
Slingshot Brings Mac OS X Style LaunchPad To Ubuntu Linux

In the wake of the new Mac launcher, imitation apps are showing up for other operating systems to replicate the functionality of the Mac OS X Launchpad. One recent example for is JumpPad, which is mean to provide the Launchpad functionality in Windows. But if you would like to get this functionality in Ubuntu, then you can give Slingshot a try. It is a Launchpad style application launcher which can be be used with the Unity Launcher to quickly locate and run applications.
Read more: Addictive tips
Compile And Run VB, C# And F# Code Without Installing Visual Studio
Posted by
jasper22
at
11:53
|

Don’t have Visual Studio installed on your system and you want to compile some C# or VB code to verify the functionality of your project modules? You should try out FastSharp. It’s is a lightweight text editor to compile not only C# and VB code but also F#. It was designed to let users compile and run C# and VB code without having to open or install Visual Studio. All the Import statements required to compile code have already been appended which enables you to compile C# and VB code without any problems. The Import list is configurable. You can access it anytime and change it to meet your coding requirements. A small output console window beneath the code editor lets you identify errors and view outputs. FastSharp also offers a small desktop gadget to compile and run VB, C# and F# code right from the desktop.
On the main toolbar, you have options to compile and run code. If you’re dealing with C # or VB code files, you can open them as well by clicking Open. Before compiling the code, make sure that you’ve specified code language from pull-down menu present alongside Run command.
Read more: Addictive Tips
Lion Skin Pack 6.0 Transform Windows 7 To Mac OS X Lion
Transform Windows 7 To Mac OS X Lion
Support:
- Windows 7 SP1
- X86(32Bit) and X64(64Bit)
- All Language Versions
Programs:
Resource Hacker
http://www.askvg.com...brief-tutorial/
Moveex 1.0 by Alexander Frink
http://wwwthep.physi.../~frink/nt.html
Universal Theme Patcher 1.5.0.22 by deepxw
Win7BootUpdater v0 Beta 1 by jeff
RocketDock 1.3.5 by punk software
myBoard 1.1 by Yann.Alet
Lion Theme by bodik87 Refresh by Me
Read more: WinMatrix
How to Network Boot the BitDefender Rescue CD (PXE)
Posted by
jasper22
at
11:08
|
We’ve already shown you how to use the BitDefender Rescue CD to clean your infected PC, but what if you wanted to achieve the same thing only without a CD over the network? In this guide, we’ll show you how.
Image by baronsquirrel
Prerequisites
- It is assumed that you have already setup the FOG server as explained in our “What Is Network Booting (PXE) and How Can You Use It?” guide.
- You will see the “VIM” program used as the editor, this is mainly because it is widely available on Linux platforms. You may use any other editor that you’d like.
Overview
In the The 10 Cleverest Ways to Use Linux to Fix Your Windows PC, one of the things we’ve shown, was that it is possible to install an antivirus and scan your computer from an Ubuntu LiveCD. With that said, what if you wanted to make absolutely sure that your computer is not infected by scanning it with another antivirus?
To that end, you could use another antivirus rescue CD, and there are some out there that we have reviewed in the past like Kaspersky and Avira. The clever thing is, what if you wanted to add this additional tool to your PXE server, so you’d never again have to look for the CD of the utility?
We’ve done the legwork and found that, even though it requires some TLA post boot, the BitDefender Rescue CD is by far the easiest to get PXEable from the above options.
In the “How to Setup Network Bootable Utility Discs Using PXE” guide, we’ve promised that we will give another example for the “Kernel + Initrd + NFS method” and we shall deliver. The principle here is just the same as for the How To Network Boot (PXE) The Ubuntu LiveCD.
Read more: How-to geek
Man Makes a Living Scraping the Sidewalk for Gold and Diamonds
Posted by
jasper22
at
11:08
|

Believe it or not, the streets of New York really are paved with gold, but you have to get down and dirty to get your hands on it. For urban prospector Raffi Stephanian this isn’t an issue, just a great way to pay the bills.
Using only a Styrofoam cup, a butter knife and tweezers, 43-year-old Raffi scours the streets of New York’s Diamond District searching for gold, diamonds and other precious jewels. You’ve probably walked on 47th Street countless times and didn’t realize the riches that were right there in front of you, but don’t beat yourself up about it, Raffi was probably the only one who ever thought there was something valuable on the sidewalk. And that only because he worked as a stone setter, years ago, when he found gold scraps on the floor of a diamond exchange. He realized if he could find gold inside, then people must have carried it outside, as well.
Read more: Oddity Central
Secretly Use Facebook At Work By Disguising It As An Excel Sheet
Posted by
jasper22
at
11:06
|

Excelbook is an Adobe Air based application which you can use to browse Facebook at work without being caught by your boss. The interface can be easily mistaken for an MS Excel or Libre Spreadsheet. You can login to your Facebook account and get all important updates, while appearing to work on a regular task. To get started, login to your Facebook account from the File menu and allow access to Excelbook application from your Facebook account.
Warning: We will not be responsible if you get fired by your angry boss. Use it at your own risk.
Read more: Addictive Tips
לא עוצרים ב-CGI
Posted by
jasper22
at
10:54
|
להקת פופ מצליחה מיפן, בשם AKB48, החברות בה 60 בנות, צרפה אליה לאחרונה את החברה ה-61. ודווקא חברה זו, מושכת עכשיו את כל תשומת הלב של המעריצים, וגם לא מעט כלי תקשורת. הסיבה – החברה החדשה, שהשתתפה בפרסומת לסוכריות, היא ווירטואלית לגמרי, והוכנה באמצעות CGI.
חברות להקת AKB48 נשכרו כדי להופיע בסרטון פרסומת של חברת Glico, יצרנית דברי מתיקה יפנית. בסרטון מופיעות חברות הלהקה היותר פופולריות, מבין 60 החברות, וכאמור, דווקא החברה החדשה, העונה לשם Aimi Eguchi, גנבה את ההצגה.
ראו את הסרטון המצורף, ונסו לראות אם אתם מצליחים לאתר מי מבין חברות הלהקה המופיעות בו היא יציר מחשב:
מי היא Aimi?
בפרסומת תוכלו לראות את חברות הלהקה ממליצות על המוצרים של חברת Glico. גם Aimi ביניהן. אם טרם זיהיתם אותה, תוכלו לראות את התמונה שלה, המופיעה היום באתר הרשמי של הלהקה, כאחת מחברות הרשמיות.
יש לציין כי הלהקה היא יוזמה של מפיק יפני והלהקה מופיעה במקום אחד בלבד, בהיכל ייעודי. במהלך יום רגיל מבצעת הלהקה מספר הופעות, באמצעות הרכבים שונים של חברות הלהקה השונות. באתר הלהקה תוכלו לראות כיצד הלהקה מחולקת לכמה קבוצות, של כמה עשרות חברות בכל קבוצה, ואלה מופיעות יחדיו במופעים השונים.
Read more: newsGeek
Encrypt And Password Protect Sensitive Information In Your Emails
Posted by
jasper22
at
10:10
|
Disseminating sensitive information online isn’t easy and many people use different techniques to mask the content of private messages. Some might give dummy names to files or send them as zipped attachments but needless to say these measures don’t provide much security. Large companies might resort to other more expensive ways of securely transmitting sensitive information but a simple solution comes from Encipher.it which allows you to encrypt text on the AES encryption standard and protect it with a password. Recipients of encrypted messages will need the password to read your message. 

Read more: Addictive tips
How Stuff Works: Fiber Optic Cables [Science]
Posted by
jasper22
at
10:09
|
Most people are familiar with the general concept of fiber optic cables–light as a method of data transmission–but how do they really work? Find out in this informative video.
Read more: How-to geek
Word Aligned Hybrid (WAH) Compression for BitArrays
Posted by
jasper22
at
09:48
|
Introduction
After much searching the internet for a .net implementation for WAH compressed BitArray and not finding one, I decided to write and publish an article here so we the .net community are not left out as all the implementations are in the java language. This ties into a pretty advanced topic of bitmap indexing techniques for databases and I needed this for my upcoming RaptorDB Document data-store database engine.
What is it?
A BitArray is a data structure in .net library for storing true/false or bits of data in a compact form within an array of Int32 objects. A WAH or word-aligned hybrid BitArray is a special run length compressed version of a BitArray which saves a lot of space and memory. All the implementations that exist in java essentially duplicate the functionality of a BitSet that is the AND, OR, NOT and XOR operations with the compressed internal storage format.
In my implementation I defer the functionality of the BitArray to itself and just add compression and decompression routines. This is much faster than the java way at the expense of memory usage, to overcome this I have also added a FreeMemory method to release the BitArray contents and keep the compressed contents. Arguably if you are using 100s million bits then a full implementation is more performant than my implementation but for most of our usecases we are at most in the 10s millions of bits range.
This original method was invented at the Berkeley Labs of US Department of Energy, it is a project named FastBit and is used for high energy physics department experiments, you can see it here : FastBit site
Why should I care?
So what! you ask?, well as mentioned before BitArrays are used in an indexing technique called bitmap indexes (wiki) and Column based databases which store data in columns instead of rows, a example which you might know is Microsoft's PowerPivot for Excel which can process millions of rows in seconds. Interestingly Microsoft has only recently announced the implementation of bitmap indexes in the upcoming SQL Server platform post 2008 R2. It has long been in use by other RDBM vendors like Oracle.
How it works
The WAH compression algorithm is as follows:
- take 31 bits from the array.
- if all zeros then increment the zero count by 31.
- if ones count > 0 then output 32 bits with bit 32 =1 and bit 31=1 and 0-30 = ones count
- if zeros count >0 then output 32 bits with bit 32=1 and bit 31=0 and 0-30 = zeros count
- if zeros or ones count >0 then output as above before.
Read more: Codeproject
How do I compress files (via NTFS compression) from the command line?
Posted by
jasper22
at
09:46
|
A customer wanted to know whether there was a way to compress files and directories (in the sense of NTFS compression) from a script or from the command line. They knew about the Properties dialog, but they wanted something scriptable.
The command-line tool for this is COMPACT.EXE. Type compact /? for usage information.
The customer liaison was grateful for this information.
Thanks for the prompt response, and yes, this will meet our customer's need to compress specific files such as *.docx under a particular directory and all its subdirectories.
Um, *.docx files are already compressed. Compressing them again gains you nothing.
Read more: The old new thing
Xfce 4.8 & Xubuntu 11.04: the cure for the GNOME blues?
Posted by
jasper22
at
09:45
|
I think we can all agree that the latest 11.04 release of Ubuntu is their weakest in recent history. From a myriad of installation problems (I have not been able to install it successfully on any of my 3 different Dell/Lenovo laptops) to the unfinished and unpolished Unity interface...the problems just keep piling up.
I had a go at Fedora 15 and GNOME 3.0 as well...I needed a couple of Advil to wash down the pain of that experience. It may become something one day...but right now it's just a confusing mess.
So I crossed the Rubikon and went Xubuntu with Xfce 4.8...a really positive surprise.
Works like a proper desktop environment, light, fast, the panels are greatly improved (and better than GNOME 2.0 at this point already), etc...
Read more: Jacek Furmankiewicz
How to Test Banking Applications
Posted by
jasper22
at
09:43
|
Banking applications are considered to be one of the most complex applications in today’s software development and testing industry. What makes Banking application so complex? What approach should be followed in order to test the complex workflows involved? In this article we will be highlighting different stages and techniques involved in testing Banking applications.
The characteristics of a Banking application are as follows:
- Multi tier functionality to support thousands of concurrent user sessions
- Large scale Integration , typically a banking application integrates with numerous other applications such as Bill Pay utility and Trading accounts
- Complex Business workflows
- Real Time and Batch processing
- High rate of Transactions per seconds
- Secure Transactions
- Robust Reporting section to keep track of day to day transactions
- Strong Auditing to troubleshoot customer issues
- Massive storage system
- Disaster Management.
Read more: Software Testing Help
Anatomy of a PDF Hack
Posted by
jasper22
at
09:39
|
By Tomer Bitton, security researcher, Imperva
PDFs are widely used business file format, which makes them a common target for malware attacks. Because PDFs have so many "features," hackers have learned how to hide attacks deep under the surface. By using a number of utilities, we are able to reverse engineer the techniques in malicious PDFs, providing insight that we can ultimately use to better protect our systems. We'll take you through the process that a hacker uses to insert a piece of malware into a sample PDF.

By opening the PDF file with a text editor it is possible to see that there are some encrypted objects. The first circle, object 11, is a command to execute Javascript in object 12. The second and third circles, are a command for object 12 to filter the Javascript with AsciiHexDecode. The main reason for this filter is to hide malicious code inside the PDF and avoid anti-virus detection. This is our first red flag.
Read more: Read Write web
"Build Secure Database Applications with Microsoft SQL Server" Series To Be - Post 0 of X
Posted by
jasper22
at
09:36
|
- Databases are prime targets because they are foundational to many applications and are the principle stores of sensitive data.
- Responsibility for the protection of our databases is distributed between multiple groups. While an optimist might see this as providing multiple layers of protection, I'm concerned that without one group or individual having overarching responsibility, there tend to be significant gaps in security policies and procedures.
With this in mind, I am speaking with folks about ways they can improve the security of their database applications built upon Microsoft SQL Server. My objectives are to:
- Improve awareness of features and practices that can be used to make SQL Server databases tougher targets, and
- Encourage folks to engage in dialogs within their organizations about database security to ensure gaps are identified and addressed.
In order to engage a broader audience, I am providing much of this information here as a series of blog posts organized around the high-level practices that should be employed. As entries are posted, I'll convert each of these practices into links to make accessing of this information a bit easier:
- Harden the database server
- Control network communications
- Limit access to database services
- Assign minimal permissions
- Encrypt your data
- Defend against common exploits
- Monitor and enforce policies
Read more: Greg's Cool [Insert Clever Name] of the Day
Secure the Authentication Process
Posted by
jasper22
at
09:32
|
SQL Server supports two authentication mechanisms: Windows authentication and SQL Server (SQL) authentication. With Windows authentication, SQL Server simply validates a user’s Windows identity with an identity management solution such as Active Directory. With SQL authentication, SQL Server generates, stores, and manages instance-specific user name and password information. While SQL Server can be configured to employ SQL authentication in addition to the Windows authentication default, it is strongly discouraged as SQL authentication is vulnerable to brute-force attacks. That’s not to say that Windows authentication is invulnerable to attack. In fact a new feature, Extended Protection, was introduced with SQL Server 2008 R2 to thwart one such attack.
Extended Protection
The man-in-the-middle (MITM) attack is executed by a malicious application which impersonates the SQL Server service to a client and the client to the service. In doing so, the malicious application places itself in the middle of the communications channel between the client and server and from this vantage point can intercept messages transmitted between the two. (This attack is also referred to as authentication relay.)
To thwart this attack, SQL Server registers its identity as a Service Principle Name (SPN) with Active Directory (typically at the time of installation). The client obtains the SPN as part of the connection process and validates this against the SPN held by SQL Server. If the malicious application does not have access to the SPN, the connection is not completed.
This process is referred to as service binding and it protects against scenarios where the malicious application lures the client to it. If the client voluntarily connects to the malicious application (usually due to spoofing), then channel binding can be employed to block the MITM attack.
With channel binding, the SQL Server service sends the connecting client the public key associated with a private key it maintains. The client generates a value known as the Client Binding Token (CBT), encrypts it with the service’s public key, and transmits the encrypted CBT to SQL Server. Using its private key, SQL Server decrypts the CBT and then uses the CBT to encrypt the channel between it and the client. Without the private key, the malicious application cannot decrypt the CBT and therefore cannot access the data passed between the client and server.
Read more: Data Otaku
Multi-platform PaaS Provider DotCloud Comes Out of Beta

There's been a surge in platform-as-a-service providers in the past year, but many of them remain in private beta. Today one more is open to the public: DotCloud.
DotCloud supports PHP, Ruby, Python, Perl, Java, Node.JS, MySQL, Redis, RabbitMQ, Solr, MongoDB and PostgreSQL. Like many other PaaSes, it runs on Amazon Web Services.
Last month DotCloud bought DuoStack, a similar multi-platform PaaS.
As part of the move to general availability, DotCloud also announced the following new features to improve resilience during AWS outages. According to it announcement:
High Availability: Applications built on DotCloud can automatically span multiple availability zones and datacenters, seamlessly distributing traffic between locations and providing automatic failover.
Dynamic scaling: As traffic to a stack or database increases, DotCloud makes it incredibly easy to allocate additional resources to ensure it can effectively handle the load.
Read more: ReadWrite web
Google's Browser Interception Plugin For Chrome
Posted by
jasper22
at
16:58
|
Google has released a passive in-the-browser reconnaissance plugin, called the 'DOM Snitch'. By intercepting JavaScript calls to the browser infrastructure, it detects common cross-site scripting, mixed content and insecure DOM changes. The plugin displays the DOM modifications in real time so developers don't have to pause the application to run an outside debugger. It exports traces for easier collaboration and analysis.
Read more: Slashdot
WordPress.org Hacked, Plugin Repository Compromised
Posted by
jasper22
at
16:23
|
Back in April hackers gained access to the WordPress.com servers and exposed passwords/API keys for Twitter and Facebook accounts. Now, hackers gained access to Wordpress.org and the plugin repository. Malicious code was found in several commits including popular plugins such as AddThis, WPtouch, or W3 Total Cache. Matt Mullenweg decided to force-reset all passwords on WordPress.org. This is a great remainder for all users not use the same password for two different services.
Read more: Slashdot
Silverlight Debug Helper (Visual Studio Add-in)
Posted by
jasper22
at
16:15
|
If you are actively using my debug helper Add-in for Visual Studio which I released last fall, you may be pleased to learn that I've uploaded a new version. And if you're not using it yet, I invite you to take a look at it.
The tool has been renamed to "Silverlight Debug Helper" (formerly "Firefox Debug Helper") because I added support for Chrome and Internet Explorer to it. If you have the previous version installed, you may want to uninstall it first.
From now on, the Debug Helper can be found on this static page (also linked to in the menu at the right), so you don't have to dig through old blog posts to find the download links and description anymore. Let me know what you think, and happy debugging :-).
Read more: Mister Goodcat
Monitoring on Unix from scratch
Posted by
jasper22
at
16:02
|
Linux, and in general many Unix-like systems, bundle lots of useful command line tools for monitoring the resources of a machine for performance's sake, with tracked parameters such as occupied memory, CPU utilization, or disk requests.
This list of commands, complete with flags and sample output, should be run while there is some kind of load on the system, in order to find out for example which resources are scarce (usually I/O) and which are instead not the bottleneck and shouldn't be upgraded.
There is also a different family of tools which run their workloads over an empty system, like Iozone and other benchmarks; in this article our interest is over monitoring tools that run over an existing production system.
top
top is maybe the most famous monitoring tool, which Linux users like me commonly use at home. By default, it works in real time, showing the processes ordered by their CPU utilization.
You can use the -d $i flag to change the updating interval, but more importantly -b to get top measurements on the standard output (stop it with CTRL-C).
[11:03:58][giorgio@Desmond:~]$ top -b > top.log
^C[11:04:10][giorgio@Desmond:~]$ head top.log
top - 11:04:09 up 1:09, 3 users, load average: 0.00, 0.08, 0.12
Tasks: 166 total, 1 running, 164 sleeping, 0 stopped, 1 zombie
Cpu(s): 6.8%us, 2.0%sy, 0.0%ni, 88.0%id, 3.1%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 3344984k total, 2202872k used, 1142112k free, 451016k buffers
Swap: 3905532k total, 0k used, 3905532k free, 929932k cached
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
920 root 20 0 77108 19m 9348 S 2 0.6 2:16.51 Xorg
2515 giorgio 20 0 156m 16m 12m S 2 0.5 0:06.72 gnome-terminal
2933 giorgio 20 0 802m 291m 33m S 2 8.9 3:54.36 firefox-bin
free
free displays current RAM statistics. You can use the -m switch to display memory quantities in megabytes instead of 109553440-like byte amount.
By default, free runs only once: the -s 5 (or any other value) flag will make it print the information every 5 seconds.
The used and free column show the amount of used and free RAM in the system:
Read more: Web Builder Zone PeerIndex meets recruitment? Labels.io introduces its own social authority scores
Posted by
jasper22
at
15:57
|
Labels.io, the recruitment startup that wants to simplify the resume, has surfaced its social authority algorithm through the introduction of a Labels Weight score on user profiles.
Perhaps similar to PeerIndex or Klout, the Labels Weight attempts to measure a job candidate’s “online professional authority” by measuring the impact of their social web activity – Twitter, Facebook, Linkedin and the site’s own internal metrics. However, Labels.io says it’s different from other such systems in that it only factors in relevant content by filtering out social web updates that don’t correlate with a user’s specified skills (or tags) as filled out in their Labels.io profile.
So, for example, my endless tweets about coffee and related @ replies won’t increase my Labels Weight as they’ll be deemed to be off topic because I haven’t tagged ‘coffee’ as a skill. In contrast, conversations on Twitter about technology or the media that I partake in should help to boost that score especially if they are deemed to have authority. That said, Labels.io says its algorithm is designed to avoid being a popularity contest so, presumably, number of followers has less impact but perhaps ‘engagement’ more so.
Read more: TechCrunch
500 jQuery tutorials
Posted by
jasper22
at
15:56
|
Web site with 500 jQuery tutorials

SelectSwitcher jQuery Plugin

A plugin to switch content visibility based on the selected option of a select. Use the full power of jQuery to define your affected elements.
gSlider Lightweight jQuery Image Slider

gSlider is an interactive image slider built on jQuery. It is versatile, lightweight and easy to implement in any website or web applications.
Read more: jQueryRain
15 Amazing Free HTML5 Templates
Posted by
jasper22
at
15:27
|
HTML5 is now supported by all major browsers in some form. HTML5 brings us easy ways to add videos, audio, graphics, etc. HTML5 website templates are easy to use and can be modified according to your requirements, giving your website a professional look. In this post, I collected 15 Amazing Free HTML5 Templates for download. Enjoy!
1.Free HTML5 Website Template - Art of Business
Say hello to a new free HTML5 website template from TemplateMonster - this time it's designed for a premium business website. As every other free website template we deliver this one also has all of the PSD source files included into the download package for you to be able to fine tune the result.

Read more: Web Builder Zone
Sending Richly Formatted Emails with .NET
Posted by
jasper22
at
15:26
|
Richly formatted emails can require quite a bit of CSS, but since email clients don’t always handle CSS well the styles need to be inlined. With Ruby this is easily handled with the Alex Dunae’s Premailer library, but calling it from .NET isn’t palatable to most developers. So Martin H. Normark built a .NET version called PreMailer.NET.
PreMailer.Net is based on code from these two projects:
A CSS Parser for .NET (by The Dynamic Programmer).
A .Net CSS Selector Engine, called Fizzler.
For those who would like to try the original you can check out Kevin Blake’s introduction on executing Ruby code from .NET. Changes to Premailer may be needed to support the IronRuby runtime.
Read more: InfoQ
Silverlight, HTML and the WebBrowser Control for Offline Apps
Posted by
jasper22
at
15:24
|
“Silverlight is a browser plug-in”
In the early days of Silverlight, it was fairly easy to understand that Silverlight content would always be rendered inside of a browser window (whether that be IE, Chrome, Firefox or Safari) where it was surrounded by the hosting HTML content and JavaScript. The HTML was hosting Silverlight rather than the other way around.
Silverlight has a pretty strong interoperability layer between the CLR code running inside the plug-in and the HTML DOM and JavaScript of the surrounding page so you could use Silverlight to exercise some “control” over the hosting HTML/JS and vice versa but HTML was the starting point.

and so if you had a bunch of HTML content to display and wanted to mix in a bit of Silverlight then it was fairly clear what your options were until…
When Silverlight 3 came along, it was possible to take a Silverlight application out of the browser and you ended up with a situation like this;
Read more: Mike Taulty's Blog
YourKit Profiler for .NET
Posted by
jasper22
at
14:51
|

- Supports:
- .NET Framework 2.0, .NET Framework 3.x, .NET Framework 4
- Integration with Microsoft Visual Studio 2005, 2008 and 2010
- Windows 2003/XP/Vista/2008/7
- 32-bit and 64-bit systems
Read more: YourKit
decompile-dump
Posted by
jasper22
at
14:41
|

Partial stuxnet source decompiled with hexrays, if anyone has better decompile tools feel free to contribute better versions. — Read more
Read more: GitHub
Project RIPS – Status
Posted by
jasper22
at
13:39
|
During the past month I spend a lot of time improving RIPS – my static analysis tool for PHP vulnerabilities. You can download the new version 0.40 here. In this post I will give a short project status report.
Whats new
There has been a couple of bugfixes and improving especially regarding file inclusions which are vital for correct analysis. Also RIPS now tries to analyse SQL queries on quotes before a decision on correct securing is made. However this feature is still not 100% working correctly in all cases.
// safe
$name = mysql_real_escape_string($_GET['name']);
mysql_query("SELECT * FROM users WHERE name = '$name'");
// vulnerable
$id = mysql_real_escape_string($_GET['id']);
mysql_query("SELECT * FROM users WHERE id = $id");
The main new visible features are graphs. Besides the list of all scanned files RIPS now gives a nice overview on how files are connected to eachother, what files accept sources (userinput) and what files have sensitive sinks or vulnerabilities. It also splits the scanned files in main files (blue) and included files (red) so that entry points can be spotted easily.
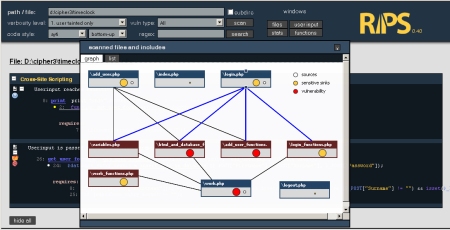
Read more: Reiners’ Weblog
Mobile Security – Users Just Don’t Care
Posted by
jasper22
at
12:47
|
It’s not that users “don’t want to keep their data safe”. They do. Most corporate users don’t want their personal or corporate, private information, available to someone else. They don’t want their email stolen or their contacts pillaged. So why do people insist on ignoring the multitude of security recommendations on how to have a more secure mobile work environment? The answer to this question is that inside, users really just don’t care.
The average corporate user of a mobile device has a litany of reasons why they think they don’t need to listen to the advice of their security organization. Some of these reasons are more legitimate than others, but what they really boil down to is the fact that they all indicate a lack of economic incentive when compared against required effort. The end result is that the user just doesn’t care about the problem.
- There are so many phones out there, it won’t happen to me. The chances are too slim.
- I don’t understand the danger here? I mean it’s a smartphone, nobody attacks phones.
- What do you mean I have to act in a secure manner? How do I do that?
- But I downloaded this app from the official marketplace. What do you mean it’s not secure?!
- You put firewalls and antivirus garbage on my laptop and it’s slow as heck, and I STILL get infected. Security doesn’t work.
Read more: Veracode
Automated License Header Extension for Visual Studio (define the license once, let VS auto-magically add it to new files...)
Posted by
jasper22
at
12:46
|

New files will automatically include the license headers defined in the current project.
License Header Manager allows you to:
- Define license headers per Visual Studio project and per file extension
- Share license headers between projects via "Add as Link"
- Add, remove and replace headers at any time for one or all files
- Put your license headers in #regions
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: License Header Manager for Visual Studio
.NET StockTrader 5 Sample Application
Posted by
jasper22
at
12:44
|
Overview
This application is an end-to-end sample application for Windows Azure and Microsoft cloud technologies. It is a service-oriented application based on the .NET Framework 4.0, including ASP.NET and Windows Communication Foundation (WCF). It illustrates many of the .NET enterprise development technologies that can be used for building highly scalable, "cloud-connected" applications. The application demonstrates a single code base that works on traditional servers, Hyper-V private clouds, and in the Windows Azure public cloud, including hybrid cloud scenarios.
The download includes the automated setup for the .NET StockTrader 5.0 and the Configuration Service 5.0, with associated technical documents that explain how to run and reconfigure the .NET StockTrader service-oriented application. Additional documentation in the download provides the steps necessary to implement the Configuration Service 5.0 in your own applications and services for central configuration management; distributed caching; load-balancing and failover across clustered service nodes. The sample includes:
· .NET StockTrader 5.0 composite Web application and middle tier services.
· Optional Windows Azure Projects for deploying to the cloud.
· New modes for Advanced Web Service (WS-*) message-level security and interoperability with a variety of non-Microsoft platforms via the SOA architecture.
· Configuration Service 5.0 with technical guides and samples.
· Capacity planning tool for running multi-agent benchmarks against the .NET StockTrader services.
· WSTest 1.5 Web services benchmark.
Read more: MS Download
Anonymous Typed Classes in C#
Posted by
jasper22
at
12:41
|
Introduction
MSDN Definition: Anonymous types provide a convenient way to encapsulate a set of read-only properties into a single object without having to explicitly define a type first. The name is generated by the compiler and is not available at the source code level or our application cannot access it. The type of each property is inferred by the compiler.
Anonymous types are a new feature introduced with C# 2.0. Anonymous class is class that has no name and it can help us to increase the readability and maintainability of applications by keeping the declarations of variables much close to the code that uses it.
We create anonymous class by using the new keyword and a pair of braces defining the fields and values that we want the class to contain. For example:
myAnonyClassObject = new { Name = "Abhimanyu", Age = 21 };
Above class contains two public fields called Name as I have initialized a string "Abhimanyu" and Age as I have initialized an integer 42. Compiler generates its name and it is unknown to us.
Now think, if we don't know the name of the class then how we will create an object? This is called anonymous class which can't be known.
After all we have one thing in hand; we can define it as variable by using var keyword. var keyword causes the compiler to create a variable of the same type. For example:
var myAnonyClassObject = new {Name = "Abhimanyu", Age = 21};
Now, we can access anonymous class fields by using dot notation. For example:
Console.WriteLine("Name:{0} Age:{1}", myAnonyClassObject.Name, myAnonyClassObject.Age};
We can also create other instances of the same anonymous class but with different values. For example:
var newMyAnonyClassObject = new {Name = "Deepak", Age = 23};
Read more: C# Corner
YouTrack 3.0 — Fully Customizable Bug Tracker, Now Free For Small Teams
Posted by
jasper22
at
12:40
|
This spring-summer time appeared to be very hot for JetBrains. And today we are happy to announce one more major release —please welcome YouTrack 3.0, a fully customizable version of our intelligent issue and bug tracker with a Free Pack now available for small teams.
YouTrack 3.0 introduces two major enhancements: customizable workflow and complete issue attributes customization. With these additions, a team can completely automate the issue life-cycle management based on its specific process needs, while still enjoying an intelligent, extremely usable and developer-oriented issue tracker.
With YouTrack 3.0, now you can:
- Define your own workflow to automate issue life-cycle management. Watch demo.
- Customize the set of issue attributes and their values
- Submit issues by email
- Automatically close or modify any related issue attributes from VCS Commit Comment
- Access and handle your issues from your mobile device
(more...)
Read more: JetBrains zone
[Silverlight] How to use mouse wheel on Silverlight and Chrome when Windowless is enabled
Posted by
jasper22
at
12:39
|
In Silverlight, the mouse wheel works very well with every main browser (Internet Explorer, Firefox, Chrome, etc.) but not when Windowless is enabled. When this feature is enabled, NAPI based browsers like Chrome or Firefox don’t allow Silverlight to manage the mouse wheel. This article explains how to get the mouse wheel event using DOM.
This article is based on code published on Compiled Experience but I’ve added some modifications to consider elements inherited from ItemsControl.
To use this behavior easily in your application, we’re going to create a Silverlight “Behavior” which will be added to your ListBox, ComboBox, etc.
Code is separated into 2 parts :
The “helper” code used to get information about wheel in DOM.
The behavior which calls the “helper” and which will be added to XAML.
public class MouseWheelEventArgs : EventArgs
{
public Point Location { get; private set; } public double Delta { get; private set; }
public bool Handled { get; set; }
public MouseWheelEventArgs(double delta)
: this(delta, new Point())
{
}
public MouseWheelEventArgs(double delta, Point location)
{
Delta = delta;
Location = location;
}
}
public class MouseWheelHelper
{
private static Worker MouseWheelWorker;
private bool isMouseOver;
public MouseWheelHelper(UIElement element)
{
if (MouseWheelWorker == null)
MouseWheelWorker = new Worker();
MouseWheelWorker.Moved += HandleMouseWheel;
element.MouseEnter += HandleMouseEnter;
element.MouseLeave += HandleMouseLeave;
element.MouseMove += HandleMouseMove;
}
public event EventHandler<MouseWheelEventArgs> Moved;
private void HandleMouseWheel(object sender, MouseWheelEventArgs args)
{
if (isMouseOver)
Moved(this, args);
}
private void HandleMouseEnter(object sender, EventArgs e)
{
isMouseOver = true;
}
Read more: Aymeric's blog
Mozilla creating Firefox PDF viewer in HTML5
Posted by
jasper22
at
12:38
|
Mozilla is developing a browser-based PDF reader, looking to help Firefox users avoid the security and performance issues associated with current plug-ins.
The PDF reader will be created in HTML5 and JavaScript, Mozilla said.
However, it's only four weeks into development, and a Mozilla spokesperson said it will be months before this feature arrives in Firefox. The development files are already available through GitHub, and an early demo version is available online, but it didn't properly display files we tested it with.
Read more: PC Pro 7 Important Creative Thinking Skills
Posted by
jasper22
at
12:37
|

We were on a call recently with an extended creative team generating ideas for client videos. During breaks, I found myself jotting down examples of important creative thinking skills the team was exhibiting. These seven creative thinking skills demonstrated during the call are ones which benefit both those who display them and those working with them too:
1. Suspending advocacy of your own idea to push for another person’s concept.
It’s helpful to be able to come into a creative situation and demonstrate your willingness to champion another person’s idea. It can open the way to getting others to support your thinking, as well.
2. Putting your own idea to the same test you apply to an idea from someone else.
When it comes to your own ideas, it’s easy to be a hypocrite and apply all kinds of hurdles to other ideas while letting your own thinking slide by unchallenged in your own mind. Just one thing to remember: don’t become somebody known for doing this!
3. Combining two different ideas and making them better (not muddled) as one idea.
Often (maybe “almost always”) compromising on creative ideas leads to something nobody likes, recognizes, or thinks satisfies the original objective. Being able to dissect ideas to pull out highlights and put them together as something new, however, is entirely different, and a great skill to have.
4. Letting someone else take “ownership” of your idea in order to build support for it.
This skill really tests whether you believe so strongly in an idea you’re willing to let someone else step up and take it on as their own idea to see it prevail. The key to seeing your idea win out can be letting somebody else be the vocal proponent for it.
Read more: Blogging Innovation
Videos of my MonoTouch and Mono and Mobile sessions from NDC 2011
Posted by
jasper22
at
12:33
|
Two weeks ago, I was in Oslo, Norway getting ready to present a few talks at the Norwegian Developer's Conference 2011 and now two weeks later, it's about time I point you to my MonoTouch and Mono and Mobile talks from the conference!
First I would like to thanks for everyone involved with the conference, the hosts, the staff, the speakers and the attendees. There was so many great talks going on that you're forced to download the videos afterwards!
All the videos from the conference are up on the NDC website for your viewing pleasure - http://ndc2011.no/agenda.aspx?cat=1071, I highly recommend Ander's talk on Coffeescript and Ryan's talk on Node.js as good starting points.
My MonoTouch: State of the Union talk is available directly here - http://ndc2011.macsimum.no/SAL4/Torsdag/1140-1240.wmv
My Mono and Mobile talk is available direct here - http://ndc2011.macsimum.no/SAL4/Torsdag/1500-1600.wmv
Whilst at the conference, there was a live panel discussion for .NET Rocks on Mobile Development - http://ndc2011.macsimum.no/SAL4/Torsdag/1740-1840.wmv
Read more: ChrisNTR
11 useful classes you'll love
Posted by
jasper22
at
12:30
|
Introduction
These utility classes are piece of code I gathered from internet the last years. And I'm sure you'll find classes you'll use everyday here.
My goal is not to create a library, but just to gather cool piece of code at the same place so people can use them by copy pasting, without any dependencies.
If that's not already the case, I highly recommend you to gather cool piece of code you see on the web and having your personal framework correctly saved in a code repository somewhere. It will save you lots of time.
Some of you will tell that you don't have to reinvent the weel, and that's right.
But the point is that sometimes you have very specific and simple (but not easy) tasks to do and don't want the burden of yet another library. Moreover you are the most likely person who will want to reuse these classes later : you already know where to find them, how they behave, what pitfalls they have, and what you learnt by using them.
I've kept original comments in the code, so sometimes, you will be able to find the original author.
I want to thanks people who shared these classes on the net, and who saved me lots of time and money. The best thing I can do is to spread their work.
All unit tests or code snippet presented here pass.
- Introduction
- Content
- 11 useful classes
- LogonUser : how to impersonate a user, the easy way
- PathUtil : how to get a relative path from an absolute folder
- LambdaExtensions : extension methods to extract a property name from an expression.
- NotifyPropertyChangedBase : a concrete use case of LambdaExtensions.
- DisposableWrapperExtension : how to dispose effectively a WCF CommunicationObject
- EnumExtensions : How to easily manipulate a flag enum.
- ThreadSafeDictionary : how to add an item atomatically, the easy way
- BlockingStream : how to easily mock a client/server communication with a single Stream.
- WeakCollectionChangedListener : how to stop memory leakage when a listener have shorter life span than the listened object.
- WeakObservableCollection : a concrete use case, a wrapper around the listened object and owned by the listener.
- AssertEx : A class to make your tests readable.
- Conclusion : what utility class do you own and use frequently ?
Read more: Codeproject
5 reasons why side projects are good business
Posted by
jasper22
at
12:29
|
Side projects can be businesses or just-for-fun efforts that we do in our nonworking hours, usually out of some passion for the work. There are some risks associated with taking up side projects. For example, I have at least one friend who was fired partly because he spent too much time working on a side project, while I have at times previously picked up way too many side projects and ended up burned out as a result. However, despite the risks, I strongly believe that most of the time, side projects benefit both the individual and the employer.
Here are a few reasons why side projects make good business sense.
- New skills. I love to use side projects as a way to stretch myself and learn new things that I wouldn’t normally do as a result of my regular work. In the past, I’ve had side projects where I co-founded a nonprofit to organize community technology events, co-founded a location-based startup, wrote a book about community, wrote a cookbook, started blogs and much more. Out of each of these efforts, I’ve learned many new skills that I’ve applied in my day job. I’ve personally benefited from each of these efforts, but the companies I’ve worked for have also benefited from the skills learned in my off-hours.
- Connections and networking. Most of my side projects have given me an excuse to meet new people. I’ve made friends and valuable industry connections that I can talk to about new ideas or trends. Especially for those of us working in technology, many of these connections bleed over from one project or company to the next. Having additional contacts in your industry gives you a broader base of people to talk to about new side projects or interesting things that you are working on in your day job.
- Sense of accomplishment. While many of us are lucky enough to have great jobs where we get a sense of accomplishment from our regular work, it isn’t always the case. There is nothing quite like launching a fun project to boost your overall mood and give you a sense of excitement. For me, the accomplishments from my side projects tend to have a positive impact on my regular job, too, since my improved mood makes me even more productive when it comes to other work. Employees with improved self-confidence from a big accomplishment can often become better workers in other areas.
Read more: GigaOm
Remote Desktop Connection and Remote Assistance (Both Methods Explained)
Posted by
jasper22
at
12:09
|
Introduction
Remote Desktop helps a person to remotely access another computer. You can access the other computer like you are directly working on it. It can help us in solving our friends' problems from a remote location, problem debugging by a technical expert, etc.
How to Perform
For performing Remote Desktop Connection, follow these steps (for Windows 7):
- Press window key+break.
- Go to Advanced system settings.
- Go to Remote tab.
- Check the option saying “Allow Connection from computer running any version of remote desktop.
- Click on Apply & then on ok.
- Goto Start->All programs->Accessories.
- Select Remote Desktop Connection.
- Enter the IP address of person you want to connect to.
- Click on Connect.
- Enter the desired username & password.
- Click on ok.
- Remote Desktop Connection is made.
Another way is: Window remote assistance feature (For windows 7).
For doing this, follow these steps:
- Press Win key+Break.
- Click on Advanced system settings.
- Choose Remote Tab.
- Check the box saying “Allow Remote Assistance Connection to this Computer”.
- Click on Apply & then ok.
- Goto start.
- In the search bar, type troubleshooting.
- Open it.
- On the left side of the troubleshooting window, click on “Get help from a friend”.
- Click on “invite someone to help you”.
- Click on Save this invitation as a file.
- Send this file to the person whom you want to connect remotely.
- Password is shown in the file you just saved. You need to give that password to your friend to provide access to your computer.
Read more: Codeproject
Introducing New Pre-computed Widgets for Your Blog and Website
Posted by
jasper22
at
12:08
|
We have been working on making Wolfram|Alpha Widgets more customizable so that it’s easier for bloggers and webmasters to incorporate them in their sites and posts. We’re now pleased to share a few updates with you.
The most exciting new feature is the pre-computed “inline” widget. With these widgets, readers get computational knowledge from Wolfram|Alpha directly, without even clicking a button! As a new twist on the iframe-style widgets, you can now choose to hide or show the inputs as well as hide or show results right on the page as a streamlined addition to your own content.
Here are some examples:
This widget will give your readers the distance from New York City to their location. It pre-computes the distance based on the reader’s IP address. If users want to know the distance to NYC from another location, all they have to do is click the plus sign to open the widget input area, where they can enter a different starting location.
Read more: Wolfram|Alpha Widgets
The 20 Essential Habits of Highly Passionate People
Posted by
jasper22
at
12:03
|
I’ve always worked hard at whatever I’ve been doing. My work-ethic comes from doing what I enjoy, and not forcing myself to do something.
Highly passionate people aren’t just lucky, they share common characteristics. They work hard, they trust their intuition and they persevere.
I personally don’t see myself having any other options than following my passion. Without doing what I truly want, life would be without color, without joy and without meaning.
We all have the habits necessary, we just need to let them out.
1. Excitement
When I was in my late teens, I wasn’t even remotely familiar with terms like “follow your passion”, “listen to your heart” or “go with your intuition”. As the years have passed, these concepts have grown and I’ve realized that the only thing that matters is what I am excited about in this very moment. It’s far too easy for me to start questioning what I’m doing. Let’s take language learning for example. It’s easy for me to argue that it’s a waste of time. But in the end, what matters is how much I’m enjoying myself. You can never know where you’ll end up, so might as well enjoy the ride, right? We’ve been taught that logic is superior, but is it really? Life isn’t a game where all the variables are known, so there’s no way you can predict the future (unless you have special powers).2. Courage
Courage is something you build up. When I was younger, I was afraid a lot more than I am now, but I didn’t let it control my life.Read more: Wake up cloud
Session and ViewState alternative
Posted by
jasper22
at
12:02
|
Introduction
When you want to remember your data in an ASP.NET site after a postback, you will have to use Session or ViewState to remember your data. It’s a lot work to use Session and ViewStates, I just want to declare variables like in a desktop application.
So I created a library called Merula SmartPages. This library will remember the properties and variables of your page.
Using the code
You can download the SmartPages Library here
Using the SmartPages library is very simple. All that you’ll have to do is create a new ASP.NET page and change the extension of the class from Page to SmartPage.
using System;using MerulaSmartPages;
namespace SmartPageTester.smartpages
{
public partial class MyPage : SmartPage
{
protected void Page_Load(object sender, EventArgs e)
{
}
}
}
In ASP.NET, this won’t work:
using System; using System.Web.UI;
using MerulaSmartPages;
namespace SmartPageTester.smartpages
{
public partial class MyPage : Page
//normal asp.net page (Change Page to SmartPage and it will work!)
{
private string value;
protected void Page_Load(object sender, EventArgs e)
{
if(!IsPostBack)
{
value = "<h1>Hello world!</h1>"; //set the value
}
else
{
Response.Write(value); //wont work, value will be empty
}
}
}
}
Read more: Codeproject
.NET Interview Questions 2; Answers
Posted by
jasper22
at
10:04
|
Describe the difference between a Thread and a Process?
--- Both are individual execution paths, but process timeslicing (and memory space) is enforced by the OS, while thread differentiation is enforced by applications.
What is a Windows Service and how does its lifecycle differ from a "standard" EXE?
--- Services are loaded by the operating system and run in contained process spaces detatched from user interaction; users logging on and off the system have no impact on them.
What is the maximum amount of memory any single process on Windows can address? Is this different than the maximum virtual memory for the system? How would this affect a system design?
--- Windows processes are allowed 4GB of virtual address space, regardless of the actual amount of memory on the machine. Windows x64 allows 16TB of address space.
What is the difference between an EXE and a DLL?
--- EXEs can be launched as processes by the operating system. DLL executable code must be invoked by an existing process.
What is strong-typing versus weak-typing? Which is preferred? Why?
--- Strong-typing refers to defining the specific type of a reference at compile time rather than at run time. This results in more efficient execution and memory optimizations at compile time, as well as reduces the chance of a programmer accidentally providing a value of a type another component wasn't expecting.
Corillian's product is a "Component Container." Name at least 3 component containers that ship now with the Windows Server Family.
--- Component containers implement the IContainer interface to wrap components, providing a meta-architecture for organizing, interacting and communicating with the components.
What is a PID? How is it useful when troubleshooting a system?
--- (Ambiguous) This could refer to either a Microsoft Product ID -- the unique key that brands each activatable component installed on a system -- or to a Process ID, which is a means of referring to a specific process in calls to the Windows API.
How many processes can listen on a single TCP/IP port?
--- One.
Read more: Michael Williams – Master of None
Net.TCP Port Sharing
Posted by
jasper22
at
09:32
|
Windows Communication Foundation (WCF) provides a new TCP-based network protocol (net.tcp://) for high-performance communication. WCF also introduces a new system component, the Net.TCP Port Sharing Service that enables net.tcp ports to be shared across multiple user processes.
Background and Motivation
When the TCP/IP protocol was first introduced, only a small number of application protocols made use of it. TCP/IP used port numbers to differentiate between applications by assigning a unique 16-bit port number to each application protocol. For example, HTTP traffic today is standardized to use TCP port 80, SMTP uses TCP port 25, and FTP uses TCP ports 20 and 21. Other applications using TCP as a transport can choose another available port number, either by convention or through formal standardization.
Using port numbers to distinguish between applications had security problems. Firewalls are generally configured to block TCP traffic on all ports except for a few well-known entry points, so deploying an application that uses a non-standard port is often complicated or even impossible due to the presence of corporate and personal firewalls. Applications that can communicate over standard, well-known ports that are already permitted, reduce the external attack surface. Many network applications make use of the HTTP protocol because most firewalls are configured by default to allow traffic on TCP port 80.
The HTTP.SYS model in which traffic for many different HTTP applications is multiplexed onto a single TCP port has become standard on the Windows platform. This provides a common point of control for firewall administrators while allowing application developers to minimize the deployment cost of building new applications that can make use of the network.
The ability to share ports across multiple HTTP applications has long been a feature of Internet Information Services (IIS). However, it was only with the introduction of HTTP.SYS (the kernel-mode HTTP protocol listener) with IIS 6.0 that this infrastructure was fully generalized. In effect, HTTP.SYS allows arbitrary user processes to share the TCP ports dedicated to HTTP traffic. This capability allows many HTTP applications to coexist on the same physical machine in separate, isolated processes while sharing the network infrastructure required to send and receive traffic over TCP port 80. The Net.TCP Port Sharing Service enables the same type of port sharing for net.tcp applications.
Read more: MSDN
Virtual Desktop Infrastructure (VDI) With Ubuntu Linux
Posted by
jasper22
at
17:59
|
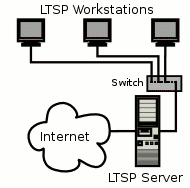
Looking to deploy Virtual Desktop Infrastructure (VDI) with Ubuntu Linux?
Virtual desktop infrastructure with Ubuntu Linux is ideal for anyone who is concerned about security of WAN based VDI. It is also perfect for organizations hosting their applications in the cloud, utilizing software-as-a-service through a web browser. VDI with Ubuntu Linux eliminates the maintenance of desktop devices, and reduces the number of hard drives in your IT footprint.
Linux Terminal Server Project (LTSP) allows the centralized deployment of virtual desktops on a local area network. Virtual desktop devices (thin clients) are connected to a switch on the LAN which connects to a server or cluster of servers delivering a desktop environment and applications.
LTSP is integrated into Ubuntu 11.04 and earlier versions. The logical choice for deployment is Ubuntu 10.04, a LTS version. LTS stands for long term support, which provides three years of security and maintenance updates.
Low Cost VDI with Ubuntu Linux
With LTSP organizations can recycle old Desktop PCs (800 MHz, 256MB RAM) or deploy new low footprint and energy efficient thin clients. A properly sized quad-core server could power up to 50 thin clients, providing desktop environments at a relatively low cost. Cost savings are most notable in maintenance and security over the years. Desktop hardware refresh cycles are between 7 and 10 years, thanks to the lack of spinning hard drive in each desktop device. Backups take place only in the server room. Desktop device replacement is as simple as drop in and power on (unless you have security customizations).
LTSP Technical Overview
Thin client devices in a virtual desktop deployment with Ubuntu Linux boot over your local area network. The virtual desktop environment and applications are executed on the server in a read only format. Users are still able to customize their desktop’s as well as access personal and shared fire storage. Applications can be delivered from local or remote application servers and can be Windows or Linux based.
Read more: Bihlman.com
pyscripter
Posted by
jasper22
at
17:58
|
PyScripter is a free and open-source Python Integrated Development Environment (IDE) created with the ambition to become competitive in functionality with commercial Windows-based IDEs available for other languages. Being built in a compiled language is rather snappier than some of the other Python IDEs and provides an extensive blend of features that make it a productive Python development environment.
Support: Get support on PyScripter by emailing to pyscripter@gmail.com or by visiting the PyScripter Internet group and posting your questions and comments.
Read more: Google Code
How to Integrate FxCop in VSTS 2010?
Posted by
jasper22
at
17:55
|
FxCop is standalone tool that can analyse managed code assemblies. It gives report about improvement in code based on Microsoft standard coding guidelines. However you can also add your rules in this tool.
FxCop is not integrated into Visual studio. There is separate extension (FxCop Integrator ) which can integrate Fxcop in Visual Studio 2010.
How to Install
You can install FxCop Integrator as independent installer or as extension in Extension Manager.

Read more: Beyond Relational
Head-to-head benchmark: C++ vs .NET
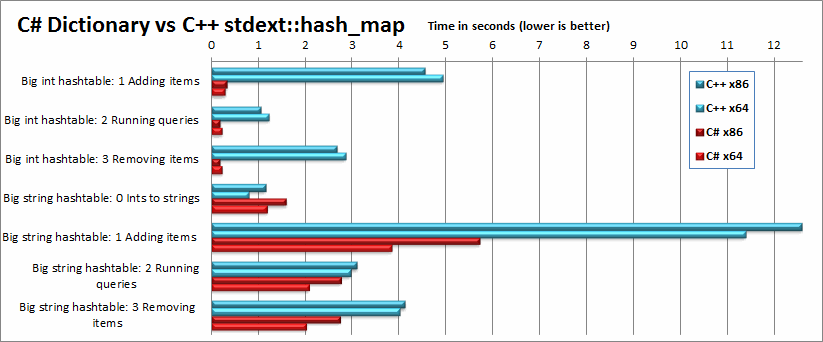
Introduction
I love the .NET Framework, C# and IntelliSense, but a lot of people are still saying it's slower than C++, pointing out that video games and "major applications" are still written in C++. Naysayers often point out that apps like Office, Internet Explorer, and Windows Media Player are still written in C++, apparently implying that C++ is still the best choice for performance. But wait, isn't this just because those applications are older than the .NET Framework itself, or because the .NET Framework has lousy support for DirectShow, or less-than-ideal support for Direct3D?
Well, I've been using C# for years and rarely had any complaint about its performance--that is, until I wrote a program for a Pocket PC and was shocked to discover that it required 35 seconds to start up.
With this article, I am attempting to make a fair comparison between the performance of C# and C++ (unmanaged), in both desktop and mobile (Windows CE) scenarios. So that the comparison is fair, I wrote most of the code in C# first, and manually ported it, line-by-line, to C++, replacing standard .NET classes with STL equivalents. Because this is labor-intensive, however, the variety and scope of the benchmarks are limited.
To compile both languages I used Visual Studio 2008; I have access to Visual Studio 2010, but Microsoft dropped support for Windows CE in VS 2010 so it was easier to keep using 2008. I welcome readers to try compiling the C++ code on GCC (there is a small amount of Windows-specific code you may have to deal with) or VS 2010 to see if it performs differently. Of course, any differences you observe may be caused by using a different processor as well as a different compiler. Likewise, if someone has access to Windows Phone 7, I welcome you to run the C# benchmark there and see if you get better results than I did for Windows CE.
My test workstation is a Quad-core 64-bit Intel Q9500 @ 2.83 GHz (but all tests are single-threaded) on Windows 7. The mobile device is a Mentor Ranger 4 with a 600MHz ARM processor, and .NET Compact Framework 3.5.
Read more: Codeproject
Freakonomics [Revised and Expanded]: A Rogue Economist Explores the Hidden Side of Everything [Hardcover]
Posted by
jasper22
at
17:30
|
Welcome to FREAKONOMICS
Steven D. Levitt is an economist. Stephen J. Dubner is a writer. They co-authored Freakonomics, a book about cheating teachers, bizarre baby names, self-dealing Realtors, and crack-selling mama’s boys. They figured it would sell about 80 copies. Instead, it has sold 4 million, in 35 languages. Then they wrote SuperFreakonomics. It also became a worldwide best-seller. A lot of other stuff happened, too. A blog. A movie. A radio show. Jon Stewart and Beauty and the Geek. A pair of pants! Now, at long last, all things Freakonomics are here in one place. Welcome to the new Freakonomics.com.
Read more: FREAKONOMICS

In Stock.
Ships from and sold by Amazon.com. Gift-wrap available.
Want it delivered Tuesday, June 21? Order it in the next 9 hours and 3 minutes, and choose One-Day Shipping at checkout. Details
Read more: Amazon
Following the Money In Cybercrime
Posted by
jasper22
at
17:23
|
Five dollars for control over 1,000 compromised email accounts. Eight dollars for a distributed denial-of-service attack that takes down a website for an hour. And just a buck to solve 1,000 captchas. Those are the going rates of cybercrime, the amounts criminals pay other criminals for the technical services necessary to launch attacks. This criminal underground was detailed Wednesday in a highly entertaining talk given by researcher Stefan Savage at the annual Usenix technical conference in Portland, Ore. Savage's research into the economics of cybercrime began as lip service to satisfy the terms of a government grant, but it turned out to be the key to stopping computer attacks. Targeted methods — such as using CAPTCHAs — don't stop criminals, but they add to the cost burden and put the inefficient criminal organizations out of business, letting security researchers focus only on the ones that survive.
Read more: Slashdot
How to Delete Your Facebook Account
Posted by
jasper22
at
16:24
|

Deleting your Facebook account might appear to be simple, but thanks to several safeguards you have to do quite a bit more than hit the delete button and say goodbye. If you want out, here's a guide to braving the arduous road ahead.
Note: This post isn't anti-Facebook. We're not trying to convince you one way or the other. If you want to delete your account—perhaps because you want out or maybe you just want to start fresh—we'll show you what you need to do to make it happen.
The deletion process is actually very easy, but it needs to be very thorough and it'll take 14 days to be official. If you're ready to say goodbye to your Facebook account, just follow these steps:
- Think of any and all sites that you log into using Facebook connect. That means any site that is not Facebook itself but lets you log in using the same username and password as you do for Facebook. Once you know every one of the sites on this list, go to each of them and close your accounts. If you log in to any of those sites during the cancellation period (which lasts two weeks) your account will be instantly reinstated and you'll have to start over again. You can always recreate the accounts later.
- Visit the Facebook Account Deletion Page. If you're asked to log in, go ahead and do so. When you see the page called "Delete My Account" with two buttons, click the one labeled "Submit."
Read more: Lifehacker
How to index your Silverlight application in search engine
Posted by
jasper22
at
15:18
|
Read the following if:
you have a Silverlight application with many internal pages
you want search engine to index your Silverlight content
you want to manage Silverlight content for search engine and reader effectively
There isn’t too many particles articles in the web talking about Silverlight SEO. Therefore, I would like to share my seo optimization knowledge with all of you.
To start with, I would like to prove that my concept is practical. One of my application Silverlight Resources Directory, which has a lot of internal pages, is now indexed with Search Engine with most of the pages. Here are the links results from Goolge, Bing and Yahoo:
Link Results from Google
Link Results from Bing
Link Results from Yahoo
For your reference, the application just launched less than 10 days and it is now receiving more than 30 search queries everyday.
Create a SEO Application together
To better demonstrating the Silverlight SEO techniques, I will attempt to create another new application with a new sub-domain to keep track the performance. If you are interested in it, I hope you could follow my articles and create you own Silverlight application for testing as well.
The detailed steps are as follow:
- Create a simple Silverlight Application
I will utilize the navigation framework in Silverlight 3 to create a simple application with numerous pages.
- Setup a PHP/ASP to host the Silverlight application
Your web server must be able to support either PHP or ASP. The server side script will be responsible for detecting who (Search Engine or Human) is viewing the page.
If it is search engine, we will display a html page corresponding to the Silverlight Application.
Read more: Shine Draw
Subscribe to:
Comments (Atom)




