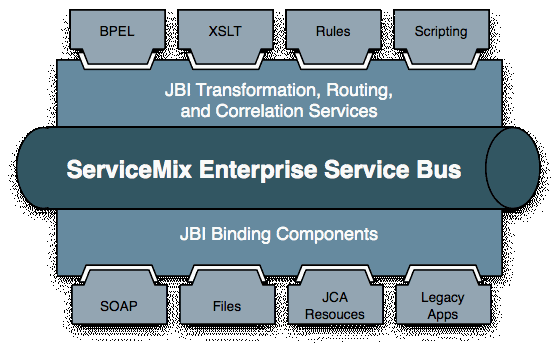
Apache ServiceMix is a runtime container for service-oriented architecture components, web services or legacy system connectivity services. It is one of the most mature, open-source implementations of an enterprise service bus and an Apache top-level project.
In this article we will take a look at what ServiceMix is and how it can be put to use.
Web Site:
http://servicemix.apache.orgVersion discussed: Apache ServiceMix 3.3, FUSE ESB 3.4
License & Pricing: Open Source with commercial support and packaging by FuseSource
Support: User mailing list, developer mailing list, Internet Relay Chat, FuseSource forums. Only the book "Open-Source ESBs in Action" by Manning is currently available.
Introduction
Before directly starting to discuss what Apache ServiceMix can be used for, a general understanding of the enterprise service bus acronym should be given. Since it is not a framework suited for everyday usage like Spring, the general context of its application is important.
Enterprise Service Bus (ESB) principle
Apache ServiceMix is an implementation of an enterprise service bus in the Java programming language.
In a typical enterprise environment, there are several applications installed. Most probably they are from different vendors and offer very diverse interfaces. The corporate IT commonly faces two challenges these days:
Exchange of data between different systems
Creation of new functionality by combining existing function block from these applications
In the past, these issues were tackled by proprietary product suites, which often were highly specialized and not able to cover a wide range of corporations' needs.
The development and adoption of web service technology is thought to solve these issues, as a common transport and description format now exists. Nonetheless, this needs to be provided, implemented and supported by the applications. Also, a single call often is not sufficient, but routing and combination logic needs to be employed, as well. To simplify these tasks, Gartner came up with the idea of an infrastructure component, which uses a harmonized way of exchanging data (messages) and provided such reusable core functionality.
This component should not only exchange messages but also incorporate the ability to route messages from one component to another component. These requirements were bundled into the term "enterprise service bus" (ESB). In contrast to enterprise application integration (EAI), the ESB concept goes beyond the mere connectivity and data exchange principles and focuses on reuse. By exposing application functionality to an ESB, new applications can be built that leverage data and services already created. These are then called "composite applications", as they can be thought off as a meta-level, creating applications from applications, instead of components or frameworks. This functionality can also be leveraged without using an enterprise service bus, but for the typical everyday challenges, a bus greatly simplifies things, since it is prepackaged with components and standard functionality.
Java Business Integration (JBI)
To standardize the ESB concept, the Java Community Process (JCP) came up with the JBI standard, short for Java Business Integration. It describes all components, which can be found in the ESB concept, matched to Java terminology and interfaces.
Read more:
Methods & Tool Posted via email from Jasper-net




 Yesterday we reported on Path’s new $8.5 million venture round, led by Kleiner Perkins and Index Ventures. I was curious about the valuation and pulled on a couple of threads. What unraveled was a stunning story about a startup that almost ran out of cash, a rebuffed $100+ million buyout offer from Google, and, finally, a new round of financing. Path is still very small, with just “hundreds of thousands” of users, said the company yesterday. It’s a private mobile network limited to just 50 friends, which makes viral spreading difficult. But we’re also hearing that 20% of active users are using it daily – a Zynga-like engagement rate that is a sign that at least some people really connect with Path. In early December Path had a signed term sheet with Kleiner Perkins and Index. At that point Google made a move, eventually offering $100 million for the company plus an earnout of $25 million to be paid over four years. Taking that Google offer would seem to most people like a no brainer. And for founders like Dustin Mierau, who haven’t had liquidity events, a life changing experience. Read more:
Yesterday we reported on Path’s new $8.5 million venture round, led by Kleiner Perkins and Index Ventures. I was curious about the valuation and pulled on a couple of threads. What unraveled was a stunning story about a startup that almost ran out of cash, a rebuffed $100+ million buyout offer from Google, and, finally, a new round of financing. Path is still very small, with just “hundreds of thousands” of users, said the company yesterday. It’s a private mobile network limited to just 50 friends, which makes viral spreading difficult. But we’re also hearing that 20% of active users are using it daily – a Zynga-like engagement rate that is a sign that at least some people really connect with Path. In early December Path had a signed term sheet with Kleiner Perkins and Index. At that point Google made a move, eventually offering $100 million for the company plus an earnout of $25 million to be paid over four years. Taking that Google offer would seem to most people like a no brainer. And for founders like Dustin Mierau, who haven’t had liquidity events, a life changing experience. Read more: 








 Parallel Nsight Professional Edition is now available for all Visual Studio 2008 and 2010 developers, free of charge. NVIDIA is now offering the full Parallel Nsight Pro feature set at no cost, as we historically have done with CUDA and our other development tools, so that a broader range of developers can take advantage of the full benefits of this popular parallel computing development tool. Parallel Nsight support will continue via the Parallel Nsight forums, and Professional developers are encouraged to sign up for NVIDIA’s Registered Developer Program, which provides priority access to new software, bug management tools, invitations to members-only developer webinars and other development resources. Simply register your name and email address and follow the steps below to acquire Read more:
Parallel Nsight Professional Edition is now available for all Visual Studio 2008 and 2010 developers, free of charge. NVIDIA is now offering the full Parallel Nsight Pro feature set at no cost, as we historically have done with CUDA and our other development tools, so that a broader range of developers can take advantage of the full benefits of this popular parallel computing development tool. Parallel Nsight support will continue via the Parallel Nsight forums, and Professional developers are encouraged to sign up for NVIDIA’s Registered Developer Program, which provides priority access to new software, bug management tools, invitations to members-only developer webinars and other development resources. Simply register your name and email address and follow the steps below to acquire Read more: