
Streeme – Open Source & HTML5-Based Personal Music Server
Streeme is a free and open source application, that consists of both the server + frontend, allowing you to listen to your personal music collection anywhere. Its front-end is HTML5-based and works in most modern browsers including smartphones. 

Read more: WebResources Depot
Read more: Streeme [Google code]
HOWTO: Install Android-x86 2.2 in VirtualBox
Posted by
jasper22
at
17:48
|
Since Android-x86 2.2 was officially released a few days ago, I figured I’d provide a quick rundown of how to get it up and running in VirtualBox. All in all, it is pretty straightforward. Download, install, download, install. But if you’ve never installed a Linux based system before, some of the steps will look quite foreign. Plenty of screenshots will help with that! Step 1: Install VirtualBoxThis one’s easy. Head over to the Downloads section on the VirtualBox site and snag the appropriate installer for your OS. Since it will be a little different for each OS, I won’t provide screenshots for each step here. In general there’s just a lot of “Next” clicking involved. Of note, the networking component of the setup process will temporarily disrupt your connection. So if you’re downloading anything else, wait until it is finished before continuing with the setup. Once installation is completed, you’ll be greeted with a screen like this the first time you run VirtualBox:
INSTALL KDE SC 4.6 IN UBUNTU 10.10 (WITH REDESIGNED ACTIVITIES SYSTEM, FASTER KWIN)
Posted by
jasper22
at
16:24
|
KDE SC 4.6 was released today, brining polish to existing functionality as well as some cool new features and bug fixes.Probably the biggest change in KDE SC 4.6 is the redesign of the Activities system which makes it easy to associate applications to activities - once you create some new activities, right clicking an window title you'll have an option to make that application part of a certain activity as you can see in the screenshot below: 
Install KDE SC 4.6 In Ubuntu 10.10 Maverick MeerkatTo install KDE SC 4.6 in Ubuntu 10.10, open a terminal and copy/paste the following commands:
sudo add-apt-repository ppa:kubuntu-ppa/backports
sudo apt-get update
sudo apt-get install kubuntu-desktopOnce installed, log out and select KDE Plasma Workspace from the login window.Read more: WEB UPD8

Install KDE SC 4.6 In Ubuntu 10.10 Maverick MeerkatTo install KDE SC 4.6 in Ubuntu 10.10, open a terminal and copy/paste the following commands:
sudo add-apt-repository ppa:kubuntu-ppa/backports
sudo apt-get update
sudo apt-get install kubuntu-desktopOnce installed, log out and select KDE Plasma Workspace from the login window.Read more: WEB UPD8
The Command Line Desktop
Posted by
jasper22
at
16:23
|

We love the command line, but this desktop takes that love to entirely new levels with detailed, integrated statistics and information all arranged to make one densely packed but beautiful package.Read more: Lifehacker
The Linux boot process, a chart
Posted by
jasper22
at
16:10
|
The Linux boot process, a branching chart. For the most part, the levels do not depend on column. LILO does not require EFI, nor does GRUB require BIOS. EFI and BIOS support are now included in both bootloaders. Yes, there is some simplification here. EFI is very featured, but hasn't been commonly exercised to its full extent. Eventually EFI could possibly replace GRUB/LILO, but that day hasn't come yet.
Read more: SysAdmin1138 Expounds
Read more: SysAdmin1138 Expounds
Date/Time Support in NHibernate
Posted by
jasper22
at
16:00
|
In this post, we’ll examine the ways that NHibernate supports the DateTime-related data types, including some new features introduced in NHibernate 2 and 3. Here is a quick summary for the impatient.
Let’s take a look at a few DateTime-related problems that developers have run into in the past…Read more: James Kovacs' Weblog
| DbType | .NET | SQL Type |
| DateTime | System.DateTime | datetime |
| LocalDateTime | System.DateTime | datetime |
| UtcDateTime | System.DateTime | datetime |
| DateTimeOffset | System.DateTimeOffset | datetimeoffset |
| DateTime2 | System.DateTime | datetime2 |
| Date | System.DateTime | date |
| Time | System.DateTime | time |
| TimeAsTimeSpan | System.TimeSpan | time |
| TimeSpan | System.TimeSpan | bigint (int64) |
Let’s take a look at a few DateTime-related problems that developers have run into in the past…Read more: James Kovacs' Weblog
Plug Hub: The Discrete Powerstrip Organizer
Posted by
jasper22
at
15:25
|

Here's a concept design showcased over at Quirky.com which we think has some commendable ideas for wrangling and organizing power cables that often snake down from our desks. The Plug Hub is an under the desk powerstrip housing which not only conceals most everything away, but also offers three cord anchors to wrap around excess cabling. Read more: Unplggd.com
Italian Scientists Claim To Have Discovered Nickel-Hydrogen Cold Fusion, Create Copper As Byproduct
Posted by
jasper22
at
15:23
|
According to PhysOrg.com, two Italian scientists from the University of Bologna have taken on one of physics' historically most discredited concepts, cold fusion, and have actually succeeded in creating a sustainable reaction. Aside from the major implications of the energy market should this be validated and recreated (an issue that buried the original Cold Fusion discovery by Stanley Pons and Martin Fleishmann), one of the more economically important side effects of this purported rediscovery is that one of the byproducts of the reaction is none other than recently uber-bubbleicious copper. One wonders what the implications for the copper supply and demand curves (and equilibrium price) would be should the reaction documented by Andrea Rossi and Sergio Focardi be proven to not be a hoax. Is modern day alchemy the only thing that can dethrone copper from its historic price highs? From Physorg:Few areas of science are more controversial than cold fusion, the hypothetical near-room-temperature reaction in which two smaller nuclei join together to form a single larger nucleus while releasing large amounts of energy. In the 1980s, Stanley Pons and Martin Fleishmann claimed to have demonstrated cold fusion - which could potentially provide the world with a cheap, clean energy source - but their experiment could not be reproduced. Since then, all other claims of cold fusion have been illegitimate, and studies have shown that cold fusion is theoretically implausible, causing mainstream science to become highly speculative of the field in general. Despite the intense skepticism, a small community of scientists is still investigating near-room-temperature fusion reactions. The latest news occurred last week, when Italian scientists Andrea Rossi and Sergio Focardi of the University of Bologna announced that they developed a cold fusion device capable of producing 12,400 W of heat power with an input of just 400 W. Last Friday, the scientists held a private invitation press conference in Bologna, attended by about 50 people, where they demonstrated what they claim is a nickel-hydrogen fusion reactor. Further, the scientists say that the reactor is well beyond the research phase; they plan to start shipping commercial devices within the next three months and start mass production by the end of 2011. Read more: Zero Hedge
Abusing HTTP Status Codes to Expose Private Information
Posted by
jasper22
at
13:40
|
When you visit my website, I can automatically and silently determine if you're logged into Facebook, Twitter, GMail and Digg. There are almost certainly thousands of other sites with this issue too, but I picked a few vulnerable well known ones to get your attention. You may not care that I can tell you're logged into GMail, but would you care if I could tell you're logged into one or more porn or warez sites? Perhaps http://oppressive-regime.example.org/ would like to collect a list of their users who are logged into http://controversial-website.example.com/? Ignoring the privacy implications for a second, as a website developer, you might like to know if your visitors are logged into GMail; you could use that information to automatically fill the email fields in your forms with "@gmail.com"... Perhaps you might want to make your Facebook "like" buttons more prominent if you can tell your visitor is logged into Facebook at the moment? Here's how I achieve this: First of all. Lets check if you're logged into GMail right now (not including Google Apps)... (Yes, you are logged in). Now, how did I get that information? Really, really, easily... I generated a hidden image in my HTML similar to this: <img style="display:none;"
onload="logged_in_to_gmail()"
onerror="not_logged_in_to_gmail()"
src="https://mail.google.com/mail/photos/static/AD34hIhNx1pdsCxEpo6LavSR8dYSmSi0KTM1pGxAjRio47pofmE9RH7bxPwelO8tlvpX3sbYkNfXT7HDAZJM_uf5qU2cvDJzlAWxu7-jaBPbDXAjVL8YGpI"
/>I generated the URL in the "src" attribute by logging into my own GMail account, then going into the general settings and uploading a picture in the "My Picture" section. I then ticked the "Visible to everyone" checkbox, and right clicked the uploaded image to get the image location. Fetching the content at that URL does two different things depending on whether or not you're logged into GMail. If you are logged into GMail, it returns an image. If you're not logged into GMail, it redirects to a HTML page. This is why the img tag in my example above works. "onload" is triggered if an image is returned, but "onerror" is triggered otherwise. I tested this technique in Firefox, Safari, Chrome, Opera and various versions of Internet Explorer and it worked in them all. I reported it to Google and they described it as "expected behaviour" and ignored it. Read more: Mike Cardwell Online
onload="logged_in_to_gmail()"
onerror="not_logged_in_to_gmail()"
src="https://mail.google.com/mail/photos/static/AD34hIhNx1pdsCxEpo6LavSR8dYSmSi0KTM1pGxAjRio47pofmE9RH7bxPwelO8tlvpX3sbYkNfXT7HDAZJM_uf5qU2cvDJzlAWxu7-jaBPbDXAjVL8YGpI"
/>I generated the URL in the "src" attribute by logging into my own GMail account, then going into the general settings and uploading a picture in the "My Picture" section. I then ticked the "Visible to everyone" checkbox, and right clicked the uploaded image to get the image location. Fetching the content at that URL does two different things depending on whether or not you're logged into GMail. If you are logged into GMail, it returns an image. If you're not logged into GMail, it redirects to a HTML page. This is why the img tag in my example above works. "onload" is triggered if an image is returned, but "onerror" is triggered otherwise. I tested this technique in Firefox, Safari, Chrome, Opera and various versions of Internet Explorer and it worked in them all. I reported it to Google and they described it as "expected behaviour" and ignored it. Read more: Mike Cardwell Online
100 P2P Users Upload 75% of Content
Posted by
jasper22
at
13:34
|
Researchers say that about 100 people (called pirates in the article) are responsible for 75 percent of all downloading on BitTorrent (and the same group does 66 percent of all uploading), and says that the way to shut down the p2p network is simply to disincentive that relatively small number of people. The other large group identified in the study were people (such as from copyright enforcement agencies) who uploaded fake content to frustrate other users. No suggestions were made about how to prevent people from uploading fake content — but it was suggested that the first group could have their ad revenue cut or could be heavily fined Read more: Slashdot
Firefox Home Dash experiment offers a radical new UI for your Mozilla browser
Posted by
jasper22
at
13:32
|

It's a little hard to describe what Firefox Home Dash is -- beyond the basics, anyway. It's an experimental add-on born from Mozilla's Prospector project which replaces (or removes) nearly all of the Firefox UI. You're left with a title bar, scrollbar, the big orange button, and not much else. The goal is to get the browser out of the way and just give you the Web. Hover over the Firefox logo in the top-left of your window or press Ctrl+T, and Dash will appear. The Firefox Awesome Bar floats to the left, offering all the same functionality you find in the browser right now. It'll search your history, bookmarks, or submit your query to any search engine with the click of a favicon. The right half of your Dash is populated by your currently open tabs (in a strip along the top -- pinned tabs on the left) and frequently visited pages (shown below). Sites you visit most often will be placed in one of the four larger, central slides. As you can see from my screenshot, Dash doesn't always render thumbnails -- but this is the first release of an experimental add-on, so we were expecting a few bugs. Read more: DownloadSquad
How to Quickly Add Multiple IP Addresses to Windows Servers
Posted by
jasper22
at
11:42
|
If you have ever added multiple IP addresses to a single Windows server, going through the graphical interface is an incredible pain as each IP must be added manually, each in a new dialog box. Here’s a simple solution. 
Needless to say, this can be incredibly monotonous and time consuming if you are adding more than a few IP addresses. Thankfully, there is a much easier way which allows you to add an entire subnet (or more) in seconds. Adding an IP Address from the Command Line
Windows includes the “netsh” command which allows you to configure just about any aspect of your network connections. If you view the accepted parameters using “netsh /?” you will be presented with a list of commands each which have their own list of commands (and so on). For the purpose of adding IP addresses, we are interested in this string of parameters: netsh interface ipv4 add addressNote: For Windows Server 2003/XP and earlier, “ipv4″ should be replaced with just “ip” in the netsh command.If you view the help information, you can see the full list of accepted parameters but for the most part what you will be interested in is something like this: netsh interface ipv4 add address “Local Area Connection” 192.168.1.2 255.255.255.0The above command adds the IP Address 192.168.1.2 (with Subnet Mask 255.255.255.0) to the connection titled “Local Area Network”. Adding Multiple IP Addresses at Once
When we accompany a netsh command with the FOR /L loop, we can quickly add multiple IP addresses. The syntax for the FOR /L loop looks like this:FOR /L %variable IN (start,step,end) DO command So we could easily add every IP address from an entire subnet using this command:FOR /L %A IN (0,1,255) DO netsh interface ipv4 add address “Local Area Connection” 192.168.1.%A 255.255.255.0This command takes about 20 seconds to run, where adding the same number of IP addresses manually would take significantly longer. Read more: How-to-geek

Needless to say, this can be incredibly monotonous and time consuming if you are adding more than a few IP addresses. Thankfully, there is a much easier way which allows you to add an entire subnet (or more) in seconds. Adding an IP Address from the Command Line
Windows includes the “netsh” command which allows you to configure just about any aspect of your network connections. If you view the accepted parameters using “netsh /?” you will be presented with a list of commands each which have their own list of commands (and so on). For the purpose of adding IP addresses, we are interested in this string of parameters: netsh interface ipv4 add addressNote: For Windows Server 2003/XP and earlier, “ipv4″ should be replaced with just “ip” in the netsh command.If you view the help information, you can see the full list of accepted parameters but for the most part what you will be interested in is something like this: netsh interface ipv4 add address “Local Area Connection” 192.168.1.2 255.255.255.0The above command adds the IP Address 192.168.1.2 (with Subnet Mask 255.255.255.0) to the connection titled “Local Area Network”. Adding Multiple IP Addresses at Once
When we accompany a netsh command with the FOR /L loop, we can quickly add multiple IP addresses. The syntax for the FOR /L loop looks like this:FOR /L %variable IN (start,step,end) DO command So we could easily add every IP address from an entire subnet using this command:FOR /L %A IN (0,1,255) DO netsh interface ipv4 add address “Local Area Connection” 192.168.1.%A 255.255.255.0This command takes about 20 seconds to run, where adding the same number of IP addresses manually would take significantly longer. Read more: How-to-geek
Desktop notifications for emails and chat messages
Posted by
jasper22
at
11:27
|
Many of us are guilty of constantly switching back to Gmail to check for new messages. And if you’re like me, you’ve probably missed an important chat message because you weren’t looking at your Gmail window when it came in. If you use Google Chrome, these days can be over since we just launched HTML5 desktop notifications which display pop-ups whenever a chat message or new email arrives. 
To turn them on, click on the Settings link in the top right corner of Gmail and scroll down to the “Desktop Notifications” section. If you just want to get notified about chat messages, or if you use Priority Inbox and only want to get notifications for important messages, you can customize your settings from there too. Read more: GMail blog

To turn them on, click on the Settings link in the top right corner of Gmail and scroll down to the “Desktop Notifications” section. If you just want to get notified about chat messages, or if you use Priority Inbox and only want to get notifications for important messages, you can customize your settings from there too. Read more: GMail blog
Google Begins Soft Censorship Of Arbitrary Piracy-Related Queries
Posted by
jasper22
at
11:23
|

The efforts of media companies to quash online piracy are a bit like someone trying to put out a forest fire with a wet noodle. The latest pathetic flail comes in the form of coercing Google into censoring its results for some search terms. A number of words will no longer be autocompleted or trigger an instant search, among them the interesting and perfectly legal “bittorrent.” It’s a new high for antipiracy theater, because you can of course still search for the terms by hitting enter, and get the same results as before, including direct links to torrent files hosted on well-known indexers. The move will accomplish two things, though: first, it will damage consumer trust of a company whose services are ostensibly objective, and second, it confirms for the hundredth time how quixotic and misguided the efforts of the MPAA et al. are in every action they take. The actual censorship (I use the word lightly) is a joke. A leakier sieve than this was never wrought. While “Bittorrent” is blocked, “torrent” is not, and while some popular cyber lockers are on the blacklist (Rapidshare, Megaupload), others aren’t (Drop.io, Hotfile). As far as preventing piracy, the policy is worthless — incompetent. I have no doubt that this list was put together by the media companies, because Google would have done a far better job of doing it. The team responsible for executing this probably lost more time to derisive laughter than long lunches. Read more: Techcrunch
20 cool free downloadable PSD files
Posted by
jasper22
at
10:58
|
If you’re looking to renew your stock of PSD templates, take a good look at the following list of free PSD files.



'Inheriting' from an Internal WinForms Designer
Posted by
jasper22
at
10:56
|
IntroductionA designer is often the best choice to extend the behavior of an associated component in design mode. While there exist other means like TypeDescriptionProvider, ITypeDescriptorFilterService or overriding the Component.Site property; a designer remains the easiest and most concise way. As most components rely on the public framework ComponentDesigner or ControlDesigner, using a derived custom designer poses no problem. Trouble starts when the designer is marked internal for the System.Design assembly and is non trivial to reimplement by 'borrowing' code from Microsoft. Customizing a smart tag is one the features, which is nearly impossible without using a custom designer. An example of problematic hidden designers are ToolStrip / ToolStripItem components, with their lot of interdepending internal classes enhancing our IDE experience. I propose the simple idea of using the internal default designer, by encapsulating it in a suitable ComponentDesigner or ControlDesigner and delegating member calls to the internal designer. This article highlights some not too obvious issues involved to make it work.The demo project uses a ContextMenuStrip and a TreeView control without any added real functionality as proof of concept. Custom Designer SkeletonThe framework ContextMenuStrip is a Control, yet it's associated ToolStripDropDownDesigner derives from the ComponentDesigner. So our custom designer will too:internal abstract class ToolStripDropDownDesigner : ComponentDesigner
{
protected ComponentDesigner defaultDesigner; public override void Initialize(IComponent component)
{
// internal class ToolStripDropDownDesigner : ComponentDesigner
// Name: System.Windows.Forms.Design.ToolStripDropDownDesigner ,
// Assembly: System.Design, Version=4.0.0.0
Type tDesigner = Type.GetType
("System.Windows.Forms.Design.ToolStripDropDownDesigner, System.Design");
defaultDesigner = (ComponentDesigner)Activator.CreateInstance
(tDesigner, BindingFlags.Instance | BindingFlags.Public, null, null, null); defaultDesigner.Initialize(component);
base.Initialize(component);
} public override void InitializeNewComponent(IDictionary defaultValues)
{
base.InitializeNewComponent(defaultValues);
defaultDesigner.InitializeNewComponent(defaultValues);
} protected override void Dispose(bool disposing)
{
if (disposing)
{
if (defaultDesigner != null)
{
defaultDesigner.Dispose();
}
} base.Dispose(disposing);
}
}
Designer Properties A designer may expose design time only properties, adding new ones or ones that shadow existing control properties.These can be marked private, as design time environment uses Reflection to read and set values. Now our custom designer was specified as the principal designer by the DesignerAttribute and our designer instead of the default designer will be queried for properties. Does this mean we have to reimplement all designer properties on our custom designer and fidget with Reflection to delegate all calls?
Luckily inserting a single line will save us from the trouble:public override void Initialize(IComponent component)
{
...
// use Designer properties of nested designer ( do before base.Initialize ! )
TypeDescriptor.CreateAssociation(component, defaultDesigner); defaultDesigner.Initialize(component);
base.Initialize(component);
}
Quoted from MSDN:"The CreateAssociation method creates an association between a primary and a secondary object. Once an association is created, a designer or other filtering mechanism can add properties that route to either object into the primary object's property set. When a property invocation is made against the primary object, the GetAssociation method will be called to resolve the actual object instance that is related to its type parameter." For clarity: Any defined properties on our designer will be queried as well, we just created an additional target. BTW, CreateAssociation() was the missing piece, when I first failed at encapsulation some years ago. IDesignerFilter MethodsComponentDesigner inherits from IDesignerFilter interface and we must override its methods to delegate the calls to the default designer. As the methods are marked protected, we cast the designer to the interface, in order to access them:
protected IDesignerFilter designerFilter;
designerFilter = defaultDesigner;
ComponentDesigner's PreFilterAttributes() and PreFilterEvents() implementations are empty, and PostFilterProperties() only deals with the seldom case, that component inherits from IPersistComponentSettings. We won't bother overriding these methods.
Read more: Codeproject
{
protected ComponentDesigner defaultDesigner; public override void Initialize(IComponent component)
{
// internal class ToolStripDropDownDesigner : ComponentDesigner
// Name: System.Windows.Forms.Design.ToolStripDropDownDesigner ,
// Assembly: System.Design, Version=4.0.0.0
Type tDesigner = Type.GetType
("System.Windows.Forms.Design.ToolStripDropDownDesigner, System.Design");
defaultDesigner = (ComponentDesigner)Activator.CreateInstance
(tDesigner, BindingFlags.Instance | BindingFlags.Public, null, null, null); defaultDesigner.Initialize(component);
base.Initialize(component);
} public override void InitializeNewComponent(IDictionary defaultValues)
{
base.InitializeNewComponent(defaultValues);
defaultDesigner.InitializeNewComponent(defaultValues);
} protected override void Dispose(bool disposing)
{
if (disposing)
{
if (defaultDesigner != null)
{
defaultDesigner.Dispose();
}
} base.Dispose(disposing);
}
}
Designer Properties A designer may expose design time only properties, adding new ones or ones that shadow existing control properties.These can be marked private, as design time environment uses Reflection to read and set values. Now our custom designer was specified as the principal designer by the DesignerAttribute and our designer instead of the default designer will be queried for properties. Does this mean we have to reimplement all designer properties on our custom designer and fidget with Reflection to delegate all calls?
Luckily inserting a single line will save us from the trouble:public override void Initialize(IComponent component)
{
...
// use Designer properties of nested designer ( do before base.Initialize ! )
TypeDescriptor.CreateAssociation(component, defaultDesigner); defaultDesigner.Initialize(component);
base.Initialize(component);
}
Quoted from MSDN:"The CreateAssociation method creates an association between a primary and a secondary object. Once an association is created, a designer or other filtering mechanism can add properties that route to either object into the primary object's property set. When a property invocation is made against the primary object, the GetAssociation method will be called to resolve the actual object instance that is related to its type parameter." For clarity: Any defined properties on our designer will be queried as well, we just created an additional target. BTW, CreateAssociation() was the missing piece, when I first failed at encapsulation some years ago. IDesignerFilter MethodsComponentDesigner inherits from IDesignerFilter interface and we must override its methods to delegate the calls to the default designer. As the methods are marked protected, we cast the designer to the interface, in order to access them:
protected IDesignerFilter designerFilter;
designerFilter = defaultDesigner;
ComponentDesigner's PreFilterAttributes() and PreFilterEvents() implementations are empty, and PostFilterProperties() only deals with the seldom case, that component inherits from IPersistComponentSettings. We won't bother overriding these methods.
Read more: Codeproject
Microsoft Books Online for SQL Server Code-Named "Denali" CTP1
Posted by
jasper22
at
10:55
|
Microsoft SQL Server Code-Named “Denali” CTP1 is the next release of Microsoft SQL Server. Books Online is the primary documentation for SQL Server.Read more: MS Download
PE .NET Simple Assemblage Protection
Posted by
jasper22
at
10:55
|

Language: VB, C#, Visual F# , & C++ /CLR ONLY/Features include: [*] - Total irreversible obfuscation [old]
[*] - code protection /through code primitive concealment method`s body/
[*] - method body decomposition (™)
[*] - Control flow obfuscation /Easy/
[*] - support dll
[*] - Native Image Generator with code cleaner in primary assembly and received image...
[*] - Framework version auto-detect /1, 2, 3, 4/
[*] - Cross-Platform /64-Bit Support/
[*] - Include: Packer NetZ Additions:[*] - Best support of the large assembly
[*] - command line interface [optional]
[*] - Added: MATCODE Compressor
Read more: Emicrox.net
Help wanted: Google hiring in 2011
Posted by
jasper22
at
10:52
|
2010 was a huge year for Google. Many of our big bets—on mobile, display advertising, the cloud and more—really started to pay off. Amazingly, Android now runs on over 100 devices with more than 300,000 activations each day. Chrome has at least 120 million active users and it’s growing quickly. Last year more than 1 million businesses switched to Google Apps and embraced its 100% web approach. And we’ve made search faster than ever, even when you’re on the go. But it wasn’t just a growth year for our products—the company grew as well. In 2010 we added more than 4,500 Googlers, primarily in engineering and sales: second only to 2007 when we added over 6,000 people to Google. I love Google because of our people. It's inspiring to be part of the team. And that's why I am excited about 2011—because it will be our biggest hiring year in company history. We’re looking for top talent—across the board and around the globe—and we’ll hire as many smart, creative people as we can to tackle some of the toughest challenges in computer science: like building a web-based operating system from scratch, instantly searching an index of more than 100 million gigabytes and even developing cars that drive themselves. There’s something at Google for everyone—from geo, to enterprise, to video—with most of the work done in small teams, effectively working as start-ups. (The average number of software engineers on a project at Google is 3.5.) That’s why the vast majority of our people stay with us, building their careers and taking on new challenges within the company. Read more: The Official Google Blog
How to make ViewState secure in ASP.NET ?
Posted by
jasper22
at
10:51
|
The ASP.NET ViewState is a client side state management. ViewState is stored in hidden field with ID named __VIEWSTATE. Typically, stored ViewState information looks as below: 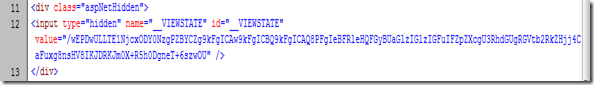
Now let us look at the value. It looks likes an encrypted string. This is nothing but Base64 Encoded string and it is not an encrypted string. So it can be easily decoded.The main reasons for making it Base64 encoding are as follows: 1. Base64 makes a string suitable for HTTP transfer
2. It makes it a little harder to read .But people often get confused that this is an encrypted string. Let us try to decode the string using ViewState Decoder (A nice tool created by Fritz Onion).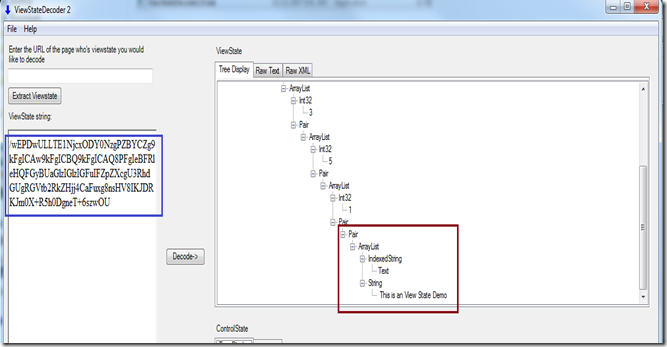
Read more: Abhijit's World of .NET

Now let us look at the value. It looks likes an encrypted string. This is nothing but Base64 Encoded string and it is not an encrypted string. So it can be easily decoded.The main reasons for making it Base64 encoding are as follows: 1. Base64 makes a string suitable for HTTP transfer
2. It makes it a little harder to read .But people often get confused that this is an encrypted string. Let us try to decode the string using ViewState Decoder (A nice tool created by Fritz Onion).

Read more: Abhijit's World of .NET
How to make all non-virtual members virtual
Posted by
jasper22
at
10:50
|
Using a simple find & replace with a regex in VS2010:
GENDARME ♥ CECIL/LIGHT
Posted by
jasper22
at
10:49
|
It's been a while since I published some benchmark numbers on Gendarme. Now with 2.10 there was a huge change by using the shiny new Cecil (aka cecil/light) library from the ever amazing JB Evain. So clearly a revision was in order... Here's a table with some common Mono applications I frequently use:Read more: Poupou's Corner of the Web
WCF Binary XML and dictionaries
Posted by
jasper22
at
10:48
|
One of the encodings which come with WCF (since its first version, in .NET Framework 3.0) is a fast and lightweight encoding for XML documents. The WCF Binary XML format (“officially” called .NET Binary Format: XML Data Structure – http://msdn.microsoft.com/en-us/library/cc219210(v=PROT.10).aspx). It is essentially a new way of representing XML, without using the “normal” angle-bracket notation (<element attr="value">the content</element>), resulting in a smaller document (for example, all “end element” nodes are represented by a single byte in the binary format (or even none, as some text nodes have the information that they are followed by an end element). That already results in a significant compression of the data. However, where the binary format can really shine is when we use its dictionaries. Essentially, a dictionary string is a string which can be identified by a small integer. So instead of having to output the whole name (for example, the name ‘Person’ would be encoded in 7 bytes – 1 for the string length and 6 for each of the letters), if this string belonged to one of the dictionaries agreed upon by the two parties (one which is encoding the XML in the binary format, the other which will read the encoded binary into XML), it would normally use 1 (or 2) bytes to be represented. An example can show it easier. The following “.NET Binary XML” document represents the XML <Envelope></Envelope>:40 08 45 6E 76 65 6C 6F 70 65 01The first byte (0x40) indicates that this is a “ShortElement” record, followed by the length of the element name (0x08), followed by the UTF-8 encoding of the local name (0x45 … 0x65). Finally, the last byte (0x01) represents an end element. If the string Envelope is part of a dictionary, however, the same document can be rewritten replacing the 9 bytes used for the element with its dictionary id. Assuming that the dictionary id of “Envelope” is 0x02, this is what the same document would be encoded: 42 02 01The first byte was changed to indicate that this is a new type of record: a “ShortDictionaryElement”. It’s followed by the dictionary id of the string it represents.Two dictionaries
Replacing the strings with its dictionary ids is without question a great size reduction strategy for the binary encoding. Read more: Carlos' blog
Replacing the strings with its dictionary ids is without question a great size reduction strategy for the binary encoding. Read more: Carlos' blog
XAP File Optimization Techniques for 2011
Posted by
jasper22
at
10:48
|
So you've created something cool in Silverlight but your XAP file is bigger than you would've hoped. What can you do about it?Well there are tips to be found on the internet. Some say that recompressing the XAP file with something like WinRAR on its "best" compression setting will help. But that was in the Visual Studio 2008 / Silverlight 2 days. Now if you're building a Silverlight 4 app in Visual Studio 2010 it's already going to be compressed about as heavily as is possible. So I'm going to talk about other effective techniques that will help you today.Tips1.) Reduce XAP size by using application library caching (not available for out-of-browser applications). Check this option in Visual Studio 2010 and when your project is built there will be extra files automatically generated. So you'll have to upload your XAP file and any auto-generated ZIP files to the same directory. The generated ZIP files contain any external assemblies that your XAP require. Behind the scenes this relationship is automatically maintained with the AppManifest. This feature is pretty cool and very easy to use. You should note, however, that the whole idea behind it is caching. And so it speeds up requests from repeat visitors, but in practice it doesn't do a thing to speed up the experience for a new visitor. Read more about this feature from Microsoft.
2.) Make sure that you're including references to assemblies that you actually need and nothing more. Sometimes you'll need a reference to an assembly but you don't want it set to "Copy Local", as that adds to the XAP. Visual Studio 2010 is usually good about automatically setting "Copy Local" when appropriate. For example, System.Windows.Controls is not part of the runtime (it's a part of the SDK). Visual Studio knows this and when you add System.Windows.Controls to the project it automatically sets "Copy Local" to true. But when in doubt about an assembly reference, try setting "Copy Local" to false and see what happens. If your application builds and runs fine, then you're good. 3.) If you have a need for just one of these controls below, then download and use it rather than including the entire System.Windows.Controls assembly:
I ripped those controls out of the Silverlight SDK a couple weeks ago, and created individual projects out of them. If you only needed the Grid Splitter, for example, then you could save around 60 KB by adding it to your project instead of the entire System.Windows.Controls.dll. 4.) Set up content expiration in IIS. So far we've just been concentrating on the XAP file itself. It's easy to forget about server configuration. Read more: SilverlightXAP Blog
2.) Make sure that you're including references to assemblies that you actually need and nothing more. Sometimes you'll need a reference to an assembly but you don't want it set to "Copy Local", as that adds to the XAP. Visual Studio 2010 is usually good about automatically setting "Copy Local" when appropriate. For example, System.Windows.Controls is not part of the runtime (it's a part of the SDK). Visual Studio knows this and when you add System.Windows.Controls to the project it automatically sets "Copy Local" to true. But when in doubt about an assembly reference, try setting "Copy Local" to false and see what happens. If your application builds and runs fine, then you're good. 3.) If you have a need for just one of these controls below, then download and use it rather than including the entire System.Windows.Controls assembly:
Calendar
Date Picker
Grid Splitter
Tab Control
I ripped those controls out of the Silverlight SDK a couple weeks ago, and created individual projects out of them. If you only needed the Grid Splitter, for example, then you could save around 60 KB by adding it to your project instead of the entire System.Windows.Controls.dll. 4.) Set up content expiration in IIS. So far we've just been concentrating on the XAP file itself. It's easy to forget about server configuration. Read more: SilverlightXAP Blog
TPL (Task Parallel Library) Dataflow CTP Released
Posted by
jasper22
at
10:47
|
TPL Dataflow Community Technology Preview
This is a Community Technology Preview (CTP) of a new .NET library for building asynchronous and parallel applications. This library, referred to as TPL Dataflow, is available for .NET 4 in the form of the System.Threading.Tasks.Dataflow.dll.
Introduction to TPL Dataflow
TPL Dataflow (TDF) is a new .NET library for building concurrent applications. It promotes actor/agent-oriented designs through primitives for in-process message passing, dataflow, and pipelining. TDF builds upon the APIs and scheduling infrastructure provided by the Task Parallel Library (TPL) in .NET 4, and integrates with the language support for asynchrony provided by C#, Visual Basic, and F#. Read more: Greg's Cool [Insert Clever Name] of the Day
This is a Community Technology Preview (CTP) of a new .NET library for building asynchronous and parallel applications. This library, referred to as TPL Dataflow, is available for .NET 4 in the form of the System.Threading.Tasks.Dataflow.dll.
Introduction to TPL Dataflow
TPL Dataflow (TDF) is a new .NET library for building concurrent applications. It promotes actor/agent-oriented designs through primitives for in-process message passing, dataflow, and pipelining. TDF builds upon the APIs and scheduling infrastructure provided by the Task Parallel Library (TPL) in .NET 4, and integrates with the language support for asynchrony provided by C#, Visual Basic, and F#. Read more: Greg's Cool [Insert Clever Name] of the Day
Protecting Your Information On the Go
Posted by
jasper22
at
10:45
|
Overview
Brochure with guidance on protecting private information on mobile phones and devices, public computers, and public Wi-Fi.Read more: MS Download
Brochure with guidance on protecting private information on mobile phones and devices, public computers, and public Wi-Fi.Read more: MS Download
Migrate SVN To TFS 2010
Posted by
jasper22
at
10:45
|
For all the SVN users that likes to migrate to TFS 2010 with all the history of SVN here is the right tool for you:http://svn2tfs.codeplex.com/This tool will help to Migrates a SubVersion 6.x (SVN) repository to Team Foundation Server (TFS) 2010 replaying every action occurred in SubVersion.
Curious about IObservable? Here’s a quick example to get you started!
Posted by
jasper22
at
10:44
|
Have you heard about IObservable/IObserver support in Microsoft StreamInsight 1.1? Then you probably want to try it out. If this is your first incursion into the IObservable/IObserver pattern, this blog post is for you! StreamInsight 1.1 introduced the ability to use IEnumerable and IObservable objects as event sources and sinks. The IEnumerable case is pretty straightforward, since many data collections are already surfacing as this type. This was already covered by Colin in his blog. Creating your own IObservable event source is a little more involved but no less exciting – here is a primer: First, let’s look at a very simple Observable data source. All it does is publish an integer in regular time periods to its registered observers. (For more information on IObservable, see http://msdn.microsoft.com/en-us/library/dd990377.aspx ). sealed class RandomSubject : IObservable<int>, IDisposable
{
private bool _done;
private readonly List<IObserver<int>> _observers;
private readonly Random _random;
private readonly object _sync;
private readonly Timer _timer;
private readonly int _timerPeriod; /// <summary>
/// Random observable subject. It produces an integer in regular time periods.
/// </summary>
/// <param name="timerPeriod">Timer period (in milliseconds)</param>
public RandomSubject(int timerPeriod)
{
_done = false;
_observers = new List<IObserver<int>>();
_random = new Random();
_sync = new object();
_timer = new Timer(EmitRandomValue);
_timerPeriod = timerPeriod;
Schedule();
} public IDisposable Subscribe(IObserver<int> observer)
{
lock (_sync)
{
_observers.Add(observer);
}
return new Subscription(this, observer);
} public void OnNext(int value)
{
lock (_sync)
Read more: Microsoft StreamInsight
{
private bool _done;
private readonly List<IObserver<int>> _observers;
private readonly Random _random;
private readonly object _sync;
private readonly Timer _timer;
private readonly int _timerPeriod; /// <summary>
/// Random observable subject. It produces an integer in regular time periods.
/// </summary>
/// <param name="timerPeriod">Timer period (in milliseconds)</param>
public RandomSubject(int timerPeriod)
{
_done = false;
_observers = new List<IObserver<int>>();
_random = new Random();
_sync = new object();
_timer = new Timer(EmitRandomValue);
_timerPeriod = timerPeriod;
Schedule();
} public IDisposable Subscribe(IObserver<int> observer)
{
lock (_sync)
{
_observers.Add(observer);
}
return new Subscription(this, observer);
} public void OnNext(int value)
{
lock (_sync)
Read more: Microsoft StreamInsight
How debuggers work: Part 1 – Basics
Posted by
jasper22
at
10:43
|
This is the first part in a series of articles on how debuggers work. I’m still not sure how many articles the series will contain and what topics it will cover, but I’m going to start with the basics. In this part
I’m going to present the main building block of a debugger’s implementation on Linux – the ptrace system call. All the code in this article is developed on a 32-bit Ubuntu machine. Note that the code is very much platform specific, although porting it to other platforms shouldn’t be too difficult. Motivation
To understand where we’re going, try to imagine what it takes for a debugger to do its work. A debugger can start some process and debug it, or attach itself to an existing process. It can single-step through the code, set breakpoints and run to them, examine variable values and stack traces. Many debuggers have advanced features such as executing expressions and calling functions in the debbugged process’s address space, and even changing the process’s code on-the-fly and watching the effects. Although modern debuggers are complex beasts [1], it’s surprising how simple is the foundation on which they are built. Debuggers start with only a few basic services provided by the operating system and the compiler/linker, all the rest is just a simple matter of programming. Linux debugging – ptrace
The Swiss army knife of Linux debuggers is the ptrace system call [2]. It’s a versatile and rather complex tool that allows one process to control the execution of another and to peek and poke at its innards [3]. ptrace can take a mid-sized book to explain fully, which is why I’m just going to focus on some of its practical uses in examples. Let’s dive right in.Stepping through the code of a process
I’m now going to develop an example of running a process in "traced" mode in which we’re going to single-step through its code – the machine code (assembly instructions) that’s executed by the CPU. I’ll show the example code in parts, explaining each, and in the end of the article you will find a link to download a complete C file that you can compile, execute and play with. Read more: Eli Bendersky's website
I’m going to present the main building block of a debugger’s implementation on Linux – the ptrace system call. All the code in this article is developed on a 32-bit Ubuntu machine. Note that the code is very much platform specific, although porting it to other platforms shouldn’t be too difficult. Motivation
To understand where we’re going, try to imagine what it takes for a debugger to do its work. A debugger can start some process and debug it, or attach itself to an existing process. It can single-step through the code, set breakpoints and run to them, examine variable values and stack traces. Many debuggers have advanced features such as executing expressions and calling functions in the debbugged process’s address space, and even changing the process’s code on-the-fly and watching the effects. Although modern debuggers are complex beasts [1], it’s surprising how simple is the foundation on which they are built. Debuggers start with only a few basic services provided by the operating system and the compiler/linker, all the rest is just a simple matter of programming. Linux debugging – ptrace
The Swiss army knife of Linux debuggers is the ptrace system call [2]. It’s a versatile and rather complex tool that allows one process to control the execution of another and to peek and poke at its innards [3]. ptrace can take a mid-sized book to explain fully, which is why I’m just going to focus on some of its practical uses in examples. Let’s dive right in.Stepping through the code of a process
I’m now going to develop an example of running a process in "traced" mode in which we’re going to single-step through its code – the machine code (assembly instructions) that’s executed by the CPU. I’ll show the example code in parts, explaining each, and in the end of the article you will find a link to download a complete C file that you can compile, execute and play with. Read more: Eli Bendersky's website
Future Photography Contained in a Really Small Lens
Posted by
jasper22
at
09:58
|
The Funamizu is back with another concept. Inspired by the WVIL concept camera shown at this year’s CES, Mac Funamizu envisaged a similar device in a slimmer package. The idea revolves around a lens system that is totally self contained with everything needed to take SLR quality photos. It wirelessly transmits the images to a hub device – in this case, a transparent screen. Designer: Mac Funamizu

Read more: Yanko design


Read more: Yanko design
Invent Your Own Computer Games with Python
Chapter HTML Related Content
Chapter 1 - Installing Python
Chapter 2 - The Interactive Shell
Chapter 3 - Strings
Chapter 4 - Guess the Number
Chapter 5 - Jokes
Chapter 6 - Dragon Realm
Chapter 7 - Using the Debugger (new!)
Chapter 8 - Flow Charts
Chapter 9 - Hangman
Chapter 10 - Tic Tac Toe
Chapter 11 - Bagels
Chapter 12 - Cartesian Coordinates
Chapter 13 - Sonar
Chapter 14 - Caesar Cipher
Chapter 15 - Reversi
Chapter 16 - AI Simulation
Chapter 17 - Graphics and Animation
Chapter 18 - Collision Detection and Input
Chapter 19 - Sound and Images
Chapter 20 - Dodger
Appendix A - Differences between Python 2 and 3
Appendix B - Statements, Functions, and Methods Reference
Appendix C - Running Python Programs Without Python Installed
Appendix D - Common Error Messages in PythonRead more: Invent Your Own Computer Games with Python
Chapter 1 - Installing Python
Chapter 2 - The Interactive Shell
Chapter 3 - Strings
Chapter 4 - Guess the Number
Chapter 5 - Jokes
Chapter 6 - Dragon Realm
Chapter 7 - Using the Debugger (new!)
Chapter 8 - Flow Charts
Chapter 9 - Hangman
Chapter 10 - Tic Tac Toe
Chapter 11 - Bagels
Chapter 12 - Cartesian Coordinates
Chapter 13 - Sonar
Chapter 14 - Caesar Cipher
Chapter 15 - Reversi
Chapter 16 - AI Simulation
Chapter 17 - Graphics and Animation
Chapter 18 - Collision Detection and Input
Chapter 19 - Sound and Images
Chapter 20 - Dodger
Appendix A - Differences between Python 2 and 3
Appendix B - Statements, Functions, and Methods Reference
Appendix C - Running Python Programs Without Python Installed
Appendix D - Common Error Messages in PythonRead more: Invent Your Own Computer Games with Python
Top 6 List of Programming Top 10 Lists
Posted by
jasper22
at
16:04
|
Dare Obasanjo: Top 10 Signs Your Software Project is Doomed
Andres Taylor: Top 10 Things Ten Years of Professional Software Development Has Taught Me
Read more: Coding Horror
- Trying to do too much in the first version.
- Taking a major dependency on unproven technology.
- Competing with an existing internal project that is either a cash cow or has powerful backers.
- The team is understaffed.
- "Complex problems require complex solutions".
- Schedule Chicken
- Scope Creep
- Second System Syndrome
- No Entrance Strategy.
- Tackling a problem you don't know how to solve.
Andres Taylor: Top 10 Things Ten Years of Professional Software Development Has Taught Me
- Object orientation is much harder than you think.
- The difficult part of software development is communication.
- Learn to say no.
- If everything is equally important, then nothing is important.
- Don't over-think a problem.
- Dive really deep into something, but don't get hung up.
- Learn about the other parts of the software development machine.
- Your colleagues are your best teachers.
- It all comes down to working software.
- Some people are assholes.
Read more: Coding Horror
Learn Python in 10 minutes
Posted by
jasper22
at
15:59
|
Preliminary fluffSo, you want to learn the Python programming language but can’t find a concise and yet full-featured tutorial. This tutorial will attempt to teach you Python in 10 minutes. It’s probably not so much a tutorial as it is a cross between a tutorial and a cheatsheet, so it will just show you some basic concepts to start you off. Obviously, if you want to really learn a language you need to program in it for a while. I will assume that you are already familiar with programming and will, therefore, skip most of the non-language-specific stuff. The important keywords will be highlighted so you can easily spot them. Also, pay attention because, due to the terseness of this tutorial, some things will be introduced directly in code and only briefly commented on. PropertiesPython is strongly typed (i.e. types are enforced), dynamically, implicitly typed (i.e. you don’t have to declare variables), case sensitive (i.e. var and VAR are two different variables) and object-oriented (i.e. everything is an object). Getting helpHelp in Python is always available right in the interpreter. If you want to know how an object works, all you have to do is call help(<object>)! Also useful are dir(), which shows you all the object’s methods, and <object>.doc, which shows you its documentation string: >>> help(5)
Help on int object:
(etc etc)>>> dir(5)
['__abs__', '__add__', ...]>>> abs.__doc__
'abs(number) -> number\n\nReturn the absolute value of the argument.'
SyntaxPython has no mandatory statement termination characters and blocks are specified by indentation. Indent to begin a block, dedent to end one. Statements that expect an indentation level end in a colon (:). Comments start with the pound (#) sign and are single-line, multi-line strings are used for multi-line comments. Values are assigned (in fact, objects are bound to names) with the equals sign (”=”), and equality testing is done using two equals signs (”==“). You can increment/decrement values using the += and -= operators respectively by the right-hand amount. This works on many datatypes, strings included. You can also use multiple variables on one line. For example: >>> myvar = 3
>>> myvar += 2
>>> myvar
5
>>> myvar -= 1
>>> myvar
4
"""This is a multiline comment.Read more: Stavros' Stuff
Help on int object:
(etc etc)>>> dir(5)
['__abs__', '__add__', ...]>>> abs.__doc__
'abs(number) -> number\n\nReturn the absolute value of the argument.'
SyntaxPython has no mandatory statement termination characters and blocks are specified by indentation. Indent to begin a block, dedent to end one. Statements that expect an indentation level end in a colon (:). Comments start with the pound (#) sign and are single-line, multi-line strings are used for multi-line comments. Values are assigned (in fact, objects are bound to names) with the equals sign (”=”), and equality testing is done using two equals signs (”==“). You can increment/decrement values using the += and -= operators respectively by the right-hand amount. This works on many datatypes, strings included. You can also use multiple variables on one line. For example: >>> myvar = 3
>>> myvar += 2
>>> myvar
5
>>> myvar -= 1
>>> myvar
4
"""This is a multiline comment.Read more: Stavros' Stuff
How Duff’s Device Works
Posted by
jasper22
at
15:57
|
I like C, but I have to admit that, sometimes, “The Old Man of Programming” can be a bit of a killjoy. This is one of the most exciting eras in computer history, but lately, C’s acting like he doesn’t even want to have a good time. While the cool kids like Ruby and Haskell are living it up, C’s over in the corner obsessing over bits and bytes and memory alignment and pointers and the stack and machine architecture and unreachable allocations and multiple indirections…and it’s…kind of a buzzkill. You want to tell him, “Dude! Lighten up! This is supposed to be fun!” But of course C can’t relax. He’s holding the entire computing universe on his shoulders, after all. It’s not turtles all the way down — it’s turtles all the way down, then C. Not a lot of room for fun underneath that, is there? Is there?Well. Here’s the secret: C does let loose sometimes. And after being bottled up for so long, when the release finally does come, it’s pretty much an F5 of crazy.Take for example a little thing called Duff’s Device: send(short *to, short *from, int count)
{
Okay, what you have here is your basic switch statement merged with a do loop. Pretty messed up, right? And just to be clear: this is totally valid C.Huh?If we look at the Jargon File entry, we see that the purpose of Duff’s Device is to continuously copy data into a memory-mapped video register.
Read more: Tenacious C
{
int n=(count+7)/8;
switch(count%8){
case 0: do{ *to = *from++;
case 7: *to = *from++;
case 6: *to = *from++;
case 5: *to = *from++;
case 4: *to = *from++;
case 3: *to = *from++;
case 2: *to = *from++;
case 1: *to = *from++;
}while( --n>0);
}}
Okay, what you have here is your basic switch statement merged with a do loop. Pretty messed up, right? And just to be clear: this is totally valid C.Huh?If we look at the Jargon File entry, we see that the purpose of Duff’s Device is to continuously copy data into a memory-mapped video register.
Read more: Tenacious C
Fedora Infrastructure Compromised
Posted by
jasper22
at
15:19
|
The infrastructure of the Fedora Project was compromised over the weekend and an account belonging to a Fedora contributor was taken over by an attacker. However, Fedora officials said they don't believe that the attacker was able to push any changes to the Fedora package system or make any actual changes to the infrastructure. The attack appears to have targeted one specific user account, which had some high-value privileges. The attacker was able to compromise the account externally, and then had the ability to connect remotely to some Fedora systems. The attacker also changed the account's SSH key, Fedora officials said. Read more: Slashdot
Read more: Fedora
Read more: Fedora
Git tooling for .NET developers
Posted by
jasper22
at
14:50
|
I’m not getting into holy wars, and I’m not trying to convince anyone that Git is better than any other VCS. Instead I’ll walk you through the tooling I use to interact with Git on Windows, with Visual Studio. Git Extensions
First thing you should be getting is Git Extensions.
With that, similar to TortoiseX family of tools you get nice context menu that gives you access to most common operations quickly, via GUI, and with no need to memorize command line options if you want to avoid it. You can also launch Git command line in the selected folder and then all power of git is at your disposal. Visual Studio
If you’re a .NET developer, you’ll want to work from within Visual Studio. I’m sure you’ll be happy to learn that Git Extensions has a really nice Visual Studio integration as well. 
First thing you should be getting is Git Extensions.

With that, similar to TortoiseX family of tools you get nice context menu that gives you access to most common operations quickly, via GUI, and with no need to memorize command line options if you want to avoid it. You can also launch Git command line in the selected folder and then all power of git is at your disposal. Visual Studio
If you’re a .NET developer, you’ll want to work from within Visual Studio. I’m sure you’ll be happy to learn that Git Extensions has a really nice Visual Studio integration as well.

Bootstrapping The .NET Framework Without An MSI Installer
Posted by
jasper22
at
14:48
|
I recently needed to test the idea of whether or not I could bootstrap .NET v4.0 onto a WinXP machine, from a USB thumb drive, without an application installer for the target app. The goal was to insert a thumb drive, run the app directly from the root of the thumb drive and have .NET 4 installed onto the system if it wasn't already there, prior to the application starting up. The High Level ProcessAt a very high level, this is fairly simple:
When I got down into the weeds of doing this, I found a few very helpful items on the interwebs. To check for a specific version of .NET, I found this StackOverflow question, which has an answer that outlines the various registry entries you can look for. Framework Version Registry Key
------------------------------------------------------------------------------------------
1.0 HKLM\Software\Microsoft\.NETFramework\Policy\v1.0\3705
1.1 HKLM\Software\Microsoft\NET Framework Setup\NDP\v1.1.4322\Install
2.0 HKLM\Software\Microsoft\NET Framework Setup\NDP\v2.0.50727\Install
3.0 HKLM\Software\Microsoft\NET Framework Setup\NDP\v3.0\Setup\InstallSuccess
3.5 HKLM\Software\Microsoft\NET Framework Setup\NDP\v3.5\Install
4.0 Client Profile HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Client\Install
4.0 Full Profile HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Full\Install
The answer goes on to detail other aspects, such as service packs, but this information was sufficient for my needs. I also grabbed a copy of the stand-alone .NET 4 Redistributable package. To be honest, the less-than 50 meg package size is rather surprising - especially when you see the greater-than 230 meg package size for .NET 3.5! One other requirement was to prevent the user from having to click a bunch of "Next" and "License Agreement" buttons during the .NET 4 installation. I had a hard time finding documentation for the command line options online, but running the /? option against the redistributable gave me the information I needed. I ended up using "/passive /showfinalerror /promptrestart" as the options. This puts the installer into passive mode, which still displays progress but skips all the user interaction, will display an error message window if any problems occur, and will prompt the user to restart if a restart is required. Implementing The BootstrapperRemember that this is a proof of concept, only, at this point. Given that and my general lack of C++ or Delphi skills (though I was a Pascal programmer back in high school, 15 years ago), I wanted to skip past the hard part of putting together a real bootstrapper executable. So... I chose to go with Windows Script Host and VBScript. Fortunately, the WSH / VBScript documentation on MSDN is good enough to get me rolling - I haven't done VBScript since the classic ASP days, and haven't done VB in any form since 2005! But it all came back to me and with the help of the docs, I was able to produce this script: Dim WshShell, value
Set WshShell = WScript.CreateObject("WScript.Shell")ON ERROR RESUME NEXTSub Run(ByVal sFile)
Dim shell
Set shell = CreateObject("WScript.Shell")
shell.Run sFile, 1, true
Set shell = Nothing
End Subvalue = wshShell.RegRead("HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Install")
if (Err.Number <> 0) Or (value is nothing) then
Run("dotnet\dotNetFx40_Full_x86_x64.exe /passive /showfinalerror /promptrestart")
end ifrun("My.Actual.App.exe")
Yes, that's an "ON ERROR RESUME NEXT" in the 2nd line! ACK! I know... but we're limited in VBScript / WSH. The reason this is needed, is the RegRead call. If the key does not exist (and it won't, on a machine that doesn't have .NET 4 installed), an exception is thrown. We have to prevent the exception from failing the script and this is the only way I know of to do that. We then check for the presence of an error and run the .net installer if one was encountered.
Read more: LosTechies
- Check for .NET 4
- If not found, install
- If found, or after install, launch the real app
When I got down into the weeds of doing this, I found a few very helpful items on the interwebs. To check for a specific version of .NET, I found this StackOverflow question, which has an answer that outlines the various registry entries you can look for. Framework Version Registry Key
------------------------------------------------------------------------------------------
1.0 HKLM\Software\Microsoft\.NETFramework\Policy\v1.0\3705
1.1 HKLM\Software\Microsoft\NET Framework Setup\NDP\v1.1.4322\Install
2.0 HKLM\Software\Microsoft\NET Framework Setup\NDP\v2.0.50727\Install
3.0 HKLM\Software\Microsoft\NET Framework Setup\NDP\v3.0\Setup\InstallSuccess
3.5 HKLM\Software\Microsoft\NET Framework Setup\NDP\v3.5\Install
4.0 Client Profile HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Client\Install
4.0 Full Profile HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Full\Install
The answer goes on to detail other aspects, such as service packs, but this information was sufficient for my needs. I also grabbed a copy of the stand-alone .NET 4 Redistributable package. To be honest, the less-than 50 meg package size is rather surprising - especially when you see the greater-than 230 meg package size for .NET 3.5! One other requirement was to prevent the user from having to click a bunch of "Next" and "License Agreement" buttons during the .NET 4 installation. I had a hard time finding documentation for the command line options online, but running the /? option against the redistributable gave me the information I needed. I ended up using "/passive /showfinalerror /promptrestart" as the options. This puts the installer into passive mode, which still displays progress but skips all the user interaction, will display an error message window if any problems occur, and will prompt the user to restart if a restart is required. Implementing The BootstrapperRemember that this is a proof of concept, only, at this point. Given that and my general lack of C++ or Delphi skills (though I was a Pascal programmer back in high school, 15 years ago), I wanted to skip past the hard part of putting together a real bootstrapper executable. So... I chose to go with Windows Script Host and VBScript. Fortunately, the WSH / VBScript documentation on MSDN is good enough to get me rolling - I haven't done VBScript since the classic ASP days, and haven't done VB in any form since 2005! But it all came back to me and with the help of the docs, I was able to produce this script: Dim WshShell, value
Set WshShell = WScript.CreateObject("WScript.Shell")ON ERROR RESUME NEXTSub Run(ByVal sFile)
Dim shell
Set shell = CreateObject("WScript.Shell")
shell.Run sFile, 1, true
Set shell = Nothing
End Subvalue = wshShell.RegRead("HKLM\Software\Microsoft\NET Framework Setup\NDP\v4\Install")
if (Err.Number <> 0) Or (value is nothing) then
Run("dotnet\dotNetFx40_Full_x86_x64.exe /passive /showfinalerror /promptrestart")
end ifrun("My.Actual.App.exe")
Yes, that's an "ON ERROR RESUME NEXT" in the 2nd line! ACK! I know... but we're limited in VBScript / WSH. The reason this is needed, is the RegRead call. If the key does not exist (and it won't, on a machine that doesn't have .NET 4 installed), an exception is thrown. We have to prevent the exception from failing the script and this is the only way I know of to do that. We then check for the presence of an error and run the .net installer if one was encountered.
Read more: LosTechies
Preventing Open Redirection Attacks in ASP.NET MVC
Posted by
jasper22
at
14:25
|
Summary
ASP.NET MVC 3 includes a new change in the the Account Controller to prevent open redirection attacks. After explaining how open redirection attacks work, I'll This tutorial explains how you can prevent open redirection attacks in your ASP.NET MVC applications. This tutorial discusses the changes that have been made in the AccountController in ASP.NET MVC 3 and demonstrates how you can apply these changes in your existing ASP.NET MVC 1.0 and 2 applications. What is an Open Redirection Attack?
Any web application that redirects to a URL that is specified via the request such as the querystring or form data can potentially be tampered with to redirect users to an external, malicious URL. This tampering is called an open redirection attack. Whenever your application logic redirects to a specified URL, you must verify that the redirection URL hasn’t been tampered with. The login used in the default AccountController for both ASP.NET MVC 1.0 and ASP.NET MVC 2 is vulnerable to open redirection attacks. Fortunately, it is easy to update your existing applications to use the corrections from the ASP.NET MVC 3 Preview. To understand the vulnerability, let’s look at how the login redirection works in a default ASP.NET MVC 2 Web Application project. In this application, attempting to visit a controller action that has the [Authorize] attribute will redirect unauthorized users to the /Account/LogOn view. This redirect to /Account/LogOn will include a returnUrl querystring parameter so that the user can be returned to the originally requested URL after they have successfully logged in. In the screenshot below, we can see that an attempt to access the /Account/ChangePassword view when not logged in results in a redirect to /Account/LogOn?ReturnUrl=%2fAccount%2fChangePassword%2f.Read more: Jon Galloway
ASP.NET MVC 3 includes a new change in the the Account Controller to prevent open redirection attacks. After explaining how open redirection attacks work, I'll This tutorial explains how you can prevent open redirection attacks in your ASP.NET MVC applications. This tutorial discusses the changes that have been made in the AccountController in ASP.NET MVC 3 and demonstrates how you can apply these changes in your existing ASP.NET MVC 1.0 and 2 applications. What is an Open Redirection Attack?
Any web application that redirects to a URL that is specified via the request such as the querystring or form data can potentially be tampered with to redirect users to an external, malicious URL. This tampering is called an open redirection attack. Whenever your application logic redirects to a specified URL, you must verify that the redirection URL hasn’t been tampered with. The login used in the default AccountController for both ASP.NET MVC 1.0 and ASP.NET MVC 2 is vulnerable to open redirection attacks. Fortunately, it is easy to update your existing applications to use the corrections from the ASP.NET MVC 3 Preview. To understand the vulnerability, let’s look at how the login redirection works in a default ASP.NET MVC 2 Web Application project. In this application, attempting to visit a controller action that has the [Authorize] attribute will redirect unauthorized users to the /Account/LogOn view. This redirect to /Account/LogOn will include a returnUrl querystring parameter so that the user can be returned to the originally requested URL after they have successfully logged in. In the screenshot below, we can see that an attempt to access the /Account/ChangePassword view when not logged in results in a redirect to /Account/LogOn?ReturnUrl=%2fAccount%2fChangePassword%2f.Read more: Jon Galloway
15 Fresh Free PSD Website Layout 2011
Posted by
jasper22
at
14:24
|
1) Sleek: Web Layout Tutorial With PSD File
This Photoshop Action will show you how to create a professional web layout in seconds. Free PSD included! Only tested in PS CS4, but should work with 
6) How to create an elegant wordpress PSD theme
In this tutorial i will show you how to create an elegant WordPress PSD theme. You can use this web template also for consulting agency templates, services websites, marketing website templates, business website templates, finance website templates.
Read more: Design Inspiration
This Photoshop Action will show you how to create a professional web layout in seconds. Free PSD included! Only tested in PS CS4, but should work with

6) How to create an elegant wordpress PSD theme
In this tutorial i will show you how to create an elegant WordPress PSD theme. You can use this web template also for consulting agency templates, services websites, marketing website templates, business website templates, finance website templates.

Read more: Design Inspiration
Napkin PC
Posted by
jasper22
at
12:39
|


List of How to Windows 7
Posted by
jasper22
at
12:22
|
This section contains the best hacks, tips and tricks for your Windows 7 operating system. All the information available here has been divided to different categories to let you identify what are you looking for in a very easy and intuitive way. As you see, majority of the articles shown below have been laid down as How to Windows 7 tutorials which clearly explain to you the step-by-step procedure to follow to achieve the results you want. Thanks to these Windows 7 tricks nothing will be impossible to you anymore. You will be able to customize and personalize every and each aspect and feature of your Windows 7. You will amaze your friends by enabling hidden tools only expert technicians know and are able to turn on. You will make the operating system more performing and responsive by tweaking unknown “registry keys” which will let Windows 7 use the resource of your computer’s hardware in a better and more efficient way. At the beginning some of the commands, shortcuts and steps used in the tutorials will seems a little tricky and difficult to you, but don’t worry. The methods, the “patterns” the schemes used here are purposefully and intentionally repeated over and over again, so that after a little practice you will be able to identify where to “work” at a first glance! And now, a little warning. Nothing to worry about! 99% of these guides are safe to use and do not create any kind of damage to your computer. However, some of the hacks reported, if not executed literally and carefully might cause data loss. The best advice I can give you is that if you are unsure about something, just don’t do it! If you feel “odd” about a procedure or a step, contact me without further delay by filling out the form available on this page. Look and Feel
Read more: web talk
- How to Increase/Reduce the Font Size Text in Windows 7
- How to Turn Off/On Shadows in Windows 7
- How to Change the Default Folder Icon in Windows 7
- How to Delete/Hide Unread Mail Messages (emails) from the Welcome Screen in Windows XP/Vista/7
- Fast Trick to Hide Your Desktop Icons in Windows 7
- How to Prevent Users from Changing Themes in Windows 7
- How to Restore Default Desktop Gadgets in Windows 7
- How to Lock Your Windows 7 Theme (Prevent Users from Changing Theme)
- How to Turn On Animation Effect Slow Down in Windows 7
- How to Turn Off and Remove the Notification Area from Windows 7
- How to Customize Windows 7 Starter Edition
- How to Turn Off and Disable the Highlight Newly Installed Program Feature in Windows 7
- How to Remove and Hide the Digital Clock From the Taskbar in Windows 7
- How to Change the Default Sounds in Windows 7 Aero Theme
(more....)
Read more: web talk
Router password
Posted by
jasper22
at
12:19
|
Welcome to the internets most comprehensive Default router password database 2010. This is the internets most complete default router password database available. Simply select the Router Make from the dropdown list and click the Find Password button. This database is constantly updated with passwords from visitors like you!! If you know a password that's not listed here, please use the form to submit it. Remember, this is the worlds largest Router Password database and your help is needed to keep it that way. Read more: Router password
Top 10 Free Ways To Discover New Music Online
Posted by
jasper22
at
12:16
|

Bored with your music and want to discover some new bands or singers? There are two main ways you can do that online. You can use services which create music maps, allowing you to explore artists similar in genre to the artists you already listen to. Or you can use music blogs and websites that showcase independent or up-and-coming artists, whether the music is being reviewed, or posted by the musicians themselves. Some of these websites have a community built around them, which gives fans the opportunity to interact directly with these new talents.Here is a list of 10 free sites to discover new music.TuneGlue
TuneGlue is straightforward and easy to use. Put in the name of a musical artist you like in the search bar and before you know it, you’ll have a whole web of musical artists that are in one way or another, similar to the band you started with.
Using TuneGlue, you start out with 6 similar artists, and can continue to explore and expand on them. In the case of some artists, you can also find added information such as a small bio and a link to their website.
Music-Map
A less flashy alternative to TuneGlue is Music-Map. While TuneGlue only initially suggests 6 similar artists, Music-Map instantly reveals all the similar artists in their database, with the most similar musicians closest to the original search term. Music Roamer
Music Roamer adds another dimension to music map sites, by not only providing suggestions of similar artists, but also allowing you to listen to music directly on their site. The songs are powered by YouTube videos, but it should be said, in our experience, all of the tracks were live versions, and not always of very good quality. They also provide links to purchase the mp3s from Amazon. Read more: Eternal Code
How to Write an Operating System
Posted by
jasper22
at
12:07
|
Overview
This semester SigOPS will hold a series of meetings discussing how to build an operating system from scratch. We provide the structure for developing your Very Own OS, you write the code. It's that simple! The Plan
What follows is an outline of the next eight or so SigOPS meetings this semester. We'll be posting all the critical information on these here web pages, so if you miss one (or have missed everything up to this point), no need to worry. Just catch up and come to the next meeting.
Hopefully, any SigOPS member who wants to write an operating system will have done so by the end of this excursion. Stay tuned for information and updates on our progress!
Table of Contents
Read more: sigops
This semester SigOPS will hold a series of meetings discussing how to build an operating system from scratch. We provide the structure for developing your Very Own OS, you write the code. It's that simple! The Plan
What follows is an outline of the next eight or so SigOPS meetings this semester. We'll be posting all the critical information on these here web pages, so if you miss one (or have missed everything up to this point), no need to worry. Just catch up and come to the next meeting.
Hopefully, any SigOPS member who wants to write an operating system will have done so by the end of this excursion. Stay tuned for information and updates on our progress!
Table of Contents
0. Introduction
I. Development Environment
II. Debugging Methods
III. Applications
IV. Memory Management
V. Multitasking
VI. Interprocess Communication
VII. Hardware Interrupts and Drivers (work in progress)
VIII. Symmetric Multiprocessing (external link)
IX. References
Read more: sigops
10 (More) Hacking and Security Software Tools for Linux
Posted by
jasper22
at
11:56
|
I noticed that our list of hacking and security software tools for Linux was not enough so I figured out that I should add some more. But before anything else, thank you to those who commented the last time and shared their favorite hacking programs. --I've included some of those that you've mentioned on this new list for others to know about. Now without any more delay, here's our latest compilation of hacking and security tools for Linux:* Ettercap Ettercap is a console-based network sniffer/interceptor/logger that is capable of intercepting traffic on a network segment, capturing passwords, and conducting active eavesdropping against a number of common protocols. Ettercap supports active and passive dissection of many protocols (including ciphered ones) and provides many features for network and host analysis. Ettercap also has the ability to actively or passively find other poisoners on the LAN. * NiktoNikto is a web server scanner that is known to perform comprehensive tests against web servers for multiple items, including over 3500 potentially dangerous files/CGIs, versions on over 900 servers, and version specific problems on over 250 servers. It performs generic and server type specific checks. It also captures and prints any cookies received. * OpenSSH OpenSSH is a Free and Open Source version of the SSH connectivity tools providing encrypted communication sessions over a computer network. It encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other attacks. Additionally, OpenSSH provides secure tunneling capabilities and several authentication methods, and supports all SSH protocol versions. Read more: TechSource
4 free open source network management software
Posted by
jasper22
at
11:54
|
A Network Management System (NMS) is a combination of hardware and software used to monitor and administer a network. NMS systems make use of various protocols for the purpose they serve. For example, SNMP protocol allows them to simply gather the information from the various devices down the network hierarchy. NMS software is responsible for identification of the problem, the exact source of the problem and solving them. The NMS systems not only are responsible for the detection of faults but also for collecting the statistics of the devices over a period of time. They may include a library where the previous network statistical data over a period of time is stored along with the problems and the solutions that worked in the past. This library can come useful in case a fault is found. NMS software can consult the library and search for the best possible method to resolve the problem. In this post I gathered top 4 Free Open Source Network Management Software that you can use as an IT Administrator in your network, Whether you run small or enterprise network, you will find those tools handy and effective in doing your monitoring work as simple as it could be. 1- SpiceWorks
Available at: www.spiceworks.comManage Everything IT…for Free! Spiceworks is the complete network management software, helpdesk, PC inventory tools & IT reporting solution designed to manage everything IT in small & medium businesses. 
Available at: www.spiceworks.comManage Everything IT…for Free! Spiceworks is the complete network management software, helpdesk, PC inventory tools & IT reporting solution designed to manage everything IT in small & medium businesses.

2- OpenNMS
Available at: www.opennms.org 3- OpenQRM
Available at: http://www.openqrm.comRead more: zaHitchBlogs
Available at: www.opennms.org 3- OpenQRM
Available at: http://www.openqrm.comRead more: zaHitchBlogs
Subscribe to:
Comments (Atom)





