Ubuntu Linux 11.04, "Natty Narwhal," Now Available
Ubuntu Linux, easily one of the most popular Linux distributions available today, is out with what may be its most significant set of changes to date. 11.04 "Natty Narwhal" has brought with it not just major version jumps for nearly every core app and service, but also a completely revamped Unity interface.
Earlier this month, we took an extensive tour through the beta release of Ubuntu's latest, and things have mostly improved since then. The beta's may have been rough around the edges, but 11.04 is now stable and it feels the part.
Love it or hate it, Unity is clearly here to stay. It's been through a major update since 10.10. The interface still does sit atop the GNOME Desktop Environment, though—so things aren't so different once you get past the layout and some basic control maneuvers. It's worth noting, though, that users can select "Ubuntu Classic" from the login screen to switch to a possibly more familiar, more GNOME-like desktop.
Read more: Lifehacker
InfoStrat Motion Framework
Posted by
jasper22
at
13:43
|
Project Description
InfoStrat Motion Framework enables you to easily use motion tracking in your WPF applications with depth sensors such as Kinect and PrimeSensor.
Read more: Codeplex
Sony: Credit Card Data Exposed in PlayStation Network Hack
Posted by
jasper22
at
12:08
|
Foster City, Calif. - Sony (NYSE: SNE) has acknowledged that the now weeklong outage of its PlayStation Network online game service was due to a security breach, during which its 70 million users' credit card information may have been accessed. "While there is no evidence at this time that credit card data was taken, we cannot rule out the possibility," the company wrote in a blog post. "If you have provided your credit card data through PlayStation Network or Qriocity, out of an abundance of caution we are advising you that your credit card number (excluding security code) and expiration date may have been obtained."
The company said that data including users real names, birthdates, physical and email addresses, and usernames and passwords associated with their PlayStation Network and Qriocity accounts were accessed by the hackers.
As a result, Sony is encouraging users "to be especially aware of e-mail, telephone, postal mail or other scans that ask for personal or sensitive information."
The company is currently engaged in an investigation of the incident, and said access to some of the downed services could be restored within a week.
In a statement, Sen. Richard Blumenthal (D-Conn.) said he wrote to the president and CEO of Sony Computer Entertainment America, calling on the company "to provide PlayStation Network users with financial data security services, including free access to credit reporting services for two years, the costs of which should be borne by the company."
Read more: DigitalMedia wire
Slackware 13.37 is released!
Posted by
jasper22
at
10:58
|
It's true! Slackware 13.37 has been released. Nearly a year in the making, you will appreciate the performance and stability that can only come with careful and rigorous testing. Slackware 13.37 uses the 2.6.37.6 Linux kernel (hence our new $SLACKWARE_VERSION.$KERNEL_VERSION naming system used for this release ;-), and also ships with 2.6.38.4 kernels for those who want to run the latest (and also includes configuration files for 2.6.35.12 and 2.6.39-rc4). The long-awaited Firefox 4.0 web browser is included, the X Window System has been upgraded (and includes the open source nouveau driver for nVidia cards). The venerable Slackware installer has been improved as well, with support for installing to btrfs (for those who would like to try a new copy on write filesystem), a one-package-per-line display mode option, and alienBOB's big surprise: an easy to set up PXE install server that runs right off the DVD!
More details may by found in the official announcement and in the release notes. For a complete list of included packages, see the package list.
Please consider supporting the Slackware project by picking up a copy of the Slackware 13.37 release from the Slackware Store. The discs are off to replication, but we're accepting pre-orders for the official 6 CD set and the DVD. The CD set is the 32-bit x86 release, while the DVD is a dual-sided disc with the 32-bit x86 release on one side and the 64-bit x86_64 release on the other. And, we still have T-shirts (coming soon, a limited edition 13.37 release commemorative black T-shirt with the classic Slackware logo on the front, and a "leet" LILO bootscreen on the back) and other Slackware stuff there, so have a look around. Thanks to our subscribers and supporters for keeping Slackware going all these years.
Thanks are again due to the Slackware crew, the developers of slackbuilds.org, the community on linuxquestions.org, Slackware IRC channels, and everyone else who helped out with this release.
Read more: The Slackware Linux Project
Microsoft returning to its Windows versioning hell
Posted by
jasper22
at
10:58
|
Word is that even as early versions of Windows 8 is being leaked to the web and we head towards a possible fall public beta that Microsoft could be returning to its ridiculous versioning scheme for the new Windows.
Not only are they preparing for RM version but also versions that won’t include Internet Explorer. From The Next Web and WinRumors we get the full list of the different versions we can expect:
- ARM.Starter=00342
- ARM.StarterN=00345
- ARM.StarterE=00348
- ARM.HomeBasic=00346
- ARM.HomeBasicN=00358
- ARM.HomeBasicE=00349
- ARM.HomePremium=00359
- ARM.HomePremiumN=00362
- ARM.HomePremiumE=00351
- ARM.Professional=00371
- ARM.ProfessionalN=00376
- ARM.ProfessionalE=00352
- ARM.Enterprise=00392
- ARM.EnterpriseN=00403
- ARM.EnterpriseE=00355
- ARM.Ultimate=00426
- ARM.UltimateN=00432
- ARM.UltimateE=00356
Read more: Winextra
SILVERLIGHT SPY APRIL 2011 UPDATE
Posted by
jasper22
at
10:55
|
An update of Silverlight Spy is now available for download. This update adds support for Silverlight 5 Beta and Silverlight 4 GDR 4 (released a week ago). Furthermore this Silverlight Spy Update adds syntax highlighting to the DLR shell, Windows 7 Jump List support and full event monitoring for Popup and Silverlight 5 windows.
A word on Silverlight 5 Beta
Please note that Silverlight 5 Beta is really a beta, it's a bit rough around the edges and consequently you may see some unexpected behavior when running Silverlight Spy with Silverlight 5. This will be taken care of as soon as Silverlight 5 reaches RTM status.
Read more: First Floor Software
.NET Windbg Extension Development in Visual Studio
Posted by
jasper22
at
10:48
|
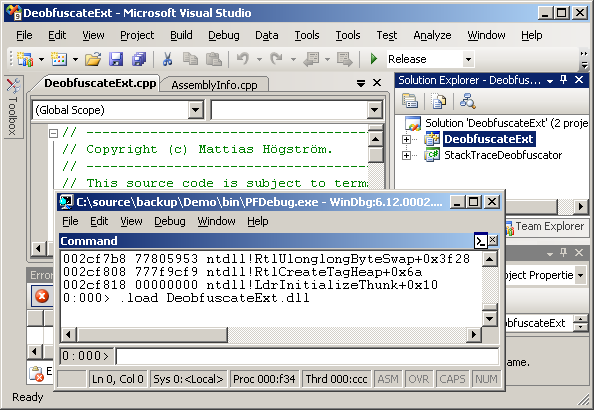
Introduction
This article will show you how to develop Windbg extensions in Visual Studio, and to leverage the .NET platform through the C++/CLI technology.
Background
I was once assigned the task to evaluate the applicability of code obfuscation of .NET assemblies with respect to protection of intellectual property, but also its consequences for debugging and support.
Obfuscation is not without drawbacks. It makes debugging almost impossible, unless it is possible to reverse the obfuscation.
The Obfuscator I evaluated provided an external tool for deobfuscation with the use of map files. You had to manually copy and paste the text into this tool.
Read more: Codeproject
The Gang of Four patterns as everyday objects
Posted by
jasper22
at
10:48
|
A System Metaphor is what eXtreme Programming use to describe an architecture: for example you can think of particular application as production lines, or flying planes, or other kinds of machines. A metaphor has its limits in describing a concept, but it's really fast in being understood by programmers who are naive to the concept.
The original Gang of Four design patterns can be explained as real, everyday (and sometimes science-fictional) objects and actions. In this list, sometimes I use other software as the metaphor, as you will be already familiar with it if you are reading here. But I try to stick to physical objects and systems when possible.
Creation patterns
An Abstract Factory is a factory conforming to some specification, like a phone factory. The concrete phones you can buy are returned by this Factory. However, the standardization is not only in the interaction with the phones (each has 0-9 keys and a call button) but also in the interaction with the Factory (for example suppliers for large companies should follow standard supplier agreements).
A Builder is a very patient architect (the one that builds houses, not software): you tell him that you want the kitchen on this floor, and two bathroom and so on, but he cares about making it work and draw a complete design which accounts for electric wiring, pipes, structural integrity and so on.
A Factory Method is a cake mix; most of the work is already done and the recipe is written, but you may (or must) provide the missing ingredients when required by the recipe. The missing ingredient may also not be edible: the mold where you put the dough can be considered an abstract Factory Method.
A Prototype is a gremlin. Once you have it, you put it in the water and you can instantly create another one (beware not to feed your Prototype pattern after midnight.) Other metaphors are cell division, or any cloned animal like the sheep Dolly (actually only if you intervene on the genes it's a Prototype pattern: if you only create exact copies it's not very useful.)
A Singleton has no correspondence in real life, because it is in fact a bad idea. It will be like a sheet of paper that when written manages files in your pc, or a credit card that charges itself without a PoS. Some says titles such as the US president can only be held by one person, so they are Singleton. Yet there are many presidents (Clinton, Bush, Obama...) and if you ship products in Europe they don't really need a reference to the US president.
Structural patterns
An Adapter can be simply an AC adapter for laptops, but also any kind of electrical adapter between different outlet types. Every geek has lots of adapters in his house so this is the easiest pattern to explain.
A Bridge is an operating system which uses drivers (thus, every OS). The interface for the client (fopen() and similar functions) are evolved separately from drivers for hard-disks, optical devices, and Flash memories.
Continuing with the electrical metaphors, a Composite is a power strip, where you can plug in many devices with a single outlet. In mathematics instead, every arithmetic expressions is a Composite which can be combined with other ones to build a longer, more complex expression.
A Decorator is a layer of colored glass: in particular sunglasses and augmented reality (or 3D) glasses fit the pattern. They do not change your interface with the world (pair of eyes), but they are interchangeable, add some kind of behavior or filtering and can be overlapped in any order.
A Facade is a customer support desk, or even a wedding planner: he hides from you the complexity of a large subsystem. The wedding planner orders flowers, makes reservations, organizes everything for you.
A Flyweight: preforked processed on the web server, although that says nothing about the idiomatical implementation of flyweight we use in oo languages
A Proxy is each SSH client you run to access a shell on another machine. Also VNC and other graphical proxies are equivalent.
Behavioral patterns
A Chain of Responsibility can be thought of as a military chain of command, where each request may be escalated to the superior officer. Also some business are an example, at least the ones that let you say "Can I talk to your boss?"
Read more: Agile Zone
XNA RPG - Learning XNA while building a RPG, a 26 part tutorial series
Posted by
jasper22
at
10:44
|
E3 2011 is a little more than a month away, the expo where nearly all the cool gaming news comes out. There's rumors that there's news coming about development "stuff" for the XBox 360 and E3 seems like the logical time for that news to be released.
To give you a leg up and help you catch that wave, today's post is curtsey of Jamie McMahon and his very cool XNA Game Programming Adventures, XNA 4.0 RPG Tutorials series.
The series takes you from install to a playable 2D RPG with each in the series building on the last. The tutorial includes not only building the game but a game/level editor too.
Part 1 - Getting Stated
This first tutorial is about getting started with the role playing game, Eyes of the Dragon. I create the basic project, two class libraries, and some components that will be used through out the rest of the tutorials.
...
Part 4 - Tile Engine
The forth tutorial is about adding in a tile engine for the game. The tile engine is what you will use to draw the maps the player will use to explore your world. In the next tutorial I will add in more to the tile engine.
...
Part 10 - Character Classes
This adds in some basic classes for characters in the game and a class to represent the world the game takes place in.
Part 11A - Game Editor
In this tutorial I add in an editor for the game and move from a static character class system to a dynamic character class system. This is part one of a three part tutorial.
...
Read more: Channel9
AdMob Tutorial - Add ads to your application
Posted by
jasper22
at
10:41
|
Edit: The AdMob SDK has changed and is not fully backwards compatible. The tutorial was updated accordingly.
Using the new AdMob library you can earn money by displaying ads in your applications.
Installing AdMob libraries:
1. Go to AdMob - Register and register to AdMob.
2. Add an application:
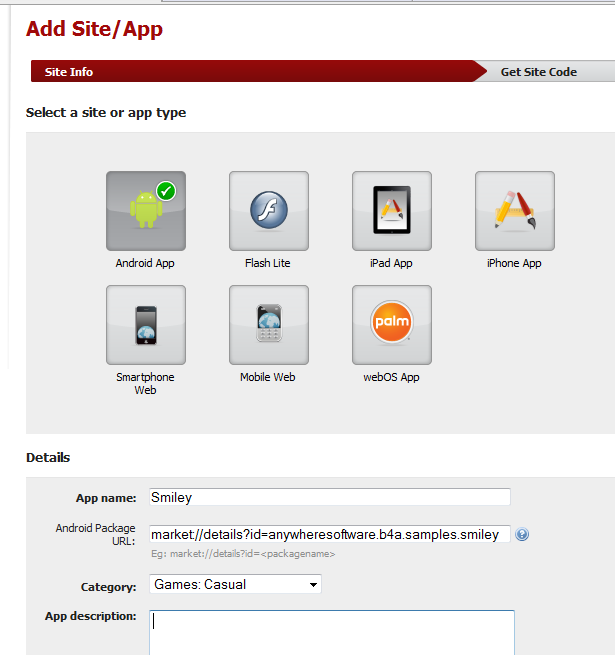
The url can be a placeholder for a future application.
3. After creating the application you should see a screen with your "Publisher ID" and a link to "get publisher code".
Later you will need to enter your publisher id in the program code. Now you should download AdMob SDK by pressing on "get publisher code".
You will download a zip file with a name similar to: GoogleAdMobAdsSdk-4.0.4.zip.
Inside the zip there is a folder with the same name. Inside this folder you will find the required jar file (GoogleAdMobAdsSdk-x.x.x.jar).
Note that you may have problems extracting the whole zip file because it contains a folder and a file with the same name. The solution is to just drag the required file.
Rename the jar file and change its name to GoogleAdMobAdsSdk.jar (removing the specific version suffix).
4. Download AdMob B4A library.
You should copy all files to the additional libraries path.
5. Copy GoogleAdMobAdsSdkAndroid.jar to the additional libraries path.
Adding AdMob to your application
1. Add a reference to AdMob and GoogleAdMobAdsSdk libraries.
2. Typical code should look like:
Code:
Sub Process_Globals
End Sub
Sub Globals
Dim AdView1 As AdView
End Sub
Sub Activity_Create(FirstTime As Boolean)
Activity.LoadLayout("1")
AdView1.Initialize("Ad", "YourPublisherId") 'publisher id that you received from AdMob.
Activity.AddView(AdView1, 0dip, 0dip, 320dip, 50dip) 'previously the height was 48dip. Now it is 50dip.
AdView1.LoadAd 'loads an ad
End Sub
'debugging only:
Sub Ad_FailedToReceiveAd (ErrorCode As String)
Log("failed: " & ErrorCode)
End Sub
Sub Ad_ReceiveAd
Read more: Anywhere software
Hiding data in disk fragmentation
Posted by
jasper22
at
10:39
|
How do you keep something secret?
If you encrypt it then the statistical properties of the stored data reveal that you have something to hide. Once the fact is out that you have something to hide then the process of revealing your secrets can begin. You could even be forced to reveal the encryption keys by law once it is known that you have encrypted data.
An alternative is to hide you secrets in plain sight - a technique called steganography. For example you can store data as part of an image by changing a few pixels by an amount that isn't detectable. As long as you do the job correctly and don't give yourself away by modifying the statistics of the steganographic medium then it is fairly difficult to detect.
The trick with steganography is to find something that you can use to hide the data without making it obvious. Now a team of researchers at University of Southern California in Los Angeles has found a novel steganographic technique, but not one without its problems.
The idea is to use the way data is stored on a hard disk. Operating systems allocate blocks of storage to any file that you create. Exactly how they do this varies and, for the sake of argument, the example uses the FAT filing system that is now mostly superseded by NTFS under Windows but it is still used on small storage devices such as memory cards and USB sticks. FAT allocates storage in "clusters" and these can be spread out all over the disk. In most cases you really want any file to be stored in a set of physically adjacent clusters, but files can become fragmented and stored all over the drive. Normally this is considered a bad thing and disk defragmenters are used to tidy up a disk and make it more efficient. Some operating systems - Windows 7 for example - even perform defragmentation automatically.
The steganographic system proposed simply uses the location of the clusters that make up a file to store the real data. There are lots of ways of hiding data in the cluster locations.
For example, a simple coding rule is:
if two storage blocks are physically next to each other then the next encoded bit is the same as the previous bit and if they are separated then the bit changes.
Read more: I Programmer
פונקציית If באקסל
Posted by
jasper22
at
10:35
|
שלום לכולם ,
כאן רותם כהן מצוות התמיכה של Microsoft .
בפוסטים הקודמים שלי למדנו כיצד להשתמש בפונקציות בסיסיות, טווחים וקיבועי נוסחאות בתוכנת אקסל .
היום נעלה רמה ונעבור ללמוד נושא מתקדם יותר והוא פונקציית If שהיא למעשה פונקציית התניה .
מהן פונקציות התניה ?
פונקציות התניה הן למעשה פונקציות המקיימות בדיקה לתנאי המוגדר בתוכן ועל ידי החזרת פלט במבנה של חיוב או שלילת התנאי מציגות את התוצאה .
נשמע מסובך ? אל חשש , במילים פשוטות יותר מדובר בפונקציה המבצעת בדיקה לתנאי שאנו נגדיר בה , בנוסף לתנאי זה נגדיר למעשה 2 תוצאות ; אחת במידה ותנאי אכן מתקיים ואחת במידה והתנאי אינו מתקיים .
בעת עבודה עם הפונקציה תתבצע בדיקה תמידית לתנאי ועל פי תוצאה זו יוצג הערך בתא .
בדוגמא הבאה למשל הגדרנו לפונקציה תנאי בו נבדוק האם תוצאת החיבור של התאים A1 ו A2 שווה למספר 3, במידה וכן הגדרנו להציג את המילה "נכון" ואילו במידה והתוצאה אינה שווה למספר 3 תוצג המילה "לא נכון".

שימו לב כי במידה ונשנה את אחד מהנתונים המוצגים כך שתוצאת התנאי תהיה שלילית והתנאי למעשה לא יתקיים תשתנה גם התוצאה בתא המציג את תוצאת פונקציית ההתניה

Read more: MS Support blog
IIS Transform Manager 1.0 (Beta)
Posted by
jasper22
at
10:34
|
Overview
IIS Transform Manager 1.0 Beta is an extensible media transform engine that enables "watch folder" job submission, queuing, management, integrated media transcoding/transmuxing, and batch-encryption of on-demand audio and video files. Windows Media-formatted and MP4-formatted files, or other encoder-supported file formats, to on-demand Smooth Streams for delivery to Smooth Streaming-compatible clients (such as Silverlight). Another example is transmuxing Smooth Streaming fragments encoded with H.264 (AVC) video and AAC-LC audio codecs to MPEG-2 Transport Stream (MPEG-2 TS) segments for delivery to Apple® mobile digital devices. Transform Manager can be integrated with the IIS Smooth Streaming feature in IIS Media Services, which delivers the "transformed" content.
Read more: IIS Transform Manager 1.0 (Beta) x86
Read more: IIS Transform Manager 1.0 (Beta) x64
Scapy
Posted by
jasper22
at
09:57
|
What is Scapy
Scapy is a powerful interactive packet manipulation program. It is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more. It can easily handle most classical tasks like scanning, tracerouting, probing, unit tests, attacks or network discovery (it can replace hping, 85% of nmap, arpspoof, arp-sk, arping, tcpdump, tethereal, p0f, etc.). It also performs very well at a lot of other specific tasks that most other tools can't handle, like sending invalid frames, injecting your own 802.11 frames, combining technics (VLAN hopping+ARP cache poisoning, VOIP decoding on WEP encrypted channel, ...), etc. See interactive tutorial and the quick demo: an interactive session (some examples may be outdated).
Read more: Scapy
Mausezahn
Posted by
jasper22
at
09:55
|
What is Mausezahn?
Mausezahn is a free fast traffic generator written in C which allows you to send nearly every possible and impossible packet. It is mainly used to test VoIP or multicast networks but also for security audits to check whether your systems are hardened enough for specific attacks.
- Mausezahn can be used for example:
- As traffic generator (e. g. to stress multicast networks)
- To precisely measure jitter (delay variations) between two hosts (e. g. for VoIP-SLA verification)
- As didactical tool during a datacom lecture or for lab exercises
- For penetration testing of firewalls and IDS
- For DoS attacks on networks (for audit purposes of course)
- To find bugs in network software or appliances
- For reconnaissance attacks using ping sweeps and port scans
- To test network behaviour under strange circumstances (stress test, malformed packets, ...)
...and more. Mausezahn is basically a versatile packet creation tool on the command line with a simple syntax and context help. It could also be used within (bash-) scripts to perform combination of tests. By the way, Mausezahn is quite fast; when started on my old PIII-Laptop (1.4 GHz, Gigabit Ethernet) I measured 755 Mbit/s using the interface packet counters of an HP ProCurve 5400 switch.
Read more: Mausezahn
Android tutorial: Dynamicaly load more items to the ListView ( Never Ending List! )
We pretty much all know the nice technique apps like GMail / Facebook use to dynamically load more items to the ListView then you scroll to the bottom. In this post i want to shed some light on how to make such a list ourselves!
We can approach this from a few sides:
The first option is to add a button to the footer of the view. when pressed it will load more content.
The second option is to check if the last item is visible and load more content when it is!
I really like the second one, because i think its more user friendly. Android makes checking is a item is in view very easy because they added a function with the following method signature:
public abstract void onScroll (AbsListView view, int firstVisibleItem, int visibleItemCount, int totalItemCount)
As you might have guessed: with these parameters we can easily figure out whats the last item on screen! Before we make this method we will first have to add a footer to the ListView.
More after the breaky break!
Read more: Programmer XR
NetTalk XMPP Messenger Server
Posted by
jasper22
at
15:02
|
Project Description
NetTalk is XMPP server based on AgsXmpp server component.
Web server running in Asp.net and no need to any service or other things to run.
Read more: Codeplex
Viewdle Releases SocialCamera For Android: Instant Photo Tagging, Sharing
Posted by
jasper22
at
14:58
|

Visual analysis company Viewdle this morning launched an Android app called SocialCamera that allows users to instantly tag photos, add captions and share them on Flickr or Facebook, by email or MMS. The demo video below explains how the app works in more detail.
The Android application, which is still in beta and not to be confused with Justin.TV’s Socialcam app, is free of charge and should be available through Android Market today.
Viewdle was founded back in 2007 and last October raised $10 million in Series B funding from a group of investors including Best Buy, BlackBerry Partners Fund and Qualcomm.
On a sidenote: I organized my first Plugg conference back in March 2008, and the fledgling company took home the top prize at the startup competition that year (it later went on to win the one at Le Web, too).
Read more: TechCrunch
TediOS Operating System
Posted by
jasper22
at
14:56
|
Project Description
A very simple OS with crude memory management, console interface and a partially implemented file system.
This OS was not intended to be used in any production environment or any particular purpose other than my personal education.
Enjoy!
Read more: Codeplex
Microsoft(R) SQL Server(R) 2008 R2 Service Pack 1 Community Technology Preview
Posted by
jasper22
at
14:48
|
Overview
SQL Server 2008 R2 Service Pack 1(SP1) Customer Technology Preview (CTP) is now available for download. SQL Server 2008 R2 service packs are cumulative updates and upgrade all service levels of SQL Server 2008 R2 to SP1 CTP. This service pack contains the cumulative updates up to SQL Server 2008 R2 SP1 cumulative update packages 6. You can use these packages to upgrade any of the following SQL Server 2008 R2 editions:
(1) SQL Server 2008 R2 Parallel Computing Edition
(2) SQL Server 2008 R2 Datacenter Edition
(3) SQL Server 2008 R2 Enterprise Edition and Developer Edition
(4) SQL Server 2008 R2 Standard Edition
(5) SQL Server 2008 R2 Web Edition
(6) SQL Server 2008 R2 Workgroup Edition
(7) SQL Server 2008 R2 Express Edition
Note : These packages are available for testing purposes only in a non-production environment. To upgrade SQL Server 2008 R2 Express Edition, obtain the SP1 version of Express Edition or Express Edition with Advanced Services.
Read more: MS Download
WCF BINDINGS NEEDED FOR HTTPS
Posted by
jasper22
at
14:47
|
I just finished writing my first production WCF application, which worked very well until I deployed it to our production environment. All of a sudden none of the WCF calls would work, and I would get a JavaScript "TestService is not defined" error. When I look inside the JS service reference (in debug mode), I got the following error:
Could not find a base address that matches scheme http for the endpoint with binding WebHttpBinding. Registered base address schemes are [https]
So apparently my WCF service registered itself as HTTPS (since it is over SSL), but my binding was only configured for HTTP. The solution is to define a custom binding inside your Web.Config file and set the security mode to "Transport". Then you just need to use the bindingConfiguration property inside your endpoint definition to point to your custom binding. The entire HTTPS-enabled system.serviceModel section is below:
<system.serviceModel>
<behaviors>
<endpointBehaviors>
<behavior name="TestServiceAspNetAjaxBehavior">
<enableWebScript />
</behavior>
</endpointBehaviors>
</behaviors>
<serviceHostingEnvironment aspNetCompatibilityEnabled="true" />
<services>
<service name="TestService">
<endpoint address="" behaviorConfiguration="TestServiceAspNetAjaxBehavior"
binding="webHttpBinding" bindingConfiguration="webBinding" contract="TestService" />
</service>
</services>
<bindings>
<webHttpBinding>
<binding name="webBinding">
<security mode="Transport">
Read more: SCOTT'S BLOG
Behind the Windows 8 build hash
Posted by
jasper22
at
14:44
|
With early builds of Windows 8 leaking, increased attention has been focused on understanding a new 16 character string affixed to the end of the build watermark. Some have speculated the characters identify the original installer (Microsoft employee) while others have dismissed the importance altogether. 

After installing the leaked Windows 8 7955 build, in plain sight are the characters a1b6210f837a32cf. Digging through shell32.dll, housing code to paint the desktop watermark, I found code that sources from HKLM\SYSTEM\WPA\478C035F-04BC-48C7-B324-2462D786DAD7-5P-9. More specifically, the Default value, comprising of 128 bytes, is read and run through a XOR-based function producing a 64-bit (8 byte) hash. I’ve included a rough translation of the algorithm (from assembly to C++) for review. (If this is an implementation of a well-known algorithm, I’d love to know.)
Read more: Within windows
Various Clients and Forms Authentication
Posted by
jasper22
at
14:38
|
Scenarios
In each of the below scenarios, forms authentication is used to secure access to the ASP.NET MVC endpoints and WCF services.
WPF accessing WCF services
WPF accessing MVC endpoints
Windows Phone 7 accessing WCF services
Desktop and mobile browsers accessing ASP.NET MVC website pages
jQuery accessing MVC endpoints
While I have not included the code for a Windows Phone 7 to access MVC endpoints that is a supported scenario as well.
Requirements
Visual Studio 2010
SQL Express 2008
Windows Phone 7 tools
If you don’t have these and don’t want to see this project, you can just remove the Windows Phone 7 project from the solution.
Background
I’ve been working on Stuff v2; a movie, game, and books application. Its primary use case is, "I’m at the store and don’t remember if I have a particular movie, game, or book. I need to determine if I have it; if not, then check the online price and ratings before making the purchase."
Given the varied application clients and devices, ASP.NET forms authentication seemed like the natural choice for authentication for the website, MVC3 JSON endpoints, and WCF services.
The reason I have varied client software and devices is more of a learning experience than an application requirement. I have other applications I want to write that will need to access the application from all my devices.
When I started programming the WPF client, I ran into a stone wall with respect to WPF accessing WCF services that are secured by forms authentication. This blog post is about getting over that stone wall.
Identifying the Problem Space
At the end of the day, the problem that needs solving is managing the forms authentication cookie or ticket.
Managing means, that after authenticating, the client must be able to retrieve the ticket returned in the response and include it in future requests to secured resources.
As you will see, client API’s vary across scenarios not only in coding patterns but in complexity as well.
Regardless of which client is accessing resources that require forms authentication, the following steps outline the required workflow:
Log in
Cache the ticket returned in the response
Include the ticket in subsequent requests
Setting up Forms Authentication
When I created the ASP.NET MVC3 application, VariousClients.Web, I used the MVC3 Internet template with the Razor view engine. This template sets up forms authentication and provides a pretty good out-of-box SQL Express membership system for you.
The below snippet from the web.config shows a few required changes:
<authentication mode="Forms">
<!-- cookieless="UseCookies" is required by non-browser clients
to authenticate using forms authentication-->
<!-- production applications, change to requiresSSL="true"-->
<forms timeout="2880" cookieless="UseCookies" loginUrl="~/Account/LogOn"
requireSSL="false" />
</authentication>
Setting up the AuthenticationService
The System.Web.ApplicationServices.AuthenticationService is a built-in service that you can expose as a service endpoint on your website. This service exposes log in, log out methods for clients that access WCF endpoints requiring forms authentication. This service uses the membership provider defined in the web.config. After logging in, the service returns a ticket in the response, similar to forms authentication log in.
Adding the service is easy. First add a folder to the root of the website named, "Services". Into that folder, add a WCF service named Authentication.svc. Delete the generated service contract and code-behind files. Next replace the contents of the Authentication.scv file with the below code snippet.
<%@ ServiceHost Language="C#" Service="System.Web.ApplicationServices.AuthenticationService" %>
Now add the following to your web.config:
<system.web.extensions>
<scripting>
<webServices>
<!-- for production applications, change to requiresSSL="true"-->
<authenticationService enabled="true" requireSSL="false"/>
</webServices>
</scripting>
</system.web.extensions>
Rebuild your web application.
The Authentication.svc will now appear in the Add Service Reference dialog when adding service references in your client applications.
Read more: Karl on WPF
Babylon engine on code.msdn.microsoft.com
Posted by
jasper22
at
14:36
|

For my first post on my new blog, I’m proud to annonce the availability of a new sample on code.msdn.microsoft.com:
You can now get the full source of Babylon, the 3D engine I wrote to demonstrate the power of Silverlight 3D.
In a near future, I will create a new Codeplex entry for Babylon to allow the community to develop on it.
Read more: Eternal Coding
Silverlight 4, UserControls and the dreaded “name already exists in the tree”
Posted by
jasper22
at
14:33
|
I was doing some work with Silverlight the other week which involved using UserControls where the control named itself. That is, a situation such as;
<UserControl x:Name=”foo”>
<!—Content of control –>
</UserControl>
and, under unpredictable circumstances I was finding that I kept hitting a semi-random error when running my code which was something along the lines of;
“The name already exists in the tree: foo”
I spent an awfully long time on this and hence the blog post to try and perhaps save you some time in the future. I took long enough on it to come up with a simple repro scenario which looks something like this;

and so in words I have a ListBox which displays instances of UserControl1 and that control is just a StackPanel which contains 2 instances of UserControl2 and that control happens to name itself in its definition.
I found that if I ran this application a few times then sometimes it would work fine and sometimes it would fail with the dreaded exception and so I asked internally whether that was expected and it was confirmed as a bug in the Silverlight 4 runtime which has been fixed in Silverlight 5.
Read more: Mike Taulty's Blog
CloudCrack
Posted by
jasper22
at
14:32
|
CloudCrack is an NVIDIA GPU-accelerated cryptanalysis suite written in CUDA, NVIDIA's massively parallel concurrent programming language. CloudCrack contains custom CUDA multiprecision math libraries for storing a large target RSA modulus n in shared GPU memory, with each GPU core working as a parallel factoring process to break the target modulus.
There are currently two versions of CloudCrack: REVA, which implements the Greatest Common Denominator (gcd) function on the GPU itself; currently there is a bug in the Montgomery math routines in the REVA gcd however. REVB includes reduction sieve performance enhancements but with the gcd function implemented on the host CPU, which requires about 25% of the PCIe bus bandwidth to shuffle targets from the GPU to the host CPU for the gcd test. Although functional, this split GPU/CPU configuration is suboptimal for highly dense GPU clustering hardware that utilizes a shared PCIe bus across multiple GPU cards such as the Dell C410x PCIe Expansion Chassis. Ideally REVC will include all of the performance enhancements inherent to the REVB fork, with a GPU-localized gcd like the architecture of REVA..
Read more: CloudCrack
How SSL Works Using Public Key Cryptography
Posted by
jasper22
at
14:31
|
Everyone has been to a webpage where the page is secured using some sort of SSL encryption and the beginning of the URL has https instead of http. Most people have a basic idea of how it works and that the data you enter in a form is encrypted when sent to the server (e.g. Your credit card information). But how can the server decrypt this encrypted information if we can’t just blatantly send the encryption key to server with the risk of an intruder stealing the key and then decrypting our information? This is the problem that began the study of public key cryptography.
Public key cryptography is the exchange of a secret key from one party to another through public transactions when the secret key isn’t exchanged. So how does it work? Say we have two people, Bob and Sally, and Bob would like to send Sally a secret box that is protected by a combination lock. If Bob sends the box to Sally with his lock on it, he will have to send Sally the combination along with the box. Anyone can read the combination and unlock the box before Sally even receives the box. This will not work. But what if Sally sends Bob her lock, Bob locks the box and sends Sally the box with her lock on it. This would work and be secure because Bob does not know the combination to her lock and once he locks the box, he can not open it. Sally is the only one who knows combination and she will safely receive her box.
So how does this work when entering your credit card information on a webpage and clicking “Buy Now”? What is the algorithm behind all of this? Well SSL uses an algorithm called Diffie Hellman Key Exchange. This algorithm works as the following.
Say we have a client and a server trying to decide on an encryption key. The client and the server share two public values p and i. The value p is a prime number, only divisible by itself and one, that is a large number greater then 1000 and the value i is an integer that is less than p. The client and the server generate a private value r that is a large number greater then 1000 and is secret to only itself. Now the server will generate a key value a using the formula a = (i^r) mod p where mod is represented as modulus division. The server will send the value a to the client where the client will use the same formula to calculate its encryption key k. k = (a^r) mod p Now the client will do the same thing by calculating the key a using a = (i^r) mod p with its values and sending the a value to the server where the server uses the a value to calculate the encryption key using the formula k = (a^r) mod p . The value of k for both the server and the client will be the same. What the best part is is that it is almost impossible to generate the encryption key value k from using all of the public transfered values.
Read more: Shawn Janas
XAML И DATA BINDING: РАСШИРЕННЫЕ ВОЗМОЖНОСТИ РАЗМЕТКИ И СВЯЗЫВАНИЯ ДАННЫХ В SILVERLIGHT
Posted by
jasper22
at
14:30
|
КОММЕНТАРИИ В XAML
Начнем с самого простого, но не менее полезного. Комментарии – помогают читать код, отключать/включать временно куски кода при отладке.
<!-- Это простой комментарий -->
Это тоже простой комментарий, но только внутри закомментирован некий код:
<!--<Image Margin="0,0,0,0" Source="Untitled-2.png" Stretch="Fill" x:Name="BackgroundPng"/>—>
Однако, учтите, что вложенные комментарии сделать не получится. Например, в данном примере внутрь тега Grid вложен комментарий, такая разметка выдаст ошибку:
<Grid>
<!-- <TextBlock Text="{Binding Path=Name}" /> -->
</Grid>
На заметку
Для того чтобы закомментировать выделенный фрагмент кода, можно нажать сочетание клавиш CTRL+K+C, а для обратного эффекта нужно нажать CTRL+K+U.
ОПРЕДЕЛЕНИЕ КОНСТАНТ В XAML
В разметку XAML можно определять константы некоторых простых типов, например, string, int, bool. Для того чтобы можно было сделать требуется добавить namespace System в документ:
xmlns:sys="clr-namespace:System;assembly=mscorlib"
Теперь в разметке можно задать константы в Resources :
<UserControl.Resources>
<sys:String x:Key="OKText">OK</sys:String>
</UserControl.Resources>
Теперь это значение можно использовать по такому же принципу как и StaticResource:
<Button Content="{StaticResource OKText}" />
На заметку
Однако, по такому принципу нельзя определить в XAML константу типа DateTime.
ПЕРЕЧИСЛЕНИЕ В XAML
Довольно часто приходится применять в XAML перечисления (enum), которые в code-behind должны выглядеть следующим образом. Есть такое перечисление:
public enum MyLovelyEnum
{
Normal, Super, Simple
}
В code-behind использование было бы таким образом:
MyLovelyEnum Lovely = MyLovelyEnum.Normal | MyLovelyEnum.Super;
Так вот, в XAML данное определение будет выглядеть так:
Lovely="Normal,Super"
DATACONTEXT VS SOURCE (DATA BINDING)
В первую очередь хотелось бы показать применение свойства Source у объекта Binding. Дело в том, что можно использовать и свойство Source и DataContext.
<TextBox DataContext="{StaticResource productResource}" Text="{Binding Name}" />
Или вот второй вариант:
<TextBox Text="{Binding Name, Source={StaticResource productResource}}" />
Эффект от применения того или иного способа будет одинаковым, за исключением некоторого нюанса. Если используется DataContext, то его “действие” распространяется на все контролы расположенные ниже по иерархии в визуальном дереве (VisualTree). Такого не происходит, если использовать Source, то есть привязка, таким образом, происходит “точечно” или “целенаправленно”. Это оправдано, когда в контексте одной формы требуется использовать несколько поставщиков данных.
ELEMENTNAME BINDING
Название параметра ElementName в классе Binding говорит само за себя. Привязка осуществляется к именованному контролу. Вот простой пример привязки:
<StackPanel>
<TextBox Name="FirstTextBox" /><TextBox Name="SecondTextBox" Text="{Binding Text, ElementName=FirstTextBox}" />
</StackPanel>
Такая привязка приведет к тому, что при изменении текста в поле TextBox с именем FirstTextBox незамедлительно изменится текст в у контрола с именем SecondTextBox. Обратного действа не произойдет, потому что по умолчанию такой важный параметр как Mode у Binding имеет значение OneWay (в одну сторону). Но если установить значение этого параметра TwoWay, то при изменении текста в любом из контролов, второй тут же получит измененное значение.
Еще одним немаловажным свойством, которое чаще всего пишется, но подразумевается по умолчанию – это свойство Path. Разметка типа:
Text="{Binding Text, ElementName=FirstTextBox}"
и
Text="{Binding Path=Text, ElementName=FirstTextBox}"
Read more: МУЗЕЙ ЮМОРА - НАЙДИ ЛУЧШЕЕ!
Tornado
Posted by
jasper22
at
14:28
|

Tornado is an open source version of the scalable, non-blocking web server and tools that power FriendFeed. The FriendFeed application is written using a web framework that looks a bit like web.py or Google's webapp, but with additional tools and optimizations to take advantage of the underlying non-blocking infrastructure.
The framework is distinct from most mainstream web server frameworks (and certainly most Python frameworks) because it is non-blocking and reasonably fast. Because it is non-blocking and uses epoll, it can handle thousands of simultaneous standing connections, which means it is ideal for real-time web services. We built the web server specifically to handle FriendFeed's real-time features — every active user of FriendFeed maintains an open connection to the FriendFeed servers. (For more information on scaling servers to support thousands of clients, see The C10K problem.)
See the Tornado documentation for a detailed walkthrough of the framework.
Download and install
Automatic installation: Tornado is listed in PyPI and can be installed with pip or easy_install. If you do not already have libcurl installed you may need to install it separately; see the prerequisites section below. Note that the source distribution includes demo applications that are not present when Tornado is installed using pip or easy_install
Read more: Tornado
What is difference between jQuery and Microsoft Ajax? When do you use Ajax and When do you use jQuery? What is the significance of each?
Posted by
jasper22
at
14:26
|
jQuery is like the ASP.NET AJAX Client Framework (MicrosoftAjax.js), with selectors, DOM selections/ manipulations, plug-ins, and better animation support. jQuery is more powerful than MS AJAX on the client side due to its light weight nature . This is the reason Microsoft integrated jQuery with Visual Studio. JQuery is integrated for post VS versions 2008, no explicit download of jQuery file is required for the versions above VS2010.
Ajax is a Technology for Asynchronous Data Transferring. AJAX is a technique to do an XMLHttpRequest from a web page to the server and send or receive data to be used on the web page.
jQuery can be used
If you love and comfortable with JavaScript
Most interaction is client-side only
If a custom solution is required
For stunning look and feel of client side UI
If animations ,DOM Selection are required
Ajax can be used
If you are using ASP.NET & VS
When server side Integration is required.
If you need json and WCF Support
Read more: Beyond Realtional
כיצד לדבג קוד שרץ תחת IIS - צעד אחר צעד
Posted by
jasper22
at
14:25
|
במידה ואתם מריצים קוד ב – Visual Studio זה לא משנה מה בחרתם במאפיינים של הפרויקט האם לעבוד עם ה – server של visual studio או לעבוד מול IIS, תוכלו לדבג את הקוד.
אבל במידה והאפליקציה נמצא ב – IIS והרצתם אותה דרך גלישה בדפדפן ועדיין אתם רוצים לדבג, זה אפשרי בכמה שלבים פשוטים. (לקריאה על Remote Debugging)
ראשית פתחו visual studio. ופתחו את הפרויקט (אם יש לכם אותו – אם אין לכם עדיין אפשר לדבג אם יש לכם את קבצי ה – pdb אבל זה כבר נושא לפוסט אחר)
בחרו ב – Attach to Process (בדרך כלל תחת tools או לחיצה של ctrl + alt + p)
תקבלו את החלון הבא

Read more: שלמה גולדברג (הרב דוטנט)
Sony: All PSN users may have been hacked
Posted by
jasper22
at
14:25
|
Security alert as millions of PlayStation Network users are told of ‘malicious’ attack
An illegal hack into the PlayStation Network may have exposed the personal data of every single user, Sony has warned.
In an admission of the sheer enormity of the security alert, Sony said “our investigation indicates that all PlayStation Network/ Qriocity accounts may be affected”.
Earlier, the company said a “malicious” hack has compromised key info of PlayStation Network users – including credit card data.
Now the platform holder has revealed the attack could put every single account at risk.
In a notice pubished on the PlayStation Blog, the company was asked if all user information had been compromised.
“In terms of possibility, yes,” the company said.
Sony announced in January this year that over 69 million people have registered a PlayStation Network account.
Read more: Develop
SwitchSvnVersion
Posted by
jasper22
at
13:31
|
SwitchSvnVersion created by Steve Dunn.
A command-line tool to modify Visual Studio projects. You can use to change the target platforms and target .NET Frameworks. You can also use it to target different versions of Visual Studio, e.g. from 2008 to 2010.
Released by Steve under the WTFPL license: http://sam.zoy.org/wtfpl/COPYING
Read more: GitHub
Using the Tika Java Library In Your .Net Application With IKVM
Posted by
jasper22
at
12:41
|
This may sound scary and heretical but did you know it is possible to leverage Java libraries from .Net applications with no TCP sockets or web services getting caught in the crossfire? Let me introduce you to IKVM, which is frankly magic:
IKVM.NET is an implementation of Java for Mono and the Microsoft .NET Framework. It includes the following components:
- A Java Virtual Machine implemented in .NET
- A .NET implementation of the Java class libraries
- Tools that enable Java and .NET interoperability
Using IKVM we have been able to successfully integrate our Dovetail Seeker search application with the Tika text extraction library implemented in Java. With Tika we can easily pull text out of rich documents from many supported formats. Why Tika? Because there is nothing comparable in the .Net world as Tika.
This post will review how we integrated with Tika. If you like code you can find this example in a repo up on Github.
Compiling a Jar Into An Assembly
First thing, we need to get our hands on the latest version of Tika. I downloaded and built the Tika source using Maven as instructed. The result of this was a few jar files. The one we are interested in is tika-app-x.x.jar which has everything we need bundled into one useful container.
Next up we need to convert this jar we’ve built to a .Net assembly. Do this using ikvmc.exe.
tika\build>ikvmc.exe -target:library tika-app-0.7.jar
Unfortunately, you will see tons of troublesome looking warnings but the end result is a .Net assembly wrapping the Java jar which you can reference in your projects.
Using Tika From .Net
IKVM is pretty transparent. You simply reference the the Tika app assembly and your .Net code is talking to Java types. It is a bit weird at first as you have Java versions of types and .Net versions. Next you’ll want to make sure that all the dependent IKVM runtime assemblies are included with your project. Using Reflector I found that the Tika app assembly referenced a lot of IKVM assemblies which do not appear to be used. I had to figure out through trial and error which assemblies where not being touched by the rich document extractions being done. If need be you could simple include all of the referenced IKVM assemblies with your application. Below I have done the work for you and eliminated all references to all the IKVM assemblies which appear to be in play.
Read more: DovetailConnect Blog
Real World Mapping with the Kinect
Posted by
jasper22
at
12:24
|
A real-time data capture application for generating real-world coloured point clouds with the Xbox Kinect and GPS capable Android phone.
This is very immature and hacky - done entirely as a proof-of-concept. Please don't expect anything at all from this. No warranty of any kind is expressed or implied.
Some of the initialisation code used in the application is courtesy of a tutorial on the C# libfreenect wrapper at SwitchOnTheCode.
The project uses libfreenect and the .NET wrapper for same, along with OpenTK for the Matrix maths and Proj.NET for the spatial transforms.
...
...
Putting those together, one can take the depth image from the Kinect and turn it in to a metric point cloud with real distances. Then, those points can be projected back to the RGB camera centre to determine which RGB pixel corresponds to each depth point, and hence arrive a colour for each point in the cloud. This lets the surfaces captured in the image appear textured. With a bit of coding I came up with this:

Read more: KinectMapper
SimpleBrowser
Posted by
jasper22
at
12:19
|
SimpleBrowser is a lightweight, yet highly capable browser automation engine designed for automation and testing scenarios. It provides an intuitive API that makes it simple to quickly extract specific elements of a page using a variety of matching techniques, and then interact with those elements with methods such as Click(), SubmitForm() and many more. SimpleBrowser does not support JavaScript, but allows for manual manipulation of the user agent, referrer, request headers, form values and other values before submission or navigation.
Requirements
.Net Framework 4.0
Features
Multiple ways of locating and interacting with page elements
A highly permissive HTML parser that converts any HTML, no matter how badly formed, to a valid XDocument object
Automatic cookie/session management
Extensive logging support with attractive and comprehensive html log file output to make it easy to identify problems loading and automating browsing sessions
Read more: SimpleBrowser
Read more: XBrowser
OutlookGnuPG
Posted by
jasper22
at
12:06
|
GnuPG addin for Outlook 2007
Welcome to the OutlookGnuPG wiki!
OutlookGnuPG is a fork of the original GPG in Outlook 2007 – OutlookGnuPG by David Cumps.
Given David had no time to pursue the development we, a colleague and myself, decided to put our hands in the source code to solve minor issues we encountered in our configuration:
- better parsing of gpg —list-key to support multiple UIDs and subkeys
- support for a default domain name for X.400 addresses
- fix overflow issue for large gpg output (e.g. public keyring is sth like > 160 keys)
See also the ChangeLog file.
Please note, the visual studio project is downgraded to Visual Studio 2005 (version 9.0) and makes use of the Visual Studio 2005 Tools for the Office System SE Solutions
Read more: GitHub
Advanced.NHibernate
Posted by
jasper22
at
11:53
|
Samples of advanced NHibernate usage
Read more: GitHub
MonoTorrent
Posted by
jasper22
at
11:43
|
MonoTorrent is a cross platform and open source implementation of the BitTorrent protocol. It supports many advanced features such as Encryption, DHT, Peer Exchange, Web Seeding and Magnet Links.
Notable features include:
- Encryption
- Dht
- Peer Exchange (uTorrent style)
- Local Peer Discovery
- Web Seeding (getright style)
- Magnet Links / Metadata download
- IPV6
- FAST Extensions
- Sparse files (NTFS file system)
- Multi-tracker torrents
- Compact tracker responses
- IP Address white listing / black listing
- Fast Resume
- Initial Seeding (super seeding)
- Selective downloading
- Prioritised downloading
- Full bittorrent tracker
- Dynamic request queue size
- Memory Cache
- Endgame mode
- Per torrent and global rate limiting
- Individual file relocation
Source code: http://github.com/mono/monotorrent
Read more: MonoTorrent
Android NDK
Posted by
jasper22
at
11:17
|
The Android NDK is a companion tool to the Android SDK that lets you build performance-critical portions of your apps in native code. It provides headers and libraries that allow you to build activities, handle user input, use hardware sensors, access application resources, and more, when programming in C or C++. If you write native code, your applications are still packaged into an .apk file and they still run inside of a virtual machine on the device. The fundamental Android application model does not change.
Using native code does not result in an automatic performance increase, but always increases application complexity. If you have not run into any limitations using the Android framework APIs, you probably do not need the NDK. Read What is the NDK? for more information about what the NDK offers and whether it will be useful to you.
The NDK is designed for use only in conjunction with the Android SDK. If you have not already installed and setup the Android SDK, please do so before downloading the NDK.
Read more: Android Developer
jni4net
Posted by
jasper22
at
10:55
|
bridge between Java and .NET (intraprocess, fast, object oriented, open-source)
How it works

Using reflection we grab public method signatures for core classes of .NET and Java and generated proxy classes for the other side.
We have .NET version of JNI API.
We use JNI to forward the call from .NET proxies to methods on real Java objects.
We use JNI to register .NET implementation of native methods of Java proxies to forward call to methods on real .NET objects.
Features
Intraprocess - it means that both VMs are in same process. Any call uses same thread and same stack for both environments. It's relatively fast.
Proxies - we use proxies which look like and behave like the real/original object. Marshaled by reference except for primitive types and arrays.
Garbage collected - if you don't create cycle between VMs heaps, the proxies and instances are collected and released properly.
Proxygen - tool to wrap your own library. Works with reflection, so you need just .jar or .dll, and proxygen config file. You could wrap most CLR or JVM classes.
Core - core classes of JDK and .NET framework are already included in jni4net. Using that for reflection and invocation across the boundary is possible.
Samples - are included with the binaries. See ReadMe.txt in directories
Troubleshooting - use knowledge base or ask people
Platforms - at the moment only Windows 32 and 64 bits. CLR 2.0 and CLR 4.0. JRE 1.5 and above.
License - opensource, GPL tools and LGPL runtime
Status - currently Alpha quality. Lot of work ahead, lot of ideas, lot of missing features, looking forward to community feedback.
Contact - use mailing group or talk to pavel.savara@gmail.com
.NET/C# to Java Hello World -> Full sample
using net.sf.jni4net;
public class Program
{
private static void Main()
{
Bridge.CreateJVM(new BridgeSetup());
java.lang.System.@out.println("Greetings from C# to Java world!");
}
}
Read more: jni4net
Psscor4 Managed-Code Debugging Extension for WinDbg
Posted by
jasper22
at
10:05
|
Overview
Psscor4 can help you diagnose high-memory issues, high-CPU issues, crashes, hangs and many other problems that might occur in a .NET application; in scenarios involving live processes or dump files.If you are familiar with SOS.dll, the managed-debugging extension that ships with the .NET Framework, Psscor4.dll provides a superset of that functionality. Most of the added functionality helps you identify issues in ASP.NET.For example, Psscor4 provides the ability to view:•managed call stacks (with source mappings)•managed exception information•what types are in the managed heap and their reference chain•which ASP.NET pages are running on which thread•the contents of the ASP.NET cache•and much more.
Read more: MS Download
Попробуй Ubuntu без установки
Posted by
jasper22
at
10:04
|
«Попробуй прежде чем купить» – это отличное предложение которое понравится любому человеку который только собирается попробовать что то новое. Canonical пошла на встречу новым пользователям, которые только задумываются о переходе на Ubuntu и дает им возможность «попробовать прежде чем загрузить».
Canonical предлагает всем желающим тест-драйв Ubuntu 11.04 в своем облаке без необходимости загружать и инсталлировать систему себе на компьютер. Используя аккаунт на launchpad вы сможете авторизироваться и попробовать новую версию уже сейчас. Каждый пользователь получает в свое распоряжение 15 минут, это конечно немного, но что бы оценить основные преимущества и недостатки вполне достаточно.
Read more: Technovzor
Read more: Ubuntu online
Burp Suite
Posted by
jasper22
at
09:16
|
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun.
Burp Suite contains the following key components:
- An intercepting proxy, which lets you inspect and modify traffic between your browser and the target application.
- An application-aware spider, for crawling content and functionality.
- An advanced web application scanner, for automating the detection of numerous types of vulnerability.
- An intruder tool, for performing powerful customized attacks to find and exploit unusual vulnerabilities.
- A repeater tool, for manipulating and resending individual requests.
- A sequencer tool, for testing the randomness of session tokens.
- The ability to save your work and resume working later.
- Extensibility, allowing you to easily write your own plugins, to perform complex and highly customized tasks within Burp.
Burp is easy to use and intuitive, allowing new users to begin working right away. Burp is also highly configurable, and contains numerous powerful features to assist the most experienced testers with their work.
Read more: Burp Suite
New in Labs: Background Send
We’re always looking for ways to make Gmail faster. One of the most common delays happens after you hit that “Send” button, when you’re waiting patiently for a couple seconds for Gmail to send your message. If you send a lot of email, that can add up to a lot of lost time.
To help give you that time back, there’s a new feature in Gmail Labs called Background Send. Once you turn it on from the Labs tab in Settings, you can get on with what you’re doing while Gmail quietly sends off your mail in the background. You can keep reading your inbox, compose new messages, chat with people — all the things you’d usually do. You can even send more than one message in the background at the same time.

Read more: GMail blog
JSPP – Morph C++ Into Javascript
Posted by
jasper22
at
17:05
|
C++ has a new standard called C++0x (Wikipedia, Bjarne Stroustrup) that includes many interesting features such as Lambda, For Each, List Initialization ... Those features are so powerful that they allow to write C++ as if it was Javascript.
The goal of this project is to transform C++ into Javascript. We want to be able to copy & paste Javascript into C++ and be able to run it. While this is not 100% feasible, the result is quite amazing.
This is only a prototype. In about 600 lines of code we manage to make the core of the Javascript language.
Read more: Vjeux
Google offers $2.05 mn for Modu’s patents
Posted by
jasper22
at
16:54
|
Google is offering US$2.05 million for the patents of failed mobile phone developer Modu.
Google submitted the offer to the Tel Aviv District Court, which is handling Modu’s liquidation.
Google topped the previous offer of US$1.46 million made by Kensington Technology in late March. In December 2010, the court appointed a receiver for Modu, founded by Dov Moran, and the company’s employees petitioned for its liquidation.
The company registered over 100 patents in its three years of operations, and they constitute its main asset.
Read more: Wireless federation
Steve Jobs on iOS Location Issue: 'We Don't Track Anyone'
Posted by
jasper22
at
16:44
|
There has obviously been a lot of discussion about last week's disclosure that iOS devices are maintaining an easily-accessible database tracking the movements of users dating back to the introduction of iOS 4 a year ago. The issue has garnered the attention of U.S. elected officials and has played fairly heavily in the mainstream press.
One MacRumors reader emailed Apple CEO Steve Jobs asking for clarification on the issue while hinting about a switch to Android if adequate explanations are not forthcoming. Jobs reportedly responded, turning the tables by claiming both that Apple does not track users and that Android does while referring to the information about iOS shared in the media as "false".
Q: Steve,
Could you please explain the necessity of the passive location-tracking tool embedded in my iPhone? It's kind of unnerving knowing that my exact location is being recorded at all times. Maybe you could shed some light on this for me before I switch to a Droid. They don't track me.
A: Oh yes they do. We don't track anyone. The info circulating around is false.
Sent from my iPhone
As is Jobs' usual style, his brief comments provide little detail or information to support his claims, and his vagueness leaves things rather open to interpretation.
Read more: MacRumors.com
Теория цвета для web дизайна и не только
Posted by
jasper22
at
14:29
|


Цветовая палитра всегда оказывала мощное воздействие на восприятие человека. Одни цвета могут успокаивать, другие наоборот, побуждать к действию. Долгие годы ученые занимаются исследованиями в этой области. И никто не будет возражать, что многие вещи и предметы мы воспринимаем в зависимости от окраски.
Сайт - это своего рода произведение искусства. А по этому его цветовое решение очень важно. Как и художнику, вэб-дизайнеру нужно знать основные принципы по которым строятся цветовые гаммы. Ведь от понимания этого вопроса, может зависеть восприятие людьми той информации, которую нужно преподать.
В этой статье мы постараемся объяснить некоторые важные моменты в подборе цветов. Приведем примеры эффективного использования цвета и дадим полезные советы, которые, надеемся, вам пригодятся в работе.
Цветовая теория и умение сочетать цвета
Для некоторых дизайнеров создать цветовую палитру сайта очень просто. Эти люди отличаются отличным вкусом и хорошо чувствуют цвет. Но таких людей не много. Для большинства, это очень сложная задача, требующая сил и времени. Для тех, кому трудно в подборе, будет полезно узнать о цветовом круге.
Еще в 1666 году Исаак Ньютон обосновал теорию света, которая является основополагающей в развитии всего, что связанно с оптикой. И тогда же он изобрел цветовой круг. Эти открытия он сделал после того как сумел доказать сложность света, который состоит из спектра. А мы видим его таким благодаря явлению дисперсии. Чтобы повторить опыт Ньютона достаточно взять стеклянную призму и сквозь нее посмотреть. Тогда весь спектр станет хорошо различим.
Read more: fresh2L
Silverlight 5.0: Custom Markup Extensions and Roles
Posted by
jasper22
at
12:31
|
Starting from Silverlight 5.0 you can create custom Markup Extensions and this is an interesting feature to easily encapsulate some logic and make it easy to be applied to properties in the XAML markup. Until now you could only use a few extensions to apply resources (StaticResource), make databinding (Binding) and connect properties with parts of a template (TemplateBinding) but now, implementing a really simple interface you can build your own.
public interface IMarkupExtension<out T> where T: class
{
T ProvideValue(IServiceProvider serviceProvider);
}
Using this interface you can specify the type to which the markup extension can be applied (the generic type T) but if you do not need a control about this type you can extend the MarkupExtension abstract class that is like you are extending IMarkupExtension<object>.
Inside the ProvideValue method there is the whole logic of the extension and using the IServiceProvider passed by the runtime you can get access to three services that let you get some informations about the markup where the extension is located.
IRootObjectProvider: provide a reference to the Root object of the VisualTree which the element is part of
IXamlTypeResolver : is able to resolve the name of the tags in the markup to the corresponding type.
IProvideValueTarget : gets a reference to the property and the elements which the markup extension is assigned
To retrieve an instance of this services you can use the GetService method on the IServiceProvider instance.
IProvideValueTarget target = (IProvideValueTarget)serviceProvider.GetService(typeof(IProvideValueTarget));
Read more: Silverlight Playground
Transparency using Alpha Channel in XAML Silverlight
Posted by
jasper22
at
12:29
|
Introduction
In Silverlight we can apply transparency either by using Alpha Channel or Opacity. In this post you will learn how to apply trnsparency using Alpha Channel.
As I have discussed in my previous post titled 'Alpha Channels in XAML Silverlight' about the Alpha Chennel. Take a little look here too.
In Alpha Channel we just add additional code as first element in existing hexadecimal color code. The additional element specifies the transparency of a color from 0 (full transparent) to 255 (full opaque). For example, if we wish to apply 'Blue' color then we'll use its hexadecimal color code as '#0000FF'. Now to apply the transcarency in this color we add additional element (from 0 to 255 (FF). FF is default means no transparency) as '#FF0000FF' (no transparency). Let's take a look at program.
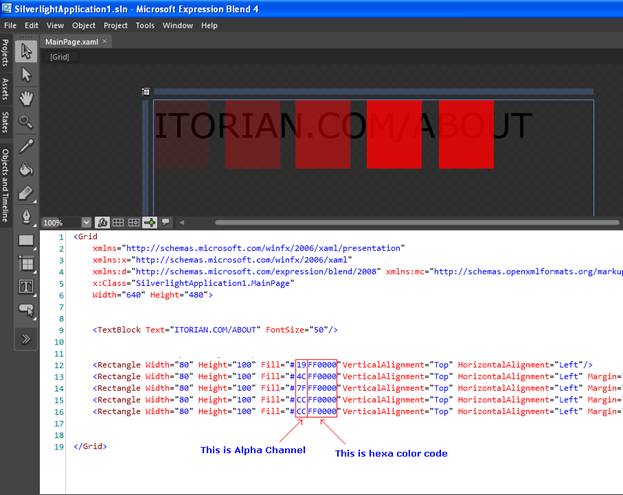
In above screenshot, I marked out the Alpha Channel and normal HTML based hexa color code.
In above example, I have used a textblock and 5 rectangles overlapped on text but to show the transparency I have used alpha channel there.
XAML Code
<Grid
xmlns:d="http://schemas.microsoft.com/expression/blend/2008" xmlns:mc="http://schemas.openxmlformats.org/markup-compatibility/2006" mc:Ignorable="d"
x:Class="SilverlightApplication1.MainPage"
Width="640" Height="480">
<!--TextBlock with text-->
<TextBlock Text="ITORIAN.COM/ABOUT" FontSize="50"/>
<!--4 circle with partially transparent background-->
<Rectangle Width="80" Height="100" Fill="#19FF0000" VerticalAlignment="Top" HorizontalAlignment="Left"/>
<Rectangle Width="80" Height="100" Fill="#4CFF0000" VerticalAlignment="Top" HorizontalAlignment="Left" Margin="104,0,0,0"/>
Read more: C# Corner
Forget 42, –1 is My New Answer to Life
Posted by
jasper22
at
11:22
|
I’ve just stumbled upon the next code statement – Thread.Sleep(-1). It left me wondering what was happening there since MSDN tells you nothing about a –1 value for the milliseconds parameter:
“The number of milliseconds for which the thread is blocked. Specify zero (0) to indicate that this thread should be suspended to allow other waiting threads to execute. Specify Infinite to block the thread indefinitely.“ – System.Threading.Thread.Sleep, MSDN
To check that out, I opened the IronRuby interactive console and filled in System::Threading::Thread.Sleep(-1) and hit Enter just to find out that this call blocks the thread indefinitely. Could it be? –1 is Infinite?
Reflector to our aid! oh wait, RedGate now charges money for it and had planted a time bomb inside the free version which made it stop working. grrrr
ILSpy to our aid! (I highly recommend ILSpy as a Reflector alternative… very similar, free, oss… great community effort!)
Anyway, ILSpy proved my concerns:

Read more: Ironshy
AppLocker – Application Locker–חלק ראשון
Posted by
jasper22
at
11:21
|
שלום לכולם,
כאן דן ויזנפלד מצוות התמיכה של Microsoft.
לאלו מאתנו שאוהבים להישאר בשליטה מלאה, השיקה Microsoft את בקרת הורים (Parental Controls) שמאפשרת לנו לנטר ולבקר את הפעילויות שעושים משתמשים אחרים (לרוב הילדים) במחשב, ובין היתר לאפשר או לאסור הפעלת תוכנות ומשחקים.
עם זאת, למשתמשים בגרסאות Ultimate ו-Enterprise של מערכת ההפעלה Windows 7, מוצעת אפשרות נוספת, מתקדמת יותר, הנוגעת לעולם בקרת השימוש במחשב – כלי ה-AppLocker.
זהו חלקו הראשון של הפוסט בנושא AppLocker. מדובר בכלי חדש למניעת התקנה וטעינה של יישומים ותוכנות, המגיע מובנה במערכת ההפעלה. ב-AppLocker משתמשים לרוב מנהלי רשת, מאחר והוא מציע אפשרויות מתקדמות שאינן נדרשות למשתמש הביתי (שכאמור ייהנה ממנגנון בקרת ההורים או Live Family Safety).
"אז דן.., ספר מה חדש"
בשמחה. בעוד שבבקרת ההורים יכולנו לחסום את היכולת של תכנית מסוימת להיטען, נדרשנו בכל פעם להוסיף כללי חסימה חדשים בעת התקנת תכנית חדשה.
לדוגמא (וסביר מאוד להניח שתזדהו איתה):
הבן התקין את GTA 3 (Grand Theft Auto) במחשב המשפחתי. לאחר שבוע או שניים הבחנתם כי לא ניתן להפריד אותו מן המחשב. במסדר בושה שערכתם, גיליתם כי בזמנו החופשי – הבן גונב מכוניות (במשחק כמובן). אז הפעלתם את מנגנון בקרת ההורים, ומנעתם ממנו לאלתר כניסה נוספת למשחק.
אבל מה יקרה כאשר הוא יתקין גרסה אחרת של אותו המשחק (GTA 4 )? הכלל שיצרתם לגבי GTA 3 כבר לא יהיה תקף לגביו.
בדוגמאות בעלות אותו רעיון (אם כי בנסיבות אחרות - אני מקווה) נתקלים גם מנהלי רשת בחברות וארגונים גדולים.
הפתרון שמציע ה-AppLocker הוא פשוט: חסימת תכניות על פי מפתח (יצרן) המוצר. מה הכוונה? בדוגמתנו, לא רק שלא ניתן יהיה להפעיל את GTA 3, לא ניתן גם יהיה להפעיל שום גרסה של המשחק שיצאה או שתצא אי פעם (רק לשם הבהרה, מדובר במשחק מצוין ששימש אותי רק לצרכי הדגמה).
יותר מזה - ה-AppLocker מאפשר גם למנוע מלכתחילה את ההתקנה של אותן תכניות.
"אז איך עושים את זה?"
אסביר כיצד ניתן להגיע לממשק הניהול של AppLocker (כמובן שחייבים להיות ברמת הרשאות של מנהל המחשב), ומהן האפשרויות העומדות בפניכם:
1. לוחצים על Start (התחל) ולאחר מכן בוחרים ב-Control Panel (לוח בקרה).

Read more: Microsoft Support Blog Part 1, Part 2
SQL SERVER – How to ALTER CONSTRAINT
Posted by
jasper22
at
11:20
|
After reading my earlier blog post SQL SERVER – Prevent Constraint to Allow NULL. I recently received question from user regarding how to alter the constraint.
No. We cannot alter the constraint, only thing we can do is drop and recreate it.
Here is the CREATE and DROP script.
CREATE DATABASE TestDB
GO
USE TestDB
GO
CREATE TABLE TestTable (ID INT, Col1 INT, Col2 INT)
GO
-- Create Constraint on Col1
ALTER TABLE TestTable ADD CONSTRAINT CK_TestTable_Col1
CHECK (Col1 > 0)
GO
-- Dropping Constraint on Col1
ALTER TABLE TestTable DROP CONSTRAINT CK_TestTable_Col1
GO
Read more: Journey to SQLAuthority
FxCop Integrator for Visual Studio 2010
Posted by
jasper22
at
11:12
|
New Feature
Code Analysis on Build
This is like "Code Analysis on Build" of Visual Studio 2010 Ultimate or Premium. This feature allow you to perform code analysis automatically when you build a project.
FxCop Dictionary Support
FxCop contains some naming rules and supports "Custom Dictionary" to allow you to customize them. Ver1.3.0 supports to pass a dictionary file to FxCop. In addition, ver1.3.0 contains FxCop dictionary editor.
Bug Fix
Silverlight Project Support
Ver1.2.0 couldn't analyze a Silverlight project because silverlight assemblies are located in %PROGRAMFILES%\Reference Assemblies\Microsoft\Framework\Silverlight\vx.x not GAC and FxCop Integrator cound't specify reference assemblies to FxCop. This problem was solved in ver1.3.0.
FxCop 1.36 Support
In ver1.2.0, you can't analyze your code with FxCop 1.36 if you specify Ruleset. Because FxCop Integrator 1.2.0 passes /rs option to FxCop whether it is ver10.0 or not. /rs is the command line option to specify Ruleset path. It is supported from FxCop 10.0. So if you specify FxCopCmd.exe of FxCop 1.36 to "FxCopCmd Path", FxCopCmd.exe fails to analyze. This problem was solved in ver1.3.0.
Read more: Codeplex
Subscribe to:
Comments (Atom)


