Read more: EricLaw's IEInternals
Understanding the IE9 Software Rendering Mode
I recently heard from some users who are seeing lower-than-expected scores on the Speed Reading and FishIE Tank benchmarks. I went to check these tests myself and found that my laptop’s score was low. In fact, it was much lower than I’d seen last year. What happened? First, a bit of background: These graphically rich demos are designed to use your PC’s Graphics Processing Unit (GPU) instead of the Central Processing Unit (CPU) to do most of the heavy lifting. Generally speaking, a faster GPU will give better performance than a slower GPU. However, there are cases where the GPU is not used for rendering, and instead the CPU is used. The primary case where this occurs is when the GPU has an outdated driver version which is not supported by the browser. In those cases, the browser will use software emulation mode, forcing the CPU to do the work instead of the GPU. You can determine whether Internet Explorer 9 is in software mode by clicking Tools > Internet Options > Advanced. The first checkbox in the list indicates whether IE9 is running in software mode.
Read more: EricLaw's IEInternals
Read more: EricLaw's IEInternals
Signature Box that Makes the Signature Look Right
Posted by
jasper22
at
12:45
|
IntroductionHave you ever noticed how childish and imprecise your signature looks when you write your name in a handheld signature box? The small size of the stylus compared to a standard pen, the nearly frictionless stylus-on-touch-screen interaction and the fact that the handheld is often hanging in the air instead of firmly lying on a table are three physical explanations for these ugly signatures. Another reason is the frequent input errors that are sent to your control from the touch screen. Those errors may vary between 1 and 4 pixels. Unnoticeable when clicking in the middle of a button, they are a pest when sampled in a signature box. By lowering the sampling rate and using Bézier curve interpolation, it's possible to reduce the impact of all these factors. 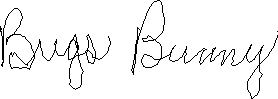
Read more: Codeproject
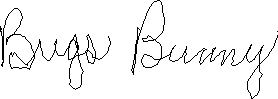
Read more: Codeproject
What is the difference between a directory and a folder?
Posted by
jasper22
at
12:44
|
Windows 95 introduced Windows Explorer and along with it the term folder. What is the relationship between folders and directories?Some people believe that Windows 95 renamed directories to folders, but it's actually more than that. Windows Explorer lets you view folders, which are containers in the shell namespace. Directories are one type of folder, namely, folders which correspond to file system locations. There are other types of folders, such as Control Panel or Network Neighborhood or Printers. These other types of folders represent objects in the shell namespace which do not correspond to files. Read more: The old new thing
10 Reasons to Say “No” to Cloud Computing ?
Posted by
jasper22
at
12:41
|
I have been writing about the benefits of migrating to the Cloud in previous articles but it is also important to highlight in which circumstances the Cloud Computing route may not be the appropriate one. Building on some answers to a similar question asked on Quora , here is a list in no specific order of ten good reasons why Public Cloud Computing may not be a good fit for your company:1) You drive a competitive advantage from the IT capabilities you are considering migrating 2) The IT capability or service you are considering moving is a mission critical aspect of your business3) You operate under stringent government data security requirements (HIPAA and FISMA in the US) 4) You handle sensitive data and need to control incident responses, eDiscovery and forensic investigations 5) You need to deploy complex enterprise class applications6) Your IT organization has not sufficient maturity to govern the additional complexity of managing additional processes and outside contracts brought by Cloud Computing 7) You run “big data” applications (i.e., financial) that require extremely low latency and/ or extreme disk I/O requirements
Read more: GetApp
Read more: GetApp
11 GPG Commands One Should NEVER Forget
Posted by
jasper22
at
12:30
|
GnuPG is the GNU project's complete and free implementation of the OpenPGP standard as defined by RFC4880 . GnuPG allows to encrypt and sign your data and communication, features a versatile key management system as well as access modules for all kinds of public key directories. 1. Create GPG Keys
$ gpg --gen-key 2. List the available keys in your keyring
$ gpg --list-keys 3. Exporting the public key - by user id
$ gpg --armor --export <uid>
Example :
$ gpg --armor --export prabath@wso2.com 4. Importing a public key of a trusted user to your keyring
$ gpg --import wso2.gpg 5. Encrypting a document - you need to import the public key corresponding to the uid-of-recipient first in to your keyring as per step - 4.
$ gpg --output <output-file> --encrypt --recipient <uid-of-recipient> <input-file>
Example :
$ gpg --output test.txt.gpg --encrypt --recipient prabath@wso2.com test.txt Read more: F A C I L E L O G I N
$ gpg --gen-key 2. List the available keys in your keyring
$ gpg --list-keys 3. Exporting the public key - by user id
$ gpg --armor --export <uid>
Example :
$ gpg --armor --export prabath@wso2.com 4. Importing a public key of a trusted user to your keyring
$ gpg --import wso2.gpg 5. Encrypting a document - you need to import the public key corresponding to the uid-of-recipient first in to your keyring as per step - 4.
$ gpg --output <output-file> --encrypt --recipient <uid-of-recipient> <input-file>
Example :
$ gpg --output test.txt.gpg --encrypt --recipient prabath@wso2.com test.txt Read more: F A C I L E L O G I N
Изоляция служб в Windows
Posted by
jasper22
at
12:26
|
Как известно, службы Windows представляют собой одно из наиболее излюбленных мест для атак на операционную систему. В худшем (для нас, конечно) случае атакующий получает возможность действовать на атакованном компьютере в контексте учетной записи, от имени которой запущена взломанная служба. И если эта учетная запись обладает административными правами, то фактически злоумышленник получает полный контроль над компьютером. От версии к версии в Windows появляются новые механизмы, обеспечивающие дополнительную изоляцию служб и, как следствие, усиливающие безопасность системы в целом. Я хотел бы вкратце рассмотреть, что принципиально изменилось в этом направлении за последние несколько лет. Первые существенные изменения в механизмах защиты служб появились в Windows XP Service Pack 2. Сейчас уже сложно себе это представить, но до выхода SP2 все службы самой операционной системы запускались в контексте встроенной учетной записи Local System, обладающей на компьютере максимально полными административными правами. SP2 добавил еще две записи: Local Service и Network Service. Принципиальные отличия трех перечисленных записей можно найти в табл. 1. Read more: Habrahabr.ru
Structure Initialization in C#
Posted by
jasper22
at
12:25
|
Structure in C# allows us to group the variables and methods. Its some what similar to classes but that's not true there are no. of difference between class and structure. But here in this post I am not going to discuss about that, here I am going to explain how to Initialize Structure. Facts:
1. Structure is Value type.
2. D# oesn't allows to create parameter less constructor because its initialize the variable with the default values. Now consider the below case where I have created two structure
structure 1 : with the public members.public struct StructMember
{
public int a;
public int b;
}structure 2 : with the properties.public struct StructProperties
{
private int a;
private int b; public int A
{
get
{ return a; }
set
{ a = value; }
} public int B
{
get
{ return b; }
set
{ b = value; }
}
} Now by considering above two facts in mind and I tried to use the both the structure as below public class MainClass
{
public static void Main()
{
StructMembers MembersStruct; StructProperties PropertiesStruct;
MembersStruct.X = 100;
MembersStruct.Y = 200; PropertiesStruct.X = 100;
PropertiesStruct.Y = 200;
}
}After doing this when I tried to compile the code I received below error the C# compiler issues the following error: error CS0165: Use of unassigned local variable 'PropertiesStruct'So by this C# compiler informs that it allow to use the first structure without an error but not allow to use second structure which exposed property. Read more: Mind Solutions
1. Structure is Value type.
2. D# oesn't allows to create parameter less constructor because its initialize the variable with the default values. Now consider the below case where I have created two structure
structure 1 : with the public members.public struct StructMember
{
public int a;
public int b;
}structure 2 : with the properties.public struct StructProperties
{
private int a;
private int b; public int A
{
get
{ return a; }
set
{ a = value; }
} public int B
{
get
{ return b; }
set
{ b = value; }
}
} Now by considering above two facts in mind and I tried to use the both the structure as below public class MainClass
{
public static void Main()
{
StructMembers MembersStruct; StructProperties PropertiesStruct;
MembersStruct.X = 100;
MembersStruct.Y = 200; PropertiesStruct.X = 100;
PropertiesStruct.Y = 200;
}
}After doing this when I tried to compile the code I received below error the C# compiler issues the following error: error CS0165: Use of unassigned local variable 'PropertiesStruct'So by this C# compiler informs that it allow to use the first structure without an error but not allow to use second structure which exposed property. Read more: Mind Solutions
Пишем игру для Android. Часть 3. Управление игровыми объектами
Posted by
jasper22
at
12:23
|
В этой статье мы рассмотрим две темы: управление игровыми объектами и их взаимодействие. Мячик у нас уже летает, осталось сделать, чтобы он отражался от стен и ракеток; также стоит реализовать управление нижней ракетки игроком, а верхней — неким алгоритмом. Итак, приступим.Движение мячикаДля начала добавим в GameObject следующие полезные функции:GameObject.java/** Верхняя граница объекта */
public int getTop() { return mPoint.y; } /** Нижняя граница объекта */
public int getBottom() { return mPoint.y + mHeight; } /** Левая граница объекта */
public int getLeft() { return mPoint.x; } /** Правая граница объекта */
public int getRight() { return mPoint.x + mWidth; } /** Центральная точка объекта */
public Point getCenter() { return new Point(mPoint.x + mWidth / 2, mPoint.y + mHeight / 2); } /** Высота объекта */
public int getHeight() { return mHeight; } /** Ширина объекта */
public int getWidth() { return mWidth; } /** @return Прямоугольник, ограничивающий объект */
public Rect getRect() { return mImage.getBounds(); } /** Проверяет, пересекаются ли два игровых объекта */
public static boolean intersects(GameObject obj1, GameObject obj2)
{
return Rect.intersects(obj1.getRect(), obj2.getRect());
}
Игровые объекты ничего не знают ни о друг друге, ни об игровом поле, поэтому все столкновения будут обрабатываться GameManager-ом. Итак, рассмотрим сначала такую ситуацию:
Read more: Virtual Reality Online
public int getTop() { return mPoint.y; } /** Нижняя граница объекта */
public int getBottom() { return mPoint.y + mHeight; } /** Левая граница объекта */
public int getLeft() { return mPoint.x; } /** Правая граница объекта */
public int getRight() { return mPoint.x + mWidth; } /** Центральная точка объекта */
public Point getCenter() { return new Point(mPoint.x + mWidth / 2, mPoint.y + mHeight / 2); } /** Высота объекта */
public int getHeight() { return mHeight; } /** Ширина объекта */
public int getWidth() { return mWidth; } /** @return Прямоугольник, ограничивающий объект */
public Rect getRect() { return mImage.getBounds(); } /** Проверяет, пересекаются ли два игровых объекта */
public static boolean intersects(GameObject obj1, GameObject obj2)
{
return Rect.intersects(obj1.getRect(), obj2.getRect());
}
Игровые объекты ничего не знают ни о друг друге, ни об игровом поле, поэтому все столкновения будут обрабатываться GameManager-ом. Итак, рассмотрим сначала такую ситуацию:

Changing a SQL Server Database Owner
Posted by
jasper22
at
12:22
|
Fact: every SQL Server database has an "owner". You can check the owner of a database by running this query:SELECT NAME, SUSER_SNAME(owner_sid)
FROM sys.databases
WHERE NAME = 'DatabaseName' However, there may come a day when you run into this error:There was error outputting database level information for ServerName.DatabaseName.
Property Owner is not available for Database '[DatabaseName]'. This property may not exist for this object, or may not be retrievable due to insufficient access rights. When you log into SQL Server Management Studio, right-click the database, and select Properties, you'll see this dialog box:
Without a database owner, you can't view the database properties. You may run into issues executing sp_helpdb. You may get an error using "EXECUTE AS OWNER". How do you fix this?The Old Way: sp_changedbowner Normally, I would use sp_changedbowner. Why? It’s familiar. It’s comfortable, like my favorite socks. But there’s a new way, and it’s time for me to learn that. (Also, Microsoft has indicated it will be removed in a future version.) The New Way: ALTER AUTHORIZATIONI had to fumble around a bit to find this command. I am familiar with using ALTER DATABASE SET… to change many database facets. However, in looking through Books Online, I didn’t see a way to use this to change the database owner. I dug a little further, and found ALTER AUTHORIZATION. The BOL syntax is:ALTER AUTHORIZATION
ON [ class_type:: ] entity_name
TO { SCHEMA OWNER | principal_name }
Read more: LessThanDot
FROM sys.databases
WHERE NAME = 'DatabaseName' However, there may come a day when you run into this error:There was error outputting database level information for ServerName.DatabaseName.
Property Owner is not available for Database '[DatabaseName]'. This property may not exist for this object, or may not be retrievable due to insufficient access rights. When you log into SQL Server Management Studio, right-click the database, and select Properties, you'll see this dialog box:

Without a database owner, you can't view the database properties. You may run into issues executing sp_helpdb. You may get an error using "EXECUTE AS OWNER". How do you fix this?The Old Way: sp_changedbowner Normally, I would use sp_changedbowner. Why? It’s familiar. It’s comfortable, like my favorite socks. But there’s a new way, and it’s time for me to learn that. (Also, Microsoft has indicated it will be removed in a future version.) The New Way: ALTER AUTHORIZATIONI had to fumble around a bit to find this command. I am familiar with using ALTER DATABASE SET… to change many database facets. However, in looking through Books Online, I didn’t see a way to use this to change the database owner. I dug a little further, and found ALTER AUTHORIZATION. The BOL syntax is:ALTER AUTHORIZATION
ON [ class_type:: ] entity_name
TO { SCHEMA OWNER | principal_name }
Read more: LessThanDot
Agile Startups – 5 Must-Have Characteristics for a Startup
Posted by
jasper22
at
12:20
|
We love startups.Especially technology startups. As a startup ourselves, Agile Scout works and runs like a lean-startup.
A question was posed to the Agile Scout as to what we look for in an individual who wants to be part of a startup. Here’s our answer:
A question was posed to the Agile Scout as to what we look for in an individual who wants to be part of a startup. Here’s our answer:
Top 5 Characteristics of a Startup Person
- Enthusiasm – Does the team and leadership of the team LOVE what they do. Are they saturated in it and absolutely ooze their product or company. Take Apple fan-boys for example. They love Apple. You just KNOW it when you see it.
- Expertise – Does the team and leadership know their domain-space. Meaning, do they know their market? Are these guys thought leaders? Are they active in their community (i.e. Software development community). Are they using social media? Are they the best ruby developers working together? Even to the point if some of them are avid bloggers or writers. These guys have to continue to love their craft. Grow themselves personally for the company.
- Know their Mission – Does the team and leadership share the same values and mission for the company? Could you pull any of the guys off the team and ask them what the mission and vision for their product is. You should get 100% of the same answers from any of the team members. Then you know they’re working together and understand the core of their business.
- Know the Plan – What is the 3-6-9-12 month plan? What iterative development plans do they have to build the next great features for the product? How are they taking community feedback and incorporating it into their next build? What are lessons learned that they have taken to heart and have learned from? Plans change, we understand that. But there has to be some plans in place.
- Who are they listening to? – This is the absolutely most crucial part. Working in a vacuum doesn’t help a company. Who is on their board? If they don’t have one, what thought leaders are they going to for advice? Who are they listening to? Who advises them on their product? Who are they leveraging to help them build the best product they can? This is crucial. A wise man once said that plans fail from lack of counsel. This is absolutely true with web development and web product development.
**Notice we didn’t talk about having a stand-out product or something that is niche. Tons of cool products come out all the time. Some have already been done. A solid team can make something that’s been done before look even better. With correct strategies in place you can make the next facebook, next twitter. Why? Because your team know’s it’s core business and can build something great from it. It’s just a matter of time before some code-savvy entrepreneurs come along and make the next Facebook. Read more: Agile scout
Bugzilla 4.0 launches out of beta
Bugzilla, Mozilla's bug-tracking system, has just hit version 4.0. While version 4 has been in beta for a while now, it's been 4 years since the stable release of version 3, which has now been declared EOL (End Of Life) and will no longer be supported. Bugzilla 4.0 comes packing quite a few new features and improvements over 3.x. Here are the highlights:
Read more: DownloadSquad
- Automatic duplicate detection for bug fillings
- Redesigned and simplified UI for the advanced search
- Redesigned attachment details UI
- Autocomplete for both usernames and keywords
- New default status workflow (Unconfirmed > Confirmed > In Progress > Resolved > Verified)
- CSS and Javascript updates for users now automatic
- WebService enhancements to bring into line with the Web interface
Read more: DownloadSquad
Read more: Bugzilla
¡Increíble! Google Turns Your Android Phone Into An On-The-Fly Conversation Interpreter
Posted by
jasper22
at
11:33
|

When it came to translations, you used to either need an interpreter or a book to navigate another language. That was either costly or cumbersome, respectively. Then the Internet came along and made things significantly easier. Except you had to be chained to your computer to translate something. A year ago, Google made things easier again by launching their Translate app for Android. But that’s nothing compared to what they’re releasing today. The latest version of Google Translate for Android comes with a few updates to celebrate the one-year anniversary. Most of these are to the user interface. But there’s also one new feature they’re previewing in alpha mode. And it’s awesome: Conversation Mode. Essentially, this allows you to speak in one language into your phone and the app will read it out loud translated into the language of the person you’re speaking with. That person can then respond and it will translate it back into your language. Yes, amazing. Read more: Techcrunch
Google To Merge Honeycomb and Gingerbread
Posted by
jasper22
at
11:25
|
In Barcelona, Google's Eric Schmidt has been revealing future plans for Google, saying that the next release will merge smartphone and tablet versions of its mobile operating system Android. Aside from bragging about Android's growth, Schmidt tiptoed around a question of Google acquiring Twitter, instead offering the very nebulous statement that YouTube doubled its revenues last year Read more: Slashdot
Please Help Me Understand the Android Releases
Posted by
jasper22
at
11:23
|
So, Google's CEO said something about a new version, but it's coming after Android 3.0 ("Honeycomb"), and it ties in with Android 2.3 ("Gingerbread'), which really hasn't moved out yet, and might also update. So, uh, what's going on with Android, exactly? Help me make sense of all these desserts! Sincerely,
Astonished by AndroidDear Astonished,Here's our best shot at deciphering the official statements made by Eric Schmidt at today's Mobile World Congress, statements made here and there by Android workers, and less-than-official bits and pieces that help color in some of this rather crowded, abstract picture.
The Majority of Android Phones, Right Now, Are Running Android 2.2, "Froyo"A bit over half of all Android devices are running Android 2.2, also known as "Froyo." That's based on Google's reporting, itself based on devices that have accessed the Market (even if only for app update checks in the background) within the last two weeks. The second largest share is Android 2.1, "Eclair," with just over 30 percent. Android 2.1 is technically an update to Android 2.0, which also falls under the "Eclair" name, but that's a separate bit of confusion that's in the past now. Android 2.3 "Gingerbread" Is Technically Released, But Barely AvailableLess than one percent of devices are running Android 2.3, because it's only available on the Nexus S (available only on T-Mobile in the U.S.), or to Android users who have installed unofficial, third-party firmware on their device (a.k.a. "rooting").
Read more: Lifehacker
Astonished by AndroidDear Astonished,Here's our best shot at deciphering the official statements made by Eric Schmidt at today's Mobile World Congress, statements made here and there by Android workers, and less-than-official bits and pieces that help color in some of this rather crowded, abstract picture.
The Majority of Android Phones, Right Now, Are Running Android 2.2, "Froyo"A bit over half of all Android devices are running Android 2.2, also known as "Froyo." That's based on Google's reporting, itself based on devices that have accessed the Market (even if only for app update checks in the background) within the last two weeks. The second largest share is Android 2.1, "Eclair," with just over 30 percent. Android 2.1 is technically an update to Android 2.0, which also falls under the "Eclair" name, but that's a separate bit of confusion that's in the past now. Android 2.3 "Gingerbread" Is Technically Released, But Barely AvailableLess than one percent of devices are running Android 2.3, because it's only available on the Nexus S (available only on T-Mobile in the U.S.), or to Android users who have installed unofficial, third-party firmware on their device (a.k.a. "rooting").
Read more: Lifehacker
VMware put an Android in your Android, so you can VM while you VM
Posted by
jasper22
at
11:22
|
So apparently VMware heard you like virtualization (or at least, that corporations do), so it made an Android virtual machine that can run inside Android's own Dalvik VM. The idea being, of course, that busy corporate types could play all night on their nifty new Android superphones, but still be able to dive into a minimalist, business-first environment with one tap when it's time to go to work. Judging from the video that our cohorts at Engadget posted earlier today, the whole thing seems to be pretty awesome, even if it is only working on an LG phone for the time being. Read more: DownloadSquad
Remote Bug Found In Ubuntu Kerberos
Posted by
jasper22
at
11:22
|
There's a remote vulnerability in the Kerberos implementation in several versions of Ubuntu, which could allow an attacker to cause a denial-of-service on vulnerable servers. The bug is in Ubuntu 8.04, Ubuntu 9.10, Ubuntu 10.04 and Ubuntu 10.10. The bug is in the Ubuntu implementation of the Kerberos authentication protocol. Ubuntu has released a slew of new packages to fix the flaw. The group said that in most cases, a normal system update will add the new fixes. Read more: Slashdot
Add the 2D Version of the New Unity Interface to Ubuntu 10.10 and 11.04
Posted by
jasper22
at
11:03
|
Is your computer or virtualization software unable to display the new 3D version of the Unity Interface in Ubuntu? Now you can access and enjoy the 2D version with just a little PPA magic added to your system! To add the new PPA open the Ubuntu Software Center, go to the Edit Menu, and select Software Sources. Access the Other Software Tab in the Software Sources Window and add the first of the PPAs shown below (outlined in red). The second PPA will be automatically added to your system. 
Once you have the new PPAs set up, go back to the Ubuntu Software Center and click on the PPA listing for Unity 2D on the left (highlighted with red in the image). Scroll down until you find the listing for “Unity interface for non-accelerated graphics cards – unity-2d” and click Install.

Once you have the new PPAs set up, go back to the Ubuntu Software Center and click on the PPA listing for Unity 2D on the left (highlighted with red in the image). Scroll down until you find the listing for “Unity interface for non-accelerated graphics cards – unity-2d” and click Install.
Share your Androidify creations
Posted by
jasper22
at
10:53
|

Google does a lot of really cool things, but some times they just get it right the first time. Take Androidify for example. Making yourself, loved ones, bitter rivals, or co-workers into Androids is fun. Using Androidify, it's simple. When simple and fun get together, you just can't beat it. I know we have a lot of creative readers, and Android Central forums member jjcasillas15 (that tall drink of water you see above is his!) started up a great thread to share what ya got. It's bound to get interesting, so jump right in and share. Androidify yourself!! Share your Androidify avatars . Read more: androidcentral
Read more: 
Hands on with MonoTouch - C# for the Apple iPhone and iPad
Posted by
jasper22
at
10:03
|
When an editor asked me for a screenshot of MonoTouch, which lets you use an open-source implementation of Microsoft's .NET Framework to target Apple's iPhone and iPad, I obtained it the best way I know, which is by installing it and trying it out. It is something I have been meaning to try for a while. There is high demand for apps on Apple's iOS, and both the iPhone and the iPad are finding their way into businesses. As all those app requests arrive on developer desks, what is the best way to meet them? They cannot be ignored for ever. I do not doubt the implication of Steve Jobs' essay, Thoughts on Flash, that, other things being equal, the best way to develop for iOS is with Objective C. Other things are never equal though; and for developers with a ton of existing .NET Framework applications along with skills in C# the possibility of creating iOS apps in a familiar language and framework is compelling. There may even be some code that could be ported. Monotouch is a commercial product, though you can get started for free, with the main limitation being that you can only deploy to the iPhone emulator.Installation is not difficult, though there are a couple of big dependencies: Apple's iPhone SDK, and the full desktop version of Mono for OSX. You probably also want MonoDevelop OS X, the Mono IDE. Oh yes, and a Mac of course. Then I got started. The New Solution dialog presents a choice of several iOS project types:
Duke Nukem Forever PC will use Steamworks
Posted by
jasper22
at
10:02
|
2K Games confirmed today on their Duke Nukem Forever forums that the PC version of the long-awaited shooter will be fully-integrated with Steamworks for DRM and online play.
Read more: GameMania
Hey guys, I've been fielding many inquiries about whether or not Duke Nukem Forever is going to be on Steam and today I'm happy to clear up any outstanding rumors and questions in your mind by saying: Yes, DNF *is* using Steamworks and only Steamworks for both the single player and multiplayer components of the game. Let me know if you have any other questions about this - and stay tuned - we're keeping track of a bunch of questions you have been asking and as they are finalized, I'll be posting more about them here.
Read more: GameMania
WP7 for iPhone and Android Developers - Introduction to C#
Posted by
jasper22
at
10:02
|
This article is part 1 from a 12-part article series on Windows Phone 7 for iPhone and Android Developers.WP7 for iPhone and Android Developers - Introduction to C# (current part)
WP7 for iPhone and Android Developers - Introduction to Xaml and Silverlight
WP7 for iPhone and Android Developers - Advanced UI
WP7 for iPhone and Android Developers - Hardware and Device Services
WP7 for iPhone and Android Developers - Using Bing Maps
WP7 for iPhone and Android Developers - Application Tiles and Push Notifications
WP7 for iPhone and Android Developers - Introducing the Execution Model and Navigation System
WP7 for iPhone and Android Developers - Local Data Storage
WP7 for iPhone and Android Developers - Consuming Web Services
WP7 for iPhone and Android Developers - From MVC on iPhone and Android to MVVM on Windows Phone 7
WP7 for iPhone and Android Developers - Building Cross/Multi-Platform Applicataions for WP7, iPhone, and Android
WP7 for iPhone and Android Developers - Introducing the App Marketplace
This article will provide an introduction to the basic concepts of writing code in C# for those of you already familiar with Java from Android development or with Objective-C from iPhone and iPad development. If you’re already a .NET developer and you’ve been building ASP.NET applications and you’re interested in learning how to write WP7 apps, then feel free to skip to the next article in this series. The ultimate goal of this series of articles is to prepare you for writing Windows Phone 7 applications, whether your background is in ASP.NET, Android, iPhone, or iPad development. The first thing developers notice about C# is how much it looks like C or C++. This is not a coincidence. Contrary to popular belief, C# was inspired by C and C++ and was not inspired by Java. If you’ve seen Java, Objective-C, and C# code side-by-side and you’ve thought about how similar they look at times, you’re not alone. All three of these languages owe much of their heritage to the original ANSI C language. In fact, Objective-C is actually a functioning superset of ANSI C so it does more than borrow it’s heritage from C, it’s a direct descendant. Like Java and Objective-C, C# is an Object-Oriented programming language. As an iOS or Android developer you should probably be very familiar with basic OOP concepts like encapsulation, inheritance, and accessors. Fortunately, the C# language looks enough like Java and Objective-C that basic arithmetic and even some conditional logic operators are indistinguishable among the three languages. Read more: Silverlight show
WP7 for iPhone and Android Developers - Introduction to Xaml and Silverlight
WP7 for iPhone and Android Developers - Advanced UI
WP7 for iPhone and Android Developers - Hardware and Device Services
WP7 for iPhone and Android Developers - Using Bing Maps
WP7 for iPhone and Android Developers - Application Tiles and Push Notifications
WP7 for iPhone and Android Developers - Introducing the Execution Model and Navigation System
WP7 for iPhone and Android Developers - Local Data Storage
WP7 for iPhone and Android Developers - Consuming Web Services
WP7 for iPhone and Android Developers - From MVC on iPhone and Android to MVVM on Windows Phone 7
WP7 for iPhone and Android Developers - Building Cross/Multi-Platform Applicataions for WP7, iPhone, and Android
WP7 for iPhone and Android Developers - Introducing the App Marketplace
This article will provide an introduction to the basic concepts of writing code in C# for those of you already familiar with Java from Android development or with Objective-C from iPhone and iPad development. If you’re already a .NET developer and you’ve been building ASP.NET applications and you’re interested in learning how to write WP7 apps, then feel free to skip to the next article in this series. The ultimate goal of this series of articles is to prepare you for writing Windows Phone 7 applications, whether your background is in ASP.NET, Android, iPhone, or iPad development. The first thing developers notice about C# is how much it looks like C or C++. This is not a coincidence. Contrary to popular belief, C# was inspired by C and C++ and was not inspired by Java. If you’ve seen Java, Objective-C, and C# code side-by-side and you’ve thought about how similar they look at times, you’re not alone. All three of these languages owe much of their heritage to the original ANSI C language. In fact, Objective-C is actually a functioning superset of ANSI C so it does more than borrow it’s heritage from C, it’s a direct descendant. Like Java and Objective-C, C# is an Object-Oriented programming language. As an iOS or Android developer you should probably be very familiar with basic OOP concepts like encapsulation, inheritance, and accessors. Fortunately, the C# language looks enough like Java and Objective-C that basic arithmetic and even some conditional logic operators are indistinguishable among the three languages. Read more: Silverlight show
Multi-Server Queries – Underappreciated features of Microsoft SQL Server
Posted by
jasper22
at
09:59
|
This is part of the series of posts that I am running under the title "Under Appreciated Features of SQL Server". The series has been inspired by Andy Warren's editorial on SQLServerCentral.com. After Activity Monitor, this is one of the other features that I was surprised to see in the list of underappreciated features. This feature has been a dream come true for anybody who manages more than one server at a time. The need to be able to query a bunch of servers in one go and the fact that this feature has been around since Microsoft SQL Server 2005 had made me think that this should have been pretty common in usage by now. Anyway, let’s quickly see how to use this wonderful feature that Microsoft SQL Server Management Studio provides.Running Multi-Server QueriesOne of our esteemed SQL Server MVPs is Mr. Pinal Dave (blog). He has, on June 14, 2009 written a very short, concise and precise blog post on how to run Multi-Server Queries. You can find that particular post here. Keep in mind that the most important usability change that you need to make in order to use this feature is that all servers participating in a multi-server query must be registered servers.What Pinal’s blog post does not cover are some navigational aids and query execution options. I will attempt to cover them here. Changes to the Query Editor windowThe Query editor window in a multi-server query is similar to the regular single-instance query editor, but there is one minor difference. The SSMS query status bar informs us about the number of servers that a particular query will run against. On my test environment, let’s say I have two registered instances. When I attempt to run a multi-server query, this is what I see: 
Read more: Beyond Relational

Getting Started with Android – Creating Android Application
Posted by
jasper22
at
09:59
|
This is ongoing blog on Getting Started with Android. In earlier blog, I provided an architecture overview of android application. In this blog, I will setup the development environment for Android and create a simple hello world application. I would say are two ways you could develop Android applications-The web development way: – Utilizing your web development skills like- HTML, CSS 3 and JavaScript (JQuery libraries). For instance, software’s like PhoneGap let you create web applications and uses a native bridge to run your applications to most leading mobiles- Android, IPhone and Blackberry.
Android SDK : – Using the Android SDK and third party android Java libraries to create applications using IDE like Eclipse.
I would start development with the later approach, but I plan to include web development also as part of this android series. Here are the software’s you would need to create Android applications –Eclipse IDE – I plan to use Eclipse IDE. You would need to install the Eclipse SDK “classic” platform. I have used the latest version 3.6. Download it from here. Android SDK Starter Package – Download the android starter package windows installer from -http://dl.google.com/android/android-sdk_r08-windows.zip . The Starter package lets you choice and installs Android SDK components. Run the Android SDK Starter Package installer. The Android SDK Starter Package requires Java 5 or 6 and it would detect during installation. Once you install Android SDK Starter Package, run the SDK Manager.exe from installed location. On the Choose packages to install, click Cancel as we would install required packages only. Note that the applications developed on new versions of android are not backward compatible, for instance applications developed on 2.3 would not work on 2.2, but applications developed on 2.2 should continue to work on 2.3. (how ever this may no be the case always, so its best to test out the application on emulator). Click on Available Packages and select SDK platform 2.3 (latest version) and Samples for SDK API 9 as shown below. This would installed Android SDK and its dependent components.Android ADT – Android development toolkit is an eclipse plug-in, which provides an integrated environment in eclipse for building and testing android applications. You can use the update manager in eclipse and install the ADT automatically or download the ADT Plugin zip from – http://dl.google.com/android/ADT-8.0.1.zip and install it manually. I prefer to use download the plug-in and install it manually. Once downloaded, follow these instructions:
Next, Click on Android. In the Android preferences, click SDK location, click Browse and provide the location Android SDK location. Click Apply. To check our installation was fine, we will create a hello world application and run it via Android emulator. Before running the Android application, you need to create an Android Virtual Device (AVD). AVD as the name suggest is a virtual device that emulates an android device and runs the application. The eclipse plug-in internally used android avd command, to create the AVD. Click on Window > Android SDK and AVD Manager. On the Virtual devices editor,Click New
Specify the Target as Android 2.3- API Level 9. (or the android environment which you want to create applications) , specify size of SD card and skin for the emulator as shown below. Click Create AVD.
Read more: Javalobby
Android SDK : – Using the Android SDK and third party android Java libraries to create applications using IDE like Eclipse.
I would start development with the later approach, but I plan to include web development also as part of this android series. Here are the software’s you would need to create Android applications –Eclipse IDE – I plan to use Eclipse IDE. You would need to install the Eclipse SDK “classic” platform. I have used the latest version 3.6. Download it from here. Android SDK Starter Package – Download the android starter package windows installer from -http://dl.google.com/android/android-sdk_r08-windows.zip . The Starter package lets you choice and installs Android SDK components. Run the Android SDK Starter Package installer. The Android SDK Starter Package requires Java 5 or 6 and it would detect during installation. Once you install Android SDK Starter Package, run the SDK Manager.exe from installed location. On the Choose packages to install, click Cancel as we would install required packages only. Note that the applications developed on new versions of android are not backward compatible, for instance applications developed on 2.3 would not work on 2.2, but applications developed on 2.2 should continue to work on 2.3. (how ever this may no be the case always, so its best to test out the application on emulator). Click on Available Packages and select SDK platform 2.3 (latest version) and Samples for SDK API 9 as shown below. This would installed Android SDK and its dependent components.Android ADT – Android development toolkit is an eclipse plug-in, which provides an integrated environment in eclipse for building and testing android applications. You can use the update manager in eclipse and install the ADT automatically or download the ADT Plugin zip from – http://dl.google.com/android/ADT-8.0.1.zip and install it manually. I prefer to use download the plug-in and install it manually. Once downloaded, follow these instructions:
- Start eclipse . Click on Help -> Install New Software
- Click on Add. In the Add Repository, Click Archive and provide the location of downloaded ADT zip file. Enter Name as ADT local. Click Ok
- Click on Developer Tools and Click Next
- Click Next. Accept the licenses and Click Finish.
- This would install ADT plug-in. Restart eclipse
- Next specify the location of Android
- Click on Windows -> preferences
Next, Click on Android. In the Android preferences, click SDK location, click Browse and provide the location Android SDK location. Click Apply. To check our installation was fine, we will create a hello world application and run it via Android emulator. Before running the Android application, you need to create an Android Virtual Device (AVD). AVD as the name suggest is a virtual device that emulates an android device and runs the application. The eclipse plug-in internally used android avd command, to create the AVD. Click on Window > Android SDK and AVD Manager. On the Virtual devices editor,Click New
Specify the Target as Android 2.3- API Level 9. (or the android environment which you want to create applications) , specify size of SD card and skin for the emulator as shown below. Click Create AVD.
Read more: Javalobby
Mobile Development with Mobile Frameworks
Posted by
jasper22
at
09:57
|
Today a number of mobiles are coming with having different awesome features, but supporting various platforms. If a mobile application has to build, it has to be build for at least 4 – 5 platform. As the top platform viz. Android, Windows, Iphone have each large number of user base. Due to variety of platforms, it has been creating an hurdle for mobile app developer, as he has to learn for each platform. But now that won’t be a hurdle any more, as cross platform mobile frameworks are available which will ease the task of the mobile developer. Once app are built using cross platform mobile frameworks, the mobile app will be able to run properly on any mobile irrespective of the underlying Operating System.
I have listed the framework along with apps and companies which are using it.RhoMobile
Rhodes is the cross platform smart phone framework for mobile application development, which
allows developers to write smart phone native apps. It follows the MVC pattern. They have also started hosting the code on cloud called RhoHub .
Apps built using Rhodes framework :: Sugar CRM, Pivotal tracker’s Track R, WikipediaPhoneGap
PhoneGap is HTML5 app platform that allows you to author native application with web technologies and get accesses to API and app store.
Apps built using PhoneGap :: groupix, babllerOpenMobileis
Open mobile IS is an open source project that aims to provide all the necessary tools, API, and documents enabling powerful normal applications development. Heart of the project, the Java framework is divided into components providing all the needed functionalities. jQuerymobile
jQuerymobile – A unified user interface system across all popular mobile device platforms, built on the rock-solid jQuery and jQuery UI foundation. Its lightweight code is built with progressive enhancement and has a flexible, easily themeable design. Also they have given mobile graded browser support chart at http://jquerymobile.com/gbs/Read more: Tutkiun!
I have listed the framework along with apps and companies which are using it.RhoMobile
Rhodes is the cross platform smart phone framework for mobile application development, which
allows developers to write smart phone native apps. It follows the MVC pattern. They have also started hosting the code on cloud called RhoHub .
Apps built using Rhodes framework :: Sugar CRM, Pivotal tracker’s Track R, WikipediaPhoneGap
PhoneGap is HTML5 app platform that allows you to author native application with web technologies and get accesses to API and app store.
Apps built using PhoneGap :: groupix, babllerOpenMobileis
Open mobile IS is an open source project that aims to provide all the necessary tools, API, and documents enabling powerful normal applications development. Heart of the project, the Java framework is divided into components providing all the needed functionalities. jQuerymobile
jQuerymobile – A unified user interface system across all popular mobile device platforms, built on the rock-solid jQuery and jQuery UI foundation. Its lightweight code is built with progressive enhancement and has a flexible, easily themeable design. Also they have given mobile graded browser support chart at http://jquerymobile.com/gbs/Read more: Tutkiun!
How to develop games on Android
Posted by
jasper22
at
09:56
|
One of the biggest markets in smart phones is games. I am sure most of us would have played around with “Angry Birds” . In this games tutorial you will learn different methods of developing “Android Games” At the end of the post is the video on how the code below works and the zip of all the source files used in this example.Android Games can be developed in 3 ways1) Developing games using Android/Java libraries
2) Developing games using External Libraries like OpenGL
3) Developing games by porting existing c-game (pc game) to android.Before getting started I assume that the reader is familiar with the basics of android programming like using activity, creating views, handling motion/touch events etc. Also, apart from android sdk and eclipse some other tools are required for the game development. Details of the tools required, how to configure and use them will be explained as and when required. I will recommend to check out our last posts Read more: Skill Guru
2) Developing games using External Libraries like OpenGL
3) Developing games by porting existing c-game (pc game) to android.Before getting started I assume that the reader is familiar with the basics of android programming like using activity, creating views, handling motion/touch events etc. Also, apart from android sdk and eclipse some other tools are required for the game development. Details of the tools required, how to configure and use them will be explained as and when required. I will recommend to check out our last posts Read more: Skill Guru
Coding4Fun.Phone.Toolkit v1.1
Posted by
jasper22
at
09:55
|
This is where Coding4Fun will house all our cool controls and tools that we come up with! Right now we’ve created and updated some great controls for Silverlight that should help out everyone! If there is a bug [report], a needed control/feature that could benefit everyone [chat], or you want to help out [email], please reach out to us! NuGet Installs:
Controls + TimeSpan Picker:
Install-Package Coding4Fun.Phone.Controls.Complete
Controls:
Install-Package Coding4Fun.Phone.Controls
Only TimeSpan Picker:
Install-Package Coding4Fun.Phone.Controls.TimeSpan
Current Coding4Fun Windows Phone Toolkit:
Controls:About Prompt
Input Prompt
Progress Overlay
Round Button
Round Toggle Button
Memory Counter
TimeSpan Picker
Abstract Classes:PopUp class for things like an Input Prompt that can be GPU accelerated unlike the built in Popup control.
Converters:Boolean to Visibility
String To Visibility
Themed Image Converter
Inversed Theme Image Converter
Visibility to BooleanRead more: Codeplex
Controls + TimeSpan Picker:
Install-Package Coding4Fun.Phone.Controls.Complete
Controls:
Install-Package Coding4Fun.Phone.Controls
Only TimeSpan Picker:
Install-Package Coding4Fun.Phone.Controls.TimeSpan
Current Coding4Fun Windows Phone Toolkit:
Controls:About Prompt
Input Prompt
Progress Overlay
Round Button
Round Toggle Button
Memory Counter
TimeSpan Picker
Abstract Classes:PopUp class for things like an Input Prompt that can be GPU accelerated unlike the built in Popup control.
Converters:Boolean to Visibility
String To Visibility
Themed Image Converter
Inversed Theme Image Converter
Visibility to BooleanRead more: Codeplex
Crysis 2 PC build leaked
Looks like the full version of Crysis 2 (though a beta build from developers) has been leaked to torrents. The build contains the entire single player campaign of the game, apparently. However, it's in debug mode and not the final build of the game. It's currently unknown how this build got onto the net but its always sad when something like this happens as it is bound to not only affect sales of the game itself but also cause publisher to try to create more complex DRM set ups that will just upset legit consumers. Crysis 2 is set to ship on PC, Xbox 360, and Playstation 3 in March 2011. Read more: GameMania
You need a mobile app. ShoutEm makes its creation incredibly easy.
Posted by
jasper22
at
17:10
|

If you’ve ever dealt with the building of a mobile application, you’ll know that it’s a realm best left to those who do it professionally. It’s so easy to build something that just doesn’t do your content justice on a mobile platform. The answers that we’ve seen to this problem so far is to build HTML5 websites that function as a mobile app. While that experience will work as a stop-gap measure, it’s not up to par with an official application. Enter ShoutEm. The company has been around for ages, serving as a microblogging and messaging platform. Its newest feature, though, could very well turn the mobile apps market on its ear. ShoutEm is now billing itself as “the world’s simplest mobile app maker”. After a 5 minute run through the service to create a mobile app ourselves, we’re inclined to agree. Read more: TNW
Read more: ShoutEm
You May Kiss The Bride, Thanks To Google Weddings
Posted by
jasper22
at
17:10
|

Google is making a big push into the wedding planning scene today, launching a full fledged planning portal for brides and grooms to be. Google Weddings is a destination that houses wedding-specific templates in Google Sites, Google Docs and Picnik for save-the-dates, wedding websites, planning materials, invitations and more. Google has also partnered with wedding planner Michelle Rago to provide tips and guidance on which designs to use. This isn’t Google’s first move in the wedding planning world, the search giant also began offering customized wedding templates in Google Docs a year ago that let users access pre-made documents to track your wedding budget, collect addresses for invitations, compare vendors and much more. Read more: Techcrunch
Read more: Google
Sonos Controller for Android with voice search will blow you away (video)
Posted by
jasper22
at
17:10
|

You can exhale Sonos fans, it's finally happening. The Sonos Controller for Android is official. After almost a year in development, the free WiFi music remote finally gives Sonos owners control over their whole-home audio system from any Android 2.1 and above device with a screen size of HVGA 320 x 480, WVGA 480 x 800 or WVGA 480 x 854. At least it will when it hits the Market at the end of March. Better yet, it trumps the Sonos iOS controller with music controls mapped directly to the buttons on your Android hardware. As such, you can control the volume of your Sonos system with the physical volume rocker on your Desire Z or use the search button on your Droid X to forage for that certain artist, track, or album. Oh, and the Sonos Controller for Android also supports voice search -- take that iOS app. Read more: Engadget
Writing with a Phone
Posted by
jasper22
at
17:09
|
The Traccia is a phone concept modeled on how we use a writing instrument, specifically a pen. The intuitive way we write on a sheet is translated to commands for the phone thanks to the embedded optical sensor located at the end of the stick. Basically whatever you write gets translated to a command or function via the installed software. This means your invisible writing can be converted to SMS or an email, just like that! The navigation design is basic with just three simple keys to one end. The built in polycarbonate gives the phone a natural feel and makes the touchscreen even more alluring. And of course no phone is complete without a camera, so the Traccia positions its camera at the center of the arc, right under the display. All said I done, I just have to wonder if the grip of this phone is as comfortable as the rest. An arc on a stick doesn’t look ideal, but you never know till you don’t try it. 

Design Trends: 25 Awesome iPhone & iPad App Website Designs
Posted by
jasper22
at
17:06
|
Mobile is blowing up. O.K., maybe it’s already blown up and I’m just a bit behind the times, but regardless of my lack of technical savvy, mobile apps make up a huge market and today I want to look over one of the most recent trends I’ve seen in web design – iPhone and iPad app website designs. One of the main things you see in every one of the examples below is a large iPhone or iPad image, which fits the design perfectly because it instantly lets the visitor know what type of website you’re on.One thing that you begin to notice after this similarity is that a lot of the designs have a general web layout that mimics the look and feel of the app itself. For instance, with the Bord app, the website features a lot of the same design elements that the app itself features.
MJPEG Decoder for WPF, WinForms, WP7 and XNA
Posted by
jasper22
at
11:30
|
Project Description
Library to decode MJPEG streams for Silverlight, Windows Phone 7, XNA 4.0, WinForms, and WPF. Sample code showing usage is included with the distribution. For more information, see the full article at Coding4Fun. Read more: Codeplex
Read more: Coding4Fun
Library to decode MJPEG streams for Silverlight, Windows Phone 7, XNA 4.0, WinForms, and WPF. Sample code showing usage is included with the distribution. For more information, see the full article at Coding4Fun. Read more: Codeplex
Read more: Coding4Fun
Working with Android Layouts and ListViews
Posted by
jasper22
at
11:29
|
I've been the owner of an Android phone for about 5 months now. The thought of creating an application for the Android platform has appealed to me ever since. That's why I recently started with Android development as a learning project for the next couple of weeks. In this post I will start sharing my experience with developing Android applications. Getting started
The basic thing, while starting out with a new technology, is getting to know the fundamentals. There are some great introduction and advanced videos by Google on how to develop applications for the Android platform. The use of proper tooling can also help out a lot on this part. Both Eclipse and IntelliJ has great support for developing Android application since IntelliJ 10 (and it's free to use). For this project I'm trying to create a native Android client based on the Hippo GoGreen mobile website. If you take a look at the mobile site, there are two main entry points for browsing the site: Products and Events. I started out with Events, where I wanted to create a list of event items and show the event with a nice calendar item on the left next to the title of the event. I wanted the end result to look something like:
In Android you can create a screen/page by creating an Activity. Adding a ListView to an Activity is a matter of configuration. With Android you can define the layout of your View either by defining a piece of XML, or by writing the code in Java. For this example I use the XML notation. <?xml version="1.0" encoding="utf-8"?>
<FrameLayout xmlns:android="http://schemas.android.com/apk/res/android"
android:layout_width="fill_parent"
android:layout_height="fill_parent">
<ListView
android:id="@android:id/list"
android:layout_width="fill_parent"
android:layout_height="fill_parent" />
<TextView
android:id="@android:id/empty"
android:layout_width="fill_parent"
android:layout_height="fill_parent"
android:text="@string/empty_events"
android:gravity="center"
android:textAppearance="?android:attr/textAppearanceMedium" />
</FrameLayout>Read more: Jeroen Reijn
The basic thing, while starting out with a new technology, is getting to know the fundamentals. There are some great introduction and advanced videos by Google on how to develop applications for the Android platform. The use of proper tooling can also help out a lot on this part. Both Eclipse and IntelliJ has great support for developing Android application since IntelliJ 10 (and it's free to use). For this project I'm trying to create a native Android client based on the Hippo GoGreen mobile website. If you take a look at the mobile site, there are two main entry points for browsing the site: Products and Events. I started out with Events, where I wanted to create a list of event items and show the event with a nice calendar item on the left next to the title of the event. I wanted the end result to look something like:

In Android you can create a screen/page by creating an Activity. Adding a ListView to an Activity is a matter of configuration. With Android you can define the layout of your View either by defining a piece of XML, or by writing the code in Java. For this example I use the XML notation. <?xml version="1.0" encoding="utf-8"?>
<FrameLayout xmlns:android="http://schemas.android.com/apk/res/android"
android:layout_width="fill_parent"
android:layout_height="fill_parent">
<ListView
android:id="@android:id/list"
android:layout_width="fill_parent"
android:layout_height="fill_parent" />
<TextView
android:id="@android:id/empty"
android:layout_width="fill_parent"
android:layout_height="fill_parent"
android:text="@string/empty_events"
android:gravity="center"
android:textAppearance="?android:attr/textAppearanceMedium" />
</FrameLayout>Read more: Jeroen Reijn
Internet Explorer 9 RC – download, what’s new and get your sites ready
Posted by
jasper22
at
11:28
|
Dean Hachamovich has just announced availability of Internet Explorer 9 Release Candidate on the official IE team blog. As Dean blogs, we have received a lot of feedback from developer and end-users. We have listened and now with the RC, IE9 has made progress in the areas of performance, standards, user interface, safety and privacy. Actions:
Since the release of Internet Explorer 9 Beta in September, we have also seen the release of new iterations of the Platform Preview. With IE9 Release Candidate, new features and additions surfaced through the Platform Previews have been rolled up into Internet Explorer 9 RC. For a good overview of where we have come from since the first Platform Preview announcement at MIX10 last year I’ve summed up the different blog posts on the official IE team blog. Read more: Katrien's MSDN Blog
- Download Internet Explorer 9 Release Candidate through www.BeautyOfTheWeb.com (available in 40 languages)
- Test your sites and web applications, make sure you review the Developer’s Guide to adapt to the new standards support
- Report issues by using Send Feedback option in Internet Explorer (Tools or Alt+X > Send Feedback)
Since the release of Internet Explorer 9 Beta in September, we have also seen the release of new iterations of the Platform Preview. With IE9 Release Candidate, new features and additions surfaced through the Platform Previews have been rolled up into Internet Explorer 9 RC. For a good overview of where we have come from since the first Platform Preview announcement at MIX10 last year I’ve summed up the different blog posts on the official IE team blog. Read more: Katrien's MSDN Blog
Alien Dalvik lets Android apps run anywhere
Posted by
jasper22
at
11:27
|
Alien Dalvik and similar technologies have the power to make all mobile devices equal and to make the Android app the only type of app you ever have to write.
Many Android users think that the only problem with Android is that it only runs on Android portable devices. More precisely they would like to run the same apps on their laptops and perhaps even desktop machines. While Android is a Linux-derived operating system customised by Google to run on mobile devices most of its apps are essentially Java applications. The main claim to fame for a Java application is that it can be run on almost any operating system - so why can't you run an Android app under Ubuntu or Windows even? Read more: I Programmer
Many Android users think that the only problem with Android is that it only runs on Android portable devices. More precisely they would like to run the same apps on their laptops and perhaps even desktop machines. While Android is a Linux-derived operating system customised by Google to run on mobile devices most of its apps are essentially Java applications. The main claim to fame for a Java application is that it can be run on almost any operating system - so why can't you run an Android app under Ubuntu or Windows even? Read more: I Programmer
Fiddler and the IE9 Release Candidate
Posted by
jasper22
at
11:26
|
I’m delighted to announce that the now-available IE9 RC includes three significant enhancements for users of proxy-based debuggers like Fiddler.These improvements are:
- The default Connections-Per-Proxy limit has been raised from 6 to 12, improving performance and in some cases reducing Observer Effect.
- Debugging of traffic sent to Localhost / 127.0.0.1 now “just works”—configuration changes are not required.
- Internet Explorer now can be configured to emit information about why a given HTTP request was issued, which helps you understand your web traffic.
I’ll explain each of these three improvements in this post.Connections-Per-Proxy Limit
Browsers are typically designed to limit the number of connections made to a single server in order to prevent overloading it or incurring other problems. Some browsers have a different limit depending on whether the server being contacted is a proxy server or a normal host (web server). Internet Explorer 6 and 7 apply the “web server” connection limit to proxies as well; the two connection limit those versions use can severely impact your debugging performance when using Fiddler. Users still using those outdated browsers can re-configure the connection limit to mitigate this problem. Internet Explorer 8 limits the connections per proxy to six, which was a welcome improvement, but still could cause performance problems when debugging sites that “shard” their requests to many different hosts. Internet Explorer 9 maintains the existing connections-per-host limit of six, but also includes an specific connections-per-proxy limit which is set to 12 by default. This increased limit should help reduce the impact of connection limits upon your debugging scenarios. For comparison, Firefox’s default value for the network.http.max-persistent-connections-per-proxy setting is eight, but the FiddlerHook extension kicks this value up to twenty-four.Proxying Localhost Traffic
The WinINET networking component that is used by Internet Explorer and many other applications will automatically bypass a fixed proxy (like Fiddler) for traffic bound for //localhost and //127.0.0.1 because these “loopback” addresses point to the local machine and traditional proxy servers will not be able to interpret such addresses properly. However, for a debugging proxy running on the local computer, these are perfectly understandable addresses, and when developers are debugging against a local server (like IIS Express or the Visual Studio Test Server Cassini) they often test against these loopback addresses. To proxy loopback traffic from IE8 and below, somewhat awkward workarounds are needed. Read more: Fiddler Web Debugger
Browsers are typically designed to limit the number of connections made to a single server in order to prevent overloading it or incurring other problems. Some browsers have a different limit depending on whether the server being contacted is a proxy server or a normal host (web server). Internet Explorer 6 and 7 apply the “web server” connection limit to proxies as well; the two connection limit those versions use can severely impact your debugging performance when using Fiddler. Users still using those outdated browsers can re-configure the connection limit to mitigate this problem. Internet Explorer 8 limits the connections per proxy to six, which was a welcome improvement, but still could cause performance problems when debugging sites that “shard” their requests to many different hosts. Internet Explorer 9 maintains the existing connections-per-host limit of six, but also includes an specific connections-per-proxy limit which is set to 12 by default. This increased limit should help reduce the impact of connection limits upon your debugging scenarios. For comparison, Firefox’s default value for the network.http.max-persistent-connections-per-proxy setting is eight, but the FiddlerHook extension kicks this value up to twenty-four.Proxying Localhost Traffic
The WinINET networking component that is used by Internet Explorer and many other applications will automatically bypass a fixed proxy (like Fiddler) for traffic bound for //localhost and //127.0.0.1 because these “loopback” addresses point to the local machine and traditional proxy servers will not be able to interpret such addresses properly. However, for a debugging proxy running on the local computer, these are perfectly understandable addresses, and when developers are debugging against a local server (like IIS Express or the Visual Studio Test Server Cassini) they often test against these loopback addresses. To proxy loopback traffic from IE8 and below, somewhat awkward workarounds are needed. Read more: Fiddler Web Debugger
VistaDB CLR Procs and Functions Introduction
Posted by
jasper22
at
11:25
|
Intro to CLR Stored Procedures and CLR FunctionsCLR Stored Procedures and Functions are a relatively new way to build extensions for your database. Traditionally stored procedure logic has been written in SQL, but SQL Server 2005 introduced the ability to use CLR code for procedures. Microsoft sometimes calls this SQL CLR as the technology used to load CLR assemblies into SQL Server. Prior to SQL CLR, you could only extend SQL Server using C++ DLLs that were difficult to build and maintain. We implemented SQL CLR assemblies very early in the VistaDB 3 development cycle to allow users to extend their databases using the same language they wrote their application (C# or VB.NET). During the upgrade to VistaDB 4, we had identified a number of small changes we wanted to make to CLR Procs to make them more compatible with SQL Server, and to make it possible to build an assembly that would work with both VistaDB and SQL Server with only a recompile (no major code changes). We have achieved that goal in VistaDB 4 through the addition of a new namespace: VistaDB.Compatibility.SqlServer. High Level Overview

Read more: Codeproject
Looking for Silverlight developers? Post your job openings in SilverlightShow open group on LinkedIn
Posted by
jasper22
at
11:24
|
SilverlightShow group on LinkedIn is now an open group. And among the main benefits of an open group is the option to share all discussions on Facebook and Twitter! Hope this will really encourage the sharing of the information discussed in the group. We see that LinkedIn is often used to post job announcements as discussions. We don't mind that - so feel free to post your Silverlight jobs in our group! We encourage you to provide more information for your openings, not just salary, location and email, if you want to avoid a huge number of applications not worth reviewing.. And - sometimes it may be worth considering the option to train your own staff in Silverlight, and not waste time looking for new developers. Check out different training options (for example, the company behind SilverlightShow, CompletIT, offers quite a variety of beginner to advanced Silverlight trainings, including fully custom ones), encourage your staff to read our articles and Get Started section, watch our Silverlight webinars, read the news referring to blog posts covering basically any topic in the world of Silverlight. The investment in training your own staff might definitely pay out! Read more: Silverlight show
Buffer.BlockCopy not as fast as you think
Posted by
jasper22
at
11:23
|
I recently wrote a quick test to prove something, that ended up being wrong…Of course this is the way of science. You form a hypothesis, then you test. The results should prove or disprove your theory. The HypothesisOk, my theory was that Buffer.BlockCopy() would outperform our current Array.Copy routines on the page level.When we are loading records off a page, we have to extract some parts of the buffer to build up a row buffer. A typical 8Kb page may have 100 or more records packed into it, and grabbing them out can take quite a bit of time. Each row data is a compressed byte array that may include information that points to extended row data as well. This is one of the differences between this same app written in C++ and C#. In C++, you would just take a pointer to the original buffer and pass that to the row routines, you wouldn't need a copy of the data. But we don't have pointers in C#, so a copy is made to get out just the part of the buffer needed by that row. Since we want the fastest way possible to read this block of data into the row, we were looking at alternative ways to do it.The Experiment I wrote a program that randomly grabs a length from an 8Kb block that contains 150 records. The length of the row was randomized (but the seed reset to the same value for both tests to ensure the same random numbers were used with both methods). The results were surprising. class Program
{
public static int pagesize = 8192;
public static int MaxLoops = 100000; static void Main( string[] args )
{
Stopwatch watch = new Stopwatch(); // Force a GC Collect so we start clean
GC.Collect(GC.MaxGeneration, GCCollectionMode.Forced);
System.Threading.Thread.Sleep(2000);
watch.Start();
DoTest(true);
watch.Stop();
Console.WriteLine("Buffer.BlockCopy took {0} ticks", watch.ElapsedTicks); watch.Reset();
GC.Collect(GC.MaxGeneration, GCCollectionMode.Forced);
System.Threading.Thread.Sleep(2000);Read more: Codeproject
{
public static int pagesize = 8192;
public static int MaxLoops = 100000; static void Main( string[] args )
{
Stopwatch watch = new Stopwatch(); // Force a GC Collect so we start clean
GC.Collect(GC.MaxGeneration, GCCollectionMode.Forced);
System.Threading.Thread.Sleep(2000);
watch.Start();
DoTest(true);
watch.Stop();
Console.WriteLine("Buffer.BlockCopy took {0} ticks", watch.ElapsedTicks); watch.Reset();
GC.Collect(GC.MaxGeneration, GCCollectionMode.Forced);
System.Threading.Thread.Sleep(2000);Read more: Codeproject
Check out a 'Query Analyzer/SSMS' for Log Parser called Log Parser Lizard
Posted by
jasper22
at
11:23
|
As any incident responder will agree, you can never have too many logs. That is, of course, until you have to analyze them! I was recently on an engagement where our team had to review hundreds of gigabytes of logs looking for evidence of hacking activity. I was quickly reminded of how much I love Microsoft Log Parser. Log Parser is often misunderstood and underestimated. It could possibly be the best forensic analysis tool every devised. Imagine having the ability to take almost any chunk of data and quickly search it using SQL-based grammar. That's Log Parser in a nutshell. It is a lightweight SQL-based search engine that operates on a staggering number of different input types (see Figure 1). Yes, I know that tools like Splunk and Sawmill are built around this same idea, but keep in mind that Log Parser was written in the year 2000. I am constantly amazed at the power it affords the forensic analyst, and you can't beat the price (free). Save perhaps memory analysis, there isn't much it can't accomplish for an incident responder. Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: Computer Forensics How-To: Microsoft Log Parser
Read more: Computer Forensics How-To: Microsoft Log Parser
Mallory – Transparent TCP & UDP Proxy
Posted by
jasper22
at
11:22
|
Mallory is a transparent TCP and UDP proxy. It can be used to get at those hard to intercept network streams, assess those tricky mobile web applications, or maybe just pull a prank on your friend.In more technical terms, Mallory is an extensible TCP/UDP man in the middle proxy that is designed to be run as a gateway. The goal is to man in the middle traffic for testing purposes. The ideal setup for Mallory is to have a “LAN” or “Victim” network that Mallory acts as the gateway for. This can be configured within a virtal machine environment using host only network interfaces. The victim virtual machines then configures the Mallory machine as the gateway by manually setting its gateway. The gateway machine will have at least one WAN interface that grants Internet access. The victim network then uses the Mallory gateway to route traffic. Folder Structureca – certificate authority files including Mallory’s private key
certs – MiTM certs that are created on the fly
db – directory where mallory stores all database files
mallory – empty directory
src – where the code lives
scripts – scripts used to configure mallory enviorment
Read more: Darknet.org.uk
certs – MiTM certs that are created on the fly
db – directory where mallory stores all database files
mallory – empty directory
src – where the code lives
scripts – scripts used to configure mallory enviorment
Read more: Darknet.org.uk
How do specify that a shortcut should not be promoted as newly-installed on the Start menu?
Posted by
jasper22
at
11:21
|
Windows XP employed a number of heuristics to determine which Start menu shortcuts should be promoted when an application is newly-installed. But what if those heuristics end up guessing wrong?You can set the System.AppUserModel.ExcludeFromShowInNewInstall property to VARIANT_TRUE to tell the Start menu, "I am not the primary entry point for the program; I'm a secondary shortcut, like a help file." #include <windows.h>
#include <tchar.h>
#include <shlobj.h>
#include <atlbase.h>// class CCoInitialize incorporated here by referenceint __cdecl _tmain(int argc, TCHAR **argv)
{
// error checking elided for expository purposes
CCoInitialize init;
CComPtr<IShellLink> spsl;
spsl.CoCreateInstance(CLSID_ShellLink);
spsl->SetPath(TEXT("C:\\Program Files\\LitWare\\LWUpdate.exe"));
PROPVARIANT pvar;
pvar.vt = VT_BOOL;
pvar.boolVal = VARIANT_TRUE;
CComQIPtr<IPropertyStore>(spsl)->SetValue(PKEY_AppUserModel_ExcludeFromShowInNewInstall, pvar);
CComQIPtr<IPersistFile>(spsl)->Save(L"LitWare Update.lnk", TRUE);
Read more: The old new thing
#include <tchar.h>
#include <shlobj.h>
#include <atlbase.h>// class CCoInitialize incorporated here by referenceint __cdecl _tmain(int argc, TCHAR **argv)
{
// error checking elided for expository purposes
CCoInitialize init;
CComPtr<IShellLink> spsl;
spsl.CoCreateInstance(CLSID_ShellLink);
spsl->SetPath(TEXT("C:\\Program Files\\LitWare\\LWUpdate.exe"));
PROPVARIANT pvar;
pvar.vt = VT_BOOL;
pvar.boolVal = VARIANT_TRUE;
CComQIPtr<IPropertyStore>(spsl)->SetValue(PKEY_AppUserModel_ExcludeFromShowInNewInstall, pvar);
CComQIPtr<IPersistFile>(spsl)->Save(L"LitWare Update.lnk", TRUE);
Read more: The old new thing
ClickOnce, TaskDialogs, Common Controls and WPF Applications
Posted by
jasper22
at
11:20
|
One of the things that I talked a little about in my talk about “Modern Windows Applications on Windows 7” was around the idea of using a TaskDialog when you’re trying to get a response from the user rather than using your own custom dialog or a MessageBox or similar. As an aside, this isn’t just about TaskDialogs and MessageBoxes and so on – there’s other reasons why you would want to get the latest version of common controls loaded into a WPF application but this particular area was one that I’d left “hanging” at that previous talk as I hadn’t resolved it at the time. TaskDialog isn’t represented in the .NET Framework at all as far as I know so you need to look to the Windows API Code Pack which provides a managed TaskDialog class that you can make use of to make getting to the native APIs pretty easy. To illustrate this in its entirety, here’s the world’s simplest example.
Read more: Mike Taulty's Blog

Read more: Mike Taulty's Blog
Kerberos Debugging Tips
Posted by
jasper22
at
11:19
|
I worked on adding Kerberos support for Apache Rampart and WSS4J during last few weeks and interop testing with WCF.Following lists some useful debugging tips I came across..1. How to list all the Kerberos tickets issued to the logged in client principal in Windows c:\Program Files (x86)\Resource Kit>klistCurrent LogonId is 0:0x29a6fCached Tickets: (2)#0> Client: administrator @ WSO2.COM
Server: krbtgt/WSO2.COM @ WSO2.COM
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e00000 -> forwardable renewable initial pre_authent
Start Time: 11/25/2010 13:19:58 (local)
End Time: 11/25/2010 23:19:58 (local)
Renew Time: 12/2/2010 13:19:58 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
#1> Client: administrator @ WSO2.COM
Server: service/myserver @ WSO2.COM
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
Ticket Flags 0x40a40000 -> forwardable renewable pre_authent ok_as_delegate
Start Time: 11/25/2010 13:19:58 (local)
End Time: 11/25/2010 23:19:58 (local)
Renew Time: 12/2/2010 13:19:58 (local)
Session Key Type: RSADSI RC4-HMAC(NT)2. How to remove cached Kerberos tickets in Windowsc:\Program Files (x86)\Resource Kit>klist purge Current LogonId is 0:0x29a6f
Deleting all tickets:
Ticket(s) purged!
Read more: F A C I L E L O G I N
Server: krbtgt/WSO2.COM @ WSO2.COM
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e00000 -> forwardable renewable initial pre_authent
Start Time: 11/25/2010 13:19:58 (local)
End Time: 11/25/2010 23:19:58 (local)
Renew Time: 12/2/2010 13:19:58 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
#1> Client: administrator @ WSO2.COM
Server: service/myserver @ WSO2.COM
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
Ticket Flags 0x40a40000 -> forwardable renewable pre_authent ok_as_delegate
Start Time: 11/25/2010 13:19:58 (local)
End Time: 11/25/2010 23:19:58 (local)
Renew Time: 12/2/2010 13:19:58 (local)
Session Key Type: RSADSI RC4-HMAC(NT)2. How to remove cached Kerberos tickets in Windowsc:\Program Files (x86)\Resource Kit>klist purge Current LogonId is 0:0x29a6f
Deleting all tickets:
Ticket(s) purged!
Read more: F A C I L E L O G I N
What should be considered when NOLOCK hint is used
Posted by
jasper22
at
11:18
|
IntroductionWith SQL Server the NOLOCK hint is very tempting especially with SELECT statements where at least one of the tables is frequently updated. Using the NOLOCK removes all queueing problems and the SELECT statement runs smoothly, but not without side effetcs. Why do we need a hint at allFirst question might be that why do we need to add this hint to get the statement running without additional waits. The answer lies on a basic database management system principle: ACID (atomicity, consistency, isolation and durability). The property isolation defines that other transactions may not see uncompleted modifications. Since SQL Server (when default locking scenario is used) uses exclusive locks which prevent acquiring read (shared) locks all reading operations must wait until exclusive locks are released. This causes the select statement to wait if the data to be fetched is locked exclusively. Using NOLOCK hint (which means exactly the same as READUNCOMMITTED) actually bypasses the check for exclusive locks and does not set shared locks at all. So what it also means is that the query sees data that is not yet committed to the database which may result to a dirty read. This means that the modifications are not isolated so one of the main database principles is ignored. This is why NOLOCK -like behaviour isn't used by default. What it actually meansLet's take an example. First let's create necessary objects. Collapse
----------------------------------
-- Create test objects
----------------------------------
-- Schema
CREATE SCHEMA LockTest;
GO-- OrderEntry -table
IF OBJECT_ID ( 'LockTest.OrderEntry', 'U' ) IS NOT NULL
DROP TABLE LockTest.OrderEntry;
GOCREATE TABLE LockTest.OrderEntry (
Id int not null identity(1,1) primary key,
Amount int not null,
UnitPrice decimal not null,
Area int not null
);
GO-- AddOrders -procedure
IF OBJECT_ID ( 'LockTest.AddOrders', 'P' ) IS NOT NULL
DROP PROCEDURE LockTest.AddOrders;
GOCREATE PROCEDURE LockTest.AddOrders @OrderCount int AS
BEGIN
DECLARE @counter int = 0; WHILE (@counter < @OrderCount) BEGIN
INSERT INTO LockTest.OrderEntry
(Amount, UnitPrice, Area)
VALUES
(ROUND(RAND()*100, 0), ROUND(RAND()*100, 2), ROUND(RAND()*10, 0)); SET @counter = @counter + 1;
END;
END;
GO
So now we have a single table and a procedure to create some random data. Let's add something to the table. Collapse
-- Add some data to the table
BEGIN TRANSACTION;
EXEC LockTest.AddOrders @OrderCount=100;
COMMIT;Read more: Codeproject
----------------------------------
-- Create test objects
----------------------------------
-- Schema
CREATE SCHEMA LockTest;
GO-- OrderEntry -table
IF OBJECT_ID ( 'LockTest.OrderEntry', 'U' ) IS NOT NULL
DROP TABLE LockTest.OrderEntry;
GOCREATE TABLE LockTest.OrderEntry (
Id int not null identity(1,1) primary key,
Amount int not null,
UnitPrice decimal not null,
Area int not null
);
GO-- AddOrders -procedure
IF OBJECT_ID ( 'LockTest.AddOrders', 'P' ) IS NOT NULL
DROP PROCEDURE LockTest.AddOrders;
GOCREATE PROCEDURE LockTest.AddOrders @OrderCount int AS
BEGIN
DECLARE @counter int = 0; WHILE (@counter < @OrderCount) BEGIN
INSERT INTO LockTest.OrderEntry
(Amount, UnitPrice, Area)
VALUES
(ROUND(RAND()*100, 0), ROUND(RAND()*100, 2), ROUND(RAND()*10, 0)); SET @counter = @counter + 1;
END;
END;
GO
So now we have a single table and a procedure to create some random data. Let's add something to the table. Collapse
-- Add some data to the table
BEGIN TRANSACTION;
EXEC LockTest.AddOrders @OrderCount=100;
COMMIT;Read more: Codeproject
Google Rolls Out Two-Factor Authentication For Everyone. You Should Use It
Posted by
jasper22
at
11:17
|

Given how much data we’re trusting to online sites these days — email, search history, even voice calls — the repercussions to having our account passwords phished, hacked, or guessed are worse than ever. Unfortunately as far as consumers are concerned, account security has been stagnant for years: nearly every service requires a username and password, and that’s it. Cue the scary music and a Dateline special on having your identity stolen. But today, Google is making things much, much better for those who want it. Update: Google is actually rolling this out over the next few days, so you may not see it quite yet.The feature is called two-factor authentication, and it’s been available to Google Apps customers since September. Now it’s rolling out to everyone. It’s a bit confusing and the set-up process will probably intimidate a lot of people, but it’s well worth looking into if you value your account data. You can activate it by hitting the ‘two-step verification’ link on this page. So what exactly does it do? In short, it makes it so that when you go to login to your Google account, you need to enter both your existing password and a special new second passcode — one that you don’t have to write down or memorize because it’s always changing, so it’s nearly impossible to phish. You generate this second password by firing up a new mobile app available for Android, iPhone, and BlackBerry called ‘Google Authenticator’, or by having Google call or send you a text message to a phone number you entered when you set up the feature. That password will expire in just a few minutes though, so be quick (and yes, you will feel like a secret agent the first few times you use it). Read more: Techcrunch
Building a database installer with WiX, datadude and Visual Studio 2010
Posted by
jasper22
at
11:16
|
Today I have been using Windows Installer XML (WiX) to build an installer (.msi file) that would install a SQL Server database on a server of my choosing; the source code for that database lives in datadude (a tool which you may know by one of quite a few other names). The basis for this work was a most excellent blog post by Duke Kamstra entitled Implementing a WIX installer that calls the GDR version of VSDBCMD.EXE which coves the delicate intricacies of doing this – particularly how to call Vsdbcmd.exe in a CustomAction. Unfortunately there are a couple of things wrong with Duke’s post:
Read more: SSIS Junkie
- Searching for “datadude wix” didn’t turn it up in the first page of search results and hence it took me a long time to find it. And I knew that it existed. If someone else were after a post on using WiX with datadude its likely that they would never have come across Duke’s post and that would be a great shame because its the definitive post on the matter.
- It was written in October 2009 and had not been updated for Visual Studio 2010.
- In VS2010 datadude’s output files have changed from being called Database.<suffix> to <ProjectName>_Database.<suffix>. Duke’s code was referencing the old file name formats.
- Duke used $(var.SolutionDir) and relative paths to point to datadude artefacts I have replaced these with Votive Project References http://wix.sourceforge.net/manual-wix3/votive_project_references.htm
- I commented out all references to MicrosoftSqlTypesDbschema in DatabaseArtifacts.wxi. I don't think this is produced in VS2010 (I may be wrong about that but it wasn't in the output from my project)
- Similarly I commented out component MicrosoftSqlTypesDbschema in VsdbcmdArtifacts.wxi. It wasn't where Duke's code said it should have been so am assuming/hoping it isn't needed.
Read more: SSIS Junkie
Securing your SSH Server
Posted by
jasper22
at
11:14
|
One of the most common questions that I see in my favorite IRC channel is: "How can I secure sshd on my server?" There's no single right answer, but most systems administrators combine multiple techniques to provide as much security as possible with the least inconvenience to the end user. Here are my favorite techniques listed from most effective to least effective:SSH key pairsBy disabling password-based authentication and requiring ssh key pairs, you reduce the chances of compromise via a brute force attack. This can also help you protect against weak account passwords since a valid private key is required to gain access to the server. However, a weak account password is still a big problem if you allow your users to use sudo. If you're new to using ssh keys, there are many great guides that can walk you through the process.FirewallLimiting the source IP addresses that can access your server on port 22 is simple and effective. However, if you travel on vacation often or your home IP address changes frequently, this may not be a convenient way to limit access. Acquiring a server with trusted access through your firewall would make this method easier to use, but you'd need to consider the security of that server as well. The iptables rules would look something like this:iptables -A INPUT -j ACCEPT -p tcp --dport 22 -s 10.0.0.20
iptables -A INPUT -j ACCEPT -p tcp --dport 22 -s 10.0.0.25
iptables -A INPUT -j DROP -p tcp --dport 22
iptables -A INPUT -j ACCEPT -p tcp --dport 22 -s 10.0.0.25
iptables -A INPUT -j DROP -p tcp --dport 22
Use a Non-Standard PortI'm not a big fan of security through obscurity and it doesn't work well for ssh. If someone is simply scanning a subnet to find ssh daemons, you might not be seen the first time. However, if someone is targeting you specifically, changing the ssh port doesn't help at all. They'll find your ssh banner quickly and begin their attack. If you prefer this method, simply adjust the Port configuration parameter in your sshd_config file.Limit Users and GroupsRead more: Codeproject
Testing a web service using “wireshark”
Posted by
jasper22
at
11:13
|
Wireshark is a well known network protocol analyzer, which further can be used to monitor web service communications as well.Here, I am going to briefly note how this tool can be used to test the web service that we have developed in our previous blog post examples. (i.e. StudentService) How to install wireshark on Linux?Just type “sudo apt-get install wireshark”.How to run wireshark on Linux?Just type “sudo wireshark” at the command prompt. You will see a page with a “interface list”. Chose the correct interface that you can test your web service. In my case I select the interface, which listens to 127.0.0.1. (Since I am running the Server and Client on the same machine for demonstration purposes) This may vary depending on your testing platform. Read more: The web space of Crishantha Nanayakkara
shared_ptr – Advanced STL, Part 1
Posted by
jasper22
at
11:13
|
Part 1 of my video lecture series exploring the Standard Template Library’s implementation is now available. In this part, I explain how some of shared_ptr’s magic works, including type erasure and make_shared<T>()’s optimizations that save both space and time. This advanced series assumes that you’re familiar with C++ and the STL’s interface, but not the STL’s implementation. If you haven’t used the STL extensively yet, I recommend watching my introductory series. For reference, here are all of the links: [STL Introduction]
(sequence containers)
[Advanced STL]
Part 1 (shared_ptr)Read more: Visual C++ Team Blog
(sequence containers)
Part 2 (associative containers)
Part 3 (smart pointers)
Part 4 (Nurikabe solver) - see Wikipedia's article and my updated source code
Part 5 (Nurikabe solver, continued)
Part 6 (algorithms and functors)
Part 7 (algorithms and functors, continued)
Part 8 (regular expressions)
Part 9 (rvalue references)
Part 10 (type traits)
[Advanced STL]
Part 1 (shared_ptr)Read more: Visual C++ Team Blog
How to Add a Checkbox to a List View Column Header
Posted by
jasper22
at
11:11
|
IntroductionThere doesn't appear to be much, if any, example code of how to place a checkbox in the column header of a list view control. This can be used to add "check/uncheck all" functionality if you're using LVS_EX_CHECKBOXES in your list view window style to display a check box next to each item. Unfortunately, the method used here only works with Windows Vista/Server 2008 and later. It appears to fail gracefully (no checkbox is displayed) when run on XP, but extensive testing has not been done.Background The list view control does not expose a way to add a checkbox to a column heading directly. It creates a Header control to display the column headings. A handle to this control can be obtained with the ListView_GetHeader() macro (or equivilent message) with which you can then manipulate. Using the codeThe sample project included was generated with VS2010 using the WTL AppWizard. Neither ATL nor WTL are needed for this technique to work. The code relevant to this method has actually been written using the SDK macros. You can of course use ATL/WTL helpers to make life easier. The sample app is simply a modal dialog application with a list view control.We'll throw some initialization code in our OnInitDialog method. First, we'll save the HWND of the list view control to a member variable for easy access later. Then, we add some styles to the control so it will display checkboxes and select the full row when clicked: // Grab the window handle for our list view
m_list = GetDlgItem(IDC_LIST);// Set some styles for the list view control. We want checkboxes and full row select.
ListView_SetExtendedListViewStyle(m_list, LVS_EX_CHECKBOXES | LVS_EX_FULLROWSELECT);
Next, we'll actually create the columns. The first column will hold only the checkbox:// Add some columns to the list view control
LVCOLUMN lvc = {0};
ListView_InsertColumn(m_list, 0, &lvc);
lvc.mask = LVCF_TEXT;
lvc.iSubItem++;
lvc.pszText = _T("First Name");
ListView_InsertColumn(m_list, 1, &lvc);
lvc.iSubItem++;
lvc.pszText = _T("Last Name");
ListView_InsertColumn(m_list, 2, &lvc);
lvc.iSubItem++;
lvc.pszText = _T("Company");
ListView_InsertColumn(m_list, 3, &lvc);// Set column widths
ListView_SetColumnWidth(m_list, 0, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 1, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 2, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 3, LVSCW_AUTOSIZE_USEHEADER);And here's where the magic starts. First, we obtain the HWND to the header control used by the list view. Then, we can modify it's window style to add the HDS_CHECKBOXES style which will allow us to display a checkbox in the header. If we don't do this, the control will not render a checkbox. We also store the control ID for later use by our message handler so we can detect when someone clicks the checkbox: // Here's where we can add the checkbox to the column header
// First, we need to snag the header control and give it the
// HDS_CHECKBOXES style since the list view doesn't do this for us
HWND header = ListView_GetHeader(m_list);
DWORD dwHeaderStyle = ::GetWindowLong(header, GWL_STYLE);Read more: Codeproject
m_list = GetDlgItem(IDC_LIST);// Set some styles for the list view control. We want checkboxes and full row select.
ListView_SetExtendedListViewStyle(m_list, LVS_EX_CHECKBOXES | LVS_EX_FULLROWSELECT);
Next, we'll actually create the columns. The first column will hold only the checkbox:// Add some columns to the list view control
LVCOLUMN lvc = {0};
ListView_InsertColumn(m_list, 0, &lvc);
lvc.mask = LVCF_TEXT;
lvc.iSubItem++;
lvc.pszText = _T("First Name");
ListView_InsertColumn(m_list, 1, &lvc);
lvc.iSubItem++;
lvc.pszText = _T("Last Name");
ListView_InsertColumn(m_list, 2, &lvc);
lvc.iSubItem++;
lvc.pszText = _T("Company");
ListView_InsertColumn(m_list, 3, &lvc);// Set column widths
ListView_SetColumnWidth(m_list, 0, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 1, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 2, LVSCW_AUTOSIZE_USEHEADER);
ListView_SetColumnWidth(m_list, 3, LVSCW_AUTOSIZE_USEHEADER);And here's where the magic starts. First, we obtain the HWND to the header control used by the list view. Then, we can modify it's window style to add the HDS_CHECKBOXES style which will allow us to display a checkbox in the header. If we don't do this, the control will not render a checkbox. We also store the control ID for later use by our message handler so we can detect when someone clicks the checkbox: // Here's where we can add the checkbox to the column header
// First, we need to snag the header control and give it the
// HDS_CHECKBOXES style since the list view doesn't do this for us
HWND header = ListView_GetHeader(m_list);
DWORD dwHeaderStyle = ::GetWindowLong(header, GWL_STYLE);Read more: Codeproject
Subscribe to:
Comments (Atom)






