Openwall GNU/*/Linux
Hi,I am pleased to announce that we have made a new major release of Openwall GNU/*/Linux, version 3.0. ISO images of the CDs for i686 and x86-64 are available for download via direct links from: http://www.openwall.com/Owl/The ISOs include a live system, installable packages, the installer program, as well as full source code and the build environment. The download size is under 450 MB (for one CPU architecture). Additional components, such as OpenVZ container templates, are available from the appropriate directories on the mirrors:http://www.openwall.com/Owl/DOWNLOAD.shtml Openwall GNU/*/Linux (or Owl for short) is a small security-enhanced Linux distribution for servers, appliances, and virtual appliances. Owl live CDs with remote SSH access are also good for recovering or installing systems (whether with Owl or not). Another secondary use is for operating systems and/or computer security courses, which benefit from the simple structure of Owl and from our inclusion of the complete build environment. This release marks roughly 10 years of our project - development started in mid-2000, and Owl 0.1-prerelease was made public in 2001. Curiously, most other "secure" Linux distros that appeared at about the same time are no longer around. (EnGarde Secure Linux appears to be the only exception, but it is completely different both in approach to security and in functionality.) Read more: Openwall GNU/*/Linux
#Hindsight2010: The Year’s Most Retweeted Tweets
In this edition of #Hindsight2010, we reveal the 10 Most Retweeted Tweets of the year. American TV personality Stephen Colbert (@StephenAtHome) tops the list with a wry Tweet about the Gulf Oil Spill, the year’s biggest Trend on Twitter. To commemorate the honor, Twitter is awarding Colbert --the titan of ‘Truthiness’-- the first-ever Golden Tweet award for the year’s Most Retweeted Tweet. Twitter co-founder Biz Stone personally presented Colbert with the award tonight on The Colbert Report. Musicians dominated 2010's Most Retweeted Tweets list: Drizzy Drake (@drakkardnoir) took the #2 spot, and Lil Wayne (@liltunechi) came in at #3. Fascination with Justin Bieber (@justinbieber) is still raging: he placed fourth, while pop stars Joe Jonas (@joejonas) and Rihanna (@rihanna) made the list at #6 and #9 with their Bieber-related Tweets. Congrats also go to Lady Gaga (@ladygaga) (#7) and Kanye West (@kanyewest) (#8). Read more: Twitter blog
Epic Google Docs Animation
Posted by
jasper22
at
15:36
|
Amazing use of Google Docs to create this animated presentation. [Ed. note: LOL at “Let's rock the Google docs!” Google is so awesome and so incredibly dorky all at the same time.]Read more: Youtube
Google declares Chrome ready for enterprise duty
Posted by
jasper22
at
15:32
|

IT administrators tend to be a fickle bunch, and with good reason. When you're supporting a vital service that can determine whether or not your entire business can operate properly, you tend to be very cautious when it comes to changing out a key component. A key component like a Web browser, for example -- say, Internet Explorer 6, which is still a force to be reckoned with in the enterprise. Google has been doing its best to get Chrome in the front door, of course. First there was Chrome Frame, which seamlessly integrates into Internet Explorer to provide a hybridized, modern Frankenbrowser. Next came Chrome's remoting feature -- which is still not ready for prime time but is positioning itself as an alternative to Terminal Services setups. Read more: DownloadSquad
Gmail Creator Says Chrome OS Is As Good As Dead
Posted by
jasper22
at
15:31
|
Former Google employee, Gmail creator, and FriendFeed founder Paul Buchheit has come right out and said what many people are thinking (or hoping for). On his FriendFeed page, Buchheit made a post titled 'Prediction: ChromeOS will be killed next year (or "merged" with Android).' In it, he bluntly says that Google's netbook-centric Chrome OS is as good as dead. 'Yeah, I was thinking, "is this too obvious to even state?", but then I see people taking ChromeOS seriously, and Google is even shipping devices for some reason,' Buchheit writes. 'Because ChromeOS has no purpose that isn't better served by Android (perhaps with a few mods to support a non-touch display) Read more: Slashdot
Official open source driver for Kinect
Posted by
jasper22
at
14:05
|
R&D company PrimeSense, the company responsible for the technology behind Microsoft's Kinect camera system, has, in conjunction with Willow Garage and Side-Kick, released official Windows and Linux (Ubuntu version 10.10 and later) open source drivers for Kinect. What was previously the work of several independent programmers has now been given the vendor's official seal of approval. Microsoft also now seems to have recognised the innate potential of amateur programmers in developing new ideas for using the Kinect for gesture control and is now actively supporting them. Read more: The H Open
BitTorrent Client Offers P2P Without Central Tracking
While BitTorrent is the most popular P2P protocol, it still relies on several centralized points for users to find the files they are looking. There have been several attempts at making BitTorrent more decentralized, and the latest Tribler 5.3 client is the first to offer the BitTorrent experience without requiring central trackers or search engines. Tribler offers some very interesting technologies; the latest version enables users to search and download files from inside the client. Plenty of other clients offer search features, including the ever-popular Torrent, but Tribler's results come from other peers rather than from a dedicated search engine. Users can search and download content without a server ever getting involved; everything is done among peers, without the need of a BitTorrent tracker or search indexer. Read more: Slashdot
Chrome OS Doesn't Trust Apps Or Users
Posted by
jasper22
at
16:59
|
Google's Chrome OS chiefs explain in Technology Review how most of the web-only OS's features flow from changing one core assumption of previous operating system designs. 'Operating systems today are centered on the idea that applications can be trusted to modify the system, and that users can be trusted to install applications that are trustworthy,' says Google VP Sundar Pichai. Chrome doesn't trust applications, or users — and neither can modify the system. Once users are banned from installing applications, or modifying the system security, usability, and more are improved, the Googlers claim Read more: Slashdot
SHA-3 Finalist Candidates Known
Posted by
jasper22
at
16:59
|
NIST just announced the final selection of algorithms in the SHA-3 hash competition. The algorithms that are candidates to replace SHA-2 are BLAKE, Grøstl, JH, Keccak and Skein. The selection criteria included performance in software and hardware, hardware implementation size, best known attacks and being different enough from the other candidates. Curiously, some of the faster algorithms were eliminated as they were felt to be 'too fast to be true.' A full report with the (non-)selection rationale for each candidate is forthcoming Read more: Slashdot
Project Aiko
Posted by
jasper22
at
16:19
|

Welcome to Project Aiko Video & Picture Gallery
Want to have your company logo on Aiko! Have Aiko wears the clothes you designed or sale.
Great Exposure!!!Restriction:
Can NOT be blue jean. (Doesn't go well with silicone, it will leave blue mark) Aiko size: Height: 152cm Bust: 82cm Waist: 57cm Hip: 84cmRead more: Project Aiko
Michael Moore Posts Julian Assange's Bail
Posted by
jasper22
at
11:53
|
Yesterday, in the Westminster Magistrates Court in London, the lawyers for WikiLeaks co-founder Julian Assange presented to the judge a document from me stating that I have put up $20,000 of my own money to help bail Mr. Assange out of jail. Furthermore, I (Michael Moore) am publicly offering the assistance of my website, my servers, my domain names and anything else I can do to keep WikiLeaks alive and thriving as it continues its work to expose the crimes that were concocted in secret and carried out in our name and with our tax dollars. Read more: Slashdot
FBI Alleged To Have Backdoored OpenBSD's IPSEC
Posted by
jasper22
at
11:52
|
Aggrajag and Mortimer.CA, among others, wrote to inform us that Theo de Raadt has made public an email sent to him by Gregory Perry, who worked on the OpenBSD crypto framework a decade ago. The claim is that the FBI paid contractors to insert backdoors into OpenBSD's IPSEC stack. Mr. Perry is coming forward now that his NDA with the FBI has expired. The code was originally added ten years ago, and over that time has changed quite a bit, "so it is unclear what the true impact of these allegations are" says Mr. de Raadt. He added: "Since we had the first IPSEC stack available for free, large parts of the code are now found in many other projects/products." (Freeswan and Openswan are not based on this code.) Read more: Slashdot
How to boot Ubuntu on the Cr-48 Chrome OS netbook
Posted by
jasper22
at
11:52
|
It was only a matter of time: a page on the Chromium Projects website has emerged, detailing how to install Ubuntu on a Cr-48 netbook. The process is, understandably, a little risky -- but it's not like there are any tech bloggers out there that don't know how to use Linux, right? Snarkiness aside, the process is actually very easy. You have to hack at the SSD's filesystem a little and fiddle with the Chrome OS kernel, but if you do everything right, you should be rewarded with a dual-boot system capable of running both Ubuntu and Chrome OS. The best bit, though, is that you have to enable 'developer mode' to escape Chrome OS's 'verified boot' security measure. To do this, you need to flip a switch on the back, under the battery, as per the hilarious instructional photo shown after the break. Read more: DownloadSquad
You're deploying it wrong! TeamCity, Subversion & Web Deploy part 4: Continuous builds with TeamCity
Posted by
jasper22
at
10:57
|
Over the last three posts in this series, we got to the point where all the Microsoft bits are working really nicely together. Config transforms, packaging and Web Deploy are great stable mates in the world of web application deployment. The bit that’s missing though is automation. Actually there are several bits missing but automation is the common solution. Deployment by developers directly from Visual Studio or command line with MSDeploy works fine most of the time but has a few flaws we’re simply not going to be able to overcome without a build and deployment server. In all likelihood, your existing release process looks something like this: 
The problems with this are numerous:

The problems with this are numerous:
- Access rights – you’re giving the developer too much if they can directly invoke Web Deploy either with their own credentials or other credentials they know. They will bend to temptation and circumvent release procedures, even though it’s normally well intentioned (just had to turn off custom errors for a moment…).
- Auditability – well, you’ve got none. You have no way of automatically capturing when, what and who. You could have a dozen releases in a day and be none the wiser because if it’s not automated, the information is inevitably not recorded or done so poorly.
- Rollback – you know how rollback is most commonly done? Copy the target folder and rename it “old_MyWebApp”, publish the new app then if it breaks, copy the old files back over. I’d bet my bottom dollar that in lieu of a build and deploy environment, this is your rollback strategy. Either that or pulling a previous revision from VCS and repeating a manual deploy which can be both time consuming and error prone.
- Version control – if you’re not deploying directly from your VCS, what confidence do you have that released source code is retrievable or reproducible? You’re (hopefully) not publishing all your source code to the target environment so short of some emergency reverse engineering, a developer could easily release code you’re never going to be able to reproduce.
Announcing Verve – A Type-Safe Operating System
Posted by
jasper22
at
10:56
|
Earlier this week Microsoft Research published a paper and announced the release of Verve, an operating system which grew out of the Singularity project, upon whose base premise is to use Typed Assembly Language, TAL, and Hoare logic to achieve the highest levels of security and safety. The Verve operating system consists of a nucleus, a kernel and one or more applications. While Verve is written in C# for convenient automatic compilation to TAL, a second check is still performed to verify type safety. The Nucleus, itself, is written in assembly language which was hand-annotated with assertions. Boogie is used to verify the assembly language against a specification and guarantees safe interaction with the TAL code and hardware. Verve successes
- The first operating system mechanically verified to ensure type safety including each assembly language instruction that runs after booting which is statically verified.
- Runs on commodity hardware supporting true language features such as classes, virtual methods, arrays and pre-emptive threads.
- Highly efficient through the use of Bartok’s native layouts for objects, method tables and arrays.
- Demonstration of automated techniques, TAL and automated theorem proving, to verify the safety of the complex low-level code in the operating system and run-time.
- Demonstrates that a small amount of code verified with automated theorem proving can support an arbitrary large amount of TAL code.
Code that is verifiably type-safe accesses memory only through object references and associated features such as fields and properties. By accessing memory through well-defined paths, the runtimes or in this case, kernels can verify that code is not accessing memory locations to which it should not have access. Essentially, type safety means that a program cannot perform an operation on an object unless that operation is valid for that object. Type safety provides the most essential element for security in modern programming languages like Java & C# and when extended to the operating system level the result is efficiency which translates into performance. Verve Limitations
Read more: InfoQ
Read more: Singularity Research Development Kit
- Lack of support for many C# features like exception handling
- Does not support the standard .NET class library due to its inclusion of unsafe code
- Lacks dynamics loading of code
- Runs only on a single processor
- Lacks a comprehensive isolation mechanism like Singularity SIPS, Java Isolates and C# AppDomains
- Verve uses verified garbage collectors that are stop-the-world and keeps interrupts disabled throughout the collection.
Read more: InfoQ
Read more: Singularity Research Development Kit
Dynamically Generating Controls in WPF and Silverlight
Posted by
jasper22
at
10:55
|
Some of the Windows Forms developers I've spoken to have said that one thing they want to learn is how to dynamically create controls in WPF and Silverlight. In this post I'll show you several different ways to create controls at runtime using Silverlight 4 and WPF 4. First, we'll start with how to create controls in XAML. From there, we'll move to dynamically-loaded XAML before we take a look at using the CLR object equivalents.
Creating Controls at Design Time in XAMLCreating controls using the design surface and/or XAML editor is definitely the easiest way to create your UI. You can use Expression Blend or Visual Studio, depending upon how creative you want to be. If you want a more dynamic layout, you can hide and show panels at runtime. Here's an example layout: <Grid Margin="10">
<Grid.ColumnDefinitions>
<ColumnDefinition Width="100" />
<ColumnDefinition Width="*" />
</Grid.ColumnDefinitions>
<Grid.RowDefinitions>
<RowDefinition Height="Auto" />
<RowDefinition Height="Auto" />
<RowDefinition Height="Auto" />
<RowDefinition Height="*" />
</Grid.RowDefinitions> <TextBlock Text="First Name"
Height="19"
Margin="0,7,31,4" />
<TextBox x:Name="FirstName"
Margin="3"
Grid.Row="0"
Grid.Column="1" />
<TextBlock Text="Last Name"
Margin="0,7,6,3"
Grid.Row="1"
Height="20" />
<TextBox x:Name="LastName"
Margin="3"
Grid.Row="1"
Grid.Column="1" />
Read more: 10REM.NET
Creating Controls at Design Time in XAMLCreating controls using the design surface and/or XAML editor is definitely the easiest way to create your UI. You can use Expression Blend or Visual Studio, depending upon how creative you want to be. If you want a more dynamic layout, you can hide and show panels at runtime. Here's an example layout: <Grid Margin="10">
<Grid.ColumnDefinitions>
<ColumnDefinition Width="100" />
<ColumnDefinition Width="*" />
</Grid.ColumnDefinitions>
<Grid.RowDefinitions>
<RowDefinition Height="Auto" />
<RowDefinition Height="Auto" />
<RowDefinition Height="Auto" />
<RowDefinition Height="*" />
</Grid.RowDefinitions> <TextBlock Text="First Name"
Height="19"
Margin="0,7,31,4" />
<TextBox x:Name="FirstName"
Margin="3"
Grid.Row="0"
Grid.Column="1" />
<TextBlock Text="Last Name"
Margin="0,7,6,3"
Grid.Row="1"
Height="20" />
<TextBox x:Name="LastName"
Margin="3"
Grid.Row="1"
Grid.Column="1" />
Read more: 10REM.NET
Get Password Expiration Date in SQL Server 2008
Posted by
jasper22
at
10:55
|
SQL Server 2008 introduces a new argument called DaysUntilExpiration in the LOGINPROPERTY function, which returns the number of days until the password expires. You can use this property using the following code: SELECT LOGINPROPERTY('sa', 'DaysUntilExpiration')Note: If you get a null while executing the query, then either the login is not a valid login or your Operating System does not support password policies. You should run this query on a SQL Server box installed on Windows Server 2003 or later. Similarly you can get additional login information using the following query:SELECT name,
create_date,
modify_date,
LOGINPROPERTY(name, 'DaysUntilExpiration') DaysUntilExpiration,
LOGINPROPERTY(name, 'PasswordLastSetTime') PasswordLastSetTime,
LOGINPROPERTY(name, 'IsExpired') IsExpired,
LOGINPROPERTY(name, 'IsMustChange') IsMustChange
From sys.sql_logins ;
Read more: SQL Server Curry
create_date,
modify_date,
LOGINPROPERTY(name, 'DaysUntilExpiration') DaysUntilExpiration,
LOGINPROPERTY(name, 'PasswordLastSetTime') PasswordLastSetTime,
LOGINPROPERTY(name, 'IsExpired') IsExpired,
LOGINPROPERTY(name, 'IsMustChange') IsMustChange
From sys.sql_logins ;
Read more: SQL Server Curry
The @” syntax in Objective-C vs C#
Posted by
jasper22
at
10:53
|
A common mistake that I see in some of the code from our customers, or from contributed samples to the MonoMac repository is the use of the @”string” syntax in C# programs.Summary: do not use the @”…” when porting Objective-C samples to C#. String Syntax in Objective-C and C#Objective-C supports two kinds of string literals in your source code, strings that are surrounded by double-quotes and strings that are prefixed with the at-sign and then double quotes. The first kind are zero-terminated C-style strings. For example the string “foo” is encoded by the compiler as the following four bytes: ‘f’, ‘o’, ‘o’ and zero plus the address of the string at the location where this is referenced. The second kind, for example @”Hello World” is a CoreFoundation string, and the compiler has to encode by creating a static instance of a CoreFoundation CFString object: it has a class identifier, some object flags, a pointer to the data (‘foo’ in this case) and the length of the string. Read more: Miguel's OSX and iOS blog
Working with the Silverlight Rich Text Box control
Posted by
jasper22
at
10:50
|
In this article, we’ll take a look at the Silverlight Rich Text Box control. The Rich Text Box was one of the new, and highly requested controls introduced in Silverlight 4.This article is accompanied by a Visual Studio solution, which you can find here. What do we get?
Out of the box, the Rich Text Box control looks like a simple TextBox: you get the typical TextBox look, nothing more. However, under the covers, it offers us the ability to display formatted text, paragraphs, hyperlinks or inline images – and even more than that: you can actually use the Rich Text Box to display any UIElement (so if you want a DataGrid in your Rich Text Box, that’s entirely possible). The Rich Text Box has a content property, Blocks, which is a collection of Paragraph elements (Paragraph derives from Block). These Paragraph elements can in turn contain elements that are derived from Inline, like Run (we know that one from the regular Text Box), Span, Bold, Italic, Underline, Hyperlink and the InlineUIContainer (which can contain UIElements). This image (from MSDN) offers an overview of the content model:
Out of the box, the Rich Text Box control looks like a simple TextBox: you get the typical TextBox look, nothing more. However, under the covers, it offers us the ability to display formatted text, paragraphs, hyperlinks or inline images – and even more than that: you can actually use the Rich Text Box to display any UIElement (so if you want a DataGrid in your Rich Text Box, that’s entirely possible). The Rich Text Box has a content property, Blocks, which is a collection of Paragraph elements (Paragraph derives from Block). These Paragraph elements can in turn contain elements that are derived from Inline, like Run (we know that one from the regular Text Box), Span, Bold, Italic, Underline, Hyperlink and the InlineUIContainer (which can contain UIElements). This image (from MSDN) offers an overview of the content model:
Silverlight basics. Validation
Posted by
jasper22
at
10:45
|
Introduction Silverlight 4 has some new ways for validate input values (some new approaches to implement validation in your application). First approach is DataAnnotation. In this case you should describe validation rules with attributes. Two other ways (both of them is came with Silverlight 4) – you should implement one of interfaces for your ViewModel: IDataErrorInfo or INotifyDataErrorInfo. I want to talk about all of these approaches, about pros and cons of using each of them. Goal of this article to get a best way to implement validation of input values in my and your applications. Read more: Codeproject
Xaml Code Behind Generator
Posted by
jasper22
at
10:43
|
Project Description
Xaml Code Behind Generator makes it easier to generate Code Behind designer code from XAML, where code can be used at places where Xaml Services are not accessible.Features
Read more: Codeplex
Xaml Code Behind Generator makes it easier to generate Code Behind designer code from XAML, where code can be used at places where Xaml Services are not accessible.Features
- Using XAML 2009 in Silverlight and WPF
- Reusing Xaml Business Pages in Silverlight and WPF
- Support for User Controls derived from any Control
- Using Complied code instead of BAML
- Improving speed of XAML runtime
- Using XAML to generate code to be used in ASP.NET, Server Core etc, where XAML Services are not available
- Generated code is pure .NET 2.0 compliant, and you can target xaml objects to run in earlier .NET version too.
- You can also create Xaml for WinForms and use it for your .NET 2.0 projects, however please notice, the features of WPF will not be available, it can only create object hierarchies based on XAML, but it can not give you binding etc features.
- x:Name support for Resources, very useful for MVVM Pattern
- Support for Custom Extension with Custom Code Generator
Read more: Codeplex
TechNet Magazine: October 2010 Issue–Lots of Cloud Security..
Posted by
jasper22
at
10:43
|
Yes I know I’m a bit late with this but hey I’m busy. You guys all know that. I thought it was worth sharing this anyway as there is quite a bit of Security related information and Cloud Security as well. Anyway I’m sharing this with you because I think it’s relevant so have a look if you want or not. It’s up to you. Check out the October edition of TechNet Magazine. Later dudes..
Python’s Innards: Introduction
Posted by
jasper22
at
10:42
|
A friend once said to me: You know, to some people, C is just a bunch of macros that expand to assembly. It’s been years ago (smartasses: it was also before llvm, ok?), but the sentence stuck with me. Do Kernighan and Ritchie really look at a C program and see assembly code? Does Tim Berners-Lee surf the Web any differently than you and me? And what on earth did Keanu Reeves see when he looked at all of that funky green gibberish soup, anyway? No, seriously, what the heck did he see there?! Uhm, back to the program. Anyway, what does Python look like in Guido van Rossum‘s1 eyes? This post marks the beginning of what should develop to a series on Python’s internals, I’m writing it since I believe that explaining something is the best way to grok it, and I’d very much like to be able to visualize more of Python’s ‘funky green gibberish soup’ as I read Python code. On the curriculum is mainly CPython, mainly py3k, mainly bytecode evaluation (I’m not a big compilation fan) – but practically everything around executing Python and Python-like code (Unladen Swallow, Jython, Cython, etc) might turn out to be fair game in this series. For the sake of brevity and my sanity, when I say Python, I mean CPython unless noted otherwise. I also assume a POSIX-like OS or (if and where it matters) Linux, unless otherwise noted. You should read this if you want to know how Python works. You should read this if you want to contribute to CPython. You should read this to find all the mistakes I’ll make and snicker at me behind me back or write snide comments. I realize it’s just your particular way to show affection. I gather I’ll glean pretty much everything I write about from Python’s source or, occasionally, other fine materials (documentation, especially this and that, certain PyCon lectures, searching python-dev, etc). Everything is out there, but I do hope my efforts at putting it all in one place to which you can RSS-subscribe will make your journey easier. I assume the reader knows some C, some OS theory, a bit less than some assembly (any architecture), a bit more than some Python and has reasonable UNIX fitness (i.e., feels comfortable installing something from source). Don’t be afraid if you’re not reasonably conversant in one (or more) of these, but I can’t promise smooth sailing, either. Also, if you don’t have a working toolchain to do Python development, maybe you’d like to head over here and do as it says on the second paragraph (and onwards, as relevant). Read more: NIL: .to write(1) ~ help:about
IE December Cumulative Security Update Now Available
Posted by
jasper22
at
10:41
|
The IE Cumulative Security Update for December 2010 is now available via Windows Update. This security update resolves four privately reported vulnerabilities and three publicly disclosed vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. This security update is rated Critical for Internet Explorer 6, Internet Explorer 7, and Internet Explorer 8. For more information about the vulnerabilities, please see the full bulletin.The security update addresses the vulnerabilities by modifying the way that Internet Explorer handles objects in memory and script during certain processes. For more information about the vulnerabilities, see the Frequently Asked Questions (FAQ) subsection for the specific vulnerability entry under the next section, Vulnerability Information. This security update also addresses the vulnerability first described in Microsoft Security Advisory 2458511.The majority of customers have automatic updating enabled and will not need to take any action because this security update will be downloaded and installed automatically. Customers who have not enabled automatic updating need to check for updates and install this update manually. For information about specific configuration options in automatic updating, see Microsoft Knowledge Base Article 294871. Read more: IEBlog
Fix a corrupted user profile
Posted by
jasper22
at
10:40
|
If you tried to log on to Windows and received an error message telling you that your user profile might be corrupted, you can try to repair it. You will need to create a new profile, and then copy the files from the existing profile to the new one. Before you create a new profileOccasionally, Windows might not read your user profile correctly—for example, if your antivirus software is scanning your computer while you try to log on. Before you create a new user profile, try restarting your computer and logging on with your user account again. To create a new user profileTo create a new profile, you must first create a new user account. When the account is created, a profile will also be created.
Read more: Windows
- Open User Accounts by clicking the Start button , clicking Control Panel, clicking User Accounts and Family Safety (or clicking User Accounts, if you are connected to a network domain), and then clicking User Accounts.
- Click Manage another account. If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
- Click Create a new account.
- Type the name you want to give the user account, click an account type, and then click Create Account.
Read more: Windows
Gtk# designer on OSX
Posted by
jasper22
at
10:40
|
Happy to see that Gtk+ and Gtk# on MacOS are complete enough that the MonoDevelop GUI designer can be used there to build UIs.In the past, we had to use Linux to do all of our GUI design. Now our Gtk+ GUI design on OSX is self-hosting: 

Providing an Alternating Background Color for an ItemsControl
Posted by
jasper22
at
10:39
|
Often something you want to do is provide an alternating background color with a list of data. The challenge is that this option is not built into any of the controls, such as an ItemsControl or a ListBox. You can go as far as extending either of these controls, though the easiest way I’ve found to accomplish this is to use a converter.
Creating A Multiple Column Header Within DataGridView
Posted by
jasper22
at
10:39
|
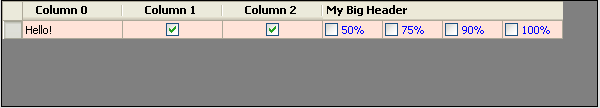
Rectangle hcRct = grid1.GetCellDisplayRectangle(hc.ColumnIndex, -1, true); The first line of code should be self-explanatory. In the second line, we're getting a Rectangle object based on the cell in question. Passing the column index and the row index ("-1" means the row header) to the DataGridView's GetCellDisplayRectangle() method gets us there. Next, we'll use that Rectangle object to get another Rectangle that represents the entire area to be covered by our new Multi-Column-Header. We can do that like so: int multiHeaderWidth = grid1.Columns[hc.ColumnIndex].Width + grid1.Columns[hc.ColumnIndex + 1].Width + grid1.Columns[hc.ColumnIndex + 2].Width + grid1.Columns[hc.ColumnIndex + 3].Width; Rectangle headRct = new Rectangle(hcRct.Left, hc.ContentBounds.Y + 2, multiHeaderWidth, grid1.ColumnHeadersHeight);
headRct.Height -= 3; As you can see, the first line above simply gets the total width of all four columns to be spanned. We then pass that variable along with the other three coordinates (left, top, and height) required to instantiate a Rectangle object. (We add 2 to the Y coordinate and subtract 3 from the Rectangle's height in the next line to create a margin, so that our header cell's top and bottom borders are still visible.)
Next we need to find the size our string will be based on its length and the font we'll be using: SizeF sz = e.Graphics.MeasureString("My Big Header", grid1.Font); Then we figure out where the top will need to be in order to make it vertically centered: int headerTop = Convert.ToInt32((headRct.Height / 2) - (sz.Height / 2)) + 2; Then we set the background color to match the grid's header color: e.Graphics.FillRectangle(new SolidBrush(SystemColors.Control), headRct); And finally, we draw the text, starting 2 pixels to the right of the left-most point of our rectangle so it looks nice: e.Graphics.DrawString("My Big Header", grid1.ColumnHeadersDefaultCellStyle.Font, Brushes.Black, hcRct.Left + 2, headerTop); Read more: C# Corner
wxPython Documentation
Posted by
jasper22
at
10:38
|
When I originally started this blog, it was mostly a brain dump on my part so I wouldn’t forget how I did something cool with Python. Later on, I decided to use it to also document what I considered under-documented portions of wxPython. If my posts drew enough interest, I would also re-work the post into a wiki page on the wxPython wiki. Thus, if you ever have trouble finding documentation on some part of wxPython, you can drop me a line and I might write something up. But before you do that, be sure to check out the following resources first: The wxPython wiki
Official wxPython online documentation and API man pages
The wxPython tome: wxPython in Action by Robin Dunn
The wxPython Docs and Demo package
The zetcode wxPython tutorial
The Advanced Generic Widgets (AGW) widget documentation
Andrea Gavana’s alternate wxPython documentationRead more: The Mouse Vs. The Python
Official wxPython online documentation and API man pages
The wxPython tome: wxPython in Action by Robin Dunn
The wxPython Docs and Demo package
The zetcode wxPython tutorial
The Advanced Generic Widgets (AGW) widget documentation
Andrea Gavana’s alternate wxPython documentationRead more: The Mouse Vs. The Python
SQLCLR vs. T-SQL - Performance Comparison
Posted by
jasper22
at
10:38
|
Before comparing the performance of SQLCLR and TSQL, just have a quick look at the definition of SQLCLR. SQLCLR is the Microsoft name for the integration of CLR as a hosted runtime within SQL SERVER. It enables the execution of managed code inside the database. Simple SQLCLR Architecture
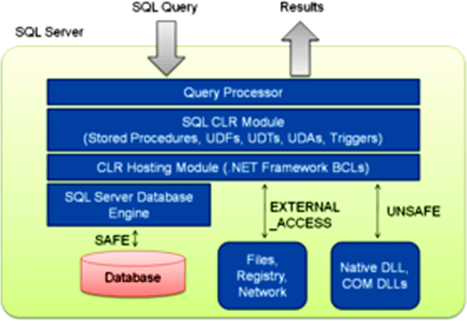
T-SQL is nothing but the Transact SQL which is the native language supported by SQL SERVER. CLR supported in SQL Server provides an alternative to the procedural approach in T-SQL.Now the question comes, when to choose SQLCLR and when to choose T-SQL for the procedural approach. We can't blindly decide, because each approach has strengths and weaknesses. So the decision should be made judiciously. Thumb Rule
Read more: C# Corner

T-SQL is nothing but the Transact SQL which is the native language supported by SQL SERVER. CLR supported in SQL Server provides an alternative to the procedural approach in T-SQL.Now the question comes, when to choose SQLCLR and when to choose T-SQL for the procedural approach. We can't blindly decide, because each approach has strengths and weaknesses. So the decision should be made judiciously. Thumb Rule
- If your logic mostly involves just the transformation of a large number of data, which can be easily performed by the declarative syntax of SQL, in that case T-SQL is preferred.
- If your logic mostly involves the complex calculation on a row basis with a small amount of data, SQLCLR is preferred.
- From the above Thumb rule, another question may arise as below.
- I have a large number of data and the complex calculations are done on the row basis, in that case which I should prefer?
It again depends on what you are going to do with the large number of data. Here we can't follow the thumb role. You need to test it with both the methods of large and small amount of data. A few inbuilt functions in SQL Server performs faster than in CLR functions and sometimes vice versa.
Read more: C# Corner
Kinect "Minority Report"
Posted by
jasper22
at
10:25
|
This is a graphical interface inspired by the movie "Minority Report". It uses the Kinect sensor from Microsoft, and the recently released libfreenect driver for interfacing with the Kinect in linux. The
graphical interface and the hand detection software were written at MIT to interface with the open source robotics package 'ROS', developed by Willow Garage (willowgarage.com). The hand detection software showcases the abilities of the Point Cloud Library (PCL), a part of ROS that MIT has been helping to optimize. The hand detection software is able to distinguish hands and
fingers in a cloud of more than 60,000 points at 30 frames per second, allowing natural, real time interaction.Code available at:
http://www.ros.org/wiki/kinect
http://www.ros.org/wiki/mit-ros-pkg
Read more: Youtube
graphical interface and the hand detection software were written at MIT to interface with the open source robotics package 'ROS', developed by Willow Garage (willowgarage.com). The hand detection software showcases the abilities of the Point Cloud Library (PCL), a part of ROS that MIT has been helping to optimize. The hand detection software is able to distinguish hands and
fingers in a cloud of more than 60,000 points at 30 frames per second, allowing natural, real time interaction.Code available at:
http://www.ros.org/wiki/kinect
http://www.ros.org/wiki/mit-ros-pkg
Read more: Youtube
6 Linux Commands to Make Life Easier
Posted by
jasper22
at
10:24
|
Man
Man is the Manual Page, and holds all the instructions for all the various commands and how to control them. Personally I often find I can’t remember the correct usage for different programs so I use the man page quite frequently. The first part of the output is the most useful, it shows how to use a command and gives an overview of what it does. Grep
Grep looks for strings or regular expressions in files. You can ask it to look for more or less any pattern in more or less any type of file, including into directories. It’s like “Find in Files”, but better. I mostly use it to check where a function is used before I delete/rename it, or to check what functions are in a given class. Trivia: Grep is not actually a word in its own right, in fact it stands for “global / regular expression / print”. I’ve been using this command for years and thinking it was a word in its own right!Read more: The new think vitamin
Man is the Manual Page, and holds all the instructions for all the various commands and how to control them. Personally I often find I can’t remember the correct usage for different programs so I use the man page quite frequently. The first part of the output is the most useful, it shows how to use a command and gives an overview of what it does. Grep
Grep looks for strings or regular expressions in files. You can ask it to look for more or less any pattern in more or less any type of file, including into directories. It’s like “Find in Files”, but better. I mostly use it to check where a function is used before I delete/rename it, or to check what functions are in a given class. Trivia: Grep is not actually a word in its own right, in fact it stands for “global / regular expression / print”. I’ve been using this command for years and thinking it was a word in its own right!Read more: The new think vitamin
Linux: 25+ Ways to Get System Information
Posted by
jasper22
at
10:19
|
There are a whole bunch of Linux commands to various things on our PC. Normally, we use only a handful of commands without knowing that there are many to be discovered, yet useful. Here’s a comprehensive list of Linux commands that you can use to get system information ranging from printing the current working directory to dumping kernel messages to avail many useful information. How to run these commands?
All you have to do is, just open up a terminal and enter these commands. In order to open up a terminal, you can either go to Applications→Accessories→Terminal or you can simply press Alt+F2 and type gnome-terminal.
All you have to do is, just open up a terminal and enter these commands. In order to open up a terminal, you can either go to Applications→Accessories→Terminal or you can simply press Alt+F2 and type gnome-terminal.
About the Scope
Well, this article is intended for those who love using Linux with experience levels of newbie and average. Not for the so called “Advanced Users”. Otherwise we’ll have to make a never-ending list of commands.
Well, this article is intended for those who love using Linux with experience levels of newbie and average. Not for the so called “Advanced Users”. Otherwise we’ll have to make a never-ending list of commands.
The Command List
pwd
Prints the current working directory (Print Working Directory)
Prints the current working directory (Print Working Directory)
hostname
Print the name of the local host (the machine on which you are working). If you want to change the name of the machine, Use netconf (as root).
Print the name of the local host (the machine on which you are working). If you want to change the name of the machine, Use netconf (as root).
id username
Print user id (uid) and his/her group id (gid), effective id (if different than the real id) and the supplementary groups.
Print user id (uid) and his/her group id (gid), effective id (if different than the real id) and the supplementary groups.
whoami
Prints your login name.
Prints your login name.
date
Print or change the operating system date and time. If you want to change the date and time to 2010-12-31 23:57 using this command:
Print or change the operating system date and time. If you want to change the date and time to 2010-12-31 23:57 using this command:
date 123123572010
To set the hardware (BIOS) clock from the system (Linux) clock, use the command (as root) setclock
To set the hardware (BIOS) clock from the system (Linux) clock, use the command (as root) setclock
who
Determine the users logged on the machine.
Determine the users logged on the machine.
rwho -a
(remote who) Determine all users logged on your network. The rwho service must be enabled for this command to run. If it isn’t, install “rwho”. Read more: Tech Hamlet
(remote who) Determine all users logged on your network. The rwho service must be enabled for this command to run. If it isn’t, install “rwho”. Read more: Tech Hamlet
Boron
Posted by
jasper22
at
10:19
|
Boron is a scripting language similar to REBOL. The interpreter is a C library which may be copied under the terms of the LGPLv3.Read more: Boron
December 2010 Security Release ISO Image
Posted by
jasper22
at
10:18
|
This DVD5 ISO image file contains the security updates for Windows released on Windows Update on December 14th, 2010.Read more: MS Download
Gawker Media Websites Hacked, Staff and User Passwords Leaked
Gawker Media, the blog powerhouse built by Nick Denton, has been hacked.After bringing the company’s websites to a standstill Sunday, one or more hackers operating under the name Gnosis released a 500-MB file apparently containing Gawker’s source code, commenter and staff passwords, and internal conversations between the company’s employees. The e-mail addresses and passwords of hundreds of thousands of Gawker users have been compromised, the hackers said.It’s the worst security breach in New York-based Gawker’s eight-year history, and a wake-up call to all web publishers. (Click here to access your Wired.com profile if you feel the need to change your password for this website.) “We’re deeply embarrassed by this breach,” Gawker said in a blog post Sunday afternoon.The attack included Gawker’s eponymous flagship property, as well as gadget site Gizmodo and the culture site Jezebel. The successful Gawker hack followed a week of escalating attacks in the wake of Wikileaks’s continued release of U.S. State Dept. documents and counter-attacks by hackers associated with a group known as Anonymous, which has staged a pro-Wikileaks campaign called Operation Payback. Read more: Wired
Ex-Wikileaks Folks Start Openleaks, The Next-Generation Of Leaking
Posted by
jasper22
at
14:50
|
That certainly didn’t take long. The former number two at Wikileaks, Daniel Domscheit-Berg, has said that he will launch the next-generation of leaking software (I guess you’d call it software) in the “coming months.” It’s to be called Openleaks, and it will try to fix some of the problems associated with the Wikileaks model, namely centralization. Read more: Techcrunch
Stunts, Idiocy, and Hero Hacks
Posted by
jasper22
at
14:21
|
InfoWorld's Paul Venezia serves up six real-world tales of IT stunts and solutions that required a touch of inspired insanity to pull off, proving once again that knowing when to throw out the manual and do something borderline irresponsible is essential to day-to-day IT work. 'It could be server on the brink of shutting down all operations, a hard drive that won't power up vital data, or a disgruntled ex-employee who's hidden vital system passwords on the network. Just when all seems lost, it's time to get creative and don your IT daredevil cap, then fire up the oven, shove the end of a pencil into the motherboard, or route the whole city network through your laptop to get the job done,' Venezia writes. Read more: Slashdot
IFS Kit - Installable File System Kit
Posted by
jasper22
at
11:59
|
This is the home page for the Installable File System (IFS) Kit, a developer's kit for the kernel mode file system and file system filter driver models. This kit provides the interfaces for developers to write file systems and file system filters for Windows 2000 and later versions of the operating system. The IFS Kit is distributed as part of the Windows Driver Kit (WDK).Read more: Windows WDK and Developer Tools
GUI для питона: пишем PageRankChecker
Posted by
jasper22
at
11:00
|
Вопрос на засыпку: что объединяет все мои предыдущие статьи по программированию, за исключением того что они посвящены питону? Правильно: все разобранные примеры написаны для консоли. Попробую разнообразить тематику статей – разберем написание программы с графическим интерфейсом. В качестве примера напишем определитель PR (PageRank) сайтов, а то на http://www.prchecker.info/ меня постоянно просят ввести символы с картинки (на http://page-rank.org.ua/ определитель PR вообще продают за 5$). Для питона существует большое количество кроссплатформенных графических библиотек. Основные из них: Tkinter – поставляется вместе с python, wxPython – расширение для wxWidgets (возможно, займет место Tkinter в следующих версия python), PyQt – обертка популярной библиотеки Qt, и другие (PyGtk, PyFLTK, FXpy, PyOpenGL). Для простоты усвоения материала рассмотрим написание программы, которая по адресу сайта будет выводить его PageRank. За основу возьмем библиотеку wxPython, как наиболее перспективную (скачать можно по адресу). В качестве IDE буду использовать BoaConstructor (скачивать по адресу). Read more: Блог им. toly
Understanding pass by value and pass by reference - Python style
Posted by
jasper22
at
10:58
|
Continuing with the Python theme -One of the guys on our Python discussion list wanted to know the difference between pass-by-value and pass-by-reference. Seeing how this same question has been asked a few time previously, I thought I would try and make a blog entry to give a simple explanation to demonstrate how it works. Some languages use pass-by-value, but Python on the other hand uses pass-by-reference. What is the difference you ask?Well pass by value is exactly what it sounds like - you pass the value (a copy of everything in the memory). This is bad when you're passing a 10,000 item list to a function - because you now have *two* 10,000 item lists. It's even worse when you have many times that amount of data. Python, OTOH passes by reference - instead of copying the list, a pointer to the list is passed, so when you see something like this:def do_something(a_list):
a_list[2] = 4mylist = [1,2,3,4]
do_something(mylist) now mylist is: [1,2,4,4].In call-by-value, the value of the arguments are copied into the function. There is no way to modify variables outside of the function since you don't have access to them, only to copies. C uses this, among many others: int a = 5
void func(int b) { b = 6; }
func(a);a == 5; /* evaluates to true, variable outside function scope remains unchanged */The value b, inside the function, contains a copy of a. So when it is
modified, the original a remains unchanged.Read more: Bringing Peace Through Programming
a_list[2] = 4mylist = [1,2,3,4]
do_something(mylist) now mylist is: [1,2,4,4].In call-by-value, the value of the arguments are copied into the function. There is no way to modify variables outside of the function since you don't have access to them, only to copies. C uses this, among many others: int a = 5
void func(int b) { b = 6; }
func(a);a == 5; /* evaluates to true, variable outside function scope remains unchanged */The value b, inside the function, contains a copy of a. So when it is
modified, the original a remains unchanged.Read more: Bringing Peace Through Programming
AppScale
Posted by
jasper22
at
10:41
|
About the Project
AppScale is an open-source implementation of the Google App Engine cloud computing interface. It is being developed by researchers in the UC Santa Barbara RACELab. AppScale enables execution of Google App Engine (GAE) applications on virtualized cluster systems. In particular, AppScale enables users to execute GAE applications using their own clusters with greater scalability and reliability than the GAE SDK provides. Moreover, AppScale executes automatically and transparently over cloud infrastructures such as the Amazon Web Services (AWS) Elastic Compute Cloud (EC2) and Eucalyptus, the open-source implementation of the AWS interfaces.
Our goal with AppScale is to provide a Platform-as-a-Service (PaaS) cloud infrastructure that enables users to deploy, test, debug, measure, and monitor their GAE applications prior to deployment on Google's proprietary resources. In addition, we would also like to facilitate investigation and extension of the PaaS implementation: services, runtime, interoperation with lower-level cloud fabric, etc. Read more: AppScale
AppScale is an open-source implementation of the Google App Engine cloud computing interface. It is being developed by researchers in the UC Santa Barbara RACELab. AppScale enables execution of Google App Engine (GAE) applications on virtualized cluster systems. In particular, AppScale enables users to execute GAE applications using their own clusters with greater scalability and reliability than the GAE SDK provides. Moreover, AppScale executes automatically and transparently over cloud infrastructures such as the Amazon Web Services (AWS) Elastic Compute Cloud (EC2) and Eucalyptus, the open-source implementation of the AWS interfaces.
Our goal with AppScale is to provide a Platform-as-a-Service (PaaS) cloud infrastructure that enables users to deploy, test, debug, measure, and monitor their GAE applications prior to deployment on Google's proprietary resources. In addition, we would also like to facilitate investigation and extension of the PaaS implementation: services, runtime, interoperation with lower-level cloud fabric, etc. Read more: AppScale
How to Read XML file and XML String through SQL Stored Procedure
Posted by
jasper22
at
10:39
|
ObjectiveIn this article I will explain reading XML data from XML String \ XML File through SQL Stored Procedure. Stored Procedure for reading XML File.There is a XML file TestXML.xml which contains following XML data. <DataSet>
<tblEmp>
<name>Vishal</name>
<designation>Developer</designation>l
</tblEmp>
<tblEmp>
<name>Jibin</name>
<designation>System Analyst</designation>l
</tblEmp>
</DataSet>SQL Stored Procedure to read XML FileCREATE PROC [dbo].[USP_READXMLFILE]
AS
/*
EXEC [USP_READXMLFILE]
*/
BEGIN
SET NOCOUNT ON
DECLARE @HANDLE INT
DECLARE @SQUERY VARCHAR(1000)
DECLARE @XMLDOC XML
SET @XMLDOC = (SELECT * FROM OPENROWSET
(BULK 'd:\TestXML.xml', SINGLE_CLOB) AS XMLDATA)
SELECT @XMLDOC
EXEC SP_XML_PREPAREDOCUMENT @HANDLE OUTPUT,@XMLDOC SELECT * FROM OPENXML(@HANDLE, '/XMLData/tblEmp', 2)
WITH (name VARCHAR(50),designation VARCHAR(50)) END
Stored Procedure for reading data from XML String.XML String<DataSet>
<tblEmp>
<name>Vishal</name> Read more: C# Corner
<tblEmp>
<name>Vishal</name>
<designation>Developer</designation>l
</tblEmp>
<tblEmp>
<name>Jibin</name>
<designation>System Analyst</designation>l
</tblEmp>
</DataSet>SQL Stored Procedure to read XML FileCREATE PROC [dbo].[USP_READXMLFILE]
AS
/*
EXEC [USP_READXMLFILE]
*/
BEGIN
SET NOCOUNT ON
DECLARE @HANDLE INT
DECLARE @SQUERY VARCHAR(1000)
DECLARE @XMLDOC XML
SET @XMLDOC = (SELECT * FROM OPENROWSET
(BULK 'd:\TestXML.xml', SINGLE_CLOB) AS XMLDATA)
SELECT @XMLDOC
EXEC SP_XML_PREPAREDOCUMENT @HANDLE OUTPUT,@XMLDOC SELECT * FROM OPENXML(@HANDLE, '/XMLData/tblEmp', 2)
WITH (name VARCHAR(50),designation VARCHAR(50)) END
Stored Procedure for reading data from XML String.XML String<DataSet>
<tblEmp>
<name>Vishal</name> Read more: C# Corner
SQL SEVER – Finding Memory Pressure – External and Internal
Posted by
jasper22
at
10:38
|
Following query will provide details of external and internal memory pressure. It will return the data how much portion in the existing memory is assigned to what kind of memory type.SELECT TYPE, SUM(single_pages_kb) InternalPressure, SUM(multi_pages_kb) ExtermalPressure
FROM sys.dm_os_memory_clerks
GROUP BY TYPE
ORDER BY SUM(single_pages_kb) DESC, SUM(multi_pages_kb) DESC
GOWhat is your method to find memory pressure?Read more: Journey to SQL Authority with Pinal Dave
FROM sys.dm_os_memory_clerks
GROUP BY TYPE
ORDER BY SUM(single_pages_kb) DESC, SUM(multi_pages_kb) DESC
GOWhat is your method to find memory pressure?Read more: Journey to SQL Authority with Pinal Dave
Five Great Linux Command Line Tricks
Posted by
jasper22
at
10:36
|
In one of our previous posts we showed you how to convert any audio/video file in Linux. Here’a a neat trick either you might have already heard of or not. In order to do this it’s essential to have ffmpeg installed on your Linux box. Why bother using a GUI when you can easily get things done with the linux command line? Here’s a detailed tutorial on getting certain things done with the linux command line in just a few seconds!1. Converting Video
2. Burning an ISO to a CD
3. Merging MP3s
4. Resizing Images
5. Cloning a Hard Drive
Read more: Tech Hamlet
If have already installed it, let’s say you want to convert a video called Original.avi to Final.mpgffmpeg -i Original.avi Final.mpg Or you can use it vice-versa.
2. Burning an ISO to a CD
Still opening GUI’s like Brasero or K3B to burn an ISO file to a CD? This will come in handy for you. cdrecord -v speed=8 dev=0,0,0 name_of_iso_file.isoNote: If you are having multiple CD/DVD drivers then you have to substitute the proper value for the “dev=” part by running cdrecord -scanbus
3. Merging MP3s
Well, this command is kind of great because you would never think that you can simply merge two MP3′s with cat command in linux! cat one.mp3 two.mp3 > merged.mp3See, Cat has a huge potential in it :)
4. Resizing Images
Why open up GIMP or Shotwell to resize your images unless you have some cropping to be done with the images? For instance, let’s say we want to resize an image to 300px (width)convert -resize 300 large.jpg small.jpg
5. Cloning a Hard Drive
DD is a very powerful tool when it comes to managing hard disks. Say you have two hard disks want to clone the first hard drive. The command would be dd if=/dev/sda of=/dev/sdcNote: If you aren’t sure about the naming conventions of your hard drives. Just run a sudo fdisk -l and change the value of “if=/dev/sda” appropriately. You can name the resulting clone drive anything. But don’t forget to name it without clashing the current drives.
Read more: Tech Hamlet
Writing Cross-Platform XAML Applications
Posted by
jasper22
at
10:35
|
This week's feature article is written by Colin Eberhardt and tackles the issue of sharing code between Silverlight, WPF and Silverlight for Windows Phone. It’s an issue that often comes up in conversation and it’s great to see Colin describe a practical example and demonstrate it’s quite possible to achieve a good degree of efficiency, and thus cost-saving, with a bit of thought. Over to Colin… “Earlier this year, Microsoft released its latest Smartphone OS, Windows Phone 7 (WP7), with handsets being made available globally by late 2010. Developers now have the opportunity to use their Silverlight skills on the mobile platform as well as the web. Furthermore, Silverlight is a subset of WPF, the latest desktop application development framework, allowing skills transfer from desktop, web to mobile, with development for all three sharing the same languages, tools (Visual Studio and Expression Blend), and frameworks. Cross Platform XAML ApplicationsWhilst the possibility of transferring skills between the three platforms is an exciting prospect in itself, what I think is more interesting is the possibility of sharing the same codebase. Silverlight is a stripped down version of WPF, with a few added extras which relate to the web context it lives within. WP7 uses a further stripped down version of the web-based Silverlight, again with a few extras relating to the mobile platform (touch and gesture support for example). What this means in practical terms is that in order to maximise the shared codebase, you need to target the shared parts of each API as much as possible. Read more: Mike Ormond's Blog
Google Nexus S – the new smartphone from Google
Posted by
jasper22
at
10:32
|
Google has launched Nexus S this December,2010 after launching Nexus One in January same year. It seems pretty good and decent slick piece of hardware from Samsung.
It comes loaded with latest Android OS 2.3 (code named Gingerbread) and powerful 1GHz Cortex A8 (Hummingbird) processor. See more of tech-specs at http://www.google.com/nexus. Specs are impressive, comes with 16GB internal memory and no expansion (which is okey...!)
It's edge to edge with iPhone 4 except display and on-screen keyboard, where it is difficult to beat iPhone 4.Read more: BLOGS@DiGiTSSDiGiTSS
It comes loaded with latest Android OS 2.3 (code named Gingerbread) and powerful 1GHz Cortex A8 (Hummingbird) processor. See more of tech-specs at http://www.google.com/nexus. Specs are impressive, comes with 16GB internal memory and no expansion (which is okey...!)
It's edge to edge with iPhone 4 except display and on-screen keyboard, where it is difficult to beat iPhone 4.Read more: BLOGS@DiGiTSSDiGiTSS
Выборка случайных строк из таблицы
Posted by
jasper22
at
10:30
|
Существует несколько способов случайной выборки строк из таблицы. Сегодня я продемонстрирую два из них:Способ 1: Случайное число строкDECLARE @n int
SET @n=RAND()*10
SELECT TOP (@n) * FROM sysobjects Способ 2: Случайное число строк в случайном порядкеDECLARE @n int
SET @n=RAND()*10
SELECT TOP (@n) * FROM sysobjects
ORDER BY NEWID()Read more: SQL4Enterprise
SET @n=RAND()*10
SELECT TOP (@n) * FROM sysobjects Способ 2: Случайное число строк в случайном порядкеDECLARE @n int
SET @n=RAND()*10
SELECT TOP (@n) * FROM sysobjects
ORDER BY NEWID()Read more: SQL4Enterprise
Creating ASP.NET MVC Multilingual Web Application
Posted by
jasper22
at
10:29
|
Introduction
In this article we are going to see how we can show localized content to your ASP.NET MVC web application.Background
We will see mainly two approaches to resolve this issue.
Using the Code
Before we start with Approach 1, I would like to request you to download the attached source code.Approach 1: Using Static Pages
We can go for this approach only when we have few/limited static localized pages. Read more: Codeproject
In this article we are going to see how we can show localized content to your ASP.NET MVC web application.Background
We will see mainly two approaches to resolve this issue.
Approach 1: Using Static Pages
Approach 2: Using Dynamic page with localized data at runtime
Using the Code
Before we start with Approach 1, I would like to request you to download the attached source code.Approach 1: Using Static Pages
We can go for this approach only when we have few/limited static localized pages. Read more: Codeproject
Another open source library : SFL(Standard Function Library)
Posted by
jasper22
at
10:28
|
Standard Function Library (SFL) consists of many useful functions which we use extensively in day to day programming. It’s a great effort from iMatix to ease a programmer’s life.
Some of the categories you can find in SFL are :
Some of the categories you can find in SFL are :
- Compression, encryption, and encoding
- Datatype conversion and formatting
- Dates, times, and calendars
- Directory and environment access
- User and process groups
- Inverted bitmap indices
- Symbol tables
- Error message files
- Configuration files
- String manipulation and searching
- File access
- Internet socket access
- Internet programming (MIME, CGI)
- SMTP (e-mail) access
- Server (batch) programming
- Program tracing
1. It is portable over a range of operating systems.
MS-Windows (MSVC, Borland, Watcom, gcc)
MS-DOS (MSVC, Borland Turbo-C)OS/2 (EMX)LinuxIBM RS/6000 AIXSun SunOSSun SolarisHP HP/UXDigital UNIXFreeBSDNetBSDSCO OpenServerSCO UnixWareDigital OpenVMS
2. Easy to use APIRead more: Simplest Codings
Best 5 Mysql Gui Tools
Posted by
jasper22
at
10:27
|
Most databases are comprised of two distinct ingredients: the back-end, where the data is kept, and the front-end, a user interface for linking with the data component. This scheme separates the user interface from data layer. It also paves the way for third parties to create applications to interact with the databases.
In this article, I am including some most used Mysql GUI tools.1.Workbench
2.Sequel Pro
3.HeidiSQLRead more: bukisa
In this article, I am including some most used Mysql GUI tools.1.Workbench
This is a free tool developed by Sun Systems/Oracle. Workbench is very useful for Microsoft Windows, Mac OS X and Linux platforms. MySQL Workbench is a visual database design tool that incorporates SQL development, administration, database design, creation and maintenance into a development environment. It is the successor to DBDesigner 4 from fabFORCE.net and it replaces the MySQL GUI Tools Bundle. The current version is 5.2, the earliest version was 5.0.
2.Sequel Pro
It is a product of The Sequel Pro Project. It supports Mac OS platform. Sequel Pro is a open-source application. It is the successor of popular CocoaMySQL Mac database management application.
3.HeidiSQLRead more: bukisa
How the Google Chrome OS Works
Posted by
jasper22
at
10:26
|
The Internet has become a central part of the computer experience. Before the Web caught fire in the late 1990s, home computing was largely a singular experience. Computer users created documents on a PC and saved those files to a hard or floppy disk, and maybe worked within a local area network at the office. File sharing usually meant walking a disk to another machine. These days, computing is a Web-centric experience, and you perform many of your Internet tasks through software called a Web browser. That browser, which may be a program such as Firefox or Internet Explorer, helps you retrieve information from the Internet multiple times per day, integrate it with other online documents and share data galore with people all over the planet. Google is trying to reshape the computer experience by using its understanding of the Web to create the new Chrome operating system (OS). Traditional operating systems, such as Windows, require a lot of hard drive space and demand some work on your part. You have to install the programs you want individually, manage OS and security updates and manage device drivers, too. Google's Chrome OS aims to overhaul that paradigm. With Chrome, the browser actually is the OS -- in this case, the Chrome OS builds on the Google browser of the same name. In total, the Chrome OS is built on an open-source version of Linux and integrated with the Chrome browser, a simple media player...and that's it. Google embraced the concept of an ultra-simple, Web-centric OS in large part due to the huge recent success of netbooks. Netbooks are small laptop computers that are designed to let users access the Web, and not much more; they're inexpensive and feature-limited hardware, and they aren't built for high-powered applications like Photoshop, for example. Unlike Windows, Chrome won't be available as a download. It'll be pre-installed by netbook manufacturers who adhere to Google's hardware specifications. Chrome is designed to run best on solid-state storage systems as opposed to traditional spinning hard drives, in part because solid-state drives are less prone to failure, but also because they're less spacious -- remember, Google wants you to store your data online. And because the OS uses Web-based applications, you don't need local storage for software, either. Read more: How stuff works
WCF: certificateValidationMode and revocationMode
Posted by
jasper22
at
10:24
|
Having spent a lot of time reasoning about WCF and certificate based authentication, here's a scoop.This forces WCF to expect a client side certificate for message based security:<behavior name="DefaultBehavior" returnUnknownExceptionsAsFaults="false" >
<serviceCredentials>
<serviceCertificate
x509FindType="FindBySubjectName"
findValue="MyCertificate"
storeLocation="LocalMachine"
storeName="My"/>
<clientCertificate>
<authentication certificateValidationMode="ChainTrust" revocationMode="Online"/>
</clientCertificate>
</serviceCredentials>
<metadataPublishing enableGetWsdl="true" enableMetadataExchange="true" enableHelpPage="true"/>
</behavior>What it says is that the client certificate must validate according to the complete certificate chain. In broader terms it forces the caller to use the certificate that is 'validatable' on the service side. This means the following:
Read more: Matevz Gacnik's Weblog
<serviceCredentials>
<serviceCertificate
x509FindType="FindBySubjectName"
findValue="MyCertificate"
storeLocation="LocalMachine"
storeName="My"/>
<clientCertificate>
<authentication certificateValidationMode="ChainTrust" revocationMode="Online"/>
</clientCertificate>
</serviceCredentials>
<metadataPublishing enableGetWsdl="true" enableMetadataExchange="true" enableHelpPage="true"/>
</behavior>What it says is that the client certificate must validate according to the complete certificate chain. In broader terms it forces the caller to use the certificate that is 'validatable' on the service side. This means the following:
- The certificate must be present at the time of request generation (client side)
- The certificate must be valid according to expiration period and certificate generation (checking done on server side)
- The certificate chain (issuing CAs path) must be valid (certificateValidationMode="ChainTrust")
- The certificate must not be obsolete and/or revoked (revocationMode="Online")
Other authentication options of certificateValidationMode and revocationMode include:
- certificateValidationMode can take a velue of ChainTrust, PeerTrust, ChainOrPeerTrust, None or Custom. None means that no certificate checking is done, Custom allows one to plug in a custom X509CertificateValidator (new, System.IdentityModel.Selectors namespace), PeerTrust forces a public key of the client certificate to be present in the 'Trusted People' certificate store on the service side and ChainTrust requests that the client cert can be validated against the root certificates on the server side. ChainOrPeerTrust just executes the OR operator on the last two.
Remark: PeerTrust and ChainOrPeerTrust are also subjected to another attribute called trustedStoreLocation. If peer trust is demanded, one can specify where the public keys are present, meaning either in LocalMachine or CurrentUser store.
Read more: Matevz Gacnik's Weblog
Google shows off Quake-clone running in Native Client
Posted by
jasper22
at
10:22
|
Google might already be impressing us all with the performance of the Chrome browser, but the search giant is only just getting started with the functionality of its web browser.Another project that has been slowly gathering pace is called Native Client. In the video above Henry Bridge, product manager for Native Client, sums up the project as follows: Native Client is an open source project that allows you to run native code in a web browser.What that means is that existing libraries developed for desktop applications to use will now be available to use in a web browser. All the developer need do is recompile their library into Native Client files to unlock their use in the web browser. By implementing such a system for the web browser Google is making it much easier to get complex feature sets and functionality running in a browser. Developing video editing apps, image manipulation features, or even a game engine using web technology like HTML and Javascript alone would be very slow. With Native Client such software can be developed as it would be for the desktop and then ported, retaining the speed, but gaining the ability to run in a browser and store data in the cloud. Google has made the Native Client SDK available for Windows, Mac, and Linux users so that interested developers can start playing around with it on their platform of choice. You can see the potential for Native Client by jumping to 4 minutes 30 seconds in the video to view Nexuiz — an open source modern Quake engine running in a browser. Read more: geek.com
9 Programming Languages To Watch In 2011
Posted by
jasper22
at
10:21
|
I have written several posts regarding job trends in programming languages. However, I have not really written any posts that looked towards the future of programming languages. With job trends, I have been focusing on more heavily adopted languages. In this case, I wanted to look at some other languages that are gaining popularity but have not really become one of the top languages to use. Part of this analysis uses the Tiobe December 2010 rankings, some from ReadWriteWeb’s recent programming languages post (based on this Dataists post), and the rest comes from the job trends that are included. Two languages from the normal job trends posts that will continue to see solid growth and deem mentioning are Objective-C and Python. Obviously, with the growing Apple ecosystem, Objective-C continues to grow. Python is being used in data analysis, which is growing rapidly, as was mentioned in my recent post on some O’Reilly data. I have not split these languages into any particular type, like traditional and scripting, because I wanted to look at everything together. Some of the jobs data is difficult to include because of the amount of noise from other industries. Go and R have a lot of noise in particular and are not included in the graphs. However, they are included due to their origin (Google) and usage (Data Analysis) respectively. First, let’s look at the languages themselves ordered by Tiobe rank (Tiobe ranking and RWW & Dataist Tier included) : Go (Tiobe: 21 , Tier: 4)
R (Tiobe: 26, Tier:3)
Lua (Tiobe: 27, Tier:3)
Scheme (Tiobe: 29, Tier:3)
ActionScript (Tiobe: 37, Tier:2)
Erlang (Tiobe: 49, Tier:3)
Groovy (Tiobe: 50-100, Tier: 3)
Scala (Tiobe: 50-100, Tier:2)
Clojure (Tiobe: 100+, Tier:3)Interestingly enough, there does not seem to be a correlation between the Tiobe rank and the Dataist Tier. If anything, it almost looks like a reverse correlation, but I am going to ignore correlation for now. So, how does the ranking data compare to the job demand data? Read more: Javalobby
R (Tiobe: 26, Tier:3)
Lua (Tiobe: 27, Tier:3)
Scheme (Tiobe: 29, Tier:3)
ActionScript (Tiobe: 37, Tier:2)
Erlang (Tiobe: 49, Tier:3)
Groovy (Tiobe: 50-100, Tier: 3)
Scala (Tiobe: 50-100, Tier:2)
Clojure (Tiobe: 100+, Tier:3)Interestingly enough, there does not seem to be a correlation between the Tiobe rank and the Dataist Tier. If anything, it almost looks like a reverse correlation, but I am going to ignore correlation for now. So, how does the ranking data compare to the job demand data? Read more: Javalobby
OpenId With Forms Authentication
Posted by
jasper22
at
10:20
|
Introduction
As some of you may know from reading some of my past articles/blogs, that I am not really a web man, but I had an idea a while back to create a tool that had to be web based, so I have been busy constructing this ASP .NET MVC web site in my spare time. It is still ongoing, but one area that the web site needed was login/authentication, which is a pretty usual requirement on web sites. In fact ASP .NET has long supplied forms authentication for this purpose (as well as other options). Thing is, I did not really want to store username/passwords in my database, then I read about this protocol called OpenId, which is a protocol that numerous web sites adhere to already. And if you have an OpenId compliant login, my site could allow its users to use those credentials directly with the OpenId compliant web site validating them. They basically handle the login/authentication process and redirect back to the original calling site (my site). This may sound quite nuts, but it is quite probable that you yourself are already in possession of an OpenId login, as there are many many OpenId compliant web sites out there. So it seemed to make sense to allow users to simply use their existing login credentials rather than for my site to ask them to create even more credentials. So this is all well and good, so what is this article all about. Quite simple really, this article will demonstrate how to use OpenId with Forms Authentication (to store the Authentication cookie) within a ASP .NET MVC web site. I should mention that this demo apps web site it is not the prettiest of web sites, as I have literally applied no styling to it what so ever, I intentionally left it without trying to muddy the water so to speak. So please be aware that it is not going to win any beauty contests at all.
A Brief Discussion About OpenIdOpenID is an open standard that describes how users can be authenticated in a decentralized manner, obviating the need for services to provide their own ad hoc systems and allowing users to consolidate their digital identities.
The OpenID protocol does not rely on a central authority to authenticate a user's identity. Moreover, neither services nor the OpenID standard may mandate a specific means by which to authenticate users, allowing for approaches ranging from the common (such as passwords) to the novel (such as smart cards or biometrics).
The term OpenID may also refer to an ID as specified in the OpenID standard; these IDs take the form of a unique URL, and are managed by some 'OpenID provider' that handles authentication.Read more: Codeproject
As some of you may know from reading some of my past articles/blogs, that I am not really a web man, but I had an idea a while back to create a tool that had to be web based, so I have been busy constructing this ASP .NET MVC web site in my spare time. It is still ongoing, but one area that the web site needed was login/authentication, which is a pretty usual requirement on web sites. In fact ASP .NET has long supplied forms authentication for this purpose (as well as other options). Thing is, I did not really want to store username/passwords in my database, then I read about this protocol called OpenId, which is a protocol that numerous web sites adhere to already. And if you have an OpenId compliant login, my site could allow its users to use those credentials directly with the OpenId compliant web site validating them. They basically handle the login/authentication process and redirect back to the original calling site (my site). This may sound quite nuts, but it is quite probable that you yourself are already in possession of an OpenId login, as there are many many OpenId compliant web sites out there. So it seemed to make sense to allow users to simply use their existing login credentials rather than for my site to ask them to create even more credentials. So this is all well and good, so what is this article all about. Quite simple really, this article will demonstrate how to use OpenId with Forms Authentication (to store the Authentication cookie) within a ASP .NET MVC web site. I should mention that this demo apps web site it is not the prettiest of web sites, as I have literally applied no styling to it what so ever, I intentionally left it without trying to muddy the water so to speak. So please be aware that it is not going to win any beauty contests at all.
A Brief Discussion About OpenIdOpenID is an open standard that describes how users can be authenticated in a decentralized manner, obviating the need for services to provide their own ad hoc systems and allowing users to consolidate their digital identities.
The OpenID protocol does not rely on a central authority to authenticate a user's identity. Moreover, neither services nor the OpenID standard may mandate a specific means by which to authenticate users, allowing for approaches ranging from the common (such as passwords) to the novel (such as smart cards or biometrics).
The term OpenID may also refer to an ID as specified in the OpenID standard; these IDs take the form of a unique URL, and are managed by some 'OpenID provider' that handles authentication.Read more: Codeproject
Build desktop and web apps with Alpha Five 10.5 Developer
Posted by
jasper22
at
10:20
|
Alpha Five is a development tool that I wanted to learn more about for some time. Whenever I mentioned it on TechRepublic, a number of Alpha Five users would comment that they love the tool. Now that I finally had the chance to work with Alpha Five, I can see why they gave it their stamp of approval. Alpha Five is definitely worth a look if it’s appropriate for your project. Note: The vendor provided me with a full version of Alpha Five 10.5 Developer free of charge for the purposes of this review.My review of Alpha Five 10.5Alpha Five is capable of generating desktop and Web applications from the same data model, which is a huge plus. Developers can leverage the tool to deliver sophisticated applications; and yet, someone without significant programming experience or skill (such as a junior developer or a good business analyst) could quickly assemble simple, data-driven applications. Alpha Five occupies a unique niche because it does more than a code generator without taking away a substantial amount of control from the developer. Alpha Five is heavily oriented towards building data-driven applications. For example, creating screens for a desktop application usually starts by picking a database table (or view) and selecting fields to include on the form. After you follow a couple of steps in the wizard (though you don’t have to use the wizard), a form for working with the table or view is created. You can edit the code for handling events by editing XBasic code directly (the BASIC-like language that Alpha Five uses) or by constructing a tree of commands in the Action Script editor (which is not the ActionScript that Flash uses) Read more: TechRepublic
One of the Most Powerful Debugging Practices
Posted by
jasper22
at
10:18
|
The hard to find bugs generally occur under circumstances that are relatively rare. After all, if the program re-boots your system every time you run it, you will usually fix that error. Some of these rare cases are caused by executing a code path that has never been executed before. When your program first starts, you will generally create a number of objects. You have a code path you take if those constructors throw exceptions, but have they ever failed? If not, you have an accident waiting to happen. What does your program actually do when that particular constructor fails? As long as you have not tested a code path, you have not fully tested your program. Be sure that you exercise every code path. If you have an "if () ... else ..." and you have always executed the "else" part, then the "if" part is a bug waiting to happen. There is a very simple way to handle this, and do so in a manner that will help you as you first run your code. The beauty of using traps is it helps you immediately, so that you will quickly find that you automatically put them in as you write code. This is composed of two methods, trap() and trap(bool) – I have included Java, C++, & assembler examples at the, but for illustration I will use C# here. What a trap does is drop you into the debugger when you hit one. First the example, then why this is so useful // Open an XML file
XmlReader reader;
if (string.IsNullOrEmpty(username)) {
Trap.Trap();
reader = XmlReader.Create(filename, xmlSettings);
} else {
Trap.Trap(!hasDomain);
Trap.Trap(hasDomain);
XmlUrlResolver resolver = new XmlZipResolver();
resolver.Credentials = hasDomain ? new NetworkCredential(user, password, domain) : new NetworkCredential(user, password);
xmlSettings.XmlResolver = resolver;
reader = XmlReader.Create(filename, xmlSettings);
}The Immediate Pay-OffWhy is this a big help from the start? Because it helps you single step through each part of your code once. In the code above you probably test at first with no username so you'll fall in the debugger on the first trap. You mark it and then step over the Create. You may single step a couple of lines after to make sure the xml is good, then you go. Read more: Windward Wrocks
XmlReader reader;
if (string.IsNullOrEmpty(username)) {
Trap.Trap();
reader = XmlReader.Create(filename, xmlSettings);
} else {
Trap.Trap(!hasDomain);
Trap.Trap(hasDomain);
XmlUrlResolver resolver = new XmlZipResolver();
resolver.Credentials = hasDomain ? new NetworkCredential(user, password, domain) : new NetworkCredential(user, password);
xmlSettings.XmlResolver = resolver;
reader = XmlReader.Create(filename, xmlSettings);
}The Immediate Pay-OffWhy is this a big help from the start? Because it helps you single step through each part of your code once. In the code above you probably test at first with no username so you'll fall in the debugger on the first trap. You mark it and then step over the Create. You may single step a couple of lines after to make sure the xml is good, then you go. Read more: Windward Wrocks
HowTo: object orientated programming / OOP in Javascript (create a simple class)
Posted by
jasper22
at
10:16
|
Because of the increasing hype about AJAX and the “file-format” JSOPN, another subject in the field of web-developmen gets more and more interesting: Javascript-development.All in all, in my opinion a little change is happening to web-development – we try to realize many things on the client. I appreciate this change because, why should I communicate with the server while sorting a chart when the files are already on the client?Exactly these are the types of assignments that are done by Javascript-Frameworks today. In Microsoft’s ASP.NET AJAX Extensions you will find a client-library as well. But there is a general question: How is it possible to encapsulate files in such a Framework? How is it possible to define own Javascript classes with methods? Defining classes and methods in Javascript – Keyword “prototype”Prototype is not only a keyword in the fields of Javascript Framework for defining methods, also in the world of JS.But step by step now. We create a very simple example: a rectangle. The attributes are width and height and we just want to know the area.Step 1: defining the constructor including memberfunction Rectangle()
{
this.height;
this.width;
}In fact, the constructor is a normal JS function because the keyword “class” doesn’t exist in JS. After that we tell them our two attributes “width” and “height” and as usual in OOP beginning with “this”. Step 2: defining getter/setterRead more: Code-Inside Blog International
{
this.height;
this.width;
}In fact, the constructor is a normal JS function because the keyword “class” doesn’t exist in JS. After that we tell them our two attributes “width” and “height” and as usual in OOP beginning with “this”. Step 2: defining getter/setterRead more: Code-Inside Blog International
Html Helpers in Asp.net MVC
Posted by
jasper22
at
10:15
|
כמה מילים על Asp.net MVC
ב – Asp.net MVC כתובת ה – url אינה מפנה לדף כמו ב – Asp.net, אלא לפונקציה ב – Controller. ה – Controller אחראי לקבל את הבקשה לטפל בה כראוי ולהפנות ל –View מתאים.
ה – View הוא קובץ aspx שמכיל Markup של Html וקטעי קוד. המנוע של Asp.net MVC יודע לרנדר אותו יחד עם האובייקט ששולח ה – Controller כדי להחזיר תשובה ל –Client .
לדוגמה:
כך נראית הפונקציה ב – Controller שמוצאת את האובייקט המתאים ומחזירה אותו ל – View הרלוונטי.
public ActionResult Details(int id)
{
Dinner dinner = dinnerRepository.GetDinner(id);if (dinner == null)
return View("NotFound");
else
return View("Details", dinner);
}
Html Helpers הם קלאסים שמרנדרים קטעי Html לתוך ה – View.
HtmlBeginForm
HtmlBeginForm מרנדר את התגית <form>. היתרון בשימוש בו הוא היכולת להשתמש ב – Using וב – Dispose.
ה – CLR מנקה את הזכרון מאובייקטים שאינם בשימוש באמצעות שימוש ב - garbage collection, ניקוי הזכרון מתבצע כאשר יש דרישה לשיפור בביצועים ותמיד כדאי לדאוג לשחרר אובייקטים שצורכים משאבים, או לדאוג שדברים יתבצעו גם אם התהליך חטף תעופה באמצע. האובייקטים שעטופים ב – Using מממשים את האינטרפייס IDisposable ואת המתודה Dispose שמנקה אותם מהזכרון לאחר שהבלוק מסתיים.
Read more: Dovi Perla's BlogInSimSniffer
Posted by
jasper22
at
10:13
|
InSimSnifferInSimSniffer is a InSim packet sniffer for the racing simulator Live for Speed. It connects to the game and displays the contents of each InSim packet that is received. This is useful both as a debugging aid and also in learning about how certain operations are handled by InSim. Read more: Codeplex
10 dirty little secrets you should know about working in IT
Posted by
jasper22
at
10:13
|
Editor’s note: This article was first published in August 2007. It has now been updated and we’ve added a slideshow for those who prefer the visuals.If you are preparing for a career in IT or are new to IT, many of the “dirty little secrets” listed below may surprise you because we don’t usually talk about them out loud. If you are an IT veteran, you’ve probably encountered most of these issues and have a few of your own to add — and please, by all means, take a moment to add them to the discussion. Most of these secrets are aimed at network administrators, IT managers, and desktop support professionals. This list is not aimed at developers and programmers — they have their own set of dirty little secrets — but some of these will apply to them as well. 10.) The pay in IT is good compared to many other professions, but since they pay you well, they often think they own you
9.) It will be your fault when users make silly errors
8.) You will go from goat to hero and back again multiple times within any given day
7.) Certifications won’t always help you become a better technologist, but they can help you land a better job or a pay raise
6.) Your nontechnical co-workers will use you as personal tech support for their home PCs Read more: TechRepublic
9.) It will be your fault when users make silly errors
8.) You will go from goat to hero and back again multiple times within any given day
7.) Certifications won’t always help you become a better technologist, but they can help you land a better job or a pay raise
6.) Your nontechnical co-workers will use you as personal tech support for their home PCs Read more: TechRepublic
Subscribe to:
Comments (Atom)





