Virtual Disk Service
PurposeThe Virtual Disk Service (VDS) manages a wide range of storage configurations, from single-disk desktops to external storage arrays. The service exposes an application programming interface (API).
Where ApplicableApplication developers who use the interfaces described in this guide can query and configure a heterogeneous set of vendor-supplied and internally managed storage. VDS hides from applications the complexities associated with storage, making the service both vendor and technology neutral. Developer AudienceThe VDS programming guide is intended for application developers who are familiar with the storage capabilities of Microsoft Windows platforms and who are knowledgeable about COM development.
The guide is also intended for hardware subsystem manufacturers who develop and support VDS hardware provider programs.Run-Time RequirementsVDS is supported on Microsoft Windows Server 2003, Windows Vista, and later. For information about run-time requirements for a particular programming element, see the Requirements section of the documentation for that element. Running 32-bit VDS applications under WOW64 is supported, but 64-bit VDS providers must run as native applications on 64-bit Windows versions.Read more: MSDN
Where ApplicableApplication developers who use the interfaces described in this guide can query and configure a heterogeneous set of vendor-supplied and internally managed storage. VDS hides from applications the complexities associated with storage, making the service both vendor and technology neutral. Developer AudienceThe VDS programming guide is intended for application developers who are familiar with the storage capabilities of Microsoft Windows platforms and who are knowledgeable about COM development.
The guide is also intended for hardware subsystem manufacturers who develop and support VDS hardware provider programs.Run-Time RequirementsVDS is supported on Microsoft Windows Server 2003, Windows Vista, and later. For information about run-time requirements for a particular programming element, see the Requirements section of the documentation for that element. Running 32-bit VDS applications under WOW64 is supported, but 64-bit VDS providers must run as native applications on 64-bit Windows versions.Read more: MSDN
Caching of, in, and around your Silverlight application
Posted by
jasper22
at
17:29
|
This is the first in a 3-part series of articles about caching & Silverlight.Part 1: The client: XAP & Assembly Caching
Part 2: The Silverlight application: Isolated Storage
Part 3: The server: caching your result sets
You can download the source code here.A lot can be written about this subject, and because of that, quite a few misunderstandings about Silverlight and caching exist.Let’s start with a general definition of caching: this is what Wikipedia has to say about this technique: In computer science, a cache is a component that improves performance by transparently storing data such that future requests for that data can be served faster. ... (en.wikipedia.org/wiki/Caching) Well, that sure opens up a lot of possible places to cache, in and outside of your Silverlight application. Can you cache the complete Silverlight application? What’s this assembly caching you keep on reading about? How do you go about keeping your data on the client when navigating to different parts of you application, instead of refetching it all the time? Can you leverage the Isolated Storage for caching, and is it possible to persist data in between different application sessions? Is it possible to share cached items between different Silverlight applications? And what about the server-side: can I minimize database hits when launching queries from my Silverlight application? If you’ve ever asked yourself one (or more) of these questions, this article series is for you. As you might notice when seeing them in the same paragraph, these questions are about different ways of caching, and they all apply to different scenarios. In the first part of this series, I’d like to talk about the caching of your Silverlight application itself and Assembly Caching – almost no code is required for this.XAP Caching
Every Silverlight application consists of one or more XAP files. Smaller applications typically consist of one XAP, but larger applications might benefit from dividing your application into different application modules, compiling into different XAP-files which are loaded on demand. When a user first navigates to a page hosting a Silverlight application, the full XAP has to be downloaded to the client. As an XAP typically contains a bunch of referenced assemblies, your XAML files, compiled code and everything else you’ve included as embedded resources in your Silverlight project, these files have a tendency to get quite big. Therefore, being able to cache these files will reduce the time a user has to wait to access your application.
Read more: Silverlight Show
Part 2: The Silverlight application: Isolated Storage
Part 3: The server: caching your result sets
You can download the source code here.A lot can be written about this subject, and because of that, quite a few misunderstandings about Silverlight and caching exist.Let’s start with a general definition of caching: this is what Wikipedia has to say about this technique: In computer science, a cache is a component that improves performance by transparently storing data such that future requests for that data can be served faster. ... (en.wikipedia.org/wiki/Caching) Well, that sure opens up a lot of possible places to cache, in and outside of your Silverlight application. Can you cache the complete Silverlight application? What’s this assembly caching you keep on reading about? How do you go about keeping your data on the client when navigating to different parts of you application, instead of refetching it all the time? Can you leverage the Isolated Storage for caching, and is it possible to persist data in between different application sessions? Is it possible to share cached items between different Silverlight applications? And what about the server-side: can I minimize database hits when launching queries from my Silverlight application? If you’ve ever asked yourself one (or more) of these questions, this article series is for you. As you might notice when seeing them in the same paragraph, these questions are about different ways of caching, and they all apply to different scenarios. In the first part of this series, I’d like to talk about the caching of your Silverlight application itself and Assembly Caching – almost no code is required for this.XAP Caching
Every Silverlight application consists of one or more XAP files. Smaller applications typically consist of one XAP, but larger applications might benefit from dividing your application into different application modules, compiling into different XAP-files which are loaded on demand. When a user first navigates to a page hosting a Silverlight application, the full XAP has to be downloaded to the client. As an XAP typically contains a bunch of referenced assemblies, your XAML files, compiled code and everything else you’ve included as embedded resources in your Silverlight project, these files have a tendency to get quite big. Therefore, being able to cache these files will reduce the time a user has to wait to access your application.
Read more: Silverlight Show
Step-by-Step Reverse Engineering Malware: ZeroAccess / Max++ / Smiscer Crimeware Rootkit
Posted by
jasper22
at
17:27
|
Part 1: Introduction and De-Obfuscating and Reversing the User-Mode Agent Dropper
Part 2: Reverse Engineering the Kernel-Mode Device Driver Stealth Rootkit
Part 3: Reverse Engineering the Kernel-Mode Device Driver Process Injection Rootkit
Part 4: Tracing the Crimeware Origins by Reversing the Injected CodeSUMMARY
This four part article series is a complete step-by-step tutorial on how to reverse engineer the ZeroAccess Rootkit. ZeroAcess is also known as the Smiscer or Max++ rootkit. You can either read along to gain an in-depth understand the thought process behind reverse engineering modern malware of this sophistication. The author prefers that you download the various tools mentioned within and reverse the rookit yourself as you read the article. InfoSec Institute would classify ZeroAccess as a sophisticated, advanced rootkit. It has 4 main components that we will reverse in great detail in this series of articles. ZeroAccess is a compartmentalized crimeware rootkit that serves as a platform for installing various malicious programs onto victim computers. It also supports features to make itself and the installed malicious programs impossible for power-users to remove and very difficult security experts to forensically analyze. At the conclusion of the analysis, we will trace the criminal origins of the ZeroAccess rootkit. We will discover that the purpose of this rootkit is to set up a stealthy, undetectable and un-removable platform to deliver malicious software to victim computers. We will also see that ZeroAccess is being currently used to deliver FakeAntivirus crimeware applications that trick users into paying $70 to remove the “antivirus”. It could be used to deliver any malicious application, such as one that steals bank and credit card information in the future. Further analysis and network forensics supports that ZeroAccess is being hosted and originates from the Ecatel Network, which is controlled by the cybercrime syndicate RBN (Russian Business Network). Symantec reports that 250,000+ computers have been infected with this rootkit. If 100% of users pay the $70 removal fee, it would net a total of $17,500,000. As it is not likely that 100% of users will pay the fee, assuming that perhaps 30% will, resulting $5,250,000 in revenue for the RBN cybercrime syndicate. Read more: infosec
Part 2: Reverse Engineering the Kernel-Mode Device Driver Stealth Rootkit
Part 3: Reverse Engineering the Kernel-Mode Device Driver Process Injection Rootkit
Part 4: Tracing the Crimeware Origins by Reversing the Injected CodeSUMMARY
This four part article series is a complete step-by-step tutorial on how to reverse engineer the ZeroAccess Rootkit. ZeroAcess is also known as the Smiscer or Max++ rootkit. You can either read along to gain an in-depth understand the thought process behind reverse engineering modern malware of this sophistication. The author prefers that you download the various tools mentioned within and reverse the rookit yourself as you read the article. InfoSec Institute would classify ZeroAccess as a sophisticated, advanced rootkit. It has 4 main components that we will reverse in great detail in this series of articles. ZeroAccess is a compartmentalized crimeware rootkit that serves as a platform for installing various malicious programs onto victim computers. It also supports features to make itself and the installed malicious programs impossible for power-users to remove and very difficult security experts to forensically analyze. At the conclusion of the analysis, we will trace the criminal origins of the ZeroAccess rootkit. We will discover that the purpose of this rootkit is to set up a stealthy, undetectable and un-removable platform to deliver malicious software to victim computers. We will also see that ZeroAccess is being currently used to deliver FakeAntivirus crimeware applications that trick users into paying $70 to remove the “antivirus”. It could be used to deliver any malicious application, such as one that steals bank and credit card information in the future. Further analysis and network forensics supports that ZeroAccess is being hosted and originates from the Ecatel Network, which is controlled by the cybercrime syndicate RBN (Russian Business Network). Symantec reports that 250,000+ computers have been infected with this rootkit. If 100% of users pay the $70 removal fee, it would net a total of $17,500,000. As it is not likely that 100% of users will pay the fee, assuming that perhaps 30% will, resulting $5,250,000 in revenue for the RBN cybercrime syndicate. Read more: infosec
Obfuscating JavaScript with Closure Compiler Advanced Optimizations
Posted by
jasper22
at
17:26
|
While working on our upcoming game, Onslaught! Arena, we wanted to obfuscate the JavaScript code as much as possible. Using tools like YUICompressor and Google Closure Compiler (with Standard Optimizations) just weren’t enough. Luckily, Closure Complier has an “Advanced Optimizations” mode. This mode will really make your JavaScript gross and unreadable!
Here are some cases to watch out for along with some tips for those trying to make their JavaScript as unreadable as possible:Don’t access object properties as string literals
Using Advanced Optimizations has its pitfalls. Because of it’s super aggressive renaming, Closure Compiler will break your code if you access object properties using string literals. For example: var thing.stuff = {
foo: 10,
bar: 20
};// This will break after Advanced Optimization :(
var foo = thing["stuff"].foo;
Closure will rewrite thing.stuff as something like a.b and accessing a["stuff"] isn’t going to work. Don’t use string literals
Closure Compiler won’t obfuscate string literals for obvious reasons so just stay away from them as much as you can! Read more: Lost Decade Games Blog
Here are some cases to watch out for along with some tips for those trying to make their JavaScript as unreadable as possible:Don’t access object properties as string literals
Using Advanced Optimizations has its pitfalls. Because of it’s super aggressive renaming, Closure Compiler will break your code if you access object properties using string literals. For example: var thing.stuff = {
foo: 10,
bar: 20
};// This will break after Advanced Optimization :(
var foo = thing["stuff"].foo;
Closure will rewrite thing.stuff as something like a.b and accessing a["stuff"] isn’t going to work. Don’t use string literals
Closure Compiler won’t obfuscate string literals for obvious reasons so just stay away from them as much as you can! Read more: Lost Decade Games Blog
The Black Art of P/Invoke and Marshaling in .NET
Posted by
jasper22
at
17:26
|
Last week I finally managed to hunt down and resolve a bug that I had been chasing for quite some time. A couple of years ago I built an ASP.NET web service that makes use of a native library to provide most of its functionality. This native DLL exposes a C API, much like the Win32 API, that we’ve been using for integrating a highly-expensive product from a certain vendor into our system. I didn’t notice any issues during the initial development of this web service, in fact, I was very pleased with how easy it was to use and integrate this API. Until this very day, I still consider this as one of the nicest and most stable C API’s I’ve ever come across. After I finished most of the features for the web service, I ran a couple of load tests in order to determine whether the respective product could withstand a fair amount of requests and also to detect any glitches that might come up in the interop layer. Nothing major turned up, so we decided to bring this service into production and go on with out merry lives. Aft first we didn’t receive any complaints. Everything worked out as expected, until earlier this year, we noticed some failures of the application pool for our web service in IIS. The event log showed some random crashes of the CLR (= very bad) with some highly obscure error message. These issues occurred completely random. One day, there were about five to six application pool crashes after which it behaved very stable again, sometimes for months in a row. After doing some investigation on my part, which also involved stretching my shallow knowledge of WinDbg, I found out that .NET runtime was doing a complete shutdown after an AccessViolationException being thrown. This exception reported the following issue: Attempted to read or write protected memory. This is often an indication that other memory is corrupt.The first thing I considered was a memory leak turning up somewhere. It’s unmanaged code after all, right? After reviewing the code that uses the imported native functions, I discovered two potential memory leaks that might come up during some edge case scenarios. So I fixed those, but unfortunately it didn’t resolve the problem. Read more: <elegantc*de>
Android Theme For GMail And 4 More New Themes
Posted by
jasper22
at
17:17
|
 Google has been bringing the Android branding to pretty much every web product they own. Earlier we told you about an Android Theme for Google Chrome Browser. Now, Google has released an Android theme for GMail which has the GMail logo turned into a Bot! Four more new theme have been released in addition to the Android theme for GMail. Apart from the Android theme for GMail, there are four more new theme namely – Basic Black, Basic White, Tree Tops and Marker. You can check out the new themes by going to settings > Themes options from GMail inbox. Here are a few screen shots of the new GMail themes.You can also try your hands at making your own GMail themes. Read more: Digitizor
Google has been bringing the Android branding to pretty much every web product they own. Earlier we told you about an Android Theme for Google Chrome Browser. Now, Google has released an Android theme for GMail which has the GMail logo turned into a Bot! Four more new theme have been released in addition to the Android theme for GMail. Apart from the Android theme for GMail, there are four more new theme namely – Basic Black, Basic White, Tree Tops and Marker. You can check out the new themes by going to settings > Themes options from GMail inbox. Here are a few screen shots of the new GMail themes.You can also try your hands at making your own GMail themes. Read more: Digitizor Hacked Kinect Brings Futuristic User Interface
Posted by
jasper22
at
16:50
|
The video above is a picture browsing application running in Ubuntu controlled using Microsoft’s Kinect. It allows for a multi-touch like control without touching the surface – like the stuffs we see in Sci-Fi movies. Read more: digitizor
Did Internet Explorer 9 Cheat In The SunSpider Benchmark?
Posted by
jasper22
at
16:46
|
A Mozilla engineer has uncovered something embarrassing for Microsoft – Internet Explorer might be cheating in the SunSpider Benchmark. The SunSpider, although developed by Apple, has nowadays become a very popular choice of benchmark for the JavaScript engines of browsers. While Mozilla engineer Rob Sayre was benchmarking Firefox 4 with different browsers, he noticed something with Internet Explorer 9 – Internet Explorer 9 was around 10 times faster than the other browsers in a particular test (math-cordic) in the SunSpider benchmark. While Chrome and Opera scored took around 10ms in that test, Internet Explorer 9 finished it it in about 1ms. Sayre investigated further by modifying the code for that test used in the SunSpider Benchmark a bit. He made two variations of the test little bits of codes to the original – one by adding a “true” and another by adding a “return”. As these “true” and “return” in this context does not do anything there should be minimal impact. The result though is startling – Internet Explorer 9 took around 20 times longer with the two new tests compared with the original. While the original took only 1ms in my laptop, the other two took around 20ms each. Read more: digitizor
Google Refine lets you fix and handle huge, messy sets of data
Posted by
jasper22
at
15:21
|
Google has just introduced a new product, and this time it's a PC application (with a browser-based UI). It's called Google Refine, and it solves a problem that is enormous for some people: it lets you take massive sets of "messy data" and massage them into shape so that they're uniform, make sense, and can be statistically analyzed. The video after the jump shows a very good example, which is based on a CSV file exported from a publicly available data source (a government contract system, in this case). The data is very realistic – descriptions are inconsistent (Firm Fixed Price on some rows and FFP on other rows), and even the number formats are inconsistent (you get 0.78 on one row and a number in the millions on another row). Google Refine lets you very easily hone in on those inconsistencies and fix them in a myriad of ways. This is an important data tool because those heaps of messy data are often public records, which are available but not transparent; being able to quickly analyze them could expose some very interesting patterns and anomalies in the way that public institutions and governments behave. Read more: DownloadSquad
Gravity attempts to be the Pandora of the Web
Posted by
jasper22
at
15:20
|

Hacked iRobot Uses XBox Kinect To See World
Posted by
jasper22
at
11:49
|
A student at MIT's Personal Robotics Group is going to put Microsoft's Kinect to a good use: controlling robots. Philipp Robbel has hacked together the Kinect 3D sensor with an iRobot Create platform and assembled a battery-powered bot that can see its environment and obey your gestured commands. Tentatively named KinectBot, Robbel's creation can generate some beautifully detailed 3D maps of its surroundings and wirelessly send them to a host computer. KinectBot can also detect nearby humans and track their movements to understand where they want it to go."
In related but less agreeable news, "Dennis Durkin, who is both COO and CFO for Microsoft's Xbox group, told investors this week that Kinect can also be used by advertisers to see how many people are in a room when an ad is on screen, and to custom-tailor content based on the people it recognizes.
In related but less agreeable news, "Dennis Durkin, who is both COO and CFO for Microsoft's Xbox group, told investors this week that Kinect can also be used by advertisers to see how many people are in a room when an ad is on screen, and to custom-tailor content based on the people it recognizes.
Read more: Slashdot
UIControlSuite .NET
Posted by
jasper22
at
11:46
|

Docking control for WPF
Multi-column combobox for WPF and Silverlight
Ribbon control for Silverlight
Advanced Grid control for the WPF
Advanced Grid control for Silverlight
Advanced Grid control for ASP.NET MVC 2.0
Scheduler for WPF, with Hour, Day, Month and Year views
Scheduler for Silverlight, with Hour, Day, Month and Year views
Our best selling product suite UIControlSuite .NET is a collection of 41 powerful .NET controls for WinForms, WPF, and Silverlight (supporting both Silverlight versions 3.0 and 4.0) Read more: Binarymission
Web Deploy: How to see the command executed in Visual Studio during publish
Posted by
jasper22
at
11:41
|
I just saw a post on Twitter asking the question Is there any easy way to see the underlying MSBuild command when building in VS2010? Want to see the MSDeploy params. @wdeploy?One thing to know is that when you publish from Visual Studio, by default we use the MSDeploy (AKA Web Deployment Tool) Object Model in order to perform the deployment. We do this for performance and other reasons. Because of this there is no real msdeploy.exe command that is being issued. You can however change that behavior. This is controlled by an MSBuild property UseMSDeployExe which is false by default. In this case since Troy wants to see the command we will need to set that property to false. There are 2 ways in which you can do this. You can set it in the project file itself, or you can define it in a .wpp.targets file. I would recommend the second approach. What you need to do is to create a file with the name {ProjectName}.wpp.targets in the same directory as the project where {ProjectName} is the name of the Web Application Project (WAP). When you do this, during a build or publish the file is automatically imported into the build process. In my example I have a WAP named WebApplication1.csproj, so I created the file WebApplication1.wpp.targets and its contents are shown below. <?xml version="1.0" encoding="utf-8"?>
<Project ToolsVersion="4.0" DefaultTargets="Build"
xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<PropertyGroup>
<UseMsdeployExe>true</UseMsdeployExe>
</PropertyGroup>
</Project>
In the snippet above you can see that I defined the property to true. Now there is one more thing to do, publish the project. Once you publish the project, in the output window you will see the MSDeploy command which is being used. In my case I published the project to localhost to the Default Web Site/Test01 application path. You may have to copy the text from the output window into Notepad and search for msdeploy.exe. The command that was issued in my case is shown below (with formatting changes for readability). "C:\Program Files (x86)\IIS\Microsoft Web Deploy\msdeploy.exe"
-source:manifest='C:\temp\_NET\ThrowAway\WebApplication3\WebApplication1\obj\Debug\Package\WebApplication1.SourceManifest.xml'
-dest:auto,IncludeAcls='False',AuthType='NTLM'
-verb:sync
Read more: Visual Web Developer Team Blog
<Project ToolsVersion="4.0" DefaultTargets="Build"
xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<PropertyGroup>
<UseMsdeployExe>true</UseMsdeployExe>
</PropertyGroup>
</Project>
In the snippet above you can see that I defined the property to true. Now there is one more thing to do, publish the project. Once you publish the project, in the output window you will see the MSDeploy command which is being used. In my case I published the project to localhost to the Default Web Site/Test01 application path. You may have to copy the text from the output window into Notepad and search for msdeploy.exe. The command that was issued in my case is shown below (with formatting changes for readability). "C:\Program Files (x86)\IIS\Microsoft Web Deploy\msdeploy.exe"
-source:manifest='C:\temp\_NET\ThrowAway\WebApplication3\WebApplication1\obj\Debug\Package\WebApplication1.SourceManifest.xml'
-dest:auto,IncludeAcls='False',AuthType='NTLM'
-verb:sync
Read more: Visual Web Developer Team Blog
GeckoFX
Posted by
jasper22
at
11:24
|

GeckoFX is a Windows Forms control written in clean, commented C# that embeds the Mozilla Gecko browser control in any Windows Forms Application. It also contains a simple class model providing access to the HTML and CSS DOM. GeckoFX was originally created by Andrew Young for the fast-growing visual CSS editor, Stylizer. It is now released as open-source under the Mozilla Public License.Visit the community support forum here: http://www.geckofx.org Read more: Google Code
OpenWrap
Posted by
jasper22
at
11:03
|
Any .NET project beyond "hello world" is going to require external libraries and tools. There's an abundance of free, open source libraries out there, but how do you get what you need? Manually searching, downloading (and in some cases building from source) is not a productive use of your time. It's even worse when one library depends on another and you have to manage dependency chains! The solution: OpenWrapFor example, say you want to use NHibernate in your project. Simply run this at the command line: c:\myproject> o add-wrap nhibernateOpenWrap will query available repositories for the NHibernate "wrap" and download it along with all the necessary dependencies, such as Castle. Wraps are simple zip files containing the binaries, tools and other useful content. They are copied into your project in an x-copy friendly manner. Read more: OpenWrap
Browser Information In Silverlight
Posted by
jasper22
at
11:01
|
In this post I will show you how to get the browser information.To get the browser information the namespace used for this is System.Windows.Browser. The BrowserInformation object contains properties such as the name, product name, product version , browser version etc. Let us start with the example which will use to get this information and display on the screen which I will share with you at the end of the post I will use two screen shot one for the Internet explorer and the second one for the Fire Fox.
For this Example I have create one class with the name BrowserInfo which has the properties like BrowserName , BrowerVersion, Platform, ProductName, UserAgent of type string , IsCookiesEnabled of type Boolean to indicate whether Cookies are enabled or not , BrowserMinorVersion and BrowserMajorVersion are of type int.You can see the default constructor of the BrowserInfo class which is used to initialize all the properties of the class. public BrowserInfo()
{
BrowserName = HtmlPage.BrowserInformation.Name;
BrowserVersion = HtmlPage.BrowserInformation.BrowserVersion.ToString();
BrowserMajorVersion = HtmlPage.BrowserInformation.BrowserVersion.Major;
BrowserMinorVersion = HtmlPage.BrowserInformation.BrowserVersion.Minor;
IsCookiesEnabled = HtmlPage.BrowserInformation.CookiesEnabled;
Platform = HtmlPage.BrowserInformation.Platform;
ProductName = HtmlPage.BrowserInformation.ProductName;
ProductVersion = HtmlPage.BrowserInformation.ProductVersion;
UserAgent = HtmlPage.BrowserInformation.UserAgent;
}Read more: Asim Sajjad
For this Example I have create one class with the name BrowserInfo which has the properties like BrowserName , BrowerVersion, Platform, ProductName, UserAgent of type string , IsCookiesEnabled of type Boolean to indicate whether Cookies are enabled or not , BrowserMinorVersion and BrowserMajorVersion are of type int.You can see the default constructor of the BrowserInfo class which is used to initialize all the properties of the class. public BrowserInfo()
{
BrowserName = HtmlPage.BrowserInformation.Name;
BrowserVersion = HtmlPage.BrowserInformation.BrowserVersion.ToString();
BrowserMajorVersion = HtmlPage.BrowserInformation.BrowserVersion.Major;
BrowserMinorVersion = HtmlPage.BrowserInformation.BrowserVersion.Minor;
IsCookiesEnabled = HtmlPage.BrowserInformation.CookiesEnabled;
Platform = HtmlPage.BrowserInformation.Platform;
ProductName = HtmlPage.BrowserInformation.ProductName;
ProductVersion = HtmlPage.BrowserInformation.ProductVersion;
UserAgent = HtmlPage.BrowserInformation.UserAgent;
}Read more: Asim Sajjad
How to: create a nonrectangular ChildWindow - part 1
Posted by
jasper22
at
10:56
|
This article describes step by step how to create a non rectangular child window. A ring-shaped child window is created. Step 1 - preparations
In expression blend 4 a new Silverlight 4 project is created. A button is added to the surface of MainPage.xaml. This button is later used to call the ChildWindow. Then--add new item… is the Silverlight project by right-clicking on the project-> ChildWindow added a ChildWindow. This ChildWindow is named "RingChildWindow.xaml". Clicking OK adds the new ChildWindow to the project. The ChildWindow receives a size from 400px x 400px. Step 2 - styling the template
In expression blend 4 RingChildWindow for editing is now displayed. The ChildWindow is selected with the left mouse button in the object tree "Objects and timeline" tab. Read more: SilverLaw
In expression blend 4 a new Silverlight 4 project is created. A button is added to the surface of MainPage.xaml. This button is later used to call the ChildWindow. Then--add new item… is the Silverlight project by right-clicking on the project-> ChildWindow added a ChildWindow. This ChildWindow is named "RingChildWindow.xaml". Clicking OK adds the new ChildWindow to the project. The ChildWindow receives a size from 400px x 400px. Step 2 - styling the template
In expression blend 4 RingChildWindow for editing is now displayed. The ChildWindow is selected with the left mouse button in the object tree "Objects and timeline" tab. Read more: SilverLaw
Changing the viewport of a listbox in WPF
Posted by
jasper22
at
10:55
|
One of the nice thing about the WPF controls is the ability for them to mimic almost anything….In my case I wanted to recreate an old Winform sample of a NASDAQ sales status board…Which required a grid to draw different colors, show new items being added – but do it with out scrollbars…Turns out the WPF Listbox does all this with no or very little code at all – in most cases just a little mark up. So how did I do this:1. Eliminate the Scrollbars:ScrollViewer.HorizontalScrollBarVisibility="Hidden" 2. Have the listbox show the last item (to simulate scrolling updates) is one line of code you add after you have added an item: ListBox1.ScrollIntoView(ListBox1.Items(ListBox1.Items.Count - 1))3. To change the colors on a item by item basis is also one line of code i.e.listitem = New ListBoxItemlistitem.Foreground = New SolidColorBrush(Colors.Sienna) ListBox1.Items.Add(listitem)So with the use of MSMQ I was able to write an order simulator pretty quickly!(The colors are the priority of the message that was sent)Read more: Ozzie Rules Blogging
Creating a ASP.NET MVC HTML Helper for Silverlight
Posted by
jasper22
at
10:52
|
Over the last few weeks I have started investing some time in learning ASP.NET MVC (specifically ASP.NET MVC 2). This has nothing with the ongoing "Silverlight is dead" debate and I actually started a deep dive into the technology back in August 2010. I think that ASP.NET MVC is very important for Silverlight developers to learn (more on this in another blog post), because of its obvious positioning in Microsoft's HTML5 tooling investments (more on that in MIX 2011). Intro to HTML HelpersHTML Helpers have the following qualities:Usually implemented via extension methods
Usually implemented part of a static class
In .NET 4.0/C# 4.0 utilize optional parameters to minimize the initialization signature
Used inline with HTML in ASP.NET MVC Views to create dynamic content, while minimizing the code written and maintained
Basically an HTML helper is a extension method that takes some parameters and renders HTML. In ASP.NET MVC you have complete control over the rendering of the HTML in your Views. If you are an ASP.NET developer you can think of it as having the ability to dictate the exact HTML/Javascript that gets surfaced when you drag over any ASP.NET server control. For example, if you drag over an ASP.NET button server control, ASP.NET handles how that control is rendered on the page. Of course in ASP.NET you could override the rendering from the server, however it was a major pain. HTML Helpers in ASP.NET MVC are there to minimize how much code you need to write. For example, instead of having to write 100 lines of HTML every time there is an input form. You could create an HTML Helper that does this for you. This minimizes the code, improves maintenance of your code and abstracts that component into its own SRP (single responsibility principle) method. ASP.NET MVC versions 1 through 3 include a ton of HTML Helpers. These helpers include basic methods for rendering simple HTML like a text box to more complex helpers. If you download the ASP.NET MVC 3 source code, you will see a lot of very complex HTML Helpers. These HTML helpers can render complex HTML with interactive HTML. For example, my companion site (http://www.silverlightbusinessintelligence.com) for my Silverlight business intelligence book utilizes the Twitter HTML helper that renders my tweets in a nice interactive HTML component with JavaScript that makes the appropriate web service requests. Some of the advanced HTML helpers include: Facebook, Twitter, video etc. The beauty of this is that in order to utilize this component I just had to reference it using one line of code. Read more: Silverlight Hack
Usually implemented part of a static class
In .NET 4.0/C# 4.0 utilize optional parameters to minimize the initialization signature
Used inline with HTML in ASP.NET MVC Views to create dynamic content, while minimizing the code written and maintained
Basically an HTML helper is a extension method that takes some parameters and renders HTML. In ASP.NET MVC you have complete control over the rendering of the HTML in your Views. If you are an ASP.NET developer you can think of it as having the ability to dictate the exact HTML/Javascript that gets surfaced when you drag over any ASP.NET server control. For example, if you drag over an ASP.NET button server control, ASP.NET handles how that control is rendered on the page. Of course in ASP.NET you could override the rendering from the server, however it was a major pain. HTML Helpers in ASP.NET MVC are there to minimize how much code you need to write. For example, instead of having to write 100 lines of HTML every time there is an input form. You could create an HTML Helper that does this for you. This minimizes the code, improves maintenance of your code and abstracts that component into its own SRP (single responsibility principle) method. ASP.NET MVC versions 1 through 3 include a ton of HTML Helpers. These helpers include basic methods for rendering simple HTML like a text box to more complex helpers. If you download the ASP.NET MVC 3 source code, you will see a lot of very complex HTML Helpers. These HTML helpers can render complex HTML with interactive HTML. For example, my companion site (http://www.silverlightbusinessintelligence.com) for my Silverlight business intelligence book utilizes the Twitter HTML helper that renders my tweets in a nice interactive HTML component with JavaScript that makes the appropriate web service requests. Some of the advanced HTML helpers include: Facebook, Twitter, video etc. The beauty of this is that in order to utilize this component I just had to reference it using one line of code. Read more: Silverlight Hack
Decoding clr20r3 .NET exception – using mono cecil
Posted by
jasper22
at
10:51
|
I have often seen Devs trying to figure out the cause of the app crash without a memory dump. The only information that is available to analyze is the Windows Error Reporting message in the event viewer which would have “Event Name: CLR20r3″ along with Watson bucket information like this. Fault bucket , type 0
Event Name: CLR20r3
Response: Not available
Cab Id: 0Problem signature:
P1: unhandledexception.exe
P2: 1.0.0.0
P3: 4ce1e0f1
P4: LibraryCode
P5: 1.0.0.0
P6: 4ce1e0f1
P7: 7
P8: 1f
P9: System.NullReferenceException
P10:I will demonstrate the steps in identifying the code that caused the app to crash with the above information.Here is the explanation on the Watson Bucket items
Event Name: CLR20r3
Response: Not available
Cab Id: 0Problem signature:
P1: unhandledexception.exe
P2: 1.0.0.0
P3: 4ce1e0f1
P4: LibraryCode
P5: 1.0.0.0
P6: 4ce1e0f1
P7: 7
P8: 1f
P9: System.NullReferenceException
P10:I will demonstrate the steps in identifying the code that caused the app to crash with the above information.Here is the explanation on the Watson Bucket items
- P1: unhandledexception.exe – is the Exe File Name
- P2:1.0.0.0 – is the Exe File assembly version number
- P3:4ce1e0f1- is the Exe File Stamp
- P4:LibraryCode- is the Faulting full assembly name
- P5:1.0.0.0- is the Faulting assembly version
- P6:4ce1e0f1- is the Faulting assembly timestamp
- P7:7- is the Faulting assembly method def
- P8:1f- is Faulting method IL Offset within the faulting method
- P9:System.NullReferenceException- is Exception type that was thrown
Word2CHM, convert a word document to a CHM file.
Posted by
jasper22
at
10:45
|
Word2CHM is a open source C# program which can convert MS Word document(in 2000/2003 format) to a CHM document. It require HTML Help Workshop and MS Word 2003.BackgroundMany people write customer help document with MS Word, because MS Word is very fit to write document include text, images and tables. But many customers did not want read help document in MS Word format, but they like CHM format. So it is useful than convert ms word document to CHM document. This is why I build Word2CHM.Word2CHMIn Word2CHM , there are three steps in converting ms word document to CHM document . First is convert ms word document to a single html file, second is split a single html file to multi html files, and thirst is compile multi html files to a single CHM file. First, Convert ms word document to a single html fileMS Word application support OLE automatic technology, a C# program can host a ms word application, open ms word binary document and save as a html file. There are some sample C# code that hosts a ms word application.private bool SaveWordToHtml(string docFileName, string htmlFileName)
{
// check doc file name
if (System.IO.File.Exists(docFileName) == false )
{
this.Alert("File '" + docFileName + "' not exist!");
return false;
}
// check output directory
string dir = System.IO.Path.GetDirectoryName(htmlFileName);
if (System.IO.Directory.Exists(dir) == false )
{
this.Alert("Directory '" + dir + "' not exist!");
return false;
} object trueValue = true;
object falseValue = false;
object missValue = System.Reflection.Missing.Value;
object fileNameValue = docFileName; // create word application instance
Microsoft.Office.Interop.Word.Application app =
new Microsoft.Office.Interop.Word.ApplicationClass();
// set word application visible
// if something is error and quit , user can close word application by self.
app.Visible = true;
// open document
Microsoft.Office.Interop.Word.Document doc = app.Documents.Open(
ref fileNameValue,
ref missValue,
ref trueValue,
ref missValue,Read more: Codeproject
{
// check doc file name
if (System.IO.File.Exists(docFileName) == false )
{
this.Alert("File '" + docFileName + "' not exist!");
return false;
}
// check output directory
string dir = System.IO.Path.GetDirectoryName(htmlFileName);
if (System.IO.Directory.Exists(dir) == false )
{
this.Alert("Directory '" + dir + "' not exist!");
return false;
} object trueValue = true;
object falseValue = false;
object missValue = System.Reflection.Missing.Value;
object fileNameValue = docFileName; // create word application instance
Microsoft.Office.Interop.Word.Application app =
new Microsoft.Office.Interop.Word.ApplicationClass();
// set word application visible
// if something is error and quit , user can close word application by self.
app.Visible = true;
// open document
Microsoft.Office.Interop.Word.Document doc = app.Documents.Open(
ref fileNameValue,
ref missValue,
ref trueValue,
ref missValue,Read more: Codeproject
Gaikai beta opens
Posted by
jasper22
at
10:44
|
Notable developer Dave Perry has announced that Gaikai entered open beta on Sunday.
The game-streaming service is being launched gradually, with 1,000 invites sent out to consumers at the weekend, and more being issued in waves of 10,000.
“Everyone will be getting invited in batches and if you are too far from our servers, don’t worry you’ve actually helped as you’ve shown us where we need to install more data centers,” wrote Perry on his blog.
Gaikai launched with a demo version of Mass Effect 2, and Perry reports that both the game’s developer BioWare and publisher Electronic Arts have “been very supportive”.
“The good news for them is we are getting a surprising amount of people clicking ‘buy’ without even making them a special offer,” he added.Read more: MCV
The game-streaming service is being launched gradually, with 1,000 invites sent out to consumers at the weekend, and more being issued in waves of 10,000.
“Everyone will be getting invited in batches and if you are too far from our servers, don’t worry you’ve actually helped as you’ve shown us where we need to install more data centers,” wrote Perry on his blog.
Gaikai launched with a demo version of Mass Effect 2, and Perry reports that both the game’s developer BioWare and publisher Electronic Arts have “been very supportive”.
“The good news for them is we are getting a surprising amount of people clicking ‘buy’ without even making them a special offer,” he added.Read more: MCV
GFS the Google File System in 199 Lines of Python
Posted by
jasper22
at
10:43
|
GFS, the Google File System, sits as the backbone of the entire Google infrastructure. However, for many it is a mystery, especially for those lucky enough to be more acquainted with high-level python code than low-level C operating system sources. But have no fear, we shall break through the veil and describe an implementation of GFS in 199 lines of python. Naturally, you may want to read about the theory and design of GFS in the original Google Research GFS paper. But we will aim to give the core concepts, with real working python code, in this article. Complete runnable python 2.6 source code, if you wish it, is available at the end of this post. A brief summary of GFS is as follows. GFS consists of three components: a client, a master, and one or more chunkservers. The client is the only user-visible, that is programmer-accessible, part of the system. It functions similarly to a standard POSIX file library. The master is a single server that holds all metadata for the filesystem. By metadata we mean the information about each file, its constituent components called chunks, and the location of these chunks on various chunkservers. The chunkservers are where the actual data is stored, and the vast majority of network traffic takes place between the client and the chunkservers, to avoid the master as a bottleneck. We will give more detailed descriptions below by going through the GFS client, master, and chunkserver as implemented in python classes, and close with a test script and its output. Read more: Python Cloud DB
No More Magic Strings! Presenting: @string.of
Posted by
jasper22
at
10:14
|
The ProblemHow many times have you seen the following code snippets?1. Checking method parametersif (executeMethod == null)
{
throw new ArgumentNullException("executeMethod");
}
2. Implementing a property in a WPF / SL view-modelpublic double Size
{
get { return _size; }
set
{
_size = value;
RaisePropertyChanged("Size");
}
}
The first time I had to wrote code like this I felt uneasy. Hardcoded strings are bad practice and should be rarely used.Even worse, using a hardcoded string of an identifier is just a bug waiting to happen. Consider what happens when you need to refactor your code and change the name of the Size property (second example) to something different like MaxSize.
The refactoring tools will not change the hardcoded string “Size” and now your WPF application stops notifying on property change the way it should! These bugs are very difficult to spot. No compile time error, no runtime error. Nothing. The only way to spot this bug is by testing this specific functionality.I’ve checked a small WPF application and found 158 (!) instances of these
almost-bugs.The SolutionAre you familiar with the typeof operator?
Don’t you just loved it if there was a stringof operator?Read more: Arik Poznanski's Blog
{
throw new ArgumentNullException("executeMethod");
}
2. Implementing a property in a WPF / SL view-modelpublic double Size
{
get { return _size; }
set
{
_size = value;
RaisePropertyChanged("Size");
}
}
The first time I had to wrote code like this I felt uneasy. Hardcoded strings are bad practice and should be rarely used.Even worse, using a hardcoded string of an identifier is just a bug waiting to happen. Consider what happens when you need to refactor your code and change the name of the Size property (second example) to something different like MaxSize.
The refactoring tools will not change the hardcoded string “Size” and now your WPF application stops notifying on property change the way it should! These bugs are very difficult to spot. No compile time error, no runtime error. Nothing. The only way to spot this bug is by testing this specific functionality.I’ve checked a small WPF application and found 158 (!) instances of these
almost-bugs.The SolutionAre you familiar with the typeof operator?
Don’t you just loved it if there was a stringof operator?Read more: Arik Poznanski's Blog
CppUnit
Posted by
jasper22
at
10:09
|
What is CppUnit? CppUnit is a C++ unit testing framework. It started its life as a port of JUnit to C++ by Michael Feathers. For a quick tour of unit testing with CppUnit, see the Cookbook in the latest documentation. For an introduction to unit testing, see [UnitTest], [ProgrammerTest], and [CodeUnitTestFirst] at the [wiki:Wiki:FrontPage C2.com wiki].
Features:
Read more: CppUnit
Features:
- XML output with hooks for additional data (XSL format avaliable in release 1.10.2 needs some FiXing)
- Compiler-like text output to integrate with an IDE
- Helper macros for easier test suite declaration
- Hierarchical test fixture support
- Test registry to reduce recompilation need
- Test plug-in for faster compile/test cycle (self testable dynamic library)
- Protector to encapsulate test execution (allow capture of exception not derived from std::exception)
- MfcTestRunner
- QtTestRunner, a Qt based graphic test runner
- CursesTestRunner
- WxWidgetsTestRunner (formerly: WxWindowsTestRunner)
Read more: CppUnit
Missing INTERNET_STATUS_REQUEST_COMPLETE callback after calling Wininet’s FtpOpenFile() in asynchronous mode
Posted by
jasper22
at
09:58
|
Symptom: To reproduce the issue:
1. Put a zero byte file on a FTP site.2. Call InternetOpen() with flag INTERNET_FLAG_ASYNC3. FtpOpenFile() to download the file. Wininet will send out a FTP request. After receiving the response, the registered callback procedure will receive an INTERNET_STATUS_REQUEST_COMPLETE event.4. Call FtpOpenFile() again.This time Wininet will not send out any FTP request, nor raise the INTERNET_STATUS_REQUEST_COMPLETE event. The application will then hang if it waits for the above event.
This issue happens only if in asynchronous mode. A zero byte file can always reproduce the issue. Troubleshooting: There is a Wininet asynchronous mode sample about how to download HTTP files: http://msdn.microsoft.com/en-us/library/cc185684(VS.85).aspx Although it is HTTP not FTP, we can learn some ideas from that sample. Solution: After test and test, it was found that if we add flag INTERNET_FLAG_RELOAD when calling FtpOpenFile(), it began to work properly. FtpOpenFile(hFtp_,path,GENERIC_READ,FTP_TRANSFER_TYPE_BINARY|INTERNET_FLAG_RELOAD,reinterpret_cast<DWORD_PTR>(this)); According to http://msdn.microsoft.com/en-us/library/aa383661(VS.85).aspx : Read more: AsiaTech: Learning by Practice
1. Put a zero byte file on a FTP site.2. Call InternetOpen() with flag INTERNET_FLAG_ASYNC3. FtpOpenFile() to download the file. Wininet will send out a FTP request. After receiving the response, the registered callback procedure will receive an INTERNET_STATUS_REQUEST_COMPLETE event.4. Call FtpOpenFile() again.This time Wininet will not send out any FTP request, nor raise the INTERNET_STATUS_REQUEST_COMPLETE event. The application will then hang if it waits for the above event.
This issue happens only if in asynchronous mode. A zero byte file can always reproduce the issue. Troubleshooting: There is a Wininet asynchronous mode sample about how to download HTTP files: http://msdn.microsoft.com/en-us/library/cc185684(VS.85).aspx Although it is HTTP not FTP, we can learn some ideas from that sample. Solution: After test and test, it was found that if we add flag INTERNET_FLAG_RELOAD when calling FtpOpenFile(), it began to work properly. FtpOpenFile(hFtp_,path,GENERIC_READ,FTP_TRANSFER_TYPE_BINARY|INTERNET_FLAG_RELOAD,reinterpret_cast<DWORD_PTR>(this)); According to http://msdn.microsoft.com/en-us/library/aa383661(VS.85).aspx : Read more: AsiaTech: Learning by Practice
30 Fresh Inspirational Web Designs
Posted by
jasper22
at
09:52
|



Web.config Transformation Syntax for Web Application Project Deployment
Posted by
jasper22
at
09:47
|
Web.config files typically include settings that have to be different depending on which environment the application is running in. For example, you might have to change a database connection string or disable debugging when you deploy a Web.config file. For Web application projects, ASP.NET provides tools that automate the process of changing (transforming) Web.config files when they are deployed. For each environment that you want to deploy to, you create a transform file that specifies only the differences between the original Web.config file and the deployed Web.config file for that environment. A transform file is an XML file that specifies how the Web.config file should be changed when it is deployed. Transformation actions are specified by using XML attributes that are defined in the XML-Document-Transform namespace, which is mapped to the xdt prefix. The XML-Document-Transform namespace defines two attributes: Locator and Transform. The Locator attribute specifies the Web.config element or set of elements that you want to change in some way. The Transform attribute specifies what you want to do to the elements that the Locator attribute finds. The following example shows the contents of a transform file that changes a connection string and replaces the customErrors element:<?xml version="1.0"?>
<configuration xmlns:xdt="http://schemas.microsoft.com/XML-Document-Transform">
<connectionStrings>
<add name="MyDB"
connectionString="value for the deployed Web.config file"
xdt:Transform="SetAttributes" xdt:Locator="Match(name)"/>
</connectionStrings>
<system.web>
<customErrors defaultRedirect="GenericError.htm"
mode="RemoteOnly" xdt:Transform="Replace">
<error statusCode="500" redirect="InternalError.htm"/>
</customErrors>
</system.web>
</configuration>
The root element of a transform file must specify the XML-Document-Transform namespace in its opening tag, as shown in the preceding example. The Locator and Transform elements themselves are not reproduced in the deployed Web.config file. This following sections provide reference information about the syntax to use in transform files.Read more: MSDN
<configuration xmlns:xdt="http://schemas.microsoft.com/XML-Document-Transform">
<connectionStrings>
<add name="MyDB"
connectionString="value for the deployed Web.config file"
xdt:Transform="SetAttributes" xdt:Locator="Match(name)"/>
</connectionStrings>
<system.web>
<customErrors defaultRedirect="GenericError.htm"
mode="RemoteOnly" xdt:Transform="Replace">
<error statusCode="500" redirect="InternalError.htm"/>
</customErrors>
</system.web>
</configuration>
The root element of a transform file must specify the XML-Document-Transform namespace in its opening tag, as shown in the preceding example. The Locator and Transform elements themselves are not reproduced in the deployed Web.config file. This following sections provide reference information about the syntax to use in transform files.Read more: MSDN
Y PPA Manager: Easily Search, Add, Remove Or Purge PPAs In Ubuntu
Y PPA Manager is a project I've been working on for a couple of weeks for easily managing and finding Launchpad PPAs in Ubuntu. Y PPA Manager is a tool for easily managing Launchpad PPAs that uses YAD for a graphical user interface (a Zenity fork which comes with a lot of improvements) and comes as a .deb and with a Launchpad PPA for easy updates. Please note that this is a pre-alpha release as I'm the only one who's ever used Y PPA Manager so far. Y PPA Manager features (in this first release):Add PPA
Delete PPA - displays all the enabled PPAs (disabled PPAs will not be listed) and you can delete any PPA from that list
Purge PPA - uses the "ppa-purge" tool to downgrade the packages in the selected PPA to the version in the official Ubuntu repositories and disables that PPA
List packages in a PPA enabled on your computer - lists all the packages that are available for your Ubuntu version in the selected PPA (only PPAs that you have added to your system and are enabled will show up here)
Search in all Launchpad PPAs - will perform a search in all the Launchpad PPAs for the package you enter in the search form. The search uses the Launchpad PPA search so it may return empty PPAs if the PPAs have a description that matches your search, or a PPA with packages for a different Ubuntu version then your current Ubuntu version (or the Ubuntu version you've set Y PPA Manager to search for - see info regarding the settings below). You will be able to perform the following operations on a PPA: add it, list all the packages in that PPA for your Ubuntu version (or the Ubuntu version you've set Y PPA Manager to search for in the settings) - including the package versions, download selected packages from a PPA, copy PPA link (so you can then paste it in a web browser). Read more: Web Upd8
Delete PPA - displays all the enabled PPAs (disabled PPAs will not be listed) and you can delete any PPA from that list
Purge PPA - uses the "ppa-purge" tool to downgrade the packages in the selected PPA to the version in the official Ubuntu repositories and disables that PPA
List packages in a PPA enabled on your computer - lists all the packages that are available for your Ubuntu version in the selected PPA (only PPAs that you have added to your system and are enabled will show up here)
Search in all Launchpad PPAs - will perform a search in all the Launchpad PPAs for the package you enter in the search form. The search uses the Launchpad PPA search so it may return empty PPAs if the PPAs have a description that matches your search, or a PPA with packages for a different Ubuntu version then your current Ubuntu version (or the Ubuntu version you've set Y PPA Manager to search for - see info regarding the settings below). You will be able to perform the following operations on a PPA: add it, list all the packages in that PPA for your Ubuntu version (or the Ubuntu version you've set Y PPA Manager to search for in the settings) - including the package versions, download selected packages from a PPA, copy PPA link (so you can then paste it in a web browser). Read more: Web Upd8
Google Translation bots
Posted by
jasper22
at
18:40
|
Google Talk can help you with quick translations, or even translate your chats in real-time! All you need to do is chat with one of our Translation Bots. The bots are named using two-letter language abbreviations formatted as '[from language]2[to language]@bot.talk.google.com,' and all available combinations are listed in the table below. To use a bot, add it to your Friends list and send it the message you want translated. For example, if you send "Hello" to en2es@bot.talk.google.com (English to Spanish), it will respond with "Hola." If you're using the Google Talk Gadget, you can also get your conversation translated by inviting a bot to a group chat with a friend. Read more: Google
The ~200 Line Linux Kernel Patch That Does Wonders
Posted by
jasper22
at
16:57
|
There is a relatively miniscule patch to the Linux kernel scheduler being queued up for Linux 2.6.38 that is proving to have dramatic results for those multi-tasking on the desktop. Phoronix is reporting the ~200 line Linux kernel patch that does wonders with before and after videos demonstrating the much-improved responsiveness and interactivity of the Linux desktop. While compiling the Linux kernel with 64 parallel jobs, 1080p video playback was still smooth, windows could be moved fluidly, and there was not nearly as much of a slowdown compared to when this patch was applied. Linus Torvalds has shared his thoughts on this patch: So I think this is firmly one of those 'real improvement' patches. Good job. Group scheduling goes from 'useful for some specific server loads' to 'that's a killer feature. Read more: Slashdot
How to rescue your friends' email addresses from Facebook and export them to Gmail
Posted by
jasper22
at
16:56
|

Cracking Passwords With Amazon EC2 GPU Instances
Posted by
jasper22
at
16:55
|
As of Nov. 15, 2010, Amazon EC2 is providing what they call 'Cluster GPU Instances': An instance in the Amazon cloud that provides you with the power of two NVIDIA Tesla 'Fermi' M2050 GPUs... Using the CUDA-Multiforce, I was able to crack all hashes from this file with a password length from 1-6 in only 49 Minutes (1 hour costs $2.10 by the way.). This is just another demonstration of the weakness of SHA1 — you really don't want to use it anymore. Read more: Slashdot
How To Use Your Wii Remote as a Gyroscopic Mouse
Posted by
jasper22
at
16:54
|

- A Wii remote (obviously)
- The Motion Plus add-on
- Windows XP, Vista, or 7
- A Bluetooth dongle for your PC
- The WIDCOMM Bluetooth stack (from Broadcom’s website) (version 6.2.1.100 at the time of writing)
- GlovePIE with Emotiv support (from the GlovePIE Project website) (version 0.43 at the time of writing)
The Software
The WIDCOMM Bluetooth stack allows you to pair your computer with the Wii remote without using a code. That’s the key piece to getting it working, and although the BlueSoleil stack can do this as well if not better, it’s not free. After the pairing is complete, the GlovePIE application will run a script that takes your controller input and translate that into mouse emulation. With some tweaking, you can extend the functionality of your makeshift mouse and even use it as a joystick/gamepad. Read more: How-to-geek
TDL4 Rootkit Bypasses Windows Code-Signing Protection
Posted by
jasper22
at
16:35
|
In recent versions of Windows, specifically Vista and Windows 7, Microsoft has introduced a number of new security features designed to prevent malicious code from running. But attackers are continually finding new ways around those protections, and the latest example is a rootkit that can bypass the Windows driver-signing protection. The functionality is contained in TDL4, which is the latest version of an older rootkit also known as TDSS and Alureon. TDSS has been causing serious trouble for users for more than two years now, and is an example of a particularly pernicious type of rootkit that infects the master boot record of a PC. This type of malware often is referred to as a bootkit and can be extremely difficult to remove once it's detected. The older versions of TDSS--TDL1, TDL2 and TDL3--are detected by most antimalware suites now, but it's TDL4 that's the most problematic right now. TDL4 has a specific function that is designed to bypass a protection in Windows 7 and Windows Vista that requires kernel-level code loaded onto a machine to be signed. The Windows kernel-mode code signing policy is mainly applicable on 64-bit machines. Read more: threatPost
DIY Kinect Hacking
Posted by
jasper22
at
16:23
|
Introduction!Everyone has seen the Xbox 360 Kinect hacked in a matter of days after our "open source driver" bounty - here's how we helped the winner and here's how you can reverse engineer USB devices as well! USB is a very complex protocol, must more complicated than Serial or Parallel, SPI and even I2C. USB uses only two wires but they are not used as 'receive' and 'transmit' like serial. Rather, data is bidirectional and differential - that is the data sent depends on the difference in voltage between the two data lines D+ and D- If you want to do more USB hacking, you'll need to read Jan Axelson's USB Complete books , they're easy to follow and discuss USB in both depth and breadth. USB is also very structured. This is good for reverse engineering because it means that at least the format of packets is agreed upon and you won't have to deal with check-sums. The bad news is it means you have to have software assistance to decode the complex packet structure. The good news is that every computer now made has a USB host core, that does a lot of the tough work for you, and there are many software libraries to assist. Today we're going to be reverse engineering the Xbox Kinect Motor, one part of the Kinect device.
Verify the VID & PID
The first place to start is to see what devices and "interfaces" or "configurations" are available for the USB device. The nicest way to do this is to use lsusb (Linux) or system_profiler (Mac) which is a "list usb" program available for Linux and mac. Sadly, it does not exist for windows, so find a mac or linux computer or friend, you'll only need it for a minute! For linux, run lsusb -vv (ultra verbose) for Mac, run system_profiler SPUSBDataTypeRead more: ladyada.net
Verify the VID & PID
The first place to start is to see what devices and "interfaces" or "configurations" are available for the USB device. The nicest way to do this is to use lsusb (Linux) or system_profiler (Mac) which is a "list usb" program available for Linux and mac. Sadly, it does not exist for windows, so find a mac or linux computer or friend, you'll only need it for a minute! For linux, run lsusb -vv (ultra verbose) for Mac, run system_profiler SPUSBDataTypeRead more: ladyada.net
101 Great Computer Programming Quotes
Posted by
jasper22
at
14:27
|
“Most software today is very much like an Egyptian pyramid with millions of bricks piled on top of each other, with no structural integrity, but just done by brute force and thousands of slaves.”
(Alan Kay)
Read more: Dev Topics
(Alan Kay)
Read more: Dev Topics
What every developer should know about fonts
Posted by
jasper22
at
14:25
|
I originally thought using fonts would be pretty simple. However, proper handling of fonts has ended up being a significant effort in Windward Reports (our XML and SQL Reporting system). If you're going to do much more than place a line of text in a form, then the details start to matter. Fonts & Glyphs
So what is a font? Fundamentally a font is a series of glyphs. What you think of as a character like the letter A is a glyph. A font is then a set of glyphs for all the letters in that font. If you get the Helvetica font, all their glyphs look one way. If you get the Times Roman font, they look another. Each is the set of glyphs from that font. Now we need to introduce the concept of code pages. A code page is a mapping from a character number to a specific glyph. Programs originally stored each character as a byte. Then for Asian character sets there were the DBCS systems (some characters were 1 byte, some 2). Programs today mostly use Unicode, but web pages tend to be UTF-8 which is a multi-byte sequence that can be up to 4 bytes. Why bring up encoding? Because each font has an encoding where character number 178 could return a very different glyph depending on the codepage used by the font. Most font files use Unicode so you have a standard there, but many programs still use specific code pages, where that page is mapped to the font. This is what occurs when you display ABC and the font is Wingdings so you get . So point one is you need to make sure that the encoding you use matches or is mapped to the encoding of the fonts you use. And it gets even more complex. The characters with the values 0xE000 – 0xF8FF are undefined. Each font can make those anything they want (one use is to add the Klingon script). So a character with a value in this range is by definition tied to the font file it is using to display that font. This is how most symbol type fonts work. Read more: Windward Wrocks
So what is a font? Fundamentally a font is a series of glyphs. What you think of as a character like the letter A is a glyph. A font is then a set of glyphs for all the letters in that font. If you get the Helvetica font, all their glyphs look one way. If you get the Times Roman font, they look another. Each is the set of glyphs from that font. Now we need to introduce the concept of code pages. A code page is a mapping from a character number to a specific glyph. Programs originally stored each character as a byte. Then for Asian character sets there were the DBCS systems (some characters were 1 byte, some 2). Programs today mostly use Unicode, but web pages tend to be UTF-8 which is a multi-byte sequence that can be up to 4 bytes. Why bring up encoding? Because each font has an encoding where character number 178 could return a very different glyph depending on the codepage used by the font. Most font files use Unicode so you have a standard there, but many programs still use specific code pages, where that page is mapped to the font. This is what occurs when you display ABC and the font is Wingdings so you get . So point one is you need to make sure that the encoding you use matches or is mapped to the encoding of the fonts you use. And it gets even more complex. The characters with the values 0xE000 – 0xF8FF are undefined. Each font can make those anything they want (one use is to add the Klingon script). So a character with a value in this range is by definition tied to the font file it is using to display that font. This is how most symbol type fonts work. Read more: Windward Wrocks
Tenacious C
Posted by
jasper22
at
14:24
|
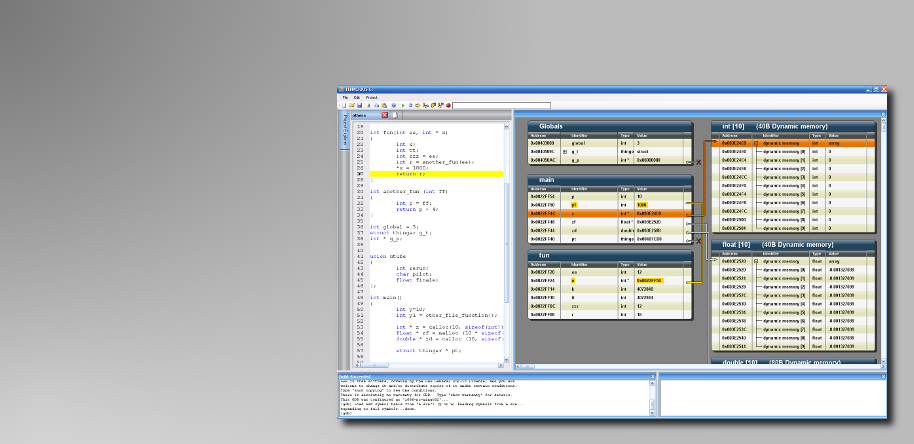
Tenacious C presents pointers and memory in a visual format that makes the hard parts of C ridiculously easy. Read more: Tenacious C
Difference between InnoDB and MyISAM in MySQL
Posted by
jasper22
at
14:21
|
MyISAM and InnoDB are two most commonly used storage engines of MySQL database. However, MyISAM is the default storage engine chosen by MySQL database, when creating a new table. The major differences between these two storage engines are : InnoDB supports transactions which is not supported by tables which use MyISAM storage engine.
InnoDB has row-level locking, relational integrity i.e. supports foreign keys, which is not possible in MyISAM.
InnoDB ‘s performance for high volume data cannot be beaten by any other storage engines available.
Tables created in MyISAM are known to have higher speed compared to tables in InnoDB. But since InnoDB supports volume, transactions, integrity it’s always a better option which you are dealing with a larger database. It is worth mentioning that a single database can have tables of different storage engines. File structure
MyISAM stores each table on disk with three files whose names begin with same as table name. These files have different extensions to differentiate their purpose. A .frm files stores the table format, and a .MYD (MYData) file stores the data of the table. If the table has indexes then these are stored in the .MYI (MYIndex) files. Read more: digimantra
InnoDB has row-level locking, relational integrity i.e. supports foreign keys, which is not possible in MyISAM.
InnoDB ‘s performance for high volume data cannot be beaten by any other storage engines available.
Tables created in MyISAM are known to have higher speed compared to tables in InnoDB. But since InnoDB supports volume, transactions, integrity it’s always a better option which you are dealing with a larger database. It is worth mentioning that a single database can have tables of different storage engines. File structure
MyISAM stores each table on disk with three files whose names begin with same as table name. These files have different extensions to differentiate their purpose. A .frm files stores the table format, and a .MYD (MYData) file stores the data of the table. If the table has indexes then these are stored in the .MYI (MYIndex) files. Read more: digimantra
HTTP Error 404.3: WCF Hostes in IIS. Add a MIME type
Posted by
jasper22
at
14:20
|
Normally when we host a WCF Service in IIS and while browsing we get the following frustrating screen.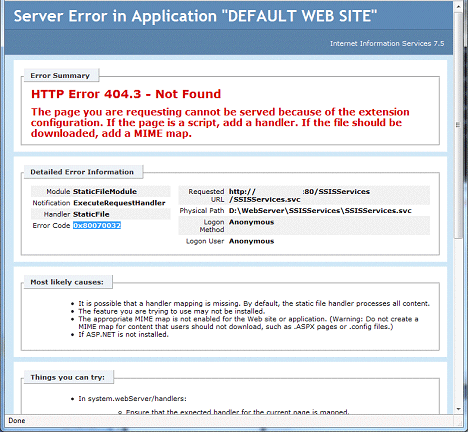
The error message in the above screen is very clear. We need to add MIME type for .SVC extension. To solve above problem
Read more: C# Corner

The error message in the above screen is very clear. We need to add MIME type for .SVC extension. To solve above problem
- Open command prompt as Administrator
- Navigate to C:Windows\Microsoft.Net\Framework\v3.0
Read more: C# Corner
How to Setup Your Java Development Environment in Ubuntu
Posted by
jasper22
at
14:19
|
In this post, I’m going to explain how you can setup a Java development environment (JDK + Eclipse) in Ubuntu. I’m using Ubuntu 10.10, but these steps should be applicable to majority of Ubuntu versions. Let’s start with JDK first.Install Sun JDK:
- Download the Linux version of latest JDK binary from the Oracle website. For Java 6, the file name would be: jdk-6u22-linux-i586.bin
- Copy the downloaded JDK file to a directory where you want to install the JDK. I use /home/<username>/java/jdk-6u22-linux-i586.bin
- Open terminal window and navigate to the directory where you copied the downloaded file. Then type the command: sudo sh jdk-6u22-linux-i586.bin and press enter.
- If it asks for root password, give it and JDK installation will begin. The JDK will be installed on the same directory where the binary is placed.
That’s it. JDK installation is done. But we still have one more step to complete. That is, setting up the JAVA_HOME environment variable.Setting up JAVA_HOME environment variable:
Read more: Javalobby
- Go to Nautilus file browser (Places -> Home Folder) and open this file: “.bashrc”. By default this file is hidden. So, press Ctrl + H which will show all hidden files and then you can see the .bashrc file.
Read more: Javalobby
List all Default Values in a SQL Server Database
Posted by
jasper22
at
14:18
|
I had earlier written a query to Find a Column Default value using T-SQL. Here’s how to find the default value of all columns in all tables of a databaseSELECT obj.name as 'Table', col.name as 'Column',
object_definition(default_object_id) AS [DefaultValue]
FROM sys.objects obj INNER JOIN sys.columns col
ON obj.object_id = col.object_id
where obj.type = 'U'The sys.objects and sys.columns provides us with the metadata needed to find the default values of all columns in a database. Read more: SQL Server curry
object_definition(default_object_id) AS [DefaultValue]
FROM sys.objects obj INNER JOIN sys.columns col
ON obj.object_id = col.object_id
where obj.type = 'U'The sys.objects and sys.columns provides us with the metadata needed to find the default values of all columns in a database. Read more: SQL Server curry
Why does Coded UI Test playback fail to scroll the Silverlight control into view?
Posted by
jasper22
at
14:17
|
Bringing the control into view is an essential part of the UITestAction during Playback since Coded UI Test performs actual Mouse/Keyboard actions on the control instead of programmatic action on the control. In case of failure to bring the control into view, the playback will throw a FailedToPerformActionOnBlockedControl exception or a PlaybackFailure exception. The Coded UI Test playback engine attempts various approaches to bring the control into the physical screen view – - Bring the application window into the screen area
- Set focus on the control.
- Scroll the control into the view port of the container within which it resides. This post focuses on the third approach and the assumptions made in the scrolling logic for Silverlight test automation in Coded UI Test.
To scroll a control into view, the control (or its accessibility peer) should either support the scrolling capability natively, or needs to be residing inside one or more scrollable containers which can then be scrolled in some sequence to bring the control into view. Silverlight controls such as ListBoxItem or ComboBoxItem have their AutomationPeer implement IScrollItemProvider which is used to scroll the item into view. [The ComboBox scroll into view in Coded UI Test is actually done through a select mechanism] Read more: Tapas Sahoo's Blog
- Set focus on the control.
- Scroll the control into the view port of the container within which it resides. This post focuses on the third approach and the assumptions made in the scrolling logic for Silverlight test automation in Coded UI Test.
To scroll a control into view, the control (or its accessibility peer) should either support the scrolling capability natively, or needs to be residing inside one or more scrollable containers which can then be scrolled in some sequence to bring the control into view. Silverlight controls such as ListBoxItem or ComboBoxItem have their AutomationPeer implement IScrollItemProvider which is used to scroll the item into view. [The ComboBox scroll into view in Coded UI Test is actually done through a select mechanism] Read more: Tapas Sahoo's Blog
Top 7 Coding Standards & Guideline Documents For C#/.NET Developers
Posted by
jasper22
at
14:16
|
Some time back, I collated a list of 7 Must Read, Free EBooks for .NET Developers, and a lot of people found it useful. So, I thought about putting together a list of Coding Standard guidelines/checklists for .NET /C# developers as well.
As you may already know, it is easy to come up with a document - the key is in implementing these standards in your organization, through methods like internal trainings, Peer Reviews, Check in policies, Automated code review tools etc. You can have a look at FxCop and/or StyleCop for automating the review process to some extent, and can customize the rules based on your requirements.
Anyway, here is a list of some good Coding Standard Documents. They are useful not just from a review perspective - going through these documents can definitely help you and me to iron out few hidden glitches we might have in the programming portion of our brain.
So, here we go, the listing is not in any specific order.1 – IDesign C# Coding Standards
IDesign C# coding standards is a pretty decent and compact (27 pages) Coding Standards Document. It covers a Naming conventions, Best practices and Framework specific guidelines 2 – Encodo C# Handbook
Encodo C# handbook is bit more recent, and has 72 pages of guidelines on Structure, Formatting, Naming. It also has a ‘Patterns and Best Practices’ section, which is a must read for any .NET/C# developer. Read more: amazedsaint's #tech journal
As you may already know, it is easy to come up with a document - the key is in implementing these standards in your organization, through methods like internal trainings, Peer Reviews, Check in policies, Automated code review tools etc. You can have a look at FxCop and/or StyleCop for automating the review process to some extent, and can customize the rules based on your requirements.
Anyway, here is a list of some good Coding Standard Documents. They are useful not just from a review perspective - going through these documents can definitely help you and me to iron out few hidden glitches we might have in the programming portion of our brain.
So, here we go, the listing is not in any specific order.1 – IDesign C# Coding Standards
IDesign C# coding standards is a pretty decent and compact (27 pages) Coding Standards Document. It covers a Naming conventions, Best practices and Framework specific guidelines 2 – Encodo C# Handbook
Encodo C# handbook is bit more recent, and has 72 pages of guidelines on Structure, Formatting, Naming. It also has a ‘Patterns and Best Practices’ section, which is a must read for any .NET/C# developer. Read more: amazedsaint's #tech journal
10 Dirty Internet Explorer CSS Hacks You Might Not know
Posted by
jasper22
at
14:15
|
IntroductionDisclaimer: The intention of this article is not to encourage to apply this hack to your web projects but to understand what have been using by other web designers/developers. The best way to solve Internet Explorer's CSS layout issue is - create different style sheets for different versions of Internet explorers. Alright, have ever found yourself in this situation, you were trying to update an existing old website, opened CSS file and you saw something that you think it's typo from previous CSS coder - but it's not. There was a CSS file I was trying to update and I saw some asterisks, underscores appear randomly as a prefix in some attributes. Did some search on Google and found out it's Internet explorer hacks! So, the main purpose of this article, is not encourage you to use hacks, but to understand what hacks have been using by others so whenever you update someone else's project you can interpret the CSS file better. :) Alright, I have collected 10 of them start from IE8 to........ IE5.0! 1. IE 8.color {color: #f00/;} 2. IE 7*+html .box {background:#fff;}
*:first-child+html .box {background:#fff;} 3. IE 7 and below*:first-child+html {} * html {} 4. IE 7 and below .box {
*background: #f00;
} 5. IE 6 only.box {
_background/**/:/**/ #f00;
} Read more: Queness
*:first-child+html .box {background:#fff;} 3. IE 7 and below*:first-child+html {} * html {} 4. IE 7 and below .box {
*background: #f00;
} 5. IE 6 only.box {
_background/**/:/**/ #f00;
} Read more: Queness
Reversing the source of the ZeroAccess crimeware rootkit
Posted by
jasper22
at
14:14
|
We recently undertook a project to update the hands-on labs in our Reverse Engineering Malware course, and one of our InfoSec Resources Authors, Giuseppe "Evilcry" Bonfa, defeated all of the anti-debugging and anti-forensics features of ZeroAccess and traced the source of this crimeware rootkit: Part 1InfoSec Institute would classify ZeroAccess as a sophisticated, advanced rootkit. It has 4 main components that we will reverse in great detail in this series of articles. ZeroAccess is a compartmentalized crimeware rootkit that serves as a platform for installing various malicious programs onto victim computers. It also supports features to make itself and the installed malicious programs impossible for power-users to remove and very difficult security experts to forensically analyze. At the conclusion of the analysis, we will trace the criminal origins of the ZeroAccess rootkit. We will discover that the purpose of this rootkit is to set up a stealthy, undetectable and un-removable platform to deliver malicious software to victim computers. We will also see that ZeroAccess is being currently used to deliver FakeAntivirus crimeware applications that trick users into paying $70 to remove the “antivirus”. It could be used to deliver any malicious application, such as one that steals bank and credit card information in the future. Further analysis and network forensics supports that ZeroAccess is being hosted and originates from the Ecatel Network, which is controlled by the cybercrime syndicate RBN (Russian Business Network).
Read more: Offensive Computing
Read more: Offensive Computing
Visual Guide to NoSQL Systems
Posted by
jasper22
at
14:12
|
There are so many NoSQL systems these days that it's hard to get a quick overview of the major trade-offs involved when evaluating relational and non-relational systems in non-single-server environments. I've developed this visual primer with quite a lot of help (see credits at the end), and it's still a work in progress, so let me know if you see anything misplaced or missing, and I'll fix it. Without further ado, here's what you came here for (and further explanation after the visual).Note: RDBMSs (MySQL, Postgres, etc) are only featured here for comparison purposes. Also, some of these systems can vary their features by configuration (I use the default configuration here, but will try to delve into others later).
How to make sharing code between .NET and Silverlight (a little) less painful
Posted by
jasper22
at
14:10
|
Windsor ships for both .NET and Silverlight. However working with the codebase in such a way that we can target both runtimes at the same time with the least amount of friction possible proved to be quite a challenge. Problem
We’re using single .sln and .csproj files to target both runtimes (actually 5 of them, as we ship for 3 versions of .NET and 2 versions of Silverlight, but I digress) with some heavy (and I mean- really heavy) Jedi trickery in MsBuild by Roelof. We’re using conditional compilation to cater for incompatibilities between frameworks. For example, SerializableAttribute and NonSerializedAttribute are not present in Silverlight, so many of our classes look like this: #if !SILVERLIGHT
[Serializable]
#endif
public class ParameterModel
{
// some code here
}This is quite cluttering the code making it harder to read. It adds friction to the process, since I have to remember each time to exclude the attribute from Silverlight build. Even more annoying is the fact, that ReSharper is not very fond of pre-processor directives in code, and certain features, like code clean up and reordering don’t really work the way they should. Solution
I figured out a way to cut the need to use conditional compilation in this case. So that I can write the code like this:[Serializable]
public class ParameterModel
{
// some code here
}and still have it compile properly under Silverlight, outputting exactly the same code as the first sample. How you ask? – using a not very well known feature of .NET BCL – ConditionalAttribute.Read more: Krzysztof Kozmic
We’re using single .sln and .csproj files to target both runtimes (actually 5 of them, as we ship for 3 versions of .NET and 2 versions of Silverlight, but I digress) with some heavy (and I mean- really heavy) Jedi trickery in MsBuild by Roelof. We’re using conditional compilation to cater for incompatibilities between frameworks. For example, SerializableAttribute and NonSerializedAttribute are not present in Silverlight, so many of our classes look like this: #if !SILVERLIGHT
[Serializable]
#endif
public class ParameterModel
{
// some code here
}This is quite cluttering the code making it harder to read. It adds friction to the process, since I have to remember each time to exclude the attribute from Silverlight build. Even more annoying is the fact, that ReSharper is not very fond of pre-processor directives in code, and certain features, like code clean up and reordering don’t really work the way they should. Solution
I figured out a way to cut the need to use conditional compilation in this case. So that I can write the code like this:[Serializable]
public class ParameterModel
{
// some code here
}and still have it compile properly under Silverlight, outputting exactly the same code as the first sample. How you ask? – using a not very well known feature of .NET BCL – ConditionalAttribute.Read more: Krzysztof Kozmic
Automating Windows Applications Using the WCF Equipped Injected Component
Posted by
jasper22
at
14:07
|
- NotepadPlugin.dll in injected into the target process with remote thread technique by Injector COM object. This is a worker thread, and its function is DllMain() of NotepadPlugin.dll. Remote thread ends after DllMain() returns. Injector COM object is instantiated by AutomationClientNET application running as a local client. Its purpose is to find a running target Notepad process (or to start a new one if there is no already running Notepads) and to inject plug-in into the target process. After NotepadPlugin.dll injection, the Injector is no longer used and may be released. Injector is used by only one local client, below referred to as Client-Injector.
- NotepadPlugin.dll subclasses outer and inner windows of target application with FrameWndProc() and ViewWndProc() window procedures respectively. These window procedures contain message handlers with new functionality for the target application. Function PluginProc() (called by DllMain()) of the NotepadPlugin.dll actually performs the subclassing. Both NotepadPlugin.dll and Injector use helper WindowFinder COM object to find Notepad windows.
- Function PluginProc() of NotepadPlugin.dll running in remote thread, posts a user-registered WM_CREATE_OBJECT Windows message to the Notepad frame window. FrameWndProc() window procedure handles WM_CREATE_OBJECT message. The handler creates a managed NotepadHandlerNET object using its COM wrapper.
Extended WPF Toolkit–Updated ColorPicker control
Posted by
jasper22
at
14:05
|
If you are using the Extended WPF Toolkit you have probably noticed the ColorPicker control. If you are not familiar with the Color Picker control, it is simply a WPF editor control that allows a user to select a color. If you are using release version 1.2 or less the color picker will look something like this: 
Read more: <elegantc*de>

Read more: <elegantc*de>
בלעדי! כל הפרטים על התקנת DENALI!
Posted by
jasper22
at
14:04
|
עלק בלעדי.
בנקודה הזאת אני בטוח שכל אחד מכם כבר הוריד את Denali, התקין, ויודע בעל פה את הסינטקס של יצירת Availability groups.
לא?
אז לכל מי שהיה לו יותר חשוב להתעסק בלחפש כורסת טלוויזיה טובה עם מסז’ ולא לכלך את הידיים עם המוצר שבסך הכל הולך לקבוע את עתידו המקצועי ובעקבות כך הכלכלי, האישי והחברתי בשנים הקרובות, קבלו את ההתקנה בתמונות:
מסך ההתקנה הראשי, זה שאף ישראלי מעולם לא קרא:
Adobe Acrobat X
Posted by
jasper22
at
14:03
|
Adobe Acrobat X has just been released! And continuing in our tradition of providing the direct download links for major Adobe software such as CS5, Lightroom 3, and Elements 9, below you’ll find the direct links for the brand new Acrobat X (10)… We also have added the direct links (DDL) for the previous version Acrobat 9 as well, in case you need them for any reason. The links given below go to the authentic and secure files residing on Adobe’s servers, are guaranteed genuine and will not change. They are especially useful when you are unable to download Adobe’s products via other means – often due to difficulties with the Akamai Download Manager (the Adobe DLM). With the links provided below, you can use your browser’s download capability, or another download manager of your choice. The links are listed below. For Windows, the Acrobat X Pro download is in the form of a single .exe file. For the Mac, unfortunately, “a trial version of Acrobat X Pro for Mac OS is not available at this time” (however the full product is available for Mac, see the FAQ). There is no actual trial version of Acrobat X Standard, but Pro includes all Standard features – so you can try out Pro for free and then decide which version you want at the time of purchase. Read more: ProDesignTools
Pure virtual destructors in C++
Posted by
jasper22
at
14:02
|
To work correctly, classes with virtual methods must also have virtual destructors. Interestingly, virtual destructors can be declared pure, which can be useful in some cases.Imagine you have a base class you want to make abstract. In this base class all methods have meaningful default implementations, and you want to allow the derived classes to inherit them as-is. However, to make a class abstract, at least one of its methods must be made pure virtual, which means the derived classes must override it. How do you make the class abstract in this case? The answer is: declare the destructor pure virtual. This will make your class abstract without forcing you to declare any other method pure virtual.// Abstract base class - can't be instantiated
//
class Base
{
public:
virtual ~Base() = 0;
virtual void method();
};Base::~Base()
{
// Compulsory virtual destructor definition,
// even if it's empty
}void Base::method()
{
// Default implementation.
// Derived classes can just inherit it, if needed
}// We can now derive from Base, inheriting the
// implementation of method()
//
class Derived : public Base
{
public:
~Derived()
{}
};
While defining (providing an implementation) pure virtual methods is rarely useful, you must define a pure virtual destructor. This is because the destructor of a base class is always called when a derived object is destroyed. Failing to define it will cause a link error. Read more: Eli Bendersky's Website
//
class Base
{
public:
virtual ~Base() = 0;
virtual void method();
};Base::~Base()
{
// Compulsory virtual destructor definition,
// even if it's empty
}void Base::method()
{
// Default implementation.
// Derived classes can just inherit it, if needed
}// We can now derive from Base, inheriting the
// implementation of method()
//
class Derived : public Base
{
public:
~Derived()
{}
};
While defining (providing an implementation) pure virtual methods is rarely useful, you must define a pure virtual destructor. This is because the destructor of a base class is always called when a derived object is destroyed. Failing to define it will cause a link error. Read more: Eli Bendersky's Website
WPF - DoEvents like Windows Forms
Posted by
jasper22
at
14:01
|
בגלל ארכיטקטורה שונה אין ב WPF את הפונקציה DOEVENT
להלן הקוד ל WPF:
public static void DoEvents(){
// Create new nested message pump.
DispatcherFrame nestedFrame = new DispatcherFrame();// Dispatch a callback to the current message queue, when getting called,
// this callback will end the nested message loop.
// note that the priority of this callback should be lower than the that of UI event messages.
DispatcherOperation exitOperation = Dispatcher.CurrentDispatcher.BeginInvoke(DispatcherPriority.Background, exitFrameCallback, nestedFrame);// pump the nested message loop, the nested message loop will immediately
// process the messages left inside the message queue.
Dispatcher.PushFrame(nestedFrame);// If the "exitFrame" callback doesn't get finished, Abort it.
if (exitOperation.Status != DispatcherOperationStatus.Completed)
{
exitOperation.Abort();
}}Read more: Uzi Drori's Blog
Shared Application Settings in machine.config
Posted by
jasper22
at
11:59
|
BackgroundApplication behavior frequently depends on exogenous parameters, such as a service URI or file paths, that are supplied by a developer or administrator. These inputs must be amenable to quick change without the need to refactor or recompile. A common answer to this requirement is to place such inputs in a configuration file: app.config for Windows applications or web.config for web applications. When settings are stored in an xml file, an administrator can easily edit them as needed. This solution works well for a single application. .NET architecture also provides a way for multiple applications to access shared settings. As a simple example of when this may be desirable, suppose you have some functionality that needs to be exposed via a command-line interface, a GUI and a web app. Since only the interfaces are different but the functionality is the same, there is a good case to pool the settings into one place. When the applications are on the same machine, their shared settings can be stored in the machine.config file. As you probably already know, you can add an <appSettings> element to a configuration file to contain custom data that your applications need. However, all data in appSettings is stored as strings and is exposed by the framework as a NameValueCollection, which is suboptimal for a number of reasons. In the next sections, I demonstrate a better solution. Solution Overview.NET already has a good alternative to appSettings, and it has a similar name: Application Settings. In contrast to appSettings, application settings are exposed as class properties, which permits them to be strongly typed, easily refactored and used in bindings. However, by default application settings are saved to app.config instead of machine.config and are accessible only within the assembly. The solution is to move the settings out of app.config into machine.config and make the class that exposes them visible outside the assembly. Multiple applications can then access these settings by simply referencing the assembly. Step-by-Step Guide1. Create a new class libraryFor this example, I started with an empty Visual Studio solution and created a new class library project, which I named Netrudder, to serve as a base reference for projects in the same namespace. 2. Add settingsAdd a new Settings template to the project. I named mine NetrudderSettings.
Open the new .settings file. The Settings Designer comes up.
Add your settings. Make sure to assign correct Type, and to change scope from User to Application.
Change Access Modifier to Public. This affects the visibility of the class whose properties map to the settings. It was created for us alongside the .settings file.
Save the project.Read more: Codeproject
Open the new .settings file. The Settings Designer comes up.
Add your settings. Make sure to assign correct Type, and to change scope from User to Application.
Change Access Modifier to Public. This affects the visibility of the class whose properties map to the settings. It was created for us alongside the .settings file.
Save the project.Read more: Codeproject
10 Best Server Monitoring Tools That Kick Ass
Posted by
jasper22
at
11:27
|
Blogger always prefer front end tools; Although Developers and designers are also worried about handling website. They have to make sure that website script looks fine from backend. Sometimes, it would be difficult to identify the problems. Most of the time physical machine is not optimized and use a lot of resources of website. It would be trouble to take full advantage for working effectively. A perfectly managed and healthy hosting server rests at the heart of any great website. As a Webmaster, You have to be alert and closely monitor the performance of your server to avoid any downtime or failures. We have identified few parameters that need to be monitored, that became the cause of the failure of server downtime. CPU utilization
Server RAM
Physical temperature of the Server and its various components
Bandwidth usage
Disk space usage
Keeping these factors, we’ve collected 10 Top Monitoring Tools that will keep your server in perfect form and provide the security, healthy, resolve overloading server, low performance and configuration problems as well. 1) Load Impact : Load Impact is useful online tool to evaluate your site and server performance. You can test the amount of concurrent visitors and connections that is handling by your server. Sometimes, you have problem of downtime problem of from your server. This is a due to getting a sudden traffic from stumbleupon, digg, or reddit. This tool helps you to help move into new machine. This tool provide two types of services either you take fee or professional service from them. 2) Simple Server Monitor: It is another stunning tool for measuring the uptime or downtime of your website in percentage. If your server starts slowing or unresponsive, you will receive a message. You can check the performance of server like any failure or losses instant.
Read more: Smashinghub
Server RAM
Physical temperature of the Server and its various components
Bandwidth usage
Disk space usage
Keeping these factors, we’ve collected 10 Top Monitoring Tools that will keep your server in perfect form and provide the security, healthy, resolve overloading server, low performance and configuration problems as well. 1) Load Impact : Load Impact is useful online tool to evaluate your site and server performance. You can test the amount of concurrent visitors and connections that is handling by your server. Sometimes, you have problem of downtime problem of from your server. This is a due to getting a sudden traffic from stumbleupon, digg, or reddit. This tool helps you to help move into new machine. This tool provide two types of services either you take fee or professional service from them. 2) Simple Server Monitor: It is another stunning tool for measuring the uptime or downtime of your website in percentage. If your server starts slowing or unresponsive, you will receive a message. You can check the performance of server like any failure or losses instant.
Read more: Smashinghub
Subscribe to:
Comments (Atom)




