QR:
8% of Android Apps Are Leaking Private Information
Neil Daswani, who is also the CTO of security firm Dasient, says that they have studied around 10,000 Android apps and have found that 800 of them are leaking private information of the user to an unauthorized server. Neil Daswani is scheduled to present the full findings at the Black Hat Conference in Las Vegas which starts on July 30th. The Dasient researchers also found out that 11 of the apps they have examined are sending unwanted SMS messages. Read more: Slashdot
QR:
QR:
The Top 15 Most Popular DYAC Texts Of All Time
Posted by
jasper22
at
16:22
|

We just blew the dust off of our Google Analytics traffic monitor and realized since we launched Damn You Autocorrect back in October, the site has gotten over 300 million page views! That’s crazy! So thanks to everyone for reading! And now, thanks to the analytics, here are the 15 most viewed autocorrect fails sent in to Damn You Autocorrect since the site launch. Can you can guess what the #1 most popular submission has been so far?Read more: Damn you, Auto Correct !
QR:
Google 'winding down' Labs, likely due to meddling older sister
Posted by
jasper22
at
16:13
|
Google Labs, that breeding ground for the wacky, sublime, and sometimes useful experiments that Mountain View's scooter-loving employees are so fond of, is getting ready to "wind down." The software giant announced today that the experimental forum for testing out potential features is being sidelined, in order for the company to focus on bigger picture ideas. Some of the more useful experimentation for properties like Calendar and Gmail will stick around, as will the Labs experiments that eventually made their way into the Android market. Google has promised to keep us all in the loop during the transition, so perhaps we can pick up a few secondhand test tubes for our own collections. Read more: Engadget
QR:
QR:
WebSocket: Bringing TCP to the browser
Posted by
jasper22
at
15:15
|
The WebSocket standard is almost finalized. However, WebSocket itself is offering “just” a (data) pipe. WebSocket is well suited to bring event- or data-driven applications to the browser. A valid example would a Web UI for a JMS or AMQP application. With help of the Kaazing Gateway this is possible! As said before, you are basically able to bring any TCP- or UDP-based application to the web. A simple TCP-based echo serverSince the WebSocket client API itself is not enough (to build a “real” application), we need some (existing) backend, or server. A very simple example would be to bring a (TCP) echo server to the browser, via WebSocket: var net = require('net');var server = net.createServer(function (socket) {
socket.write("Echo server\r\n");
socket.pipe(socket);
});server.listen(1337, "127.0.0.1"); The above code is a VERY simple “EchoServer” that runs on port “1337″. It is in Node.js. The code is borrowed from their website.Bring it to the WebTo be able to access this TCP server with a WebSocket application you need to add the following configuration to the Kaazing WebSocket Gateway: <service>
<accept>ws://localhost:8000/echo</accept>
<connect>tcp://localhost:1337/</connect>
<type>proxy</type>
<cross-site-constraint>
<allow-origin>*</allow-origin>
</cross-site-constraint>
</service>Read more: Matthias Wessendorf's Weblog
QR:
socket.write("Echo server\r\n");
socket.pipe(socket);
});server.listen(1337, "127.0.0.1"); The above code is a VERY simple “EchoServer” that runs on port “1337″. It is in Node.js. The code is borrowed from their website.Bring it to the WebTo be able to access this TCP server with a WebSocket application you need to add the following configuration to the Kaazing WebSocket Gateway: <service>
<accept>ws://localhost:8000/echo</accept>
<connect>tcp://localhost:1337/</connect>
<type>proxy</type>
<cross-site-constraint>
<allow-origin>*</allow-origin>
</cross-site-constraint>
</service>Read more: Matthias Wessendorf's Weblog
QR:
Free SDK from Microsoft: Facebook C# SDK
Posted by
jasper22
at
15:12
|
The Facebook SDK needed updating for sometime and it is freshly updated as of 7/11/2011. Download and get started creating cool Facebook apps!http://facebooksdk.codeplex.com/ If you have questions make sure to go to the http://stackoverflow.com and use the tag ‘facebook-c#-sdk’ for help.
Professors:Use this to demonstrate the use of the open source C# language in your class and in the real world! Read more: Systems, architecture and engineering solutions!
QR:
Professors:Use this to demonstrate the use of the open source C# language in your class and in the real world! Read more: Systems, architecture and engineering solutions!
QR:
Hosting WCF NetTcp services in Azure with a Silverlight client
Posted by
jasper22
at
15:09
|
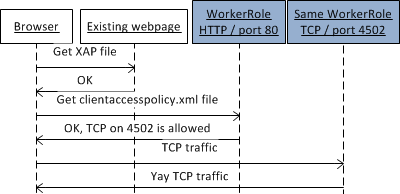
UPDATE: Folks from the Windows Azure team have posted an improved solution for how to host NetTcp services in Azure by using a WebRole instead of a WorkerRole, which simplifies the setup quite a bit. Silverlight 4 added support for WCF’s NetTcpBinding, which is a performant and scalable TCP-based binding. It is also a useful binding when used in Windows Azure because it is not affected by Azure’s random load-balancer when using multiple instances of the service and creates an effectively pinned duplex connection to the cloud. The only disadvantage of the NetTcp binding is that it Silverlight does not support TCP transport security, so all the traffic to the web service is unsecured and can be intercepted by malicious parties. That may or may not be acceptable for your application. I put together a sample on how to host a NetTcp service in Azure and consume it using a Silverlight client. The first thing to keep in mind here, is that Silverlight has some networking restrictions for security reasons. One of this restrictions is that if you want to speak TCP to a server, the server has to expose a policy file over port 80 explicitly listing the ports that it allows TCP for. Moreover, the ports have to be in the range 4502-4530. In other words if my Silverlight app wants to talk to net.tcp://contoso.cloudapp.net:4502, then I need to expose a policy file at http://contoso.cloudapp.net:80. Read more: Yavor Georgiev's Blog
QR:
Introducing MetroTwit Show: a visualizer for Twitter
Posted by
jasper22
at
15:07
|
Cross posted from MetroTwit.com. One of the many features we’ve been planning for MetroTwit since day one is the ability to visualize and enjoy tweets in a more casual and interactive format. Today, we’re making available MetroTwit Show, a project that’s been in the oven for a few weeks to make the reading experience for Twitter more vibrant. To make the experience accessible, MetroTwit Show is a Silverlight 4 out-of-browser application to take advantage of the widespread adoption of Silverlight on both Windows and Macs. Like MetroTwit, it is inspired by Microsoft’s Metro design language and prides itself on beautiful animations and elegant typography. Read more: I Started something
QR:
Now It's Official (I think) - Israeli Developers Can Register to Develop WP7 Apps
Posted by
jasper22
at
15:06
|
At last, Israeli developers can register in AppHub.
I wrote about Microsoft’s intentions after a Mix 11 session, I thought it was possible two months ago, but we’re finally in.A couple of minutes ago, after reading a blog post about maintenance being done on AppHub website, I decided to try to create a new account, and here is a screenshot of the registration page:
Read more: .NET client side - so simple to get complex
QR:
I wrote about Microsoft’s intentions after a Mix 11 session, I thought it was possible two months ago, but we’re finally in.A couple of minutes ago, after reading a blog post about maintenance being done on AppHub website, I decided to try to create a new account, and here is a screenshot of the registration page:

QR:
How To Use a .NET 4 Based DLL From .NET 2 Based Application?
Posted by
jasper22
at
15:05
|
IntroductionThe official answer is you can’t. Even with the In-Process Side by Side execution (SxS) feature, introduced in .NET 4.The SxS feature was intended to be used when COM is involved. For example, if you got an application that loads plugins, like outlook, and it loads 2 COM plugins, one is using .NET 4 and the other is using .NET 2.0 then it will load two versions of the CLR into the process using the new SxS feature. What if I simply have a .NET 2 application or DLL that needs to access a .NET 4 DLL?Personally I’ve encountered two scenarios when I had to solve this problem: I had a 3rd-party control that would load only in a .NET 3.5 application, but I had to use it in a .NET 4 application.
I wanted to write a plug-in for Windows Live Writer, which must use .NET 2.0, but I needed to use in my plug-in a .NET 4 DLL. So, what can we do if no COM is involved?Well, simply add COM to the mixture.. The idea is that you can expose the required classes from your DLL (which uses .NET Framework X) as COM classes (using COM Interop), and then use those classes from your other DLL (which uses .NET Framework Y). Since you are crossing a COM interface, in-process SxS will kick in and work its magic. Steps to work around the problem
Create a .NET 4 DLLSuppose we have a .NET 4 DLL which does some .NET 4 functionality. In the attached example our .NET 4 class prints the CLR version, which should be 4. This DLL is compiled with .NET Framework 4. using System;namespace Net4Assembly
{
public class MyClass
{
public void DoNet4Action()
{
Console.WriteLine("CLR version from DLL: {0}", Environment.Version);
}
}
}Create a .NET 2 EXEHere we create a .NET 2 EXE which will eventually call the .NET 4 DLL, currently all it does is write it’s own CLR version.using System;namespace Net2Assembly
{
}
Create a .NET 4 to .NET 2 adapterHere we create a .NET 4 DLL that exposes the same functionality we need from our original .NET 4 DLL only it exposes it in a COM-friendly way. In this example, it only needs to delegate the call to the original implementation, but in more advanced scenarios it should translate the parameters to something more COM friendly. In addition to changing the parameters the classes also implement interfaces (as required by COM) and are marked with ComVisible and Guid attributes to allow access using COM. Here is our COM visible interface:using System;
using System.Runtime.InteropServices;namespace Net4ToNet2Adapter
{
Read more: .NET Zone
QR:
I wanted to write a plug-in for Windows Live Writer, which must use .NET 2.0, but I needed to use in my plug-in a .NET 4 DLL. So, what can we do if no COM is involved?Well, simply add COM to the mixture.. The idea is that you can expose the required classes from your DLL (which uses .NET Framework X) as COM classes (using COM Interop), and then use those classes from your other DLL (which uses .NET Framework Y). Since you are crossing a COM interface, in-process SxS will kick in and work its magic. Steps to work around the problem
Create a .NET 4 DLLSuppose we have a .NET 4 DLL which does some .NET 4 functionality. In the attached example our .NET 4 class prints the CLR version, which should be 4. This DLL is compiled with .NET Framework 4. using System;namespace Net4Assembly
{
public class MyClass
{
public void DoNet4Action()
{
Console.WriteLine("CLR version from DLL: {0}", Environment.Version);
}
}
}Create a .NET 2 EXEHere we create a .NET 2 EXE which will eventually call the .NET 4 DLL, currently all it does is write it’s own CLR version.using System;namespace Net2Assembly
{
class Program
{
{
static void Main(string[] args)
{
{
Console.WriteLine("CLR version from EXE: {0}", Environment.Version);
}
}Create a .NET 4 to .NET 2 adapterHere we create a .NET 4 DLL that exposes the same functionality we need from our original .NET 4 DLL only it exposes it in a COM-friendly way. In this example, it only needs to delegate the call to the original implementation, but in more advanced scenarios it should translate the parameters to something more COM friendly. In addition to changing the parameters the classes also implement interfaces (as required by COM) and are marked with ComVisible and Guid attributes to allow access using COM. Here is our COM visible interface:using System;
using System.Runtime.InteropServices;namespace Net4ToNet2Adapter
{
[ComVisible(true)]
[Guid("E36BBF07-591E-4959-97AE-D439CBA392FB")]
public interface IMyClassAdapter
{
[Guid("E36BBF07-591E-4959-97AE-D439CBA392FB")]
public interface IMyClassAdapter
{
void DoNet4Action();
}
}And our COM visible class, which delegates its calls to the original class. Read more: .NET Zone
QR:
Strings, immutability and persistence
Posted by
jasper22
at
15:03
|
Todays post is based on a question from StackOverflow; I liked it so much I figured hey, let's just blog it today.When you look at a string in C#, it looks to you like a collection of characters, end of story. But of course, behind the scenes there is a data structure in memory somewhere to implement that collection of characters. In the .NET CLR, strings are laid out in memory pretty much the same way that BSTRs were implemented in OLE Automation: as a word-aligned memory buffer consisting of a four-byte integer giving the length of the string, followed by the characters of the string in two-byte chunks of UTF-16 data, followed by two zero bytes. (Recall that BSTR originally stood for "BASIC string", because the OLE Automation team was actually part of the Visual Basic team; this is the format that Visual Basic used.) Using this as the internal implementation of strings has a number of benefits. For example: it only requires one heap allocation per string. The length can be determined without counting characters. The string can contain embedded zero bytes, unlike formats that use zero bytes as end-of-string markers. If you disregard surrogate pairs then the nth individual character can be fetched in O(1) time, unlike in variable-width encodings like UTF-8. If the string is pinned in place and contains no zero characters then the address of the string data can be passed unmodified to unmanaged code that takes a WCHAR*. And so on. Strings are immutable in .NET, which also has many benefits. As I've discussed many times, immutable data types are easier to reason about, are threadsafe, and are more secure. (*)One of the benefits of the immutable data types I've talked about here previously is that they are not just immutable, they are also "persistent". By "persistent", I mean an immutable data type such that common operations on that type (like adding a new item to a queue, or removing an item from a tree) can re-use most or all of the memory of an existing data structure. Since it is all immutable, you can re-use its parts without worrying about them changing on you. Read more: Fabulous Adventures In Coding
QR:
QR:
Manual Stack Walking
Posted by
jasper22
at
15:02
|
Corrupted stacks are no fun at all – when you get a crash dump or a live exception in an application, pretty much the first thing you do is take a look at the call stack. When the stack itself is corrupted, your primary investigation tool is taken away. Still, it is sometimes possible to reconstruct the stack even in face of a corruption. I’ve been showing how in the .NET Debugging and C++ Debugging courses, but by popular demand will show one example here as well. You can follow along on your own with the dump file, symbol file, and sources from here.Here we go – open the dump file in WinDbg (32-bit) obtains the following output:User Mini Dump File: Only registers, stack and portions of memory are available
. . .
This dump file has an exception of interest stored in it.
The stored exception information can be accessed via .ecxr.
(1ed0.870): Access violation - code c0000005 (first/second chance not available)
eax=00000000 ebx=00000001 ecx=73536122 edx=00000000 esi=002af37c edi=0000004e
eip=00000000 esp=002af1a8 ebp=00000000 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
00000000 ?? ???
0:000> k
ChildEBP RetAddr
WARNING: Frame IP not in any known module. Following frames may be wrong.
002af1a4 00000000 0x0This is already bad news – the current instruction is at address 0x00000000, which means the instruction pointer (EIP) has been corrupted. You can also see that EBP has been corrupted – its value is 0x00000000 as well, which is why the k command has nothing to report. Read more: All Your Base Are Belong To Us
QR:
. . .
This dump file has an exception of interest stored in it.
The stored exception information can be accessed via .ecxr.
(1ed0.870): Access violation - code c0000005 (first/second chance not available)
eax=00000000 ebx=00000001 ecx=73536122 edx=00000000 esi=002af37c edi=0000004e
eip=00000000 esp=002af1a8 ebp=00000000 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
00000000 ?? ???
0:000> k
ChildEBP RetAddr
WARNING: Frame IP not in any known module. Following frames may be wrong.
002af1a4 00000000 0x0This is already bad news – the current instruction is at address 0x00000000, which means the instruction pointer (EIP) has been corrupted. You can also see that EBP has been corrupted – its value is 0x00000000 as well, which is why the k command has nothing to report. Read more: All Your Base Are Belong To Us
QR:
Tilt Ball Walkthrough
Posted by
jasper22
at
15:01
|
IntroductionThis tutorial guides you through creating a simple application for the Android phone. The application demonstrates using the accelerometer to make a ball move across the screen when the phone is tilted. The project is built using Eclipse and the Android SDK.
BackgroundThis tutorial assumes you already have the Eclipse environment up and running. If you are new to Eclipse and Android development, I recommend going through the temperature converter tutorial which can be found here.
Using the CodeYou can create the project by going through the steps listed below. If you prefer to load the entire project, download and unzip the project file, then open Eclipse and choose File->Import..->General->Existing Projects and choose the root folder of the TiltBall project. Let's begin:Start Eclipse (I'm using Eclipse Classic version 3.6.2).Choose File -> New -> Project -> Android -> Android Project.
Read more: Codeproject
QR:
BackgroundThis tutorial assumes you already have the Eclipse environment up and running. If you are new to Eclipse and Android development, I recommend going through the temperature converter tutorial which can be found here.
Using the CodeYou can create the project by going through the steps listed below. If you prefer to load the entire project, download and unzip the project file, then open Eclipse and choose File->Import..->General->Existing Projects and choose the root folder of the TiltBall project. Let's begin:Start Eclipse (I'm using Eclipse Classic version 3.6.2).Choose File -> New -> Project -> Android -> Android Project.

Read more: Codeproject
QR:
How do I find the original name of a hard link?
Posted by
jasper22
at
14:58
|
A customer asked, "Given a hardlink name, is it possible to get the original file name used to create it in the first place?"Recall that hard links create an alternate name for a file. Once that alternate name is created, there is no way to tell which is the original name and which is the new name. The new file does not have a "link back to the original"; they are both links to the underlying file content. This is an old topic, so I won't go into further detail. Though this question does illustrate that many people continue to misunderstand what hard links are. Anyway, once you figure out what the customer is actually asking, you can give a meaningful answer: "Given the path to a file, how can I get all the names by which the file can be accessed?" The answer is FindFirstFileNameW. Note that the names returned by the FindFirstFileNameW family of functions are relative to the volume mount point. To convert it to a full path, you need to append it to the mount point. Something like this: typedef void (*ENUMERATEDNAMEPROC)(__in PCWSTR);void ProcessOneName(
__in PCWSTR pszVolumeRoot,
__in PCWSTR pszLink,
__in ENUMERATEDNAMEPROC pfnCallback)
{
wchar_t szFile[MAX_PATH];
if (SUCCEEDED(StringCchCopy(szFile, ARRAYSIZE(szFile), pszVolumeRoot)) &&
PathAppend(szFile, pszLink)) {
pfnCallback(szFile);
}
}Read more: The old new thing
QR:
__in PCWSTR pszVolumeRoot,
__in PCWSTR pszLink,
__in ENUMERATEDNAMEPROC pfnCallback)
{
wchar_t szFile[MAX_PATH];
if (SUCCEEDED(StringCchCopy(szFile, ARRAYSIZE(szFile), pszVolumeRoot)) &&
PathAppend(szFile, pszLink)) {
pfnCallback(szFile);
}
}Read more: The old new thing
QR:
The strategy behind Mono has shifted: ten years of open source .NET
Posted by
jasper22
at
14:52
|
Yesterday, SUSE and Xamarin announced, in effect, the transfer of all things Mono to Xamarin. The agreement grants Xamarin a broad, perpetual license to all intellectual property covering Mono, MonoTouch, Mono for Android and Mono Tools for Visual Studio. Xamarin will also provide technical support to SUSE customers using Mono-based products, and assume stewardship of the Mono open source community project. Xamarin is a startup formed by Mono founder Miguel de Icaza following the acquisition of Novell and SUSE by Attachmate, which ceased Mono development.Attachmate acquired Novell in November 2010. Mono has been plucked from the abyss with impressive speed. That said, the strategy behind Mono has shifted. Mono exists because de Icaza liked what Microsoft announced back in 2000 when it introduced C# and the .NET Framework. Microsoft made a show of standardizing the .NET CLI (Common Language Infrastructure), which made PR sense at the time since there was controversy over Sun’s ownership of Java, though nobody really believed that Microsoft knew how to steward an open source development platform or indeed believed that it was really serious about it. History largely justifies that scepticism; but de Icaza called Microsoft’s bluff and forged ahead with Mono, implementing not only the CLI and C# but most of the .NET Framework as well. The goal of Mono, as I recall, was to bring the benefits of C# and .NET to Linux developers, and to enable developers to move applications freely between Windows and Linux. Apple OS X was also on the radar, though it took longer to become much use. Recalling Mono’s early days, de Icaza said: Mono to me is a means to an end: a technology to help Linux succeed on the desktop.
Read more: Tim Anderson’s ITWriting
QR:
Read more: Tim Anderson’s ITWriting
QR:
Upload Large File of More Than 5 MB From Silverlight to Server Location Using WCF
Posted by
jasper22
at
14:50
|
This article is based on the article File Upload from Silverlight using WCF. So please read it before proceeding with this article.A while back I wrote an article on uploading a File from Silverlight to a server location using WCF. I found my own article quiet useful. However, when I reread and implemented the code, I mentioned in the article, I found a few discrepancies: Code was unable to upload file with sizes in MB
There was a bug in binding configuration.
In this article, I am going to rectify the above two bugs.First modify basicHttpBinding as below: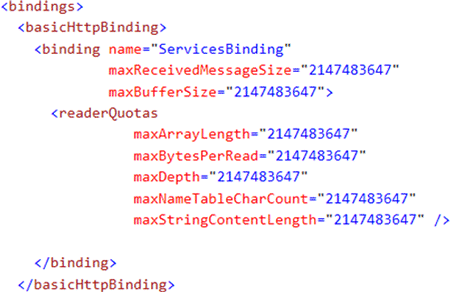
Configure Endpoint as below: 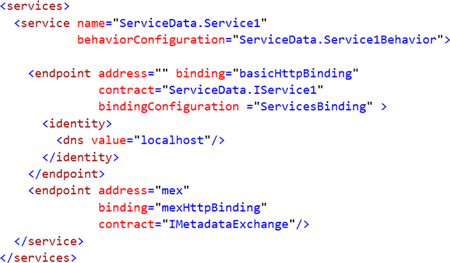
So far everything is fine and if you run the code, you will be able to upload a file of a maximum size of 3MB. I tested it and I was able to upload a document file of 2.75 MB in size. Now the question becomes, what if we want to upload a file of about 10 MB in size?For that we need to reconfigure the things in the configuration file:
QR:
There was a bug in binding configuration.
In this article, I am going to rectify the above two bugs.First modify basicHttpBinding as below:


So far everything is fine and if you run the code, you will be able to upload a file of a maximum size of 3MB. I tested it and I was able to upload a document file of 2.75 MB in size. Now the question becomes, what if we want to upload a file of about 10 MB in size?For that we need to reconfigure the things in the configuration file:
- Configure service behavior maximum number of items to serialize or deserialize.
- Configure HTTP Request length limit.
QR:
Updated Archive of the Debug Ninja’s Twitter Debug Tips
Posted by
jasper22
at
12:44
|
Every Wednesday (usually) I post a debug tip to our twitter page at https://twitter.com/#!/ntdebugging. This blog is an archive of these tips to allow our readers to find this information easily. I will update this blog periodically with the new tips; follow us on twitter if you want to see the tips as I post them. The goal of these tips is to share debug commands, and forms of commands (parameters, flags, etc) that my colleagues and I find useful. I hope you can add these commands to your toolkit and they will help you debug more efficiently. Tips:!thread/!process [address] e - on x64 will not show you the meaningless Args to Child information..frame /c [FrameNumber] - sets context to specified stack frame. Provides more reliable information than .trap on x64. kn - Dumps call stack with frame numbers, easier than counting stacks for .frame..frame /r [FrameNumber] - same as .frame /c, but shows registers without changing context.Note: With .frame /c or /r you can only trust the nonvolatile registers. See http://msdn.microsoft.com/en-us/library/9z1stfyw(VS.80).aspx for vol/nonvol regs. k=rbp rip FrameCount - Dumps call stack starting at rbp/rip on x64. Useful when the stack is corrupt. #debug ^DN.process/.thread /p /r [address] - sets new process context, sets .cache forcedecodeuser, and reloads user symbols. #debug ^DebugNinja !process [address] 17 - Sets the context for this command, avoids the need for .process to see user stacks. Try !process 0 17 #debug ^DN~~[ThreadID]s - Changes threads in user mode. Use Thread ID number from output such as !locks. Ex: ~~[1bd4]s #debug ^DN runas /netonly /u:<account> windbg.exe - Launch windbg with domain account. Use when dbg computer isn't in domain and symbol server is. ^DN!heap -p -a <address> - Shows information about the heap block containing <address>, even if you aren't using pageheap. #debug ^DN ub - Unassembles starting at a location prior to your address. Accepts l<number> to specify how many instructions to go back. ub . l20 ^DN!stacks 2 [FilterString] - Finds kernel mode call stacks that contain the FilterString in a symbol. #debug ^DN !thread [address] 17 (or 1e on x64) - Sets context for this command, avoids the need for .thread/.process for user stacks. #debug ^DN.hh [Text] - Opens the debugger help. [Text] is the topic to lookup in the index. Example: .hh !pte #debug ^DN ?? can dump structs using C++ style expressions. Ex: ??((nt!_KTHREAD*)(0xfffffa800ea43bb0))->ApcState #debug ^DNbp /t EThread - Sets a kernel mode breakpoint that only triggers when hit in the context of this thread. #debug ^DN (more....)
Read more: Ntdebugging Blog
QR:
Read more: Ntdebugging Blog
QR:
Google Plus WordPress Theme
Posted by
jasper22
at
12:29
|

Introducing the Google Plus WordPress theme called Reflex Plus developed by me (Naeem Noor). The theme is of course inspired by the new Social Media Site Google+. Reflex Plus is my first ever publicly released WordPress theme ever. It’s a simple minimalist 3 columns design, amazingly fast and jQuery Powered read more pagination.
Theme Features 3 Columns Minimal Design
Google+ Inspired
Valid Xhtml & CSS3
Custom Menus compatible
Post thumbnails support
jQuery Powered read more pagination
Fixed width
GPL Licensed
Read more: CSSReflex
QR:
MonoDevelop on Lion
Posted by
jasper22
at
12:28
|
We here at Xamarin are as excited as you are about the release of Lion. But unfortunately we're not quite ready to support you on Lion yet, and MonoDevelop doesn't work quite right. We're working around the clock to make MonoDevelop work perfectly on Lion, and we'll let you know as soon as it's ready. Read more: Personal blog of Miguel de Icaza
QR:
QR:
Defrag: SSD Questions, Tagging Files, Mirroring Drives, Hardware Hacks
Posted by
jasper22
at
12:27
|
Microsoft tech troubleshooter extraordinaire Gov Maharaj and I help walk you through troubleshooting solutions to your tech support problems. If you have a problem you want to send us, you can use the Problem Step Recorder in Windows 7 (see this for details on how) and send us the zip file to DefragShow@microsoft.com. We will also be checking comments for problems, but the email address will let us contact you if needed. 00:20 Eric Meijer and Charles interview Gov Maharaj.
04:12 All About SSDs - How do you know TRIM is enabled?
07:00 Is there any benefit to a defrag on an SSD?
08:42 What's the fastest way to connect a SSD
09:44 Can I tag text files like I do pictures in Windows 7?
12:53 Monitor no longer wakes from sleep.
14:42 Can I mirror my C: drive to another drive as a backup while Windows is running?
18:32 Will a "low level format" fix a thumbdrive that has bad sectors?
22:21 Deleted Thumbs.db and Desktop.ini, now having problems.
27:12 Windows crashes non-responding app too soon, is there a way to make it wait longer?
30:30 Hacking hardware - our pick of the week is Sugru.
Read more: Channel9
QR:
04:12 All About SSDs - How do you know TRIM is enabled?
07:00 Is there any benefit to a defrag on an SSD?
08:42 What's the fastest way to connect a SSD
09:44 Can I tag text files like I do pictures in Windows 7?
12:53 Monitor no longer wakes from sleep.
14:42 Can I mirror my C: drive to another drive as a backup while Windows is running?
18:32 Will a "low level format" fix a thumbdrive that has bad sectors?
22:21 Deleted Thumbs.db and Desktop.ini, now having problems.
27:12 Windows crashes non-responding app too soon, is there a way to make it wait longer?
30:30 Hacking hardware - our pick of the week is Sugru.
Read more: Channel9
QR:
10 dirty little secrets you should know about working in IT
Posted by
jasper22
at
12:26
|
10.) The pay in IT is good compared to many other professions, but since they pay you well, they often think they own youAlthough the pay for IT professionals is not as great as it was before the dot-com flameout and the IT backlash in 2001-2002, IT workers still make very good money compared to many other professions (at least the ones that require only an associate’s or bachelor’s degree). And there is every reason to believe that IT pros will continue to be in demand in the coming decades, as technology continues to play a growing role in business and society. However, because IT professionals can be so expensive, some companies treat IT pros like they own them. If you have to answer a tech call at 9:00 PM because someone is working late, you hear, “That’s just part of the job.” If you need to work six hours on a Saturday to deploy a software update to avoid downtime during business hours, you get, “There’s no comp time for that since you’re on salary. That’s why we pay you the big bucks!” 9.) It will be your fault when users make silly errors
8.) You will go from goat to hero and back again multiple times within any given day
7.) Certifications won’t always help you become a better technologist, but they can help you land a better job or a pay raise
Read more: TechRepublic
QR:
8.) You will go from goat to hero and back again multiple times within any given day
7.) Certifications won’t always help you become a better technologist, but they can help you land a better job or a pay raise
Read more: TechRepublic
QR:
T-SQL Tuesday #20 – T-SQL Best Practices
Posted by
jasper22
at
12:21
|
Here we go again! It’s T-SQL Tuesday #20 – a monthly blog party, this time hosted by Amit Banerjee. (Thanks Amit!) This month, we’re talking about “T-SQL Best Practices”.I used to write a lot more T-SQL than I do now. I had lots of rules for how T-SQL was written in my shop. But rather than sharing that extensive document, today I want to share with you my top three pieces of T-SQL advice. KISS (Keep It Simple, Developer)There are a lot of ways to solve problems in T-SQL. Once you get beyond a simple SELECT or UPDATE, you can really start playing. Derived tables, Common Table Expressions, CASE statements, aggregation, cursors, window functions, functions, pivoting…the things you can play with are endless. One of the beautiful things about T-SQL is that there is almost always more than one way to solve a problem. Remember, though, to keep it simple. Someday, someone else will need to read that code, and interpret it, and possibly (gasp) edit it. It could even be you.Table AliasesNo, you don’t need to ask people in the office to start calling you by your Twitter handle (no matter how funny that would be). SQL Server includes a “correlation name” or “range variable” to make FROM statements more easily readable. It’s also known as a “table alias”. A table alias is easy to implement, and saves trouble in the long run. How? Let’s look at this simple query: SELECT Customer.CustomerID, SalesOrderID, OrderDate, TotalValue
FROM Customer
INNER JOIN SalesOrder ON SalesOrder.CustomerID = Customer.CustomerID It’s a pain to reference a field with the full table name. And while this query is readable, what table does “OrderDate” reside in? Can you easily tell?Try this version instead: SELECT CUST.CustomerID, SO.SalesOrderID, SO.OrderDate, SO.TotalValue
FROM Customer CUST
INNER JOIN SalesOrder SO ON SO.CustomerID = CUST.CustomerID
Read more: Less than dot
QR:
FROM Customer
INNER JOIN SalesOrder ON SalesOrder.CustomerID = Customer.CustomerID It’s a pain to reference a field with the full table name. And while this query is readable, what table does “OrderDate” reside in? Can you easily tell?Try this version instead: SELECT CUST.CustomerID, SO.SalesOrderID, SO.OrderDate, SO.TotalValue
FROM Customer CUST
INNER JOIN SalesOrder SO ON SO.CustomerID = CUST.CustomerID
Read more: Less than dot
QR:
VirtualBox 4.1 has been released! PPA Ubuntu
Posted by
jasper22
at
12:19
|

Oracle today released VirtualBox 4.1, a new major release. Introducing VM clones, this mean the ability to clone virtual machines via the GUI and VBoxManage.virtualbox the New Advanced wizard for creating new virtual disks and virtual disk copy also for 64-bit memory limit is up to 1 TB. For guest Additions, status of modules and features can now be queried separately by the frontends, Experimental support for PCI passthrough for Linux hosts Check the changelog for a complete info about this release.Read more: Unixmen
QR:
Make money with In-App Payments for the Web
Cross-posted from the Google Commerce Blog.At the Google I/O conference back in May, Vikas Gupta introduced a preview of the Google In-App Payments API during the Chrome keynote speech. Google In-App Payments purchases were demonstrated as a simple click right within a web app, so buyers could enjoy a developer’s content, without interruption. Today, we’re making Google In-App Payments available for all web application developers to integrate with their web apps wherever they’re hosted, including the Chrome Web Store. Integration is simple with just a few lines of code. And pricing is set at just 5-percent. Read more: Google code
QR:
QR:
It's All About the SynchronizationContext
Posted by
jasper22
at
11:12
|
Multithreaded programming can be quite difficult, and there’s a tremendous body of concepts and tools to learn when one embarks on this task. To help out, the Microsoft .NET Framework provides the SynchronizationContext class. Unfortunately, many developers aren’t even aware of this useful tool. Regardless of the platform—whether it’s ASP.NET, Windows Forms, Windows Presentation Foundation (WPF), Silverlight or others—all .NET programs include the concept of SynchronizationContext, and all multithreading programmers can benefit from understanding and applying it.
The Need for SynchronizationContextMultithreaded programs existed well before the advent of the .NET Framework. These programs often had the need for one thread to pass a unit of work to another thread. Windows programs were centered on message loops, so many programmers used this built-in queue to pass units of work around. Each multithreaded program that wanted to use the Windows message queue in this fashion had to define its own custom Windows message and convention for handling it. When the .NET Framework was first released, this common pattern was standardized. At that time, the only GUI application type that .NET supported was Windows Forms. However, the framework designers anticipated other models, and they developed a generic solution. ISynchronizeInvoke was born. The idea behind ISynchronizeInvoke is that a “source” thread can queue a delegate to a “target” thread, optionally waiting for that delegate to complete. ISynchronizeInvoke also provided a property to determine whether the current code was already running on the target thread; in this case, queuing up the delegate would be unnecessary. Windows Forms provided the only implementation of ISynchronizeInvoke, and a pattern was developed for designing asynchronous components, so everyone was happy. Version 2.0 of the .NET Framework contained many sweeping changes. One of the major improvements was introducing asynchronous pages to the ASP.NET architecture. Prior to the .NET Framework 2.0, every ASP.NET request needed a thread until the request was completed. This was an inefficient use of threads, because creating a Web page often depends on database queries and calls to Web services, and the thread handling that request would have to wait until each of those operations finished. With asynchronous pages, the thread handling the request could begin each of the operations and then return back to the ASP.NET thread pool; when the operations finished, another thread from the ASP.NET thread pool would complete the request. Read more: MSDN Magazine
QR:
The Need for SynchronizationContextMultithreaded programs existed well before the advent of the .NET Framework. These programs often had the need for one thread to pass a unit of work to another thread. Windows programs were centered on message loops, so many programmers used this built-in queue to pass units of work around. Each multithreaded program that wanted to use the Windows message queue in this fashion had to define its own custom Windows message and convention for handling it. When the .NET Framework was first released, this common pattern was standardized. At that time, the only GUI application type that .NET supported was Windows Forms. However, the framework designers anticipated other models, and they developed a generic solution. ISynchronizeInvoke was born. The idea behind ISynchronizeInvoke is that a “source” thread can queue a delegate to a “target” thread, optionally waiting for that delegate to complete. ISynchronizeInvoke also provided a property to determine whether the current code was already running on the target thread; in this case, queuing up the delegate would be unnecessary. Windows Forms provided the only implementation of ISynchronizeInvoke, and a pattern was developed for designing asynchronous components, so everyone was happy. Version 2.0 of the .NET Framework contained many sweeping changes. One of the major improvements was introducing asynchronous pages to the ASP.NET architecture. Prior to the .NET Framework 2.0, every ASP.NET request needed a thread until the request was completed. This was an inefficient use of threads, because creating a Web page often depends on database queries and calls to Web services, and the thread handling that request would have to wait until each of those operations finished. With asynchronous pages, the thread handling the request could begin each of the operations and then return back to the ASP.NET thread pool; when the operations finished, another thread from the ASP.NET thread pool would complete the request. Read more: MSDN Magazine
QR:
WCF Extensibility – Custom Serialization in Silverlight
Posted by
jasper22
at
11:11
|
This post is part of a series about WCF extensibility points. For a list of all previous posts and planned future ones, go to the index page.This post takes a detour from the normal flow of the series, since I was working on a scenario last week which I think will add value to the series as a whole. On the post about contract behaviors, I showed an example of how to hook up a custom serializer to the WCF pipeline. That sample used the DataContractSerializerOperationBehavior extensibility in which you could inherit from that class, override the CreateSerializer methods and replace that behavior on the operation with your own custom class. That’s fairly simple and has been done extensively in WCF. However, this doesn’t work in Silverlight. This post isn’t about one specific extensibility point, but about a scenario which can be covered by the extensibility points already covered in this series, in a different platform. The WCF portions of Silverlight is a subset (*) of the full framework. Due to many restrictions in the Silverlight platform, such as the sandbox, support for multiple OS, and primarily size (the runtime download time could not be too large, otherwise people might give up installing it), many features in the full WCF didn’t make it into SL. Other features actually went in, but in order to reduce the (large) number of extensibility points, they were made internal. The class DataContractSerializerOperationBehavior is one of those which didn’t make the cut, and for most of the cases it hasn’t been a problem – SL has been released for about 3 years now and only recently I’ve seen a couple of requests for being able to replace the serializer in SL. (*) It’s not really a proper subset, as there are some features in SL which aren’t available in the full framework, such as the classes in the System.Json namespace; they may eventually make it to the framework, but at this time they’re only available in the WCF Codeplex site.
Real World Scenario: expanding custom serialization to SilverlightThe first thing to be able to replace the DataContractSerializerOperationBehavior in SL is to actually find out what it does at the client side. I’ve been using Reflector (while it’s free) and it shows that the ApplyClientBehavior method does two things: determines whether the operation input / output should be serialized (if the operation uses untyped messages, then no serialization is necessary, and it then creates the client formatter which will be used to serialize / deserialize the request / reply. So like in the desktop case, our new operation behavior will do something similar. Also, like in the DataContractSerializerOperationBehavior, I’ve made the method CreateSerializer virtual, so that it can be extended to easily replace the serializer. Read more: Carlos' blog
QR:
Real World Scenario: expanding custom serialization to SilverlightThe first thing to be able to replace the DataContractSerializerOperationBehavior in SL is to actually find out what it does at the client side. I’ve been using Reflector (while it’s free) and it shows that the ApplyClientBehavior method does two things: determines whether the operation input / output should be serialized (if the operation uses untyped messages, then no serialization is necessary, and it then creates the client formatter which will be used to serialize / deserialize the request / reply. So like in the desktop case, our new operation behavior will do something similar. Also, like in the DataContractSerializerOperationBehavior, I’ve made the method CreateSerializer virtual, so that it can be extended to easily replace the serializer. Read more: Carlos' blog
QR:
Log Parser 2.2
OverviewLog parser is a powerful, versatile tool that provides universal query access to text-based data such as log files, XML files and CSV files, as well as key data sources on the Windows® operating system such as the Event Log, the Registry, the file system, and Active Directory®. You tell Log Parser what information you need and how you want it processed. The results of your query can be custom-formatted in text based output, or they can be persisted to more specialty targets like SQL, SYSLOG, or a chart. Most software is designed to accomplish a limited number of specific tasks. Log Parser is different... the number of ways it can be used is limited only by the needs and imagination of the user. The world is your database with Log Parser. Read more: MS Download
Read more: Slashdot (C# example)
QR:
Read more: Slashdot (C# example)
QR:
Remove PPAs Which Cause 404 Not Found Errors In Ubuntu With Fix404 PPA
Posted by
jasper22
at
09:57
|

Entering the wrong PPA (Private Package Repository) in the Ubuntu Terminal results in a 404 Not Found error. This error can result in the slow down of the apt-get update and seems pretty annoying. Fix404 PPA is a script which disables the PPAs that cause 404 Not Found errors. It provides the convenience of not having to disable faulty PPAs from Software Sources. Fix 404 PPAs checks for 404 messages for PPAs and alerts you to disable them. Fix 404 can be installed in Ubuntu 11.04 Natty by entering the following commands in the Terminal:sudo apt-add-repository ppa:lkjoel/fix404
sudo apt-get update
sudo apt-get install fix404If you are using a pre-Natty version, a Deb package can be downloaded from the Launchpad link given at the end of this post. If you would like to try out a software which can help you easily search and add application PPAs from Launchpad, then check out YPPA Manager. Read more: Addictive tips
QR:
How To Jailbreak and Upgrade Old Android Phones
Posted by
jasper22
at
09:42
|
InfoWorld's Serdar Yegulalp provides an in-depth tutorial on how he rooted and upgraded his Motorola Cliq XT, one of many Android phones made infamous for not receiving further Android updates beyond 1.5. 'It turned out to be quite an odyssey, with twists and turns I describe here in order to help those who wish to embark on a similar journey,' Yegulalp writes. 'Was it worth the trouble? Yes, in the sense that learning how to jailbreak your own phone is a valuable skill, and I got much more functionality out of the Cliq, when I was expecting to simply junk it. Read more: Slashdot
QR:
QR:
What Are The 20 Most Expensive Keyword Categories In Google AdWords?
Posted by
jasper22
at
09:40
|
WordStream, a venture capital-backed provider of hosted software that automates most of the manual work involved with creating and optimizing both paid and natural search engine marketing campaigns, has done some research to discover which keyword categories fetch the highest costs per click (CPC) in Google’s AdWords solution. And of course, they made an infographic based on the results of their research (embedded below).WordStream compiled data from its own, vast keyword database and the Google Keyword Tool to determine the top 10,000 most expensive English-language keywords over a 90-day period. Subsequently, the list was organized into categories by theme. The largest keyword categories were then determined by weighting the number of keywords within each category, as well as the estimated monthly search volume and average cost per click for each keyword. For the record, Google AdWords is an auction-based marketplace where advertisers bid on keywords to compete for top ad placement, with a minimum bid of 5 cents per keyword (update: actually, there’s no longer a minimum bid for CPC campaigns). The top twenty keyword categories that demanded the highest costs per click are:1. Insurance (example keyword: “auto insurance price quotes”)
2. Loans (example keyword: “consolidate graduate student loans”)
3. Mortgage (example keyword: “refinanced second mortgages”)
4. Attorney (example keyword: “personal injury attorney”)
5. Credit (example keyword: “home equity line of credit”)
6. Lawyer
7. Donate
8. Degree
9. Hosting
10. Claim
11. Conference Call
12. Trading
13. Software
14. Recovery
15. Transfer
16. Gas/Electricity
17. Classes
18. Rehab
19. Treatment
20. Cord Blood
Read more: TechCrunch
QR:
2. Loans (example keyword: “consolidate graduate student loans”)
3. Mortgage (example keyword: “refinanced second mortgages”)
4. Attorney (example keyword: “personal injury attorney”)
5. Credit (example keyword: “home equity line of credit”)
6. Lawyer
7. Donate
8. Degree
9. Hosting
10. Claim
11. Conference Call
12. Trading
13. Software
14. Recovery
15. Transfer
16. Gas/Electricity
17. Classes
18. Rehab
19. Treatment
20. Cord Blood
Read more: TechCrunch
QR:
Test Driving GNU Hurd, With Benchmarks Against Linux
Posted by
jasper22
at
09:29
|
After last week's news that GNU Hurd is coming, Phoronix set out to install Debian GNU Hurd and to provide GNU Hurd vs. Linux benchmarks. Linux was mostly faster than The Hurd while also having much better hardware support, multi-core SMP support, and other modern functionality. Read more: Slashdot
QR:
QR:
LulzSec Hacks Murdoch-Owned ‘The Sun,’ Redirects Homepage To @LulzSec Twitter Account
Posted by
jasper22
at
09:28
|

QR:
Build your own operating system
Posted by
jasper22
at
09:23
|
Ten years ago (around the year 2001) I wrote a simple x86 protected-mode OS just to find out how operating systems work. That was really great fun and I learned very much about OS concepts and paradigms (and also a lot of stuff about computer hardware, programming, software architecture, data structures etc.). Ever since the gathered experience and knowledge by building my own operating system has been extremely valuable. I began by reading Andrew Tanenbaum's book "Operating Systems: Design and Implementation" during which I studied a lot of Minix source code. Later I also read his other books about modern operating systems and structured computer organization.
To get started with this challenging task, one needs some profound knowledge of the memory-management-unit (MMU) of the x86 CPU and its protected mode. To me, the best known tutorial on the web is the "Protected Mode Tutorial" by Jens Hohmuth of the Westsächsische Hochschule Zwickau. Sadly, this tutorial is only available in german. If you do not speak german you may try to translate it with Google Translate. The best parts of the tutorial are its great assembly language examples for Borland's TASM and Microsoft's MASM. I typed in all the examples by hand and played with them until I understood every single line of code :-). What is also helpful to understand the MMU and protected-mode of the x86 CPU is Intels Architecture Software Developer’s Manual and Hans-Peter Messmer's book The Indispensable PC Hardware Book. Read more: Daniel's Blog
QR:
To get started with this challenging task, one needs some profound knowledge of the memory-management-unit (MMU) of the x86 CPU and its protected mode. To me, the best known tutorial on the web is the "Protected Mode Tutorial" by Jens Hohmuth of the Westsächsische Hochschule Zwickau. Sadly, this tutorial is only available in german. If you do not speak german you may try to translate it with Google Translate. The best parts of the tutorial are its great assembly language examples for Borland's TASM and Microsoft's MASM. I typed in all the examples by hand and played with them until I understood every single line of code :-). What is also helpful to understand the MMU and protected-mode of the x86 CPU is Intels Architecture Software Developer’s Manual and Hans-Peter Messmer's book The Indispensable PC Hardware Book. Read more: Daniel's Blog
QR:
COM ByteArray and Dynamic type issues in .NET
Posted by
jasper22
at
09:16
|
In .NET 4.0 the dynamic type has made it A LOT easier to work with COM interop components. I'm still working quite a bit with customers that need to work with FoxPro COM objects in .NET and there are some extra fun issues to deal with when working with COM SafeArrays (byte arrays) returned from a COM client. Currently I'm working with a customer who needs to work with Web Services that publish and capture a lot of binary data. A couple of interesting things came up when returning byte arrays over COM to .NET via a dynamic type. I've written about COM binary arrays before in a previous post. The issue is that when you make a COM call to retrieve a binary result from a COM object the result gets returned as byte[*] type rather than byte[]. To demonstrate imagine you have a simple COM client that returns a binary result as a SafeArray of bytes. The following dumbed down example is a FoxPro method in COM published component where an object is returned that contains a ByteResult property that holds binary data: ************************************************************************
* SendBinaryFile
****************************************
FUNCTION SendBinaryFile(lcPath)
LOCAL lvBinary, lcBinary, loResult as ServiceResult TRY
*** Grab the file from disk into a string
lcBinary = FILETOSTR(lcPath) *** Turn the string to binary - over COM this turns into a SAFEARRAY
lvBinary = CREATEBINARY(lcBinary) && OR CAST(lcBinary as Q) *** Return value is standard Service Response object
loResult = CREATEOBJECT("ServiceResult") *** Attach the binary response to the ServiceResult
loResult.ByteResult = lvBinary
CATCH TO loException
loResult = this.ErrorToServiceResult(loException,20)
ENDTRYRETURN loResult
ENDFUNCThe interesting part in relation to this post is the binary result which in this case is the content of a file. Internally FoxPro treats binary values as strings since it's stuck with ANSI codepages, so string can easily contain binary data. However FoxPro cannot return that string as a binary value over COM. In order to return a binary value the value needs to be explicitly converted using CREATEBINARY() or CAST(val as Q) which turns it into a SAFEARRAY when passed back over COM. This binary value is then assigned to a ServiceResult object that returns actual result value(s) back to the .NET Web Service which in turn publishes these values through the Service interface. Read more: Rick Strahl blog
QR:
* SendBinaryFile
****************************************
FUNCTION SendBinaryFile(lcPath)
LOCAL lvBinary, lcBinary, loResult as ServiceResult TRY
*** Grab the file from disk into a string
lcBinary = FILETOSTR(lcPath) *** Turn the string to binary - over COM this turns into a SAFEARRAY
lvBinary = CREATEBINARY(lcBinary) && OR CAST(lcBinary as Q) *** Return value is standard Service Response object
loResult = CREATEOBJECT("ServiceResult") *** Attach the binary response to the ServiceResult
loResult.ByteResult = lvBinary
CATCH TO loException
loResult = this.ErrorToServiceResult(loException,20)
ENDTRYRETURN loResult
ENDFUNCThe interesting part in relation to this post is the binary result which in this case is the content of a file. Internally FoxPro treats binary values as strings since it's stuck with ANSI codepages, so string can easily contain binary data. However FoxPro cannot return that string as a binary value over COM. In order to return a binary value the value needs to be explicitly converted using CREATEBINARY() or CAST(val as Q) which turns it into a SAFEARRAY when passed back over COM. This binary value is then assigned to a ServiceResult object that returns actual result value(s) back to the .NET Web Service which in turn publishes these values through the Service interface. Read more: Rick Strahl blog
QR:
Mapping the Memory Usage of .NET Applications: Part 2, VMMap and MemoryDisplay
Posted by
jasper22
at
09:15
|
How can you map the memory usage of your .NET application? We'll start with VMMap, a free Sysinternals tool that visualizes your process' virtual address space. Below is VMMap's output for an example process: 
The type statistics give you a detailed overview of how memory usage is distributed – there are 240MB of DLLs, 50MB of managed heaps (of which only 10MB are committed), etc. In the bottom details view you can see each individual address range on the heap, including its type, size, committed size, and other details (such as DLL names for the "Image" type and file names for the "Mapped File" type). Within the GC heap, VMMap features the ability to identify the various generations (and the Large Object Heap) within the GC segments:
Read more: All Your Base Are Belong To Us
QR:

The type statistics give you a detailed overview of how memory usage is distributed – there are 240MB of DLLs, 50MB of managed heaps (of which only 10MB are committed), etc. In the bottom details view you can see each individual address range on the heap, including its type, size, committed size, and other details (such as DLL names for the "Image" type and file names for the "Mapped File" type). Within the GC heap, VMMap features the ability to identify the various generations (and the Large Object Heap) within the GC segments:

QR:
Effective Website Designs with Dark Color Schemes
Posted by
jasper22
at
09:13
|
Not everyone can pull off a dark color scheme, especially for a website design. Going too dark results in a barely navigable site. You also run the risk of being too edgy, too depressing, or even too boring. The best websites with dark color schemes seem to include common elements and techniques for making the design work. High contrast, the perfect amount of textures, and knowing which fonts need to be light and which can be a middle hue all seem to be a part of the effective use of dark colors in websites. The following sites have done an excellent job of balancing the use of dark colors in their design. Take a peek to see what seems to work for each of the websites below, and maybe gather some ideas for your own darkly colored designs as well. Osvaldas.info
Read more: Design your way
QR:

QR:
Troubleshooting with the New Sysinternals Administrator’s Reference
Posted by
jasper22
at
09:11
|
Aaron Margosis and I are thrilled to announce that the long awaited, and some say long overdue, official guide to the Sysinternals tools is now available! I’ve always had the idea of writing a book on the tools in the back of my mind, but it wasn’t until a couple of years ago that Dave Solomon, my coauthor on Windows Internals, convinced me to pursue it. After a few false starts, I decided that a coauthor would help get the book done more quickly, and turned to Aaron, a good friend of mine who’s also a long-time user and expert on the tools at his day job in the Federal Division of Microsoft Consulting Services. It was a great choice and I’m proud to put the Sysinternals brand on the book. Whether you’re new to the tools or have been using them since Bryce Cogswell (my Sysinternals and Winternals Software cofounder, now retired) and I released NTFSDOS in 1996, you’re sure to take away new insights that will give you the edge when tackling tough problems and managing your Windows systems. The book covers all 70+ tools, with chapters dedicated to the major tools like Process Explorer, Process Monitor, and Autoruns. For each we provide a thorough tour of all of the tool’s features, how to use the tool, and include our favorite tips and techniques. There’s no better way to learn than by example, though. The last section of the book will be familiar to anyone that’s read this blog or watched my Case of the Unexplained conference sessions, because it presents 17 real-world cases that show how Windows power users and administrators like you solved otherwise impossible-to-solve problems by using the tools.
Read more: Mark's Blog
QR:
Read more: Mark's Blog
QR:
Subscribe to:
Comments (Atom)


