QR:
Tizen Source Code Released
news that developers for the Tizen project, an open source mobile OS based on MeeGo (itself a child of Moblin and Maemo), have posted a preview of their source code and SDK. They warn, "Please keep in mind that this is a very early preview and is not yet designed for use to create production applications. Further enhancements and improvements to Tizen and its development environment will continue as we work towards a formal release over the coming months." The source code is available here. Read more: Slashdot
QR:
QR:
גל פריצות נוסף: הפעם מוסדות אקדמים ואתר הכרויות
Posted by
jasper22
at
17:51
|

האקרים פרו פלשתינים ממשיכים את מסע תקיפות הסייבר כנגד אתרים ישראלים, על הכוונת עלו הפעם אתרים של אוניברסיטת בר-אילן, הטכניון, אתר חדשות מקומיות וככל הנראה גם אתר הכרויות. מההודעה שפרסמו הפורצים, טוענים אלה כי הצליחו לחדור למאגרי המידע של אותם גופים ולשלוף משם את הפרטים האישיים של המשתמשים השונים.
טענות לרובהפורצים גם הפעם, כפי שקרה בעת האחרונה, מפרסמים באותו אתר את הודעתם. בתוך ההודעה נטען, כי הם הצליחו לפרוץ למגוון רחב של אתרים במתחם הישראלי (co.il), כולל אתרים מסחריים, אתרים אקדמאיים, ואתרים בתת-המתחמים org.il ו-gov.il. ומציינים ספציפית מספר אתרים, ביניהם אתר של מחלקת הגיאוגרפיה של אוניברסיטת בר-אילן, אתר קישורים פיקטוגרפיים, אתר חדשות הקריות והאתר של הפקולטה לרפואה של הטכניון. בפועל, בדיקת החומרים שפורסמו מעלה שגם אתר הכרויות שלא צוין שמו במפורש נפרץ, שכן חלק מהחומרים שפרסמו הפורצים כוללים מידע אישי שיש להניח שהגיע מאתר שכזה, כגון פרטים אישיים ולצידם תיאורים מילולים בעלי גוון ספציפי המתארים את האדם ואישיותו.
Comcast DNSSEC Goes Live
Posted by
jasper22
at
17:50
|
In a blog post, Comcast's Jason Livingood has announced that Comcast has signed all of its (5000+) domains in addition to having all of its customers using DNSSEC-validating resolvers. He adds, 'Now that nearly 20 million households in the U.S. are able to use DNSSEC, we feel it is an important time to urge major domain owners, especially commerce and banking-related sites, to begin signing their domain names. Read more: Slashdot
QR:
QR:
Toshiba FlashAir wireless LAN SD card hands-on (video)
Posted by
jasper22
at
16:50
|

The first card using the SD association's Wireless LAN standard is Toshiba's FlashAir and we've just spent some time with it here at CES. It's much like existing Eye-Fis insofar that it also crams WiFi into a diminutive SD card, but instead of merely being able to join a network, the FlashAir creates its own outright. The 8GB class six card broadcasts an 802.11b/g/n hotspot, replete with its own web server onboard, which means its contents -- like say pictures you've previously snapped in your camera -- can be accessed in a browser by any connected device. Read more: Engadget
QR:
Lion UX Pack Transforms Windows 7 To Mac OS X Lion User Interface
Posted by
jasper22
at
16:48
|

Those of you who have been regularly following AddictiveTips, would know that we have covered a number of elegant skin packs for our readers in the past, including the Android , Mango, iOS, Windows 8 and the Ubuntu Skin Pack. Most of these skin packs were developed by Hamed, and required following a simple setup wizard for getting the job done, instead of going through any complex theme patching methods. Recently, we cam across a Mac OS X Lion skin pack that was even easier to install than the previously reviewed Lion Skin Pack. The Lion UX Pack has been designed to instantly transform your Windows 7 system into a Mac OS X Lion style desktop. You can simply install the Lion UX Pack by launching the setup file, selecting the system font, dock configuration (enabled, disabled or auto-hide), and selecting other OS X UI elements that you want, including the start orb, caption button, expose feature and spaces. Click Install to transform your Windows 7 desktop. Read more: Addictive tips
QR:
How To Improve Database Performance Without Changing Code
Posted by
jasper22
at
13:45
|
I hear it all the time. It’s a familiar refrain. Most of the time it is innocent enough, and understandable. But there are times when hearing those words are like hearing the screech of fingernails on a chalkboard: “We can’t change the code.”There you are, listening to someone complain to you about the database server, and wanting you to fix the problem. You examine the situation and can see an easy code change that would improve performance immediately only to be told “no code changes allowed”. Your heart sinks. You get frustrated that they won’t make any code changes. The user gets frustrated that you don’t have any other options to offer. You ask about changing a stored procedure, or rewriting a view definition, or helping to redesign a few tables from the ‘database’ that is nothing more than an Excel spreadsheet. “No”, “no”, and “no” you are told, along with “stop blaming the code, you always blame the code!” You are at an impasse. You wish you had a handy list of things to try.And now you do.Here are six ways you can improve database performance without changing code, listed in no particular order. They have different levels of difficulty but they all have something in common: no code changes necessary. And your end user will be happy that you can provide them some options. 1. Utilize a proper indexing strategyI know I said “no code changes”, but indexes are more of a schema change than a code change. And unless you have code that utilizes index hints, you shouldn’t have to worry too much about needing to change code to avoid using an index. There are more than a handful of blogs out there that talk about missing or unused indexes. I will point you to the MSDN article on how to find missing indexes, as that is likely to be the most useful for you. I will also give you this caveat: adding indexes is not always the right thing to do! You need to be aware of all the activity hitting the underlying table. If you decide to create an index to improve a specific query run monthly to generate a report, you could be doing a disservice to the hourly DUIs (Deletes, Updates, Inserts) that are happening. Be aware of the overall usage before you just start adding indexes for performance. As for eliminating unused indexes, I would caution you there to make certain you know that the index is truly not being used. If you have been looking at index usage for the past week and find a few hundred that haven’t been touched, don’t go around dropping them because they could very well be used on a monthly basis. Again, know the system and workloads a bit before making these changes. One thing you are likely to be able to do right away is to remove duplicate indexes. A proper indexing strategy would involve the periodic investigation into finding indexes that are missing, that are duplicates, and are unused.2. Add memoryEverything SQL Server does *has* to go through memory. Every query you run *has* to read/write pages from/to memory. So why not make certain you have enough memory on your server in order to store as many pages as possible? No, I can’t think of any reason either. Read more: SqlServerPedia
QR:
QR:
[Limited Time] "Nmap Cookbook: The Fat-free Guide to Network Scanning" Currently free for the Kindle...
Posted by
jasper22
at
13:44
|
Nmap(r) Cookbook: The fat-free guide to network scanning provides simplified coverage of network scanning features available in the Nmap suite of utilities. Every Nmap feature is covered with visual examples to help you quickly understand and identify proper usage for practical results. Topics covered include: Installation on Windows, Mac OS X, Unix/Linux platforms
Basic and advanced scanning techniques
Network inventory and security auditing
Firewall evasion techniques
Zenmap - A graphical front-end for Nmap
NSE - The Nmap Scripting Engine
Ndiff - A Nmap scan comparison utilityFormat: Kindle Edition
File Size: 2730 KB
Publisher: CreateSpace (January 27, 2010)
Sold by: Amazon Digital Services
Language: English
ASIN: B005ZK84NU
Text-to-Speech: Enabled
Lending: Enabled
Average Customer Review: 4.6 out of 5 stars See all reviews (10 customer reviews)
Amazon Best Sellers Rank: #431 Free in Kindle Store (See Top 100 Free in Kindle Store) Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: Nmap Cookbook: The Fat-free Guide to Network Scanning
QR:
Basic and advanced scanning techniques
Network inventory and security auditing
Firewall evasion techniques
Zenmap - A graphical front-end for Nmap
NSE - The Nmap Scripting Engine
Ndiff - A Nmap scan comparison utilityFormat: Kindle Edition
File Size: 2730 KB
Publisher: CreateSpace (January 27, 2010)
Sold by: Amazon Digital Services
Language: English
ASIN: B005ZK84NU
Text-to-Speech: Enabled
Lending: Enabled
Average Customer Review: 4.6 out of 5 stars See all reviews (10 customer reviews)
Amazon Best Sellers Rank: #431 Free in Kindle Store (See Top 100 Free in Kindle Store) Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: Nmap Cookbook: The Fat-free Guide to Network Scanning
QR:

How to deploy Mono projects with Heroku
Posted by
jasper22
at
13:43
|
Last week I mentioned how I had successfully deployed Nancy / Mono (C# frameworks) onto Heroku. This post covers how you can deploy your own Mono projects onto Heroku.As before, this approach is completely unsupported by Heroku and I'm not 100% sure if it's production ready. I would love to hear your experiences. 0) Prerequisites
There are a few requirements before deploying a project.
- The solution can compile using Mono on Linux (Ubuntu 10.04 - Lucid Lynx).
- The launch application must be a self-hosted executable.
- The self-hosted executable must stay alive and not exit. Example: https://github.com/BenHall/nancy-demo-hosting-self/blob/master/src/Program.cs#L20-23 1) Update heroku gem
Before you continue, make sure your running the latest heroku gem as you need the buildpack option which is only supported in later versions. Thanks Andy Pike for pointing this out.$ gem update heroku
2) Listening to Heroku requests
This is the only part which I'm not too happy with. In order for Mono to accept Heroku requests, you need to bind the listener to the full hostname provided by Heroku - for example http://deep-moon-1452.herokuapp.com. The application also needs to listen on a particular port randomly defined by Heroku. This is provided via an environment variable. Example:
https://github.com/BenHall/nancy-demo-hosting-self/blob/master/src/Program.cs#L12
Read more: Ben Hall's blog
QR:
There are a few requirements before deploying a project.
- The solution can compile using Mono on Linux (Ubuntu 10.04 - Lucid Lynx).
- The launch application must be a self-hosted executable.
- The self-hosted executable must stay alive and not exit. Example: https://github.com/BenHall/nancy-demo-hosting-self/blob/master/src/Program.cs#L20-23 1) Update heroku gem
Before you continue, make sure your running the latest heroku gem as you need the buildpack option which is only supported in later versions. Thanks Andy Pike for pointing this out.$ gem update heroku
2) Listening to Heroku requests
This is the only part which I'm not too happy with. In order for Mono to accept Heroku requests, you need to bind the listener to the full hostname provided by Heroku - for example http://deep-moon-1452.herokuapp.com. The application also needs to listen on a particular port randomly defined by Heroku. This is provided via an environment variable. Example:
https://github.com/BenHall/nancy-demo-hosting-self/blob/master/src/Program.cs#L12
Read more: Ben Hall's blog
QR:
BugAid - Enhanced C# Debugging tool (and free for non-commercial open source projects too)
Posted by
jasper22
at
12:49
|

We here at BugAid Software are really big fans of the .NET open source community. From NuGet to NHibernate to NUnit, you can hardly do any serious .NET development work today without coming to rely on these great collaborations between people from different countries, working together to create quality software for the benefit of us all. “BugAid for Visual Studio”, specifically, relies on the excellent SharpDevelop libraries for all of our code parsing and semantic analysis. It’d be fair to say that without the passion, hard work, and huge talent of the people who’ve contributed to these libraries, our project would not have been possible. Furthermore, we’ve come to rely on Google Code Search as an indispensable tool in our day-to-day work. With this in mind, we’ve decided to announce that “BugAid for Visual Studio” is now free (as in beer and nachos) for non-commercial open source development. If you are actively engaged in .NET open source development, now would be the time to apply for your free one-year license! Please note though, that the BugAid Open Source license can only be used for non-commercial open source development, so if you’re an open source hacker by night and a cubicle warrior by day, you’ll still need to ask your boss to buy a corporate license for you to use at work. Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: BugAid is free for non-commercial open source projects!
QR:
Install Cuda and Use Managed Code with VS 2008 Express on Windows 7-x64
Posted by
jasper22
at
12:47
|
IntroductionGetting NVidia Cuda up and running when you are on a Visual Studio Express budget can be frustrating, particularly if you want to access Cuda functions from managed code. There are plenty of resources on line to help you on your way but you have to combine information from different sources – while avoiding certain dead ends. It’s a little hit and miss. I hope you can benefit from my journey so far. For now, I decided to keep it simple: use VS 2008 Express, write my own wrappers, and stick to the x86 platform. Here’s how I succeeded:
Background I have not configured Cuda for VS 2010 Express. I understand that part of the process requires configuring your 2010 project to use the VS 2008 (VC 90) compiler instead of the VS 2010 (VC100) compiler. Most likely there are a few other hacks required to get things going. There appear be some resources that provide direction on doing this. In particular, I saw one article that looks promising at http://blog.cuvilib.com/2011/02/24/how-to-run-cuda-in-visual-studio-2010/ Running managed code using configurations other than x86 did not work for me. There are several convoluted posts on the web concerning this configuration with VS Express. Google search “Visual C++ 2008 Express Edition And 64-Bit Targets” for some entertaining ways to break your VS Express install. Working out the install in a virtual machine first is a good idea but it was unclear to me how to access the host’s GPU hardware directly from my guest machine. My VBox virtual graphics adapter is not Cuda enabled and, as best I can tell, Cuda no longer easily supports the emulator mode. So I used the standard technique: make mistakes, break the install, reinstall, and follow the smoke. I am particularly interested in Fourier transforms on the GPU. Only a few of the canned wrappers sport CUFFT functionality. Cudafy (CodePlex) seemed the most promising but it’s not (yet) an out of the box set-up when you have VS Express.
Read more: Codeproject
QR:
Background I have not configured Cuda for VS 2010 Express. I understand that part of the process requires configuring your 2010 project to use the VS 2008 (VC 90) compiler instead of the VS 2010 (VC100) compiler. Most likely there are a few other hacks required to get things going. There appear be some resources that provide direction on doing this. In particular, I saw one article that looks promising at http://blog.cuvilib.com/2011/02/24/how-to-run-cuda-in-visual-studio-2010/ Running managed code using configurations other than x86 did not work for me. There are several convoluted posts on the web concerning this configuration with VS Express. Google search “Visual C++ 2008 Express Edition And 64-Bit Targets” for some entertaining ways to break your VS Express install. Working out the install in a virtual machine first is a good idea but it was unclear to me how to access the host’s GPU hardware directly from my guest machine. My VBox virtual graphics adapter is not Cuda enabled and, as best I can tell, Cuda no longer easily supports the emulator mode. So I used the standard technique: make mistakes, break the install, reinstall, and follow the smoke. I am particularly interested in Fourier transforms on the GPU. Only a few of the canned wrappers sport CUFFT functionality. Cudafy (CodePlex) seemed the most promising but it’s not (yet) an out of the box set-up when you have VS Express.
Read more: Codeproject
QR:
NetTcpBinding Configurations for WCF and Silverlight Application on IIS 7
IntroductionIn this article, I would like to give a brief idea on using NetTcpBinding with Silverlight application and hosting configuration to be done on IIS 7.Note: Only IIS7 has support for net.tcp binding. One of the most important features in Silverlight 4 is the introduction of NetTcpBinding support; we can communicate with a WCF service using net.tcp protocol.
Advantages of using NetTcpBinding Performance: Silverlight applications using NetTcpBinding communicates with WCF service in your intranet zone. Performance of NetTcpBinding compared to HTTP polling duplex is the key reason to consider using the WCF net.tcp protocol in duplex communication scenarios. NetTcpBinding offers major performance gains when compared to httpPollingDuplex on these parameters:
Increase in throughput of data notifications a client application can receive from the server.
Increase in the maximum number of connected clients the server can support concurrently.
Duplex Communication: Supports Duplex communication between client and service.
IDE Integration: Net.tcp protocol is well integrated with the Add Service Reference feature in Visual Studio 10. A WCF service proxy to a WCF service exposed using the net.tcp binding can be easily generated for a Silverlight 4 client application. Net.tcp protocol comes with Silverlight configuration support (ServiceReferences.ClientConfig), so the details of the binding, including service address, can be changed without recompiling the application.
Improved library factoring to help optimize the Silverlight application (XAP) size. Applications that utilize only request/response exchange patterns using WCF have all the required components available in Silverlight core. Applications that require duplex message exchange patterns must include the System.ServiceModel.Extensions.dll in the XAP, as well as one or both of System.ServiceModel.NetTcp.dll and System.ServiceModel.PollingDuplex.dll, depending on the protocol the application is using. System.ServiceModel.Extensions.dll contains functionality common for all duplex communication scenarios. System.ServiceModel.NetTcp.dll supports the WCF net.tcp protocol and System.ServiceModel.PollingDuplex.dll the HTTP polling duplex protocol. When a proxy is created in a Silverlight 4 project using the Add Service Reference feature of Visual Studio 10, appropriate library references will be added to the project depending on the actual protocols the WCF service exposes. Note: NetTcpBinding is subject to TCP port limitations, Silverlight applications with NetTcpBinding can run only on ports 4502-4534.
Read more: Codeproject
QR:
Advantages of using NetTcpBinding Performance: Silverlight applications using NetTcpBinding communicates with WCF service in your intranet zone. Performance of NetTcpBinding compared to HTTP polling duplex is the key reason to consider using the WCF net.tcp protocol in duplex communication scenarios. NetTcpBinding offers major performance gains when compared to httpPollingDuplex on these parameters:
Increase in throughput of data notifications a client application can receive from the server.
Increase in the maximum number of connected clients the server can support concurrently.
Duplex Communication: Supports Duplex communication between client and service.
IDE Integration: Net.tcp protocol is well integrated with the Add Service Reference feature in Visual Studio 10. A WCF service proxy to a WCF service exposed using the net.tcp binding can be easily generated for a Silverlight 4 client application. Net.tcp protocol comes with Silverlight configuration support (ServiceReferences.ClientConfig), so the details of the binding, including service address, can be changed without recompiling the application.
Improved library factoring to help optimize the Silverlight application (XAP) size. Applications that utilize only request/response exchange patterns using WCF have all the required components available in Silverlight core. Applications that require duplex message exchange patterns must include the System.ServiceModel.Extensions.dll in the XAP, as well as one or both of System.ServiceModel.NetTcp.dll and System.ServiceModel.PollingDuplex.dll, depending on the protocol the application is using. System.ServiceModel.Extensions.dll contains functionality common for all duplex communication scenarios. System.ServiceModel.NetTcp.dll supports the WCF net.tcp protocol and System.ServiceModel.PollingDuplex.dll the HTTP polling duplex protocol. When a proxy is created in a Silverlight 4 project using the Add Service Reference feature of Visual Studio 10, appropriate library references will be added to the project depending on the actual protocols the WCF service exposes. Note: NetTcpBinding is subject to TCP port limitations, Silverlight applications with NetTcpBinding can run only on ports 4502-4534.
Read more: Codeproject
QR:
Deploying WCF and Silverlight Applications on IIS 5 and 7
Posted by
jasper22
at
15:55
|
Contents
- 3.1 Check for IIS in the server machine
- 3.2. Hosting a WCF service on IIS 5
- 3.3. Testing the WCF service
- 4.1. Installing IIS 7 in the machine
- 4.2. Hosting the WCF service on IIS 7
- 4.3. Testing the WCF service
1. Prerequisites
In this article I would like to dive into the configuration and deployment of WCF services used by a Silverlight client on IIS 5 and IIS 7.
1.1 Server side
You should have installed the following: Windows XP or Window 7IIS installed
.NET Framework 3.5 or 4.0 (recommended)1.2 Client side
Silverlight 2, 3, or 4 (preferably the right version of Silverlight; if the right version is not used, the Silverlight application would be non-functional).
1.3. Local Area Network
A Local Area Network is essential to test our application.
2. Creation of a WCF Service
To create a WCF service, you have to define the Service Contract that has to be exposed to the client. An example of a service contract interface for a calculator service is shown below:Read more: Codeproject
QR:
Are you ready for slow reading?
Posted by
jasper22
at
15:52
|
Imagine a line at a fast food restaurant that serves two types of burgers, and a customer at the cashier is stuck for a while deciding what he wants to order, making the rest of the line anxious, slowing down the business. Now imagine a line at the same restaurant, but with a sign saying "think ahead of your order," which is supposed to speed things up. But now the customer orders hundreds of burgers, pays, and the line is stuck again, because he can take only 5 burgers at time to his car, making signs ineffective. While developing the slowhttptest tool, I thought about this burger scenario, and became curious about how HTTP servers react to slow consumption of their responses. There are so many conversations about slowing down requests, but none of them cover slow responses. After spending a couple of evenings implementing proof-of-concept code, I pointed it to my so-many-times-tortured Apache server and, surprisingly, got a denial of service as easily as I got it with slowloris and slow POST. Let me remind you what slowloris and slow POST are aiming to do: A Web server keeps its active connections in a relatively small concurrent connection pool, and the above-mentioned attacks try to tie up all the connections in that pool with slow requests, thus causing the server to reject legitimate requests, as in first reastaurnt scenario. The idea of the attack I implemented is pretty simple: Bypass policies that filter slow-deciding customers, send a legitimate HTTP request and read the response slowly, aiming to keep as many connections as possible active. Sounds too easy to be true, right?
Crafting a Slow ReadLet’s start with a simple case, and send a legitimate HTTP request for a resource without reading the server’s response from the kernel receive buffer.We craft a request like the following: GET /img/delivery.png HTTP/1.1
Host: victim
User-Agent: Opera/9.80 (Macintosh; Intel Mac OS X 10.7.0; U; Edition MacAppStore; en) Presto/2.9.168 Version/11.50
Referer: http://code.google.com/p/slowhttptest/ Read more: Qualys Security Labs
QR:
Crafting a Slow ReadLet’s start with a simple case, and send a legitimate HTTP request for a resource without reading the server’s response from the kernel receive buffer.We craft a request like the following: GET /img/delivery.png HTTP/1.1
Host: victim
User-Agent: Opera/9.80 (Macintosh; Intel Mac OS X 10.7.0; U; Edition MacAppStore; en) Presto/2.9.168 Version/11.50
Referer: http://code.google.com/p/slowhttptest/ Read more: Qualys Security Labs
QR:
Уязвимости серверов к медленному чтению
Posted by
jasper22
at
15:49
|
Приветствую.
Хочу рассказать, чем я баловался в свободное от работы в Qualys время. Так как в англоязычном интернете на удивление много шума про Slow Read DoS attack, и уверен что получу здесь много полезной критики и дельных предложений. В августе 2011 года написал програмку slowhttptest, которая тестирует веб-серверы на наличие уязвимостей, связанных с обработкой медленных HTTP запросов, таких как slowloris и slow HTTP Post. Цель — создать конфигурируемый инструмент, облегчающий работу разработчиков и позволить им концентрироваться на создании эффективных защит, а не ковырянии в питоне, на котором написаны большинство proof-of-concept эксплоитов. А потом решил попробовать, как реагируют серверы на медленное чтение клиентами HTTP респонсов. На удивление плохо реагируют. Дефолтные apache, nginx, lightpd, IIS отказывают в обслуживании на ура.А суть такова: если найти ресурс на веб сервере, который размером больше send buffer-a, который ядро выделило для соединения, в который серверная программа пошлет ресурс, то если каким то образом вынудить ядро не принимать все данные — сервер будет пытаться послать оставшийся кусок данных, занимая ограниченную в размере очередь соединений, процессорное время, память, и свободное время сисадмина. Если забить такими соединяниями всю очередь — сервер, соответственно начнет отказывать в обслуживании быстрым клиентам. Заставить ядро себя так вести довольно просто и описано было еще в 2008 году ребятами из Outpost24 в методе Sockstress: например, посылать в TCP пакете размер окна равным 0, т.е. у клиента нет места для приема данных. Дизайн TCP правильно подразумевает, что приложение, а не ядро обязано контролировать медленные и мертвые соеднинения. Однако за 4 года никто не пошевелил пальцем. Sockstress вручную создает пакеты, высчитывает, когда послать очередное подтверждение, чтоб не ресетнуть persist timer на сервере, сложно короче.
Мой метод даже школьник в состоянии реализовать на практике:
Создаете сокет, задаете сравнительно малый размер receive buffer-а на клиенте, посылаете совершенно целостный и нормальный HTTP запрос на картинку размером 100Кб, например. Сервер берет картинку из памяти, дает ядру, чтоб тот передал ее в сеть. Сервер берет кусок картинки и шлет, клиент принимает первые тыщу байт, и говорит стоп, места нету. Сервер poll-ает сокет, пытаясь понять когда он будет готов к записи, а он не готов! Раз в минуту читаете пару байтов из клиентского receive buffer, чтоб TCP стек послал что то отличное от нуля, тем самым создав видимость живого соедниения для файрволов и IDS-ов. Read more: Habrahabr.ru
QR:
Хочу рассказать, чем я баловался в свободное от работы в Qualys время. Так как в англоязычном интернете на удивление много шума про Slow Read DoS attack, и уверен что получу здесь много полезной критики и дельных предложений. В августе 2011 года написал програмку slowhttptest, которая тестирует веб-серверы на наличие уязвимостей, связанных с обработкой медленных HTTP запросов, таких как slowloris и slow HTTP Post. Цель — создать конфигурируемый инструмент, облегчающий работу разработчиков и позволить им концентрироваться на создании эффективных защит, а не ковырянии в питоне, на котором написаны большинство proof-of-concept эксплоитов. А потом решил попробовать, как реагируют серверы на медленное чтение клиентами HTTP респонсов. На удивление плохо реагируют. Дефолтные apache, nginx, lightpd, IIS отказывают в обслуживании на ура.А суть такова: если найти ресурс на веб сервере, который размером больше send buffer-a, который ядро выделило для соединения, в который серверная программа пошлет ресурс, то если каким то образом вынудить ядро не принимать все данные — сервер будет пытаться послать оставшийся кусок данных, занимая ограниченную в размере очередь соединений, процессорное время, память, и свободное время сисадмина. Если забить такими соединяниями всю очередь — сервер, соответственно начнет отказывать в обслуживании быстрым клиентам. Заставить ядро себя так вести довольно просто и описано было еще в 2008 году ребятами из Outpost24 в методе Sockstress: например, посылать в TCP пакете размер окна равным 0, т.е. у клиента нет места для приема данных. Дизайн TCP правильно подразумевает, что приложение, а не ядро обязано контролировать медленные и мертвые соеднинения. Однако за 4 года никто не пошевелил пальцем. Sockstress вручную создает пакеты, высчитывает, когда послать очередное подтверждение, чтоб не ресетнуть persist timer на сервере, сложно короче.
Мой метод даже школьник в состоянии реализовать на практике:
Создаете сокет, задаете сравнительно малый размер receive buffer-а на клиенте, посылаете совершенно целостный и нормальный HTTP запрос на картинку размером 100Кб, например. Сервер берет картинку из памяти, дает ядру, чтоб тот передал ее в сеть. Сервер берет кусок картинки и шлет, клиент принимает первые тыщу байт, и говорит стоп, места нету. Сервер poll-ает сокет, пытаясь понять когда он будет готов к записи, а он не готов! Раз в минуту читаете пару байтов из клиентского receive buffer, чтоб TCP стек послал что то отличное от нуля, тем самым создав видимость живого соедниения для файрволов и IDS-ов. Read more: Habrahabr.ru
QR:
The Truth About Value Types
Posted by
jasper22
at
15:40
|
As you know if you've read this blog for a while, I'm disturbed by the myth that "value types go on the stack". Unfortunately, there are plenty of examples in our own documentation and in many books that reinforce this myth, either subtly or overtly. I'm opposed to it because: It is usually stated incorrectly: the statement should be "value types can be stored on the stack", instead of the more common "value types are always stored on the stack".
It is almost always irrelevant. We've worked hard to make a managed environment where the distinctions between different kinds of storage are hidden from the user. Unlike some languages, in which you must know whether a particular storage is on the stack or the heap for correctness reasons.
It is incomplete. What about references? References are neither value types nor instances of reference types, but they are values. They've got to be stored somewhere. Do they go on the stack or the heap? Why does no one ever talk about them? Just because they don't have a type in the C# type system is no reason to ignore them. The way in the past I've usually pushed back on this myth is to say that the real statement should be "in the Microsoft implementation of C# on the desktop CLR, value types are stored on the stack when the value is a local variable or temporary that is not a closed-over local variable of a lambda or anonymous method, and the method body is not an iterator block, and the jitter chooses to not enregister the value." The sheer number of weasel words in there is astounding, but they're all necessary: Versions of C# provided by other vendors may choose other allocation strategies for their temporary variables; there is no language requirement that a data structure called "the stack" be used to store locals of value type.
We have many versions of the CLI that run on embedded systems, in web browsers, and so on. Some may run on exotic hardware. I have no idea what the memory allocation strategies of those versions of the CLI are. The hardware might not even have the concept of "the stack" for all I know. Or there could be multiple stacks per thread. Or everything could go on the heap.
Lambdas and anonymous methods hoist local variables to become heap-allocated fields; those are not on the stack anymore.
Iterator blocks in today's implementation of C# on the desktop CLR also hoist locals to become heap-allocated fields. They do not have to! We could have chosen to implement iterator blocks as coroutines running on a fiber with a dedicated stack. In that case, the locals of value type could go on the stack of the fiber.
Read more: Fabulous Adventures In Coding
QR:
It is almost always irrelevant. We've worked hard to make a managed environment where the distinctions between different kinds of storage are hidden from the user. Unlike some languages, in which you must know whether a particular storage is on the stack or the heap for correctness reasons.
It is incomplete. What about references? References are neither value types nor instances of reference types, but they are values. They've got to be stored somewhere. Do they go on the stack or the heap? Why does no one ever talk about them? Just because they don't have a type in the C# type system is no reason to ignore them. The way in the past I've usually pushed back on this myth is to say that the real statement should be "in the Microsoft implementation of C# on the desktop CLR, value types are stored on the stack when the value is a local variable or temporary that is not a closed-over local variable of a lambda or anonymous method, and the method body is not an iterator block, and the jitter chooses to not enregister the value." The sheer number of weasel words in there is astounding, but they're all necessary: Versions of C# provided by other vendors may choose other allocation strategies for their temporary variables; there is no language requirement that a data structure called "the stack" be used to store locals of value type.
We have many versions of the CLI that run on embedded systems, in web browsers, and so on. Some may run on exotic hardware. I have no idea what the memory allocation strategies of those versions of the CLI are. The hardware might not even have the concept of "the stack" for all I know. Or there could be multiple stacks per thread. Or everything could go on the heap.
Lambdas and anonymous methods hoist local variables to become heap-allocated fields; those are not on the stack anymore.
Iterator blocks in today's implementation of C# on the desktop CLR also hoist locals to become heap-allocated fields. They do not have to! We could have chosen to implement iterator blocks as coroutines running on a fiber with a dedicated stack. In that case, the locals of value type could go on the stack of the fiber.
Read more: Fabulous Adventures In Coding
QR:
NHibernate Pitfalls: SQL Queries and Parameter Prefix
Posted by
jasper22
at
15:39
|
This is part of a series of posts about NHibernate Pitfalls. See the entire collection here.When you execute an SQL query with NHibernate with named parameters, you would perhaps expect them to be prefixed with a symbol specific to the current DB you are accessing, for example, @ for SQL Server and : for Oracle; that is not the case. NHibernate requires that you always use it’s DB-neutral parameter prefix, :, the same that you use for HQL queries: //for SQL queries
session.CreateSQLQuery("SELECT * FROM [Order] WHERE Id = :id").SetParameter("id", 1).List();
//for HQL queries
session.CreateQuery("from Order where id = :id").SetParameter("id", 1).List(); Read more: Development With A Dot
QR:
session.CreateSQLQuery("SELECT * FROM [Order] WHERE Id = :id").SetParameter("id", 1).List();
//for HQL queries
session.CreateQuery("from Order where id = :id").SetParameter("id", 1).List(); Read more: Development With A Dot
QR:
Apple планирует защищать свою продукцию от краж хранением пароля в зарядном устройстве
Posted by
jasper22
at
13:05
|

На днях Apple запатентовала метод, который призван повысить безопасность данных пользователей, если, к несчастью, их устройство было потеряно или украдено.В патенте под номером 2012/0005747 приводится следующее рассуждение: "… Если пароль для устройства или сложный или его трудно восстановить, то покупатель или вообще от него откажется или будет использовать слишком простой". Поэтому, в случае потери или кражи устройства, злоумышленник с большой долей вероятности получит неограниченный доступ к Macbook или iPhone без особых проблем. Далее, рассуждают в Apple, поскольку покупатели чаще всего лишаются самих устройств, а не их «зарядок», то предлагается поступить следующим образом: зарядное устройство снабжается неким модулем памяти, который хранит или зашифрованный пароль или кодовую фразу («Как звали Вашу первую учительницу»). Read more: Habrahabr.ru
QR:
Former Facebook Engineer Impressively Logs A Bunch Of Facebook Bugs
Posted by
jasper22
at
12:50
|
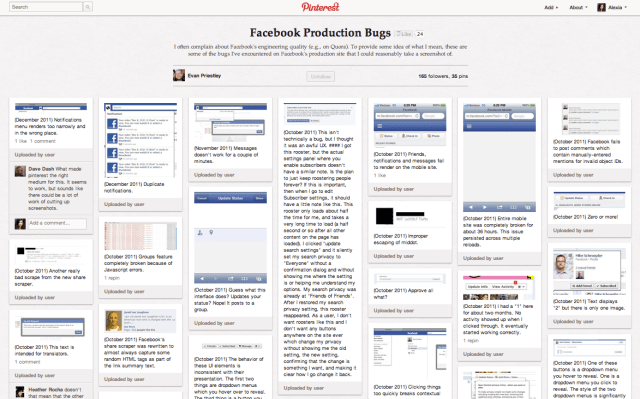
About two weeks ago, I couldn’t update my status on Facebook, like it just wouldn’t let me, showing me “Invalid Request” error messages even though my requests are totally valid DAMMIT.And then just like that the fail stopped and I could update, inexplicably. In my humble experience, I’ve come across so many Facebook bugs I’ve given up on getting frustrated and now just hope they’ll eventually go away. I regularly just straight up don’t receive Messages and can we just talk about how the Like button just doesn’t work. Can we? Former Facebook engineer (and current Phabricator creator) Evan Priestley has taken the opposite route; In the spirit of coding excellence, Priestly has created a Pinterest log of over 30 Facebook bugs he’s tracked since September 2011. It’s really impressive. Read more: Techcrunch
QR:
Hidden TortoiseSVN Commands
Posted by
jasper22
at
12:16
|

You may already be familiar with TortoiseSVN’s context menu, but did you know that if you hold down the shift key, you can access an extended context menu? This menu has some additional options.1) Merge reintegrate – merges all the changes from a branch back to the trunk.
2) Break lock – this command breaks someone else’s lock (useful in emergencies!)
3) Delete unversioned items – this opens a dialog that lists all the unversioned items in the working copy. From here, you can select which unversioned items to move to the recycle bin (of course, they can be recovered from the recycle bin, if you make a mistake!) Read more: Subversion Tip of the Week
QR:
Secret and Hidden Codes for Android
Posted by
jasper22
at
12:15
|

Nothing unethical here. All these codes are perfectly ok and legit. If you like tweaking and playing with your Android, this little piece of information is just for you. With these codes, you can have better control of your Android device. I tried these codes on my Samsung Galaxy tab and they worked there. I’m pretty sure they will work on any Android phone. if you like these codes, please share this article on Twitter, Google plus, or Facebook so that others can benefit from these codes as well. Disclaimer: Though I’ve tested these codes myself, I don’t take any responsibility if a code gives any problems. This article is for experienced Android users and not for noobs.*#*#4636#*#*It can give some really interesting data about the battery and phone. it will take you to a menu with 4 options: phone information, battery information, battery history, and usage statistics. *#*#7780#*#*This is the factory reset code. It will remove the settings of Google account from your phone (this is very helpful if you ever have to hand your phone over to someone for a few days). Plus it will reset the data and settings of system and downloaded apps. You can try this code safely because once you enter it, your phone will ask for confirmation. You can then opt out of it. Even if you do reset the settings, it will not erase the memory card files. *2767*3855#Think twice before you try this one because it will not ask for confirmation. Once the code has been entered, the only way to stop is by taking out the battery. Since I couldn’t take the battery out of the tablet, I didn’t try this one. So you are on your own here. This one formats the internal storage and resets all settings. Read more: GooGez
QR:
ManagedMSIExec - A managed wrapper for MSI'ing
Posted by
jasper22
at
12:12
|

Windows Installer is the installation and configuration service used by Windows to add and remove applications. (For more information, Wikipedia has a great overview of Windows Installer, covering products, components, setup phases, permissions, etc..) In addition to exposing a rich, native API, Windows Installer comes with msiexec.exe, a command-line tool that offers fine-grained control over the install/uninstall process. I wanted to familiarize myself with the use of the Windows Installer API from .NET, so I wrote a wrapper class to expose it to managed applications and then a simple program to exercise it. Unlike msiexec.exe which can do all kinds of things, my ManagedMsiExec supports only UI-less install and uninstall of a .MSI Windows Installer package (i.e., /quiet mode). By default, ManagedMsiExec provides simple status reporting on the command line and renders a text-based progress bar that shows how each phase is going. In its "verbose" mode, ManagedMsiExec outputs the complete set of status/progress/diagnostic messages generated by Windows Installer (i.e., /l*) so any problems can be investigated. Aside: Although I haven't tested ManagedMsiExec exhaustively, it's fundamentally just a thin wrapper around Windows Installer, so I'd expect it to work for pretty much any MSI out there.
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: "Make things as simple as possible, but not simpler.” [ManagedMsiExec sample app shows how to use the Windows Installer API from managed code]
QR:
Design and Build Native iOS Apps on Windows with MobiOne, No Mac or Objective-C Needed
Posted by
jasper22
at
12:10
|

MobiOne is designed for web developers, marketing departments, business consultants, and anyone who doesn’t know Objective-C or want to buy a Mac, but wants to create and build App Store-ready iOS applications and webapps. The communications power plant inside MobiOne is a cloud technology that Genuitec engineered called “AppCenter,” where app designers can test their native and webapps in a private Genuitec cloud for access anywhere. The AppCenter technology allows for easy testing of apps and webapps over the air (using iOS 4+) or through iTunes. Testing links can be shared via email or SMS for multiple device testing and previews. Not to add too much hyperbole in this blog post, but we know this is a “game changer” in iOS app development as we’ve effectively lowered the bar for anyone to create native and web iOS apps – we’ve given the power to you, the everyday users to get in the app development game. MobiOne is $99 annually and is fully supported by our staff. If you have any questions, check out our forums first or drop a note in there and we’ll get back to you soon. Go, here.Read more: Genuitec
QR:
Web server software NGINX is now bigger than Microsoft IIS
Posted by
jasper22
at
12:08
|
In the latest Netcraft Web Server, for January 2012, the lightweight open source web server software NGINX amassed more active sites than Microsoft Internet Information Server for the first time.That makes NGINX the second most used web server software in the world right now, only trumped by Apache. Let’s look at the numbers.
NGINX is bigger than IIS for active sitesLooking at the development of the top four web server software packages from January 2011 to January 2012, we get this chart:
Read more: pingdom
QR:
NGINX is bigger than IIS for active sitesLooking at the development of the top four web server software packages from January 2011 to January 2012, we get this chart:

Read more: pingdom
QR:
Linux kernel hits version 3.2, plenty of power-saving features in town
Posted by
jasper22
at
12:07
|

It's a little later than originally anticipated, but Linux kernel 3.2 is finally here. As per usual, it packs a number of improvements -- most them under the hood. Perhaps most exciting are some power-saving features related to graphics drivers, which should help get those battery life issues under control in Ubuntu 12.04. Other improvements include better (and hopefully more stable) WiFi drivers and faster read access to EXT4 formatted file systems. The list of changes is pretty epic to say the leastRead more: Engadget
QR:
Group Policy Resource Round-up
Posted by
jasper22
at
12:06
|
My last post on getting started with Active Directory was so popular that I thought I would do one for getting started with Group Policy. Once again this link list will satisfy everyone from beginner to advanced. I know there are many other third party resources and books, but I want to surface Microsoft white papers and articles that may not always be obvious. Enjoy! Group Policy – Beginners
Group Policy – Advanced
Group Policy – PowerShell
Group Policy – More Information
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: Everything you need to get started with Group Policy
QR:
Group Policy – Advanced
Group Policy – PowerShell
Group Policy – More Information
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: Everything you need to get started with Group Policy
QR:
x86 Assembly for C Programmers 1
Posted by
jasper22
at
12:04
|
IntroductionI’m writing a series of tutorials on x86 assembly for C programmers who are already familiar with many of the basics of programming and computing. The assembly tutorials available online just aren’t doing it for me, and I need something organized the way I think, on the topics I’m interested in, presented in a way which make comprehensive understanding easy. I’ll do the work, go find the answers, and then drop everything here for you to enjoy. Please note I do not claim to be an expert on the assembly language.My interest in assembly is for both optimizing C applications, and the purpose of developing exploits for vulnerabilities in common applications, not write applications in assembly from scratch. I’m not interested in, “Good,” examples of assembly, I’m interested in real examples. This will affect the assembly we look at. More specifically, I write the code in C, compile it with gcc, and what comes out is what we’ll be dissecting. For the purposes of these tutorials, 32-bit x86 assembly. Everything compiled/built/disassembled on the latest stable distro of Ubuntu.
ReferencesThe Art of Assembly is an excellent reference, and if you need clarification of any of the topics discussed, I recommend checking it out. Chapter six covers all of the instructions, how they work, and what specifically they do.
Thanks To:Bushmills from irc.freenode.net##asm for taking the time to explain to a noob why the first 7 lines of assembly were what they were.
The CodeLet’s take a look at a simple C application, and it’s disassembled assembly code.
gcc one.c -o one#include int main (int argc, char * argv [])
{ int i; argc++; for (i = 0; i < 10; i++)
printf("%d\n", i); return 0; }Disassembled counterpart (for main):
objdump -d one -M intel Read more: endeavor
QR:
ReferencesThe Art of Assembly is an excellent reference, and if you need clarification of any of the topics discussed, I recommend checking it out. Chapter six covers all of the instructions, how they work, and what specifically they do.
Thanks To:Bushmills from irc.freenode.net##asm for taking the time to explain to a noob why the first 7 lines of assembly were what they were.
The CodeLet’s take a look at a simple C application, and it’s disassembled assembly code.
gcc one.c -o one#include int main (int argc, char * argv [])
{ int i; argc++; for (i = 0; i < 10; i++)
printf("%d\n", i); return 0; }Disassembled counterpart (for main):
objdump -d one -M intel
080483c4 : 80483c4: 8d 4c 24 04 lea ecx,[esp+0x4] 80483c8: 83 e4 f0 and esp,0xfffffff0 80483cb: ff 71 fc push DWORD PTR [ecx-0x4] 80483ce: 55 push ebp 80483cf: 89 e5 mov ebp,esp 80483d1: 51 push ecx 80483d2: 83 ec 24 sub esp,0x24 80483d5: 83 01 01 add DWORD PTR [ecx],0x1 80483d8: c7 45 f8 00 00 00 00 mov DWORD PTR [ebp-0x8],0x0 80483df: eb 17 jmp 80483f8 80483e1: 8b 45 f8 mov eax,DWORD PTR [ebp-0x8] 80483e4: 89 44 24 04 mov DWORD PTR [esp+0x4],eax 80483e8: c7 04 24 d0 84 04 08 mov DWORD PTR [esp],0x80484d0 80483ef: e8 04 ff ff ff call 80482f8
QR:
New Tricks in Fiddler 2.3.8.2
Posted by
jasper22
at
12:03
|
The new Fiddler Beta has a few useful tricks. First, you can copy a DataURI to your clipboard (from Fiddler itself, or anywhere else):
and use the new Edit > Paste Files as Sessions command:
… to instruct Fiddler to parse the DataURI and create a new Session for it. You can then use Fiddler’s inspectors to examine the resulting object:
Read more: Fiddler Web Debugger
QR:

and use the new Edit > Paste Files as Sessions command:


QR:
Looking at Silverlight adoption statistics (for fun)
Posted by
jasper22
at
12:01
|
Jan 2012
These stats are purely for fun, digest these figures with a huge serving of salt! Smile. All these stats come from RIASTAT’s and I’ve pulled them from other people’s posts. There are other statistic collection sites that I also like to use, like StatOwl.The stats collected are from ALL INTERNET CONNECTED DEVICES, even if Silverlight doesn’t work on that device e.g. Android, iOS etc. It basically sums up ALL devices that connect to the internet and detects if Silverlight is installed. It just so happens that the majority of internet connected devices are Windows OS’s hence the large Silverlight/Flash adoption. As mobile devices increase I would expect the Silverlight and Flash stats to diminish, thou we aren’t seeing that yet. Which could mean that even thou mobile devices are increasing in adoption, so are PC’s and MAC’s. Read more: Silverlight and other cool things …
QR:
Fix Common IE Problems: Update your Docmode for Web Standards
Posted by
jasper22
at
11:59
|
Document compatibility defines how a browser renders your website. The more specific you are at telling the browser what to expect, the better the experience for your users. When using web standards like HTML5, start by explicitly declaring the HTML5 document type:
<!DOCTYPE html>This markup triggers standards mode in Internet Explorer 9 and 10. And it also works well in Chrome and Firefox. Four steps will get your site ready for many browsers and devices:Step 1: Validate that your site uses standards mode Check whether or not your site is currently in standards mode: Open the website in IE10 platform preview.
Note: You can also follow the same steps to update the docmode for IE9 only without downloading the preview.
Press F12 to launch the IE Developer Tools or find it on the Tools menu as shown below:
Read more: Rey Bango
QR:
<!DOCTYPE html>This markup triggers standards mode in Internet Explorer 9 and 10. And it also works well in Chrome and Firefox. Four steps will get your site ready for many browsers and devices:Step 1: Validate that your site uses standards mode Check whether or not your site is currently in standards mode: Open the website in IE10 platform preview.
Note: You can also follow the same steps to update the docmode for IE9 only without downloading the preview.
Press F12 to launch the IE Developer Tools or find it on the Tools menu as shown below:

QR:
Validations and Certifications FIPS and Common Criteria HSM Solutions
Posted by
jasper22
at
11:16
|
SafeNet Hardware Security Modules (HSMs) provide reliable protection against compromise for applications and information assets to ensure regulatory compliance, reduce the risk of legal liability, and improve profitability. SafeNet’s robust FIPS and Common Criteria validated HSM solutions are tamper resistant and offer the highest level of security. View all HSMs with Security Evaluations Federal Information Processing Standards (FIPS)FIPS ValidatedSafeNet HSMs are laboratory-tested under the Cryptographic Module Validation Program (CMVP) of the US National Institute for Standards and Technology NIST, in conjunction with the Canadian Communications Security Establishment (CSE). The standards relevant to cryptographic modules are the Federal Information Processing Standards (FIPS) SecurityRequirements for Cryptographic Modules and are publicly announced and developed by the Unites States federal government for use by all non-military government agencies and by government contractors. SafeNet modules validated as conforming to FIPS 140-1 and FIPS 140-2 are accepted by the Federal Agencies of Canada and USA for the protection of sensitive information and are accompanied by documentation bearing the FIPS logo of approval. Please refer to the table below for a list of all SafeNet HSMs that are validated to FIPS 140-1 and 140-2. To see SafeNet HSMs listed on the NIST website, follow http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm Common Criteria (CC)A broad portfolio of SafeNet products have been awarded Common Criteria certification for meeting the security requirements defined by the Common Criteria for Information Technology Security Evaluation. Read more: Safe-net
QR:
QR:
NIDS with psad and fwsnort
Posted by
jasper22
at
10:58
|
Introductionpsad and fwsnort are a pair of light weight tools which can be used as an effective NIDS. psad home page
fwsnort home pagepsad is a set of lightweight daemons that monitor network traffic (iptables logs) for port scans and/or suspicious activity. psad also has the potential to actively respond to potential threats and can be configured to automagically blacklist naughty ip addresses. fwsnort, as the name implies, converts snort rules to iptables. fwsnort first evaluates your current firewall and only adds rules for accepted traffic. By default, fwsnort logs suspicious traffic, and psad, as above, monitors the logs. Both tools, psad and fwsnort, assume you understand iptables or at least can configure iptables. If you need a quick review of iptables see my iptables page or other online reference.Note: Most of these commands are run as root. Install psadpsad is in the Debian, Fedora, and Ubuntu repositories and you may install pasd with apt-get / yum .The disadvantage of installing from the repositories is that Debian/Ubuntu install a number of dependencies (bastille) or, in the case of Fedora 13, the psad package has a few bugs. IMO it is almost as easy to simply install from "source". This is easy to do and is essentially running a perl script and answering a few questions.
Install the perl dependenciesAlthough the dependencies are the same, the package names vary between deb and rpm systems. gcc is required to compile psad and wget is used by both psad and fwsnort to update the respective rule sets.
Debian / UbuntuUsing any method, install the following packages:sudo apt-get -y install libcarp-clan-perl libdate-calc-perl \
libiptables-chainmgr-perl libiptables-parse-perl libnetwork-ipv4addr-perl \
libunix-syslog-perl libbit-vector-perl gcc wgetRead more: Bodhizazen.net
QR:
fwsnort home pagepsad is a set of lightweight daemons that monitor network traffic (iptables logs) for port scans and/or suspicious activity. psad also has the potential to actively respond to potential threats and can be configured to automagically blacklist naughty ip addresses. fwsnort, as the name implies, converts snort rules to iptables. fwsnort first evaluates your current firewall and only adds rules for accepted traffic. By default, fwsnort logs suspicious traffic, and psad, as above, monitors the logs. Both tools, psad and fwsnort, assume you understand iptables or at least can configure iptables. If you need a quick review of iptables see my iptables page or other online reference.Note: Most of these commands are run as root. Install psadpsad is in the Debian, Fedora, and Ubuntu repositories and you may install pasd with apt-get / yum .The disadvantage of installing from the repositories is that Debian/Ubuntu install a number of dependencies (bastille) or, in the case of Fedora 13, the psad package has a few bugs. IMO it is almost as easy to simply install from "source". This is easy to do and is essentially running a perl script and answering a few questions.
Install the perl dependenciesAlthough the dependencies are the same, the package names vary between deb and rpm systems. gcc is required to compile psad and wget is used by both psad and fwsnort to update the respective rule sets.
Debian / UbuntuUsing any method, install the following packages:sudo apt-get -y install libcarp-clan-perl libdate-calc-perl \
libiptables-chainmgr-perl libiptables-parse-perl libnetwork-ipv4addr-perl \
libunix-syslog-perl libbit-vector-perl gcc wgetRead more: Bodhizazen.net
QR:
.NET Framework and Other Protocols
Posted by
jasper22
at
10:57
|
This set of protocol documentation covers .NET Framework and other protocols that support communication among server applications, ASP.NET applications, and XML Web services. The technologies supported by these protocols include message queuing (MSMQ), OleTx two-phase commit transaction processing, DCOM, Windows Presentation Foundation (WPF), Windows Communication Foundation (WFC), Windows Workflow Foundation (WF), and Microsoft's Peer-to-Peer collaboration technologies that provide a peer-to-peer, serverless framework for collaborative planning, communication, content distribution, and multiplayer-game-matchmaking applications. This documentation also includes protocols that support SOAP message exchange. AudienceThe .NET Framework and Other Protocols technical documentation is intended for use in conjunction with publicly available standard specifications, network programming art, and Windows distributed systems concepts. It assumes that the reader either is familiar with this material or has immediate access to it. The technical documentation provides the following levels of audience support. For implementers: Conceptual and reference information for an implementation of one or more protocol specifications for a given task or scenario. For reviewers: A resource for readers who want to evaluate or understand one or more protocols.More InformationFor more information on these protocols, please visit Microsoft Open Specifications.
Read more: MSDN
QR:
Read more: MSDN
QR:
Description of the Credential Security Support Provider (CredSSP) in Windows XP Service Pack 3
Posted by
jasper22
at
10:56
|
CredSSP is a new Security Support Provider (SSP) that is available in Windows XP SP3 by using the Security Support Provider Interface (SSPI). CredSSP enables a program to use client-side SSP to delegate user credentials from the client computer to the target server. (The target server is accessed by using server-side SSP). Windows XP SP3 involves only the client-side SSP implementation. The client-side SSP implementation is currently being used by Remote Desktop Protocol (RDP) 6.1 Terminal Services (TS). However, the client-side SSP implementation can be used by any third-party program that is willing to use the client-side SSP to interact with programs that are running server-side SSP implementations in Windows Vista or in Windows Server 2008. To download the CredSSP protocol specification, visit the following Microsoft Web site:http://download.microsoft.com/download/9/5/E/95EF66AF-9026-4BB0-A41D-A4F81802D92C/%5BMS-CSSP%5D.pdf Note By default, CredSSP is turned off in Windows XP SP3.Read more: MS Support
QR:
QR:
Subscribe to:
Comments (Atom)


