n-tuple is a sequence (or ordered list) of n elements, where n is a positive integer. There is also one 0-tuple, an empty sequence. (From Wikipedia) Purpose: Some time we need to return more than one value from a method or function.Using the codeLet us perform a simple experiment for the basic arithmetic operations for the concept to understand. Let us first write our Calculate Function ///
/// Calculate
private void Calculate(out int add, out int sub,out int mul,out int div)
{
int num1 = 5;
int num2 = 4;
add = num1 + num2;
sub = num1 - num2;
mul = num1 * num2;
div = num1 / num2;
}Older approach (Till dotnet 3.5)Approach 1: Using OUT parameterRead more: Codeproject
10 Tips you should know about “Watch Window” While debugging in Visual Studio
Posted by
jasper22
at
12:06
|
Watch windows is one of most commonly used debugging tool with Visual Studio. We generally used to explore the objects, values, properties and other nested objects as a tree structure. Most of the time we used watch window to only view the values or change the current object properties values to see the effects of changed object during debugging. But we can use watch windows for many different purposes. In this blog post I am going to show 10 Tips, that may help you while dealing with Watch Window. Tips 1 : Calling Methods From Watch Window
As I said earlier, most of time we used watch window to explore the objects and it’s properties but we can call a methods from watch window as well. If you are exploring some objects inside watch window, you can simple call any of the methods for that object inside watch window. Tips 2 : Drag-Drop & Copy-Paste Code inside Watch Window
Tips 3: Use Runtime Object’s With Help of Immediate Window
Tips 4 : Using Multiple Watch Window
Tips 5 : Moving Values between multiple Watch Window
Tips 6 : Create Object IDRead more: Abhijit's World of .NET
As I said earlier, most of time we used watch window to explore the objects and it’s properties but we can call a methods from watch window as well. If you are exploring some objects inside watch window, you can simple call any of the methods for that object inside watch window. Tips 2 : Drag-Drop & Copy-Paste Code inside Watch Window
Tips 3: Use Runtime Object’s With Help of Immediate Window
Tips 4 : Using Multiple Watch Window
Tips 5 : Moving Values between multiple Watch Window
Tips 6 : Create Object IDRead more: Abhijit's World of .NET
Visual Studio - Always Run as Administrator
Posted by
jasper22
at
12:03
|
By elevating permissions for Visual Studio, you can perform all tasks related to features such as building and debugging applications, which 'might not' work correctly under standard user permissions. To elevate permissions, go to the Start Menu and right click Visual Studio > click 'Run as Administrator'. However if you are the only user on the machine and frequently need to do this, it could be annoying, plus there are chances you could forget running VS with elevated permissions. Here's how to always run Visual Studio as Administrator in Windows Vista/ Windows 7.Go to Start > All Programs > Expand Visual Studio folder > Right click Visual Studio.exe > Properties 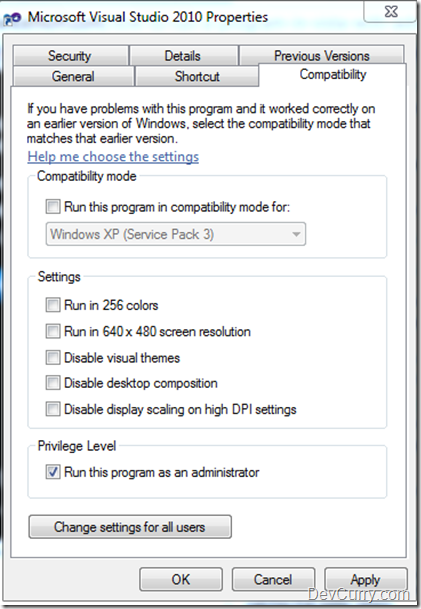
Read more: devcurry

Read more: devcurry
The Future of Silverlight
Posted by
jasper22
at
12:01
|
There are a lot of questions being asked about where Silveright is going, and what is it for. Microsoft has been giving pretty straight answers on the future of Silverlight but there has been a lack of quality reporting on those answers. For example, when Steve Ballmer was recently asked about HTML 5 and Silverlight his answer was that Silverlight started off as a cross-browser, cross-technology [for making websites] but that it has been repurposed as a [cross-browser, cross-technology] platform for creating client applications. This was transformed by Network World into Ballmer saying that he "sees Silverlight as useful for adding multimedia to client apps" and they also put a description on the article saying that Ballmer was commenting on the "near death of Silverlight." It is no wonder that people are confused, perfectly good and straighforward answers are being transformed into meaningless FUD by the media. With Ballmer's actual response (which you can see at the link above), the Gu's recent video with John Papa, and the Silverlight's teams on Future of Silverlight blog post, I think the answers from Microsoft have been very clear on where Silverlight is going. However, I know there is still some confusion and people want a simple answer. So, I am going to try and condense this down to a simple graphic: 
Read more: The Elephant and the Silverlight

Read more: The Elephant and the Silverlight
More Secure Browsing Over Wi-Fi
Posted by
jasper22
at
11:57
|
In recent days, a new tool called Firesheep has become available that can “sniff out” the login information that’s being sent over wireless networks. Such tools have always been available, but this one makes it easy for anyone to collect other people’s private data. I’m sure that you, as a web professional, know that it’s important to use a VPN or to encrypt your connection by using https:// whenever you can. But this might be a good time to remind colleagues and friends. And there are several ways of forcing secure connections. With Firefox, you can use:
- HTTPS-Anywhere, an add-on that comes pre-configured with rules for over two dozen popular sites, including Facebook and Twitter. You can add your own rules, but you’ll need to edit an XML file.
- Force-TLS, an add-on that has a much simpler way of adding sites to connect with securely, but it doesn’t come with any pre-configured sites.
How To Protect Your Login Information From Firesheep
Posted by
jasper22
at
10:54
|

TechCrunch reader Steve Manuel claims to have found a workaround to Firesheep, the controversial Firefox extension that allows anyone on an insecure open Wifi network to access user login info for almost every single social network in existence. Firesheep banks on the fact that most social sites default to the HTTP protocol because it’s quicker. The already existing Firefox extension Force-TLS attempts to circumvent this by forcing those sites to use the HTTPS protocol, therefore making user cookies invisible to Firesheep. Like the alternative option HTTPS Everywhere, the Force-TLS Firefox extension allows your browser to change HTTP to HTTPS on sites that you indicate in the Firefox Add On “Preferences” menu, protecting your login information and ensuring a secure connection when you access social sites. HTTPS encrypts user data, so if a script like Firesheep’s like tries to pull it, it can’t be read. Force-TLS forces a number of sites to make all of their requests over an SSL secured channel and while some sites, like Amazon, don’t currently have the secure option, the majors like Facebook, Twitter, Google, etc all allow a HTTPS connection. How to configure:1. Download the plugin here and install into Firefox.Read more: Techcrunch
Firesheep
Posted by
jasper22
at
10:53
|

It's extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable. HTTP session hijacking (sometimes called "sidejacking") is when an attacker gets a hold of a user's cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy. This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. The only effective fix for this problem is full end-to-end encryption, known on the web as HTTPS or SSL. Facebook is constantly rolling out new "privacy" features in an endless attempt to quell the screams of unhappy users, but what's the point when someone can just take over an account entirely? Twitter forced all third party developers to use OAuth then immediately released (and promoted) a new version of their insecure website. When it comes to user privacy, SSL is the elephant in the room. Today at Toorcon 12 I announced the release of Firesheep, a Firefox extension designed to demonstrate just how serious this problem is.After installing the extension you'll see a new sidebar. Connect to any busy open wifi network and click the big "Start Capturing" button. Then wait. Read more: { codebutler }
An introduction to System.Lazy
Posted by
jasper22
at
10:51
|
IntroductionObject creation is always expensive. It is better to create object when it is actually needed to do so. Otherwise, unnecessary memory allocation on the heap will cause a memory load. Lazy<T> which is defined in the mscorlib assembly and belongs to System namespace, ensures that object is created only when it is needed. Using the codeConsider the below programstatic void Main(string[] args)
{ var lazyObject = new Lazy>
(
() =>
{
List expandoList = new List();
//Writing to Expando Collection
for (int i = 3; i-- > 1; )
{
dynamic dynObject = new ExpandoObject();
dynObject.Prop1 = GetValue(i);
expandoList.Add(dynObject);
}
return expandoList;
}
);Console.WriteLine("Enter a value. 1 to proceed");
var read = Console.ReadLine();
List expandoObj = null; if (read == "1")
{
//If the value is not created
if (!lazyObject.IsValueCreated)
//Gets the lazily initialized value of the current Lazy>
//instance.
expandoObj = lazyObject.Value;
//Read the values once the object is initialize
if (expandoObj != null)
{
Console.WriteLine(Environment.NewLine);
Console.WriteLine("The values are:");
foreach (dynamic d in expandoObj)
Console.WriteLine(d.Prop1);
} }
}The GetValue method is as underprivate static string GetValue(int i)
{
Dictionary dict = new Dictionary();
dict.Add(1, "Niladri");
dict.Add(2, "Arina");
return dict[i];
}Let us go step by step as what we are doing hereRead more: Codeproject
{ var lazyObject = new Lazy>
(
() =>
{
List expandoList = new List();
//Writing to Expando Collection
for (int i = 3; i-- > 1; )
{
dynamic dynObject = new ExpandoObject();
dynObject.Prop1 = GetValue(i);
expandoList.Add(dynObject);
}
return expandoList;
}
);Console.WriteLine("Enter a value. 1 to proceed");
var read = Console.ReadLine();
List expandoObj = null; if (read == "1")
{
//If the value is not created
if (!lazyObject.IsValueCreated)
//Gets the lazily initialized value of the current Lazy>
//instance.
expandoObj = lazyObject.Value;
//Read the values once the object is initialize
if (expandoObj != null)
{
Console.WriteLine(Environment.NewLine);
Console.WriteLine("The values are:");
foreach (dynamic d in expandoObj)
Console.WriteLine(d.Prop1);
} }
}The GetValue method is as underprivate static string GetValue(int i)
{
Dictionary dict = new Dictionary();
dict.Add(1, "Niladri");
dict.Add(2, "Arina");
return dict[i];
}Let us go step by step as what we are doing hereRead more: Codeproject
SQL SERVER – A Brief Introduction to DW 2.0
The traditional form of storing digital data has been disk storage. However, the huge advances in technology means that there has been a huge need for data storage to evolve to keep up with the fast-changing times. Microsoft SQL Server has gone through a huge overhaul in order to keep up with the amount of data storage that is necessary, and that is where data warehousing comes into play. For many online applications, there is a need to not only access small amount of information from disk storage, but large amounts in the forms of sets. SQL Server allows access to these sets of data in a sequential manner that optimizes computer. This proprietary technology makes SQL Server the go-to system to fit these computing needs. SQL Server has also solved the problem of changing from “data marts” to data warehouses. As companies grow, their digital storage needs change and expand as well. Previously, transferring a system over to an SQL Server meant having to destroy old data during the transfer. This was the source of a lot of data loss and server problems. However, the new versions of SQL Server have built-in systems that help organizations transfer to the larger data storage system. The costs of data storage and data warehousing are becoming a huge concerns for small businesses and corporations alike. It is a known rule of thumb that the larger the main server, the more expensive it is. SQL Server also addresses this problem by allowing data warehousing to be run on multiple processors – in the end rendering it much cheaper than having one main data warehousing server. SQL Servers uses the “hub-and-spoke” system, which allows data warehousing to be broken up by multiple systems without losing any data. Read more: Journey to SQL Authority with Pinal Dave
Updated Windows Registry and Mac resources & Jad's Software....updated
Posted by
jasper22
at
14:23
|
As several sites have rightfully pointed out....Accessdata has made a huge jump ahead with their recent release of FTK Imager v3.0. (not to mention FTK 3.2 and their most recent "Volatile tab.") Just finished testing it today by mounting physical images and using VFC to virtually boot XP and Win7 systems. Flawless! While wandering around their site (actually looking for updated RSR files to add to their most recent Registry Viewer version), I stumbled across two additional documents that I believe are very worthy of a good read - or at least printing out as a permanent reference. Registry Quick Find Chart - a very recently updated 34-page reference documenting Registry locations for the standard 5 Registry files. The document has a few new columns in the document - one which lists what versions of Windows the reference pertains to (ie: XP, Vista or Win7) and a second column that states when the Registry reference is updated (immediately, when document opened, at logon...) This document would also be great starting reference to initiate further research on Registry locations and extractable artifacts. D/L it....know it....print it and keep it handy! Read more: Computer Forensics and IR - What's New?
FloatingWindow - Multi-windows Interface for Silverlight 4
Posted by
jasper22
at
14:22
|
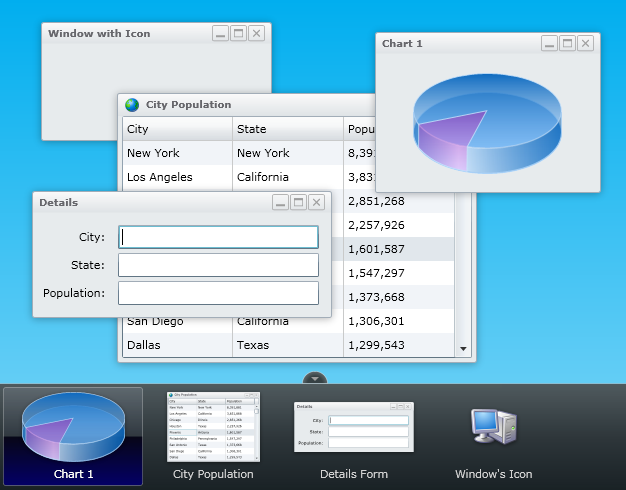
Added possibility to snap in moving or resizing window to the nearest window's boundary
Window can be minimized, maximized and restore its position and size
Added a task bar, displaying minimized or all windows
The task bar can display a snapshot of a minimized window or an icon - a FrameworkElement attached to the window.
How It WorksReally I don't want to explain how it works - you have my source code. I'd better describe how it can be used. But before we start, I'll introduce some terms and properties used in the library. The picture below will help me to illustrate them Read more: Codeproject
Использование Thrift в .NET
Posted by
jasper22
at
14:21
|
Хочу поделиться с вами примером того как можно использовать такую удобную штуку как Thrift в своих .NET проектах. Для тех кто не знает, Thrift — это фреймворк для облегчения взаимодействия между кодом написанным на разных языках, а именно C++, Java, Python, PHP, Ruby, Erlang, Perl, Haskell, C#, Cocoa, Smalltalk и OCaml. Thrift используется и был изначально создан Facebook. Так же неоднократно упоминался здесь, на Хабре, но примеров для .NET я не нашел, кстати пошаговое руководство для .NET отсутствует и на официальном сайте. В гугле если честно, тоже не смог найти, хотя может плохо искал. Thrift позволяет один раз описать сервис, структуры данных и даже исключения, а потом сгенерировать код для всех поддерживаемых языков. Таким образом, если вы, например, напишете сервер с использованием Thrift на .NET, то вы
- Сэкономите кучу времени для написания клиент серверного приложения, например с использованием сокетов.
- Почти автоматически получаете клиентов на всех поддерживаемых языках.
An introduction to Complex Struct of dotnet 4.0
Posted by
jasper22
at
14:19
|
The Complex struct which resides in System.Numerics assembly is use for representing complex numbers.For using the Complex struct, we need to Add the System.Numerics assembly to our projectUsing the code Let us see some examples as how it helps usExample 1: Display the Real,Imaginary,Magnitude and Phase parts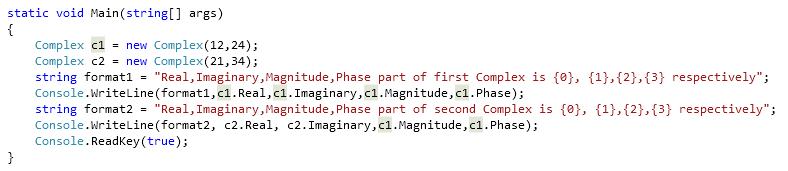
Read more: Codeproject

Read more: Codeproject
Create your own packet sniffer in C
Posted by
jasper22
at
14:17
|
A simple implementation of a packet sniffer in C on linux platform using the libpcap library. This packet sniffer currently sniffs IP , TCP , ICMP and UDP packets. It can be modified to any protocol as needed just by introducing the header information in it. It is a little modified version of sniffer from tcpdump website.Note : To run this code you require root permissions. Here's the code: //sniffer.c
//To compile : gcc -o sniffer sniffer.c
//To run : ./sniffer [interface-name]#include <pcap.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <ctype.h>
#include <errno.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>/* default snap length (maximum bytes per packet to capture) */
#define SNAP_LEN 1518/* ethernet headers are always exactly 14 bytes [1] */
#define SIZE_ETHERNET 14/* Ethernet addresses are 6 bytes */
#define ETHER_ADDR_LEN 6/* Ethernet header */
struct sniff_ethernet {
u_char ether_dhost[ETHER_ADDR_LEN]; /* destination host address */
u_char ether_shost[ETHER_ADDR_LEN]; /* source host address */
u_short ether_type; /* IP? ARP? RARP? etc */
};/* IP header */
struct sniff_ip {
u_char ip_vhl; /* version << 4 | header length >> 2 */
u_char ip_tos; /* type of service */
u_short ip_len; /* total length */
u_short ip_id; /* identification */
u_short ip_off; /* fragment offset field */
#define IP_RF 0x8000 /* reserved fragment flag */
#define IP_DF 0x4000 /* dont fragment flag */
#define IP_MF 0x2000 /* more fragments flag */
#define IP_OFFMASK 0x1fff /* mask for fragmenting bits */
u_char ip_ttl; /* time to live */
u_char ip_p; /* protocol */
u_short ip_sum; /* checksum */
struct in_addr ip_src,ip_dst; /* source and dest address */
};
#define IP_HL(ip) (((ip)->ip_vhl) & 0x0f)
#define IP_V(ip) (((ip)->ip_vhl) >> 4)/* TCP header */
typedef u_int tcp_seq;Read more: Simplest Codings
//To compile : gcc -o sniffer sniffer.c
//To run : ./sniffer [interface-name]#include <pcap.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <ctype.h>
#include <errno.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>/* default snap length (maximum bytes per packet to capture) */
#define SNAP_LEN 1518/* ethernet headers are always exactly 14 bytes [1] */
#define SIZE_ETHERNET 14/* Ethernet addresses are 6 bytes */
#define ETHER_ADDR_LEN 6/* Ethernet header */
struct sniff_ethernet {
u_char ether_dhost[ETHER_ADDR_LEN]; /* destination host address */
u_char ether_shost[ETHER_ADDR_LEN]; /* source host address */
u_short ether_type; /* IP? ARP? RARP? etc */
};/* IP header */
struct sniff_ip {
u_char ip_vhl; /* version << 4 | header length >> 2 */
u_char ip_tos; /* type of service */
u_short ip_len; /* total length */
u_short ip_id; /* identification */
u_short ip_off; /* fragment offset field */
#define IP_RF 0x8000 /* reserved fragment flag */
#define IP_DF 0x4000 /* dont fragment flag */
#define IP_MF 0x2000 /* more fragments flag */
#define IP_OFFMASK 0x1fff /* mask for fragmenting bits */
u_char ip_ttl; /* time to live */
u_char ip_p; /* protocol */
u_short ip_sum; /* checksum */
struct in_addr ip_src,ip_dst; /* source and dest address */
};
#define IP_HL(ip) (((ip)->ip_vhl) & 0x0f)
#define IP_V(ip) (((ip)->ip_vhl) >> 4)/* TCP header */
typedef u_int tcp_seq;Read more: Simplest Codings
An introduction to BIG INTEGER class of dotnet 4.0
Posted by
jasper22
at
14:04
|
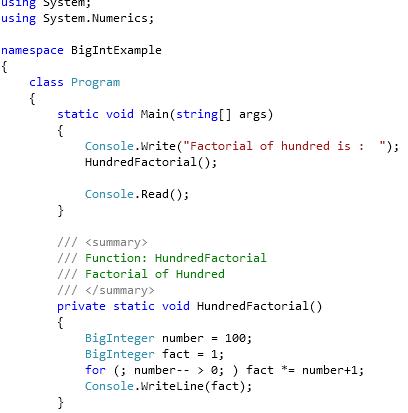
IntroductionBigInteger class that resides in the System.Numerics namespace helps in representing any large integer without any loss of precision. It has been introduced earlier in dotnet framework 3.5 but was removed(don’t know the exact reason). However, it is again back in framework 4.0 Using the codeExample 1: To find the factorial of 100.
Boot to VHD / Boot from VHD
Posted by
jasper22
at
14:03
|
I recently learned about boot to/from Virtual Hard Disk (VHD) and how it makes it very easy to set up and manage multiple system configurations. After having my Windows 7 configuration get completely messed up and being really lazy about creating clean OS images, I figured I would give the VHD route a try and discovered it's much easier than I expected - if you can create an image in Virtual PC, you can change it to be bootable. The gist of how it works is you create a virtual image for use within a VHD (I used Hyper-V from Server R2) and then you use bcdedit (the Windows boot manager, BCD stands for Boot Configuration Data) to copy an existing entry and point that entry to the VHD file. Here are the steps I took with some details where things get a little tricky:First, I installed Windows Server 2008 R2.Next, I opened Server Manager and added/enabled the Hyper-V role.Next, I opened the Hyper-V manager and added a new Virtual Machine (VM). I installed Windows 7 in the VM.After the VM was set up, I shut it down and copied the virtual machine file [Win7.vhd] from the default folder [C:\ProgramData\Microsoft\Windows\Hyper-V\] to a new folder named to [c:\VHDs\Win7.vhd]. Finally, I opened an administrator command prompt and modified my boot configuration.To modify my boot configuration, I needed to use bcdedit to add a virtual hard disk to the boot menu. All I did was run the following commands: C:\>bcdedit /copy {current} /d "Windows Server 2008 R2-Boot from VHD"
This returned a GUID, I copied that GUID and ran the following commands with the GUID set:bcdedit /set {newguid} device vhd=[locate]\VHDs\Win7.vhd
bcdedit /set {newguid} osdevice vhd=[locate]\VHDs\Win7.vhd
bcdedit /set {newguid} detecthal onAnd that was it. Read more: See Also
This returned a GUID, I copied that GUID and ran the following commands with the GUID set:bcdedit /set {newguid} device vhd=[locate]\VHDs\Win7.vhd
bcdedit /set {newguid} osdevice vhd=[locate]\VHDs\Win7.vhd
bcdedit /set {newguid} detecthal onAnd that was it. Read more: See Also
Interesting tips in JavaScript
Posted by
jasper22
at
14:01
|
Describes about 5 interesting tips in JavaScript
In this article I would like to share some of the interesting things I came to know on JavaScript.These are the five tips we will see.. #1 Dynamic script loading #2 Instantiation without "new" #3 Memoizing #4 Mixin classes #5 Inheritance by cloning #1 Dynamic script loading Most of the times, we load all the scripts and other resources initially when the page renders. Loading all the scripts initially increases the HTTP requests to the server also considerably reduces the time taken to see the page by user. As an example, when working with Google Maps usually we load the Google Maps API initially and show the map. What will be the case if you want to show the map only the user needs it. Here is the script that does that job! var api = "http://maps.google.com/maps/api/js?sensor=false&callback=initialize";//The function that loads any external JavaScript dynamically
function loadScript(src) {
var script = document.createElement("script");
script.type = "text/javascript";
script.src = src;
document.body.appendChild(script);
}
//Google maps api callback
function initialize() {
var myLatlng = new google.maps.LatLng(-34.397, 150.644);
var myOptions = {
zoom: 8,
center: myLatlng,
mapTypeId: google.maps.MapTypeId.ROADMAP
}
var map = new google.maps.Map(document.getElementById("map_canvas"), myOptions);
}<div id="map_canvas" style="width:500px; height:500px"></div>
<input type="button" value="Load Map" onclick="loadScript(api)" /> Read more: Codeproject
In this article I would like to share some of the interesting things I came to know on JavaScript.These are the five tips we will see.. #1 Dynamic script loading #2 Instantiation without "new" #3 Memoizing #4 Mixin classes #5 Inheritance by cloning #1 Dynamic script loading Most of the times, we load all the scripts and other resources initially when the page renders. Loading all the scripts initially increases the HTTP requests to the server also considerably reduces the time taken to see the page by user. As an example, when working with Google Maps usually we load the Google Maps API initially and show the map. What will be the case if you want to show the map only the user needs it. Here is the script that does that job! var api = "http://maps.google.com/maps/api/js?sensor=false&callback=initialize";//The function that loads any external JavaScript dynamically
function loadScript(src) {
var script = document.createElement("script");
script.type = "text/javascript";
script.src = src;
document.body.appendChild(script);
}
//Google maps api callback
function initialize() {
var myLatlng = new google.maps.LatLng(-34.397, 150.644);
var myOptions = {
zoom: 8,
center: myLatlng,
mapTypeId: google.maps.MapTypeId.ROADMAP
}
var map = new google.maps.Map(document.getElementById("map_canvas"), myOptions);
}<div id="map_canvas" style="width:500px; height:500px"></div>
<input type="button" value="Load Map" onclick="loadScript(api)" /> Read more: Codeproject
Microsoft(R) SQL Server(R) StreamInsight 1.1
Posted by
jasper22
at
13:53
|
OverviewMicrosoft® StreamInsight is a platform for the continuous and incremental processing of unending sequences of events (event streams) from multiple sources with near-zero latency. These requirements, shared by vertical markets such as manufacturing, oil and gas, utilities, financial services, health care, web analytics, and IT and data center monitoring, make traditional store and query techniques impractical for timely and relevant processing of data. The ability to monitor, analyze and act on the data in motion provides significant opportunity to make more informed business decisions in near real-time. Further resources can be found on the StreamInsight Blog, its MSDN Portal, and on CodePlex.These are the new features in StreamInsight 1.1:
Microsoft® StreamInsight has two different methods to complete the installation process:
Attended Installation – an interactive user interface will guide you through the set-up process and obtain all of the information and consent required to complete the installation. This includes the displaying, acknowledgement, and archiving of the applicable SQL Server license terms. Read more: MS Download
- .Net Sequence Support
With the new release, StreamInsight supports event sources and event sinks that implement the IObservable and IEnumerable interfaces. These interfaces are the dominant general-purpose contracts in the .NET Framework for pulling (IEnumerable) and pushing (IObservable) data among an application’s components. This new API is especially convenient for historical queries, where the full set of input events is known in advance, and ad-hoc queries over live data sources, where a query is short-lived and only needs to exist as long as the client app listens to the results. This new API also simplifies query testing.For the integration with IObservable, you need to have .NET 4.0 installed.
- Side-by-Side Installation Support
The new version of StreamInsight installs without replacing a previous version. If you have an existing installation, 1.0 and 1.1 will co-exist on the same system. All existing and new StreamInsight applications will automatically link to the new libraries, unless specified otherwise by redirecting the assembly versions through the application’s configuration file. No recompilation of existing applications is necessary.
- Performance and Stability Improvements
A number of bug fixes and performance improvements have gone into this release. Notable is the reduction of latency for hopping windows, where a certain pattern of CTIs would make the engine hold back window results longer than needed in previous versions. Another important fix drastically increases throughput for join operations on edge streams (produced by an edge adapter or the Clip operator), which is a common pattern when combining real-time with reference streams.The Microsoft® StreamInsight Client package installs a subset of Microsoft® StreamInsight which lets you implement only the client side functionality: Connecting to an existing StreamInsight server, managing queries, and using the debugger tool. It does not support running an embedded server or creating a StreamInsight service. The license for the Microsoft® StreamInsight Client is free.
Microsoft® StreamInsight has two different methods to complete the installation process:
Attended Installation – an interactive user interface will guide you through the set-up process and obtain all of the information and consent required to complete the installation. This includes the displaying, acknowledgement, and archiving of the applicable SQL Server license terms. Read more: MS Download
AJAXPRC
Posted by
jasper22
at
13:52
|
AJAXPRC : the JavaScript Remote Procedure Call, fast and easy . It allows JavaScript to be able to call into the server-side methods synchronously or asynchronously, based on JSON, open-source license(LGPL).
Use AJAXRPC, you can develop as a traditional C / S procedures, to develop the WEB program that allows WEB development simpler and more efficient.
Languages Supported: Java, .Net, Php.Browsers Supported: IE、FireFox、Opera、Safari、Chrome.
Downloads: Java .Net PHP
Developer Guide:English Chinese Japanese
Latest version: 1.0
Latest updated: 2010-10-10AJAXRPC Quick StartFirst,we have to define a class and a static method: public class Test {
public static String sayHello(String name){
return "hello, " + name;
}
}Note: The static methord must be a public method.
Then we can call the method on the server by the AJAXRPC client program.
Note:When we call the RPC methods,if there is no callback function, then the call is synchronous;if there is one, then the call is asynchronous.Read more: AJAXPRC
Use AJAXRPC, you can develop as a traditional C / S procedures, to develop the WEB program that allows WEB development simpler and more efficient.
Languages Supported: Java, .Net, Php.Browsers Supported: IE、FireFox、Opera、Safari、Chrome.
Downloads: Java .Net PHP
Developer Guide:English Chinese Japanese
Latest version: 1.0
Latest updated: 2010-10-10AJAXRPC Quick StartFirst,we have to define a class and a static method: public class Test {
public static String sayHello(String name){
return "hello, " + name;
}
}Note: The static methord must be a public method.
Then we can call the method on the server by the AJAXRPC client program.
Note:When we call the RPC methods,if there is no callback function, then the call is synchronous;if there is one, then the call is asynchronous.Read more: AJAXPRC
An example of Strategy Design pattern for beginners
Posted by
jasper22
at
13:51
|
IntroductionSometime we need to carry out several computation / algorithms depending on certain conditions. We go ahead in implementing those generally by applying either switch or ternary operator or if else. Though initially somehow we manage to write those program but if the program demands too complex then it is difficult to frame such as well as to maintain. Moreover, writing all the logic at a single place is not at all advisable as it yields into tight coupling.BackgroundIn many situations we come across to write computational logic/ algorithms which we generally accomplish by using if else / switch or ternary operator. It becomes difficult at time to write such a program and later on adds a lot of cost while maintenance. RescuerStrategy design pattern. It comes under the category of Behavioral PatternsHowa)It decouples the client and the algorithm/ computation logic in separate classesb)Helps to switch algorithms at any time c)Easily allow to plug in a new algorithm.Pattern ComponentsThe strategy pattern comprises of the following componentsa)Strategy Interface –Interface common to all concrete strategies. b)Concrete Strategies / Different algorithm classes-Various concrete classes that implement the strategy interface for the sake of algorithm implementation specific to itself.Read more: Codeproject
Output Caching in asp.net
Posted by
jasper22
at
11:24
|
Recently one of my friend ask about output cache so I decided to put a post about how output cache works and what is the advantages and disadvantage of using output cache. Output cache is a technique to cache generated response from the asp.net pages or controls. Output Caching increases the performance drastically by reducing server round trips. We can use @OutputCache directive to controls output caching for a page or controls. The @OutputCache includes following attributes.
Read more: DOTNETJAPS ALL ABOUT .NET
- Duration: This attribute will explain how long output cache will be there for a page or control. It can be set in seconds. If you set 60 then it will not going to generate response from server until 60 second It will generate response from the cache it self. Here is example of duration where it will set 60 second for page.
<%@ OutputCache Duration="60" %>
- VaryByParam: This attribute will determine cache entries based on get or post parameters. It will vary cache based on get or post parameters suppose you set product Id query string as VaryByParam it will create a different cache based on product Id. Following is a example how you can set the VaryByParam based on Product Id.
<%@ OutputCache Duration="Seconds" VaryByParam="ProductId"%>
Read more: DOTNETJAPS ALL ABOUT .NET
A first look at the Windows Web Services API
The article shows how to interop between a WCF service and a WWS client, and also how to rewrite the WCF service in WWS retaining compatibility with existing WCF clients.IntroductionThe Windows Web Services API is a native implementation of SOAP and can be used to interop transparently with existing WCF services and clients, in addition to offering the ability to completely achieve a client-server implementation in pure native code. I have been longing to play with it ever since I heard Nikola Dudar talk about it at the MVP Summit earlier this year. It’s natively included with Windows 7, but can also be installed and used from older OSes such as XP, Vista, 2003 and 2008. You can write pure native clients using WWS that can connect to an existing managed WCF service, and also write a WWS native service that can be consumed by a WCF client. It’s so compatible that you can replace either a WCF client or a WCF service with a WWS equivalent without the other party being aware of it. In this article, I'll talk about a simple WCF service and its WCF client, and then show how to use WWS to write a native client that can consume the WCF service. I'll then show how the WCF service itself can be replaced transparently with an equivalent WWS service, and how both the WCF and WWS clients can connect to this WWS service without any changes in code. Note : The examples were written on a 64 bit Windows 7 RC machine running VS 2010 beta 1.The example WCF serviceThe first thing to do is to create a very simple WCF service. For our example I'll use a string reversing service that exposes a single method that accepts a string and returns the reversed string. Read more: Codeproject
gSOAP 2.8.0
Posted by
jasper22
at
11:38
|
1 Introduction The gSOAP tools provide an automated SOAP and XML data binding for C and C++ based on compiler technologies. The tools simplify the development of SOAP/XML Web services and XML application in C and C++ using autocode generation and advanced mapping methods. Most toolkits for Web services adopt a WSDL/SOAP-centric view and offer APIs that require the use of class libraries for XML-specific data structures. This forces a user to adapt the application logic to these libraries because users have to write code to populate XML and extract data from XML using a vendor-specific API. This often leads to fragile solutions with little or no assurances for data consistency, type safety, and XML validation. By contrast, gSOAP provides a type-safe and transparent solution through the use of compiler technology that hides irrelevant WSDL-, SOAP-, and XML-specific details from the user, while automatically ensuring XML validity checking, memory management, and type-safe serialization. The gSOAP tools automatically map native and user-defined C and C++ data types to semantically equivalent XML data types and vice-versa. As a result, full SOAP interoperability is achieved with a simple API relieving the user from the burden of WSDL/SOAP/XML details, thus enabling him or her to concentrate on the application-essential logic.
The gSOAP tools support the integration of (legacy) C/C++ codes (and other programming languages when a C interface is available), embedded systems, and real-time software in SOAP/XML applications that share computational resources and information with other SOAP applications, possibly across different platforms, language environments, and disparate organizations located behind firewalls.
The gSOAP tools are also popular to implement XML data binding in C and C++. This means that application-native data structures can be encoded in XML automatically, without the need to write conversion code. The tools also produce XML schemas for the XML data binding, so external applications can consume the XML data based on the schemas. 1.1 Getting Started To start building Web services applications or automate XML data bindings with gSOAP, you need:
The gSOAP package from http://www.genivia.com/Products/downloads.html (select gSOAP toolkit standard edition from the list of software packages) A C or C++ compiler.You may want to install OpenSSL and the Zlib libraries to enable SSL (HTTPS) and compression. These libraries are available for most platforms and are often already installed.The gSOAP software is self-contained, so there is no need to download any third-party software (unless you want to use OpenSSL and the library is not already installed, or if you need to rebuild the soapcpp2 tool, see below).
The gSOAP packages available from SourceForge include pre-build tools in the gsoap/bin directory:
The wsdl2h WSDL/schema importer and data binding mapper tool.The soapcpp2 stub/skeleton compiler and code generator. Read more: gSOAP
The gSOAP tools support the integration of (legacy) C/C++ codes (and other programming languages when a C interface is available), embedded systems, and real-time software in SOAP/XML applications that share computational resources and information with other SOAP applications, possibly across different platforms, language environments, and disparate organizations located behind firewalls.
The gSOAP tools are also popular to implement XML data binding in C and C++. This means that application-native data structures can be encoded in XML automatically, without the need to write conversion code. The tools also produce XML schemas for the XML data binding, so external applications can consume the XML data based on the schemas. 1.1 Getting Started To start building Web services applications or automate XML data bindings with gSOAP, you need:
The gSOAP package from http://www.genivia.com/Products/downloads.html (select gSOAP toolkit standard edition from the list of software packages) A C or C++ compiler.You may want to install OpenSSL and the Zlib libraries to enable SSL (HTTPS) and compression. These libraries are available for most platforms and are often already installed.The gSOAP software is self-contained, so there is no need to download any third-party software (unless you want to use OpenSSL and the library is not already installed, or if you need to rebuild the soapcpp2 tool, see below).
The gSOAP packages available from SourceForge include pre-build tools in the gsoap/bin directory:
The wsdl2h WSDL/schema importer and data binding mapper tool.The soapcpp2 stub/skeleton compiler and code generator. Read more: gSOAP
Why Server-Side JavaScript?
Posted by
jasper22
at
10:13
|
Chris Nicola left this excellent comment on Justin Etheredge’s blog:Even with a competitive way to do SSJS [(server-side JavaScript)] on the Windows platform, I just have to ask... why would anyone? Server-side JavaScript means that the server portion of a web application is written in JavaScript. Personally, I believe that server-side JavaScript will be the next big advance in web development.If I were Microsoft I would be looking to hit a touchdown out of the ball park with server-side JavaScript, to win back the respect of the more advanced web development community. Here are some of the reasons why server-side JavaScript will win.Homogenous Programming ExperienceWith server-side JavaScript (SSJS) you can use the same language on the server, on the client and over the wire (JSON). JavaScript is even deeply integrated into a number of database platforms. This lowers the concept count for web development and reduces the need for context switching. JavaScript Runtime EnginesThere is a large and ever expanding list of quality, cross-platform JavaScript engines. Every browser contains a JS runtime and there is currently a gold rush on JS performance improvements. PerformanceIf you have ever seen IE6 I know you will have your doubts, but JavaScript is fast. Not fast relative to C, but fast relative to languages with comparable features, and it is getting faster. Interpreted LanguageYou are too old for training wheels, and programming is too old for a compilation step. Now that we know the benefits of agile, and TDD, and rapid feedback loops, an interpreted language is a big advantage. Read more: Liam McLennan
Subscribe to:
Comments (Atom)