
ownCloud

ownCloud gives you universal access to your files through a web interface or WebDAV. It also provides a platform to easily view & sync your contacts, calendars and bookmarks across all your devices and enables basic editing right on the web.
Discover more …
Installation has minimal server requirements, doesn’t need special permissions and is quick. ownCloud is extendable via a simple, but powerful API for applications.
Developer info …
Support and Services for companies is provided by ownCloud, Inc. Please visit owncloud.com for more information.
Read more: ownCloud
QR: 
Springpad
Posted by
jasper22
at
17:42
|
Springpad is a free app that makes it quick and easy to take notes and save anything you want to remember - from notes and tasks to products, places, movies, recipes and more.Read more: Springpad
QR:
30+ Free HTML Email Newsletter Templates
Posted by
jasper22
at
17:34
|


Email newsletters play a significant role when it comes to interacting with your customers and keeping them up to date with all the latest happening in your company. The design and layout of your newsletter is very important for grabbing the attention of your customers instantly . Beautiful and interesting designs will obvious attract customers and spread information about your product or service. A good HTML Email Templates, which have handy modification options, are always liked by readers as they not heavy for the reader’s Inbox. So today we have a list of Some Awesome Free HTML Email Newsletter Templates to make your Email newsletter stand out from the rest. Use any of these Free HTML Email Templates on this effective and cost effective marketing tool for keeping in touch with your clients and subscribers, and for spreading information about your services. Check them out and pick the one you like the best! Read more: Smashing Hub
QR:
CentOS 6.2 Release
Posted by
jasper22
at
16:24
|
Welcome to the CentOS 6.2 release. CentOS is an Enterprise-class Linux Distribution derived from sources freely provided to the public by our Upstream OS Provider (UOP)1.CentOS conforms fully with the upstream vendor's redistribution policy and aims to be 100% binary compatible. (CentOS mainly changes packages to remove upstream vendor branding and artwork.) We have decided not to follow the UOP's usage of Installation Codes. All 'channels' are available to the System Administrator at time of installation.Similar to the practice of the upstream vendor, there is no supported path to 'upgrade' an installation of a prior major CentOS release (presently CentOS 5 or CentOS 4) to a new major release. This is not a CentOS imposed limitation, but rather reflects the upstream's approach on this matter. People who feel adventuresome and want to experiment are reminded to take and test backups first. As a note to people who attempt the upgrade in spite of this warning, such as by the unsupported upgradeany option from the media install command line, please note that you will need to manually retrieve the current centos-release package, manually do a rpm -e --nodeps removal of the prior centos-release package, and then manually install the CentOS 6 centos-release package, before yum can have any chance of working properly. The continuous release ( CR ) repository makes generally available packages that will appear in the next point release of CentOS, on a testing and hotfix basis until formally released.Please read through the other sections before trying an install or reporting an issue. 3. Install Media and sha1sumsha1sum i386:
ad741581b3d3969bcf867cf1e47160902c8876f6 CentOS-6.2-i386-bin-DVD1.iso
6131d4c8ca2be77a25eaf1c61f94c7500786e683 CentOS-6.2-i386-bin-DVD2.iso
58cddfb2a6bd5094687a36f9fe94ce82967a4af0 CentOS-6.2-i386-LiveCD.iso
6c891e23c959787931fd2eb472211afd51709aa5 CentOS-6.2-i386-LiveDVD.iso
353d7e070a4cfc34148f9610b05cf1c55ad4fa57 CentOS-6.2-i386-minimal.iso
02444d6984089d9fc16ca989781482c8202357f0 CentOS-6.2-i386-netinstall.iso sha1sum x86_64:
d97377c83fab7493dbd1c2e04dab29c8ba6cd351 CentOS-6.2-x86_64-bin-DVD1.iso
7eac42c403725891b53cd899f0ef7560dc3a9d72 CentOS-6.2-x86_64-bin-DVD2.iso
0c329da3db427c3279d44f15a57ba85341d12197 CentOS-6.2-x86_64-LiveCD.iso
086f102c4c3ee228c5663cbaa2f1d6bf2edf5c4b CentOS-6.2-x86_64-LiveDVD.iso
10b26ce414af86be26f3a47dcc76d8f81e333979 CentOS-6.2-x86_64-minimal.iso
4858a8870cc5048876edd51dead25b9c718fcfbe CentOS-6.2-x86_64-netinstall.iso
Read more: CentOS
QR:
ad741581b3d3969bcf867cf1e47160902c8876f6 CentOS-6.2-i386-bin-DVD1.iso
6131d4c8ca2be77a25eaf1c61f94c7500786e683 CentOS-6.2-i386-bin-DVD2.iso
58cddfb2a6bd5094687a36f9fe94ce82967a4af0 CentOS-6.2-i386-LiveCD.iso
6c891e23c959787931fd2eb472211afd51709aa5 CentOS-6.2-i386-LiveDVD.iso
353d7e070a4cfc34148f9610b05cf1c55ad4fa57 CentOS-6.2-i386-minimal.iso
02444d6984089d9fc16ca989781482c8202357f0 CentOS-6.2-i386-netinstall.iso sha1sum x86_64:
d97377c83fab7493dbd1c2e04dab29c8ba6cd351 CentOS-6.2-x86_64-bin-DVD1.iso
7eac42c403725891b53cd899f0ef7560dc3a9d72 CentOS-6.2-x86_64-bin-DVD2.iso
0c329da3db427c3279d44f15a57ba85341d12197 CentOS-6.2-x86_64-LiveCD.iso
086f102c4c3ee228c5663cbaa2f1d6bf2edf5c4b CentOS-6.2-x86_64-LiveDVD.iso
10b26ce414af86be26f3a47dcc76d8f81e333979 CentOS-6.2-x86_64-minimal.iso
4858a8870cc5048876edd51dead25b9c718fcfbe CentOS-6.2-x86_64-netinstall.iso
Read more: CentOS
QR:
Mono in 2011
Posted by
jasper22
at
12:13
|
This was a very interesting year for Mono, and I wanted to capture some of the major milestones and news from the project as well as sharing a bit of what is coming up for Mono in 2012.I used to be able to list all of the major applications and great projects built with Mono. The user base has grown so large that I am no longer able to do this. 2011 was a year that showed an explosion of applications built with Mono. In this post I list a few of the high profile projects, but it is by no means an extensive list. There are too many great products and amazing technologies being built with Mono, but a comprehensive list would take too long to assemble.
XamarinThe largest event for Mono this year was that the team working on Mono technologies at Novell was laid off after Novell was acquired.We got back on our feet, and two weeks after the layoffs had taken place, the original Mono team incorporated as Xamarin. Xamarin's goal is to deliver great productivity and great tools for mobile developers. Our main products are Mono on iOS and Mono on Android.These products are built on top of the open source Mono project and the MonoDevelop project. We continue to contribute extensively to these two open source projects. Launching Xamarin was a huge effort for all of us.Xamarin would not have been possible without our great customers and friends in the industry. Many people cared deeply about the technology and helped us get up and running. In July, we announced an agreement with Attachmate that ensured a bright future for our young company.A couple of days later, we were ready to sell the mobile products that had been previously developed at Novell, and we started to provide all existing Novell customers with ongoing support for their Mono-based products. Half a year later, we grew the company and continued to do what we like the most: writing amazing software.Meanwhile, our users have created amazing mobile applications. You can see some of those in our App Catalog.
C# EverywhereOn the Mobile Space: This year Sony jumped to C# in a big way with the introduction of PS Suite (see the section below) and Nokia adopted Windows Phone 7 as their new operating system.And we got you covered on Android and iOS for all of your C# needs. On the Browser: we worked with Google to bring you Mono to Native Client. In fact, every demo shown at the Google Native Client event on December 8th was powered by Mono.On the Desktop: this year we added MacOS X as a first-class citizen in the world of supported Mono platforms. We did this by introducing MonoMac 1.0 and supporting Apple's MacStore with it. Games: continue to take advantage of C# blend of performance and high-level features. Read more on my GDC 2011 post.It is a wild new world for C# and .NET developers that were used to build their UI using ASP.NET or Winforms only. It has been fascinating to see developers evolve their thinking from a Microsoft-only view of the world to a world where they design libraries and applications that split the presentation layer from the business logic. Developers that make this transition will be able to get great native experiences on each device and form factor. Read more: Personal blog of Miguel de Icaza
QR:
XamarinThe largest event for Mono this year was that the team working on Mono technologies at Novell was laid off after Novell was acquired.We got back on our feet, and two weeks after the layoffs had taken place, the original Mono team incorporated as Xamarin. Xamarin's goal is to deliver great productivity and great tools for mobile developers. Our main products are Mono on iOS and Mono on Android.These products are built on top of the open source Mono project and the MonoDevelop project. We continue to contribute extensively to these two open source projects. Launching Xamarin was a huge effort for all of us.Xamarin would not have been possible without our great customers and friends in the industry. Many people cared deeply about the technology and helped us get up and running. In July, we announced an agreement with Attachmate that ensured a bright future for our young company.A couple of days later, we were ready to sell the mobile products that had been previously developed at Novell, and we started to provide all existing Novell customers with ongoing support for their Mono-based products. Half a year later, we grew the company and continued to do what we like the most: writing amazing software.Meanwhile, our users have created amazing mobile applications. You can see some of those in our App Catalog.
C# EverywhereOn the Mobile Space: This year Sony jumped to C# in a big way with the introduction of PS Suite (see the section below) and Nokia adopted Windows Phone 7 as their new operating system.And we got you covered on Android and iOS for all of your C# needs. On the Browser: we worked with Google to bring you Mono to Native Client. In fact, every demo shown at the Google Native Client event on December 8th was powered by Mono.On the Desktop: this year we added MacOS X as a first-class citizen in the world of supported Mono platforms. We did this by introducing MonoMac 1.0 and supporting Apple's MacStore with it. Games: continue to take advantage of C# blend of performance and high-level features. Read more on my GDC 2011 post.It is a wild new world for C# and .NET developers that were used to build their UI using ASP.NET or Winforms only. It has been fascinating to see developers evolve their thinking from a Microsoft-only view of the world to a world where they design libraries and applications that split the presentation layer from the business logic. Developers that make this transition will be able to get great native experiences on each device and form factor. Read more: Personal blog of Miguel de Icaza
QR:
WPFSpark gets all V1.0!
Posted by
jasper22
at
12:07
|
WPFSpark is a library of user controls which can be used by developers to provide a rich User Experience in their applications.
"I am glad to announce that WPFSpark has finally hit v1.0! This release adds four new controls - SparkWindow, FluidPivotPanel, FluidProgressBar and FluidStatusBar.It also brings the following improvements to the existing three controls: SprocketControl
Internal timer stopped when control is no longer visible. It is started only when the control is Visible. This reduces CPU load.
Added the LowestAlpha dependency property which indicates the lowest Opacity value that must be used while rendering the SprocketControl's spokes.
Added the AlphaTicksPercentage dependency property which indicates the percentage of total ticks which must be considered for step by step reduction of the alpha value. The remaining ticks remain at the LowestAlpha value.
SprocketControl now implements IDisposable.
ToggleSwitch
Added the IsCheckedLeft dependency property which indicates whether the checked content appears in the left or right side of the ToggleSwitch
Added the CheckedToolTip property which is displayed when the ToggleSwitch is in the Checked state. Set this property to String.Empty( "" ) to prevent this tooltip from displaying.
Added the UncheckedToolTip property which is displayed when the ToggleSwitch is in the Unchecked state. Set this property to String.Empty( "" ) to prevent this tooltip from displaying.
FluidWrapPanel
Added the ItemSource dependency property which can be bound to an ObservableCollection<UIElement>.
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: WPFSpark
QR:
"I am glad to announce that WPFSpark has finally hit v1.0! This release adds four new controls - SparkWindow, FluidPivotPanel, FluidProgressBar and FluidStatusBar.It also brings the following improvements to the existing three controls: SprocketControl
Internal timer stopped when control is no longer visible. It is started only when the control is Visible. This reduces CPU load.
Added the LowestAlpha dependency property which indicates the lowest Opacity value that must be used while rendering the SprocketControl's spokes.
Added the AlphaTicksPercentage dependency property which indicates the percentage of total ticks which must be considered for step by step reduction of the alpha value. The remaining ticks remain at the LowestAlpha value.
SprocketControl now implements IDisposable.
ToggleSwitch
Added the IsCheckedLeft dependency property which indicates whether the checked content appears in the left or right side of the ToggleSwitch
Added the CheckedToolTip property which is displayed when the ToggleSwitch is in the Checked state. Set this property to String.Empty( "" ) to prevent this tooltip from displaying.
Added the UncheckedToolTip property which is displayed when the ToggleSwitch is in the Unchecked state. Set this property to String.Empty( "" ) to prevent this tooltip from displaying.
FluidWrapPanel
Added the ItemSource dependency property which can be bound to an ObservableCollection<UIElement>.
Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: WPFSpark
QR:
Implementing a message pass-through WCF Behaviour (Router WCF service)
Posted by
jasper22
at
11:38
|

I recently came across a requirement to implement a Windows Communication Service that acts as a message router across several other WCF backend services. This router service main functionality is to encapsulate the backend services and also to add automatic request monitoring. This should not be hard I was thinking but there are couple of twists, first the router service should not sensitive to the services themselves and how they change and communicate with their clients. It also will be handing encrypted messages that it cannot decrypt as these messages belong to other partners that we do not control and of course do not have the certificate used for encryption. The way this is done is by implementing custom WCF message dispatch inspector and custom WCF message client message inspector behaviours. Why do we need both as our service acts as a WCF to all the clients and as a client to all the backend services. So the main idea is to when a message is received over the wire the entire message body is escaped and placed in a custom header element and before this message is sent to the backend the original message body is extracted from the header and written back to the message sent. While the response is being received from the backend service the same logic happens but in the reverse order. So the reply is written to the custom header as an escaped string and then before this reply is delivered to the original caller the reply is read from the header and sent to the client. Simple right J well it will get even better; since we want the original message unparsed and not changed coming on the wire this has to be done using a custom message encoder for both ways, receiving requests from the clients and receiving responses from the backend services. So to try to make this simple I placed the following diagram.
Read more: BizTalk & Development Thoughts
QR:
A Visual Explanation of SQL Joins
Posted by
jasper22
at
11:37
|
I thought Ligaya Turmelle's post on SQL joins was a great primer for novice developers. Since SQL joins appear to be set-based, the use of Venn diagrams to explain them seems, at first blush, to be a natural fit. However, like the commenters to her post, I found that the Venn diagrams didn't quite match the SQL join syntax reality in my testing. I love the concept, though, so let's see if we can make it work. Assume we have the following two tables. Table A is on the left, and Table B is on the right. We'll populate them with four records each. id name id name
-- ---- -- ----
1 Pirate 1 Rutabaga
2 Monkey 2 Pirate
3 Ninja 3 Darth Vader
4 Spaghetti 4 NinjaLet's join these tables by the name field in a few different ways and see if we can get a conceptual match to those nifty Venn diagrams. SELECT * FROM TableA
INNER JOIN TableB
ON TableA.name = TableB.nameid name id name
-- ---- -- ----
1 Pirate 2 Pirate
3 Ninja 4 Ninja

Inner join produces only the set of records that match in both Table A and Table B.
Read more: Coding Horror
QR:
-- ---- -- ----
1 Pirate 1 Rutabaga
2 Monkey 2 Pirate
3 Ninja 3 Darth Vader
4 Spaghetti 4 NinjaLet's join these tables by the name field in a few different ways and see if we can get a conceptual match to those nifty Venn diagrams. SELECT * FROM TableA
INNER JOIN TableB
ON TableA.name = TableB.nameid name id name
-- ---- -- ----
1 Pirate 2 Pirate
3 Ninja 4 Ninja
Read more: Coding Horror
QR:
Cloud Standards Wiki
Cloud Standards CoordinationWelcome to the Wiki site for Cloud Standards Coordination. The goal of this wiki is to document the activities of the various SDOs working on Cloud standards. There is a Press Release announcing our formation. We plan to follow the same process as was used to create the group known as the Standards Development Organization Collaboration on Networked Resources Management (SCRM-WG): SCRM wikiThis includes the development of a Cloud Landscape to overview the various efforts and introduce terms and definitions that allow each standard to be described in common language, and an entry for each standard categorized by organization. We are working on a Template to use in describing each standard and a list of Topics for potential standardization.Below are descriptions of each group with pointers to their efforts (each group has provided their own description).
Cloud Standards OverviewThe group prepared a presentation that overviews the standards coordination activities we are doing. It includes a draft landscape and some recommendations for central government collaboration cloud standards overview.
Cloud Standards PositioningA hopefully interesting initiative can be that of editing and sharing a general "cloud computing standardization positioning", in which more relevant cloud standardization intiatives can be seen and related. a first informal proposal of the positioning can be seen at cloud standards positioning. If interested please provide comments in order to improve the picture. Read more: Cloud Standards Wiki
QR:
Cloud Standards OverviewThe group prepared a presentation that overviews the standards coordination activities we are doing. It includes a draft landscape and some recommendations for central government collaboration cloud standards overview.
Cloud Standards PositioningA hopefully interesting initiative can be that of editing and sharing a general "cloud computing standardization positioning", in which more relevant cloud standardization intiatives can be seen and related. a first informal proposal of the positioning can be seen at cloud standards positioning. If interested please provide comments in order to improve the picture. Read more: Cloud Standards Wiki
QR:
AlienVault Open Source SIEM (OSSIM)
Posted by
jasper22
at
09:16
|

AlienVault Open Source SIEM (OSSIM) is a complete Security Management solution available at no cost. Along with the AlienVault Unified SIEM, AlienVault OSSIM is in use at more organizations than all alternatives combined. AlienVault OSSIM provides all of the functionality required to detect and profiles attacks and provides a comprehensive, intelligent Security Management platform and toolset.The entire solution is composed of open source distributions including all seamlessly integrated tools, and the security management platform. The OSSIM project was created and is currently coordinated by the founders of AlienVault.
The OSSIM platform consists of a Management Server, and Sensor or “Probe”. A professional version that includes Logger functionality is also available (please see below). The solution may be implemented as a single monolithic appliance or a set of appliances in which probes are separated from the management server, and distributed throughout the enterprise. Probes capture network and system information in real time, and send it to the central Management Server where the data is analyzed to assess immediate threats and risk, filter out false positives, and locate false negatives that other security devices and software on the network cannot detect. Read more: AlienVault
QR:
w3af
Posted by
jasper22
at
09:09
|

w3af is a Web Application Attack and Audit Framework. The project's goal is to create a framework to find and exploit web application vulnerabilities that is easy to use and extend. To read our short and long term objectives, please click over the Project Objectives item in the main menu. This project is currently hosted at SourceForge , for further information, you may also want to visit w3af SourceForge project page . Read more: w3af
QR:
Rapid7
Posted by
jasper22
at
09:08
|

Rapid7’s security risk intelligence solutions include the integrated vulnerability management and penetration testing products Nexpose® and Metasploit®, which empower organizations to proactively obtain accurate, actionable and contextual intelligence into their threat and risk posture. With daily reports of new high-profile data breaches, an ever increasing proliferation of new threats and widespread adoption of virtualization techniques, organizations need to obtain a more precise and predictable view into their risk posture. Rapid7 is uniquely positioned to deliver a closed-loop solution for security risk intelligence that dynamically determines the existence and likelihood of risk by combining the capabilities of Nexpose for vulnerability management and Metasploit for penetration testing and risk validation. By correlating data on vulnerabilities, exploit and malware exposure, misconfigurations and penetration test information, Rapid7 quantifies the Real Risk™ within your environment. Armed with this accurate and contextual information, we can provide clear and concise recommendations on mitigation and remediation strategies, as well as measuring and tracking risk trends over time. Read more: Rapid7 Community edition
QR:
Linux Kernel in a Nutshell
When the topic of this book was first presented to me, I dismissed it as something that was already covered by the plentiful documentation about the Linux kernel. Surely someone had already written down all of the basics needed in order to build, install, and customize the Linux kernel, as it seemed to be a very simple task to me. [1] After digging through the different HOWTOs and the Linux kernel Documentation directory, I came to the conclusion that there was not any one place where all of this information could be found. It could be gleaned by referencing a few files here, and a few outdated websites there, but this was not acceptable for anyone who did not know exactly what they were looking in the first place. So this book was created with the goal of consolidating all of the existing information already scattered around the Internet about building the Linux kernel, as well as adding a lot of new and useful information that was not written down anywhere but had been learned by trial and error over my years of doing kernel development. My secret goal of this book is to bring more people into the Linux kernel development fold. The act of building a customized kernel for your machine is one of the basic tasks needed to become a Linux kernel developer. The more people that try this out, and realize that there is not any real magic behind the whole Linux kernel process, the more people will be willing to jump in and help out in making the kernel the best that it can be. Audience for the bookThis book is intended to cover everything that is needed to know in order to properly build, customize, and install the Linux kernel. No programming experience is needed to understand and use this book. Some familiarity with how to use Linux, and some basic command-line usage is expected of the reader.This book is not intended to go into the programming aspects of the Linux kernel; there are many other good books listed in the Bibliography that already cover this topic.
Read more: Linux Kernel in a Nutshell
QR:
Read more: Linux Kernel in a Nutshell
QR:
.NET Client Library for Google+ (Both in original binary form and decompiled/source version too)
Posted by
jasper22
at
11:05
|

Are you a .NET developer looking for a .NET Client library to develop cool applications using Google+ data? Here is a .NET library, developed using C#. You can download the .NET Library from here and use it to develop applications We are excited to announce the release of GooglePlusLib, a .NET library for Google+ APIs.Google announced the version 1 of Google+ APIs couple of days ago. As usual, Google released the APIs along with a couple of client libraries, including .NET client library. However, the client libraries released by Google have some learning curve since the usage is not in the native .NET programming style. Here is a .NET client library we developed for Google+ APIs. They are very easy to use in your applications.Licensing
You are welcome to use the GooglePlusLib.NET client library as you like. You can use this library to develop applications and distribute it with your applications. Read more: Greg's Cool [Insert Clever Name] of the Day
Read more: .NET Client Library for Google+ APIs from GooglePlusTips.com
QR:
Why have CPUs been limited in frequency to around 3.5Ghz for so many years? What prevents us from increasing the frequency to 10, 100, 1000Ghz?
Posted by
jasper22
at
09:46
|
Question:
Why have CPUs been limited in frequency to around 3.5Ghz for so many years? What prevents us from increasing the frequency to 10, 100, 1000Ghz?
Answer:Oh cool I actually know the answer to a question in askscience. I am an electrical engineer and I work in the IC (integrated circuit) industry. The short answer is that scaling of semiconductor transistors has reached a limit due to the physical properties defining them. In the 1980s and 1990s, we enjoyed "ideal" scaling and were able to increase the speed and decrease the size by keeping all electric fields inside the transistor constant. As they got smaller and smaller, effects that previously could be ignored due to the macroscopic nature of the devices took a bigger and bigger role in how the devices functioned. One of the most important factors affecting constant-field scaling for devices intended to be used for digital applications (processors) is inability to scale the threshold voltage due to sub-vt operation causing leakage power. Basically the transistor is a switch, and you don't get a very good "off" if the threshold voltage is too low and every transistor inside the chip dissipates power all the time. Usually power is only dissipated in a logic circuit when it switches. Here is a good paper explaining constant field scaling.Edit: a lot of people have asked "why don't we just increase the area?" The area for chips has been roughly the same for a long time, and the reason for this is defect density and process variability. The logic behind this is that if there are a set number of defects in the manufacturing process per wafer [in #defects/cm2], then the bigger the chip is, the more area that the defect affects and you can't sell.
Read more: Reddit
QR:
Why have CPUs been limited in frequency to around 3.5Ghz for so many years? What prevents us from increasing the frequency to 10, 100, 1000Ghz?
Answer:Oh cool I actually know the answer to a question in askscience. I am an electrical engineer and I work in the IC (integrated circuit) industry. The short answer is that scaling of semiconductor transistors has reached a limit due to the physical properties defining them. In the 1980s and 1990s, we enjoyed "ideal" scaling and were able to increase the speed and decrease the size by keeping all electric fields inside the transistor constant. As they got smaller and smaller, effects that previously could be ignored due to the macroscopic nature of the devices took a bigger and bigger role in how the devices functioned. One of the most important factors affecting constant-field scaling for devices intended to be used for digital applications (processors) is inability to scale the threshold voltage due to sub-vt operation causing leakage power. Basically the transistor is a switch, and you don't get a very good "off" if the threshold voltage is too low and every transistor inside the chip dissipates power all the time. Usually power is only dissipated in a logic circuit when it switches. Here is a good paper explaining constant field scaling.Edit: a lot of people have asked "why don't we just increase the area?" The area for chips has been roughly the same for a long time, and the reason for this is defect density and process variability. The logic behind this is that if there are a set number of defects in the manufacturing process per wafer [in #defects/cm2], then the bigger the chip is, the more area that the defect affects and you can't sell.
Read more: Reddit
QR:
Sharing with CompositionScopeDefinition in MEF 2
Posted by
jasper22
at
09:43
|
In the previous post, we introduced ExportFactory<T> and demonstrated how it can be used to control the lifetimes of MEF parts. In this article we will talk about a new type MEF called CompositionScopeDefinition that can be used in conjunction with ExportFactory<T> to control sharing. Let’s take a scenario that we could not achieve using what we know currently and how CompositionScopeDefinition provides the needed control. Important note: CompositionScopeDefinition is geared towards more advanced, desktop application scenarios. If you're using MEF in an ASP.NET MVC web application and want to control sharing and lifetime on a per-HTTP-request level, you should use the pre-defined ASP.NET MVC integration. Lets go back to our application block diagram that we built in Part 1 of this article.
Now let’s add a few details to this architecture. As our application has grown more complex, we have decided to factor out the data access part into a separate component called DataAccessLayer, which handles manages the connection to the database and reading and writing to it. In addition to this we also want to add a logger, which also logs some tracking information to the same database. So our slightly expanded functional diagram looks like the following. Read more: BCL Team Blog
QR:
QR:
CXXI: Briding the C++ and C# worlds.
Posted by
jasper22
at
09:41
|
The Mono runtime engine has many language interoperability features but has never had a strong story to interop with C++.Thanks to the work of Alex Corrado, Andreia Gaita and Zoltan Varga, this is about to change. The short story is that the new CXXI technology allows C#/.NET developers to: Easily consume existing C++ classes from C# or any other .NET language
Instantiate C++ objects from C#
Invoke C++ methods in C++ classes from C# code
Invoke C++ inline methods from C# code (provided your library is compiled with -fkeep-inline-functions or that you provide a surrogate library)
Subclass C++ classes from C#
Override C++ methods with C# methods
Expose instances of C++ classes or mixed C++/C# classes to both C# code and C++ as if they were native code. CXXI is the result of two summers of work from Google's Summer of Code towards improving the interoperability of Mono with the C++ language.
The AlternativesThis section is merely a refresher of of the underlying technologies for interoperability supported by Mono and how developers coped with C++ and C# interoperability in the past. You can skip it if you want to get to how to get started with CXXI. As a reminder, Mono provides a number of interoperability bridges, mostly inherited from the ECMA standard. These bridges include: The bi-directional "Platform Invoke" technology (P/Invoke) which allows managed code (C#) to call methods in native libraries as well as support for native libraries to call back into managed code.
COM Interop which allows Mono code to transparently call C or C++ code defined in native libraries as long as the code in the native libraries follows a few COM conventions [1].
A general interceptor technology that can be used to intercept method invocations on objects. When it came to getting C# to consume C++ objects the choices were far from great. For example, consider a sample C++ class that you wanted to consume from C#:class MessageLogger {
public:
MessageLogger (const char *domain);
void LogMessage (const char *msg);
}One option to expose the above to C# would be to wrap the Demo class in a COM object. This might work for some high-level objects, but it is a fairly repetitive exercise and also one that is devoid of any fun. You can see how this looks like in the COM Interop page. The other option was to produce a C file that was C callable, and invoke those C methods. For the above constructor and method you would end up with something like this in C:/* bridge.cpp, compile into bridge.so */
MessageLogger *Construct_MessageLogger (const char *msg)
{
return new MessageLogger (msg);
}void LogMessage (MessageLogger *logger, const char *msg)
{
logger->LogMessage (msg);
}
Read more: Personal blog of Miguel de Icaza
QR:
Instantiate C++ objects from C#
Invoke C++ methods in C++ classes from C# code
Invoke C++ inline methods from C# code (provided your library is compiled with -fkeep-inline-functions or that you provide a surrogate library)
Subclass C++ classes from C#
Override C++ methods with C# methods
Expose instances of C++ classes or mixed C++/C# classes to both C# code and C++ as if they were native code. CXXI is the result of two summers of work from Google's Summer of Code towards improving the interoperability of Mono with the C++ language.
The AlternativesThis section is merely a refresher of of the underlying technologies for interoperability supported by Mono and how developers coped with C++ and C# interoperability in the past. You can skip it if you want to get to how to get started with CXXI. As a reminder, Mono provides a number of interoperability bridges, mostly inherited from the ECMA standard. These bridges include: The bi-directional "Platform Invoke" technology (P/Invoke) which allows managed code (C#) to call methods in native libraries as well as support for native libraries to call back into managed code.
COM Interop which allows Mono code to transparently call C or C++ code defined in native libraries as long as the code in the native libraries follows a few COM conventions [1].
A general interceptor technology that can be used to intercept method invocations on objects. When it came to getting C# to consume C++ objects the choices were far from great. For example, consider a sample C++ class that you wanted to consume from C#:class MessageLogger {
public:
MessageLogger (const char *domain);
void LogMessage (const char *msg);
}One option to expose the above to C# would be to wrap the Demo class in a COM object. This might work for some high-level objects, but it is a fairly repetitive exercise and also one that is devoid of any fun. You can see how this looks like in the COM Interop page. The other option was to produce a C file that was C callable, and invoke those C methods. For the above constructor and method you would end up with something like this in C:/* bridge.cpp, compile into bridge.so */
MessageLogger *Construct_MessageLogger (const char *msg)
{
return new MessageLogger (msg);
}void LogMessage (MessageLogger *logger, const char *msg)
{
logger->LogMessage (msg);
}
Read more: Personal blog of Miguel de Icaza
QR:
How to test SSL based WCF services
I usually work with WCF service that needs to be secured with Certificates or simply using HTTPS. The usual question from other dev in the team is “how can I simulate HTTPS to work with WCF?”The problem arise that to test https sites, people usually work with IIS self issued certificates. 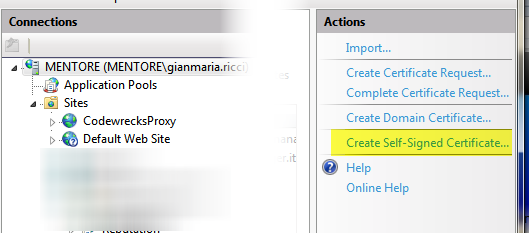
This works great for sites, you can use the auto signed certificate in your sites in https binding, then when you navigate to the site you usually got an error because the certificate is not issued for the right site. What I need is usually to modifiy the hosts file in windows, creating an alias of www.mydomain.com to 127.0.0.1, so I can directly point to the right address with WCF client application and can simply manage to use the local or remote service simply modifying the hosts file. Sadly enough, WCF does not tolerate problem in certificates and this makes useless working with Self-Signed Certificate. To be able to use a WCF Service secured with SSL in your dev machine you should issue yourself a valid certificate. The solution is using the SelfSSL.exe tool that comes with the IIS6 Resource Kit Tools. Once installed you can simply go to installation folder with Administrator Command Prompt (you need to launch the command prompt as administrator or it wont work) and simply create a valid certificate with this command line Selfssl /N:CN=www.codewrecks.com /V :2000 /S:3as you can see with the option /N:CN you are able to specify the Common Name you want to use, the /V option is used to specify the duraction in years of the certificate, and the /S: is used to specify the Id of the site you want to change, just select the “site” node on IIS7 administration console to see the ID assigned to each site.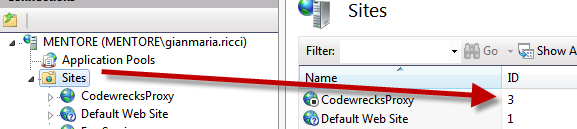
Read more: Alkampfer's Place
QR:

This works great for sites, you can use the auto signed certificate in your sites in https binding, then when you navigate to the site you usually got an error because the certificate is not issued for the right site. What I need is usually to modifiy the hosts file in windows, creating an alias of www.mydomain.com to 127.0.0.1, so I can directly point to the right address with WCF client application and can simply manage to use the local or remote service simply modifying the hosts file. Sadly enough, WCF does not tolerate problem in certificates and this makes useless working with Self-Signed Certificate. To be able to use a WCF Service secured with SSL in your dev machine you should issue yourself a valid certificate. The solution is using the SelfSSL.exe tool that comes with the IIS6 Resource Kit Tools. Once installed you can simply go to installation folder with Administrator Command Prompt (you need to launch the command prompt as administrator or it wont work) and simply create a valid certificate with this command line Selfssl /N:CN=www.codewrecks.com /V :2000 /S:3as you can see with the option /N:CN you are able to specify the Common Name you want to use, the /V option is used to specify the duraction in years of the certificate, and the /S: is used to specify the Id of the site you want to change, just select the “site” node on IIS7 administration console to see the ID assigned to each site.

QR:
SSMS Tools Pack : the tool that any T-SQL developer and SQL SERVER DBA must To install
Posted by
jasper22
at
15:42
|
As a DBA I instruct all the developer / DBA to Install this Tools.Read this Article And see why.Let's Start with the List of Features comes with the New Version 2.1. 
You can Download this Tool from :http://www.ssmstoolspack.com/Download The Biggest Feature on this version is the :Execution Plan AnalyzerThat going to help you analyze the Query Execution Plan AnalyzerIs a feature that will :Cut your query troubleshooting time at least by half or more. With it you can easily see the costliest plan operatorsbased on different propertiesLike IO, CPU, Number of rows, Cardinality, Relatice cost, etc....Can't find a node that is on a particular index? Read more: Yehuda Lasri
QR:

QR:
Task != Thread
Posted by
jasper22
at
11:51
|
whenever I teaching the Tpl Task subject I continually repeating the mantra which say that "task is a metadata/context of execution and it does not really responsible for the actual execution". Task is a data structure which hold information about code execution, it's hold the delegate which will be execute, status, state, result, exception synchronization object, ext...
but the responsibility of the execution is actually belong to the Task Scheduler. in matter of fact task can be execute synchronously. Console.WriteLine(Thread.CurrentThread.ManagedThreadId);
Task t = new Task(() =>
Console.WriteLine(Thread.CurrentThread.ManagedThreadId));
t.RunSynchronously();
by default it is execute on a thread pool worker thread but it can be execute on non thread pool thread (using the TaskCreationOption.LongRunning overload). Task.Factory.StartNew(() =>
Console.WriteLine(Thread.CurrentThread.IsThreadPoolThread));
Task.Factory.StartNew(() =>
Console.WriteLine(Thread.CurrentThread.IsThreadPoolThread),
TaskCreationOptions.LongRunning); it can be benefit from IOCP (IO Completion Port) in order to avoid thread pool starvation (when performing IO operations). IO operation are not CPU bounded operation, those operation performed by the hard disk controller, the network card, ext...
Read more: Bnaya Eshet
QR:
but the responsibility of the execution is actually belong to the Task Scheduler. in matter of fact task can be execute synchronously. Console.WriteLine(Thread.CurrentThread.ManagedThreadId);
Task t = new Task(() =>
Console.WriteLine(Thread.CurrentThread.ManagedThreadId));
t.RunSynchronously();
by default it is execute on a thread pool worker thread but it can be execute on non thread pool thread (using the TaskCreationOption.LongRunning overload). Task.Factory.StartNew(() =>
Console.WriteLine(Thread.CurrentThread.IsThreadPoolThread));
Task.Factory.StartNew(() =>
Console.WriteLine(Thread.CurrentThread.IsThreadPoolThread),
TaskCreationOptions.LongRunning); it can be benefit from IOCP (IO Completion Port) in order to avoid thread pool starvation (when performing IO operations). IO operation are not CPU bounded operation, those operation performed by the hard disk controller, the network card, ext...
Read more: Bnaya Eshet
QR:
How to Build libiconv with Microsoft Visual Studio
Posted by
jasper22
at
11:49
|
IntroductionLibiconv is one of the most useful and famous libraries that converts texts between encodings and has been developed under GNU projects. However, now it does not provide the way to build it with Microsoft Visual Studio but with gcc. Before, it had provided but now stopped explaining how to build it with Microsoft Visual Studio. However, many of the computer programmers are using Microsoft Visual Studio and want to build libiconv with Microsoft Visual Studio. So, this article is about how to build libiconv with Microsoft Visual Studio. If you can build libiconv with Microsoft Visual Studio, you will be able to change various compilation options and build it in order to optimize libiconv according to your preference and needs.
BackgroundIf you have no idea about libiconv, you can refer to it here or you can Google for it. You may be confused with iconv and libiconv. Iconv is the executable program that uses libiconv while libiconv is the library for converting text strings between two different encodings. This article is related to libiconv. However, this article is not about libiconv but about how to build libicon with Microsoft Visual Studio. The GNU library libiconv is under LGPL license. So, you have to be really careful when you use libiconv for your commercial use or when you don't want to publicize your source code. About LPGL license, you can refer here.
How to Get the Source Code of libiconvAt the moment, the most recent version of libiconv is 1.14. You can download the source code of libiconv 1.14 here and here. Of course, you can get the older versions of libiconv here.
How to BuildI am going to explain the case of Microsoft Visual Studio 2010 professional edition but the explanation can be applied to the earlier versions of Microsoft Visual Studio and to the express edition of each of them.
First StepYou download the most recent version of libiconv which is 1.14 from here or here. And unzip the downloaded file "libiconv-1.14.tar.gz" on your certain folder.Read more: Codeproject
QR:
BackgroundIf you have no idea about libiconv, you can refer to it here or you can Google for it. You may be confused with iconv and libiconv. Iconv is the executable program that uses libiconv while libiconv is the library for converting text strings between two different encodings. This article is related to libiconv. However, this article is not about libiconv but about how to build libicon with Microsoft Visual Studio. The GNU library libiconv is under LGPL license. So, you have to be really careful when you use libiconv for your commercial use or when you don't want to publicize your source code. About LPGL license, you can refer here.
How to Get the Source Code of libiconvAt the moment, the most recent version of libiconv is 1.14. You can download the source code of libiconv 1.14 here and here. Of course, you can get the older versions of libiconv here.
How to BuildI am going to explain the case of Microsoft Visual Studio 2010 professional edition but the explanation can be applied to the earlier versions of Microsoft Visual Studio and to the express edition of each of them.
First StepYou download the most recent version of libiconv which is 1.14 from here or here. And unzip the downloaded file "libiconv-1.14.tar.gz" on your certain folder.Read more: Codeproject
QR:
Легальные буткиты
Posted by
jasper22
at
11:48
|
Умница Русаков, которого многие до сих пор ошибочно называют РусТОКов, написал очередную статью на www.securelist.ru. И опять — про руткит-технологии. Впрочем, в этой статье не упоминается ни TDL 4, ни какая-либо другая вредоносная программа. Потому что статья — про опасности использования неаккуратно реализованных руткит-технологий в легальных продуктах, о чем автор прямо сообщает во введении. Кстати, за введение ему отдельное спасибо, потому что без него неподготовленный читатель вообще бы ничего не понял — несмотря на то, что в тексте довольно много картинок. Для начала автор с подозрительной прозорливостью придумывает несколько случаев той самой неаккуратной реализации, которая могла бы позволить злодеям использовать легальные драйверы, протекторы, крипторы и классические анти-руткиты в своих злодейских целях. Ему практически удается убедить читателя, что легальный подписанный драйвер представляет потенциальную угрозу безопасности, в том случае, если руткит-технологии реализованы в нем с тщательностью российского автопрома. Мало того, с подозрительной осведомленностью утверждая, что и по ту сторону баррикад не дураки имеются, автор запугивает читателей возможностью злодеев разобрать им же самим придуманную небрежную реализацию драйвера режима ядра по косточкам и полученные таким варварским способом знания опять же — использовать в злодейских целях. 
Read more: Habrahabr.ru
QR:

QR:
Why have a stack?
Posted by
jasper22
at
11:46
|
Last time I discussed why it is that we have all the .NET compilers target an "intermediate language", or "IL", and then have jitters that translate IL to machine code: because doing so ultimately reduces the costs of building a multi-language, multi-hardware platform. Today I want to talk a bit about why IL is the way it is; specifically, why is it a "stack machine"? To begin with, what is a "stack machine"? Let's consider how you might design a machine language that could describe the operation of adding together two integers to make a third. You could do it like this: add [address of first addend], [address of second addend], [address of sum]
When the machine encounters this instruction it looks up the values of the addends stored in the two addresses, somehow adds them together -- how it does so is its business -- and stores the result in the third address. You might instead say that there is a special region of memory called the "accumulator" which knows how to add a given value to itself:clear_accumulator
increase_accumulator [address of first addend]
increase_accumulator [address of second addend]
save_accumulator [address of sum]
Or, you could say that there is a special region of memory called the "stack" which can grow and shrink; you get access to the items on the top: push_value_at [address of first addend]
push_value_at [address of second addend]
add
pop_value_into [address of sum]
The "add" instruction takes the two values off the top of the stack, somehow adds them, and then puts the result back on the stack; the net result is that the stack shrinks by one. A virtual machine where most of the instructions are of this third form is called a "stack machine", for obvious reasons.IL specifies a stack machine, just like many other virtual machines. But most hardware instruction sets actually more closely resemble the second form: registers are just fancy accumulators. Why then are so many virtual machines specifying stack machines?
Read more: Fabulous Adventures In Coding
QR:
When the machine encounters this instruction it looks up the values of the addends stored in the two addresses, somehow adds them together -- how it does so is its business -- and stores the result in the third address. You might instead say that there is a special region of memory called the "accumulator" which knows how to add a given value to itself:clear_accumulator
increase_accumulator [address of first addend]
increase_accumulator [address of second addend]
save_accumulator [address of sum]
Or, you could say that there is a special region of memory called the "stack" which can grow and shrink; you get access to the items on the top: push_value_at [address of first addend]
push_value_at [address of second addend]
add
pop_value_into [address of sum]
The "add" instruction takes the two values off the top of the stack, somehow adds them, and then puts the result back on the stack; the net result is that the stack shrinks by one. A virtual machine where most of the instructions are of this third form is called a "stack machine", for obvious reasons.IL specifies a stack machine, just like many other virtual machines. But most hardware instruction sets actually more closely resemble the second form: registers are just fancy accumulators. Why then are so many virtual machines specifying stack machines?
Read more: Fabulous Adventures In Coding
QR:
Import Apache mod_rewrite Rules in IIS 7
Posted by
jasper22
at
11:39
|
With Microsoft's Web Stack, many PHP applications are now hosted on IIS. As PHP is an open source, one of the advantages of using PHP is that you will find plenty of free script for ready to use. And basically these all ready to use scripts are written for LAMP model, so we might face some problem related to web server (Apache vs IIS) configuration while running these scripts on IIS. Recently one of my friend face similar problem with Apache rewrite rules while he deployed ready to use PHP script on IIS, and asked me to resolve it. We need to convert apache mod_rewrite rules into IIS URL Rewrite rules to deploy PHP application on IIS. We can accomplish this task in two ways.
First wayOpen .htaccess file of PHP and manually convert each apache mod_rewrite rule in IIS URL Rewrite rule and then save it in web.config. Now loop through above process for total number of apache mod_rewrite rule ;)
Smarter wayInstead of manually loop through each apache mod_rewrite rule and converting it in IIS URL Rewrite rule, we can automate this process with IIS URL Rewrite Module. Earlier in one post we have seen how we can use IIS URL Rewrite Module to set preferred domain. Following is the steps for converting apache mod_rewrite rules into IIS URL Rewrite rules. Open URL Rewrite Module in IIS.
Read more: dotnetExpertGuide.com
QR:
First wayOpen .htaccess file of PHP and manually convert each apache mod_rewrite rule in IIS URL Rewrite rule and then save it in web.config. Now loop through above process for total number of apache mod_rewrite rule ;)
Smarter wayInstead of manually loop through each apache mod_rewrite rule and converting it in IIS URL Rewrite rule, we can automate this process with IIS URL Rewrite Module. Earlier in one post we have seen how we can use IIS URL Rewrite Module to set preferred domain. Following is the steps for converting apache mod_rewrite rules into IIS URL Rewrite rules. Open URL Rewrite Module in IIS.

QR:
Remote Desktop Services (RDS) Architecture
Posted by
jasper22
at
11:39
|
שלום רב.כאן שוב כפיר מלח מצוות יועצי התשתיות של AgileIT והיום אני אמשיך בסדרת הכתבות על Microsoft Virtual Infrastructure והפעם על Remote Desktop Services ובעיקר על הארכיטקטורה שלו. ב-Windows Server 2008 R2 שירותי הטרמינל הורחבו וכעת נקראים Remote Desktop Services או בקיצור RDS. הארכיטקטורה החדשה והמשופרת מנצלת את הוירטואליזציה ובכך הופכת את הגישה מרחוק לפתרון גמיש יותר . על מנת לממש את את היכולות של RDS יש צורך להבין את הפונקציונליות של רכיבי המפתח הארכיטקטוניים וכיצד הם משלימים זה את זה בתהליך הבקשה. ב-RDS ישנם חמישה רכיבים עיקריים כאשר כל אחד מהם דורש שרת רישוי RDS, לכל אחד מהרכיבים יש חמישה תכונות שנועדו להשיג פונקצינליות מסוימת, כאשר יחדיו הם יוצרים מסגרת גישה לשרותי טרמינל, יישומים, שולחנות עבודה עם גישה מרחוק, ושולחנות עבודה וירטואליים . לפיכך WS2008R2 מציע סדרה של אבני יסוד עם פונקציות חיוניות לבנייה ארגונית עם ארכיטקטורה של גישה מרחוק.
Mnemonic: assisting your (virtual) memory
Posted by
jasper22
at
11:37
|
IntroductionThis article describes a tool I wrote to show, pictorially and dynamically, the consumption of virtual memory by a Windows process.
Background Recently, I needed to investigate the way in which a Windows process was consuming Virtual Memory (VM). I wanted to get a picture in my head of the available VM and how it was being allocated, freed and mapped by the process, and phenomena such as virtual memory fragmentation. I came across this tool by Charles Bailey: http://hashpling.org/asm/. It works well and it helped, but I wanted more information about particular types of allocation (those corresponding to memory-mapped files and managed and unmanaged assemblies loaded by the process), and I wanted to be able to understand for myself what was going on 'under the hood'. So I wrote my own tool.
Using the tool Simply run the executable. It requires the .Net framework 4 Client profile, but otherwise needs no installation.Select a running process from the dropdown list. Alternatively, type the name of a process (e.g. "Excel"), and wait for it to start; Mnemonic will automatically scan the process for as long as it runs. You'll see a screen such as this: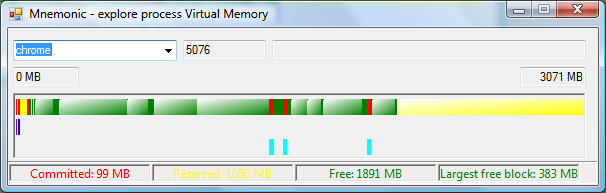
Read more: Codeproject
QR:
Background Recently, I needed to investigate the way in which a Windows process was consuming Virtual Memory (VM). I wanted to get a picture in my head of the available VM and how it was being allocated, freed and mapped by the process, and phenomena such as virtual memory fragmentation. I came across this tool by Charles Bailey: http://hashpling.org/asm/. It works well and it helped, but I wanted more information about particular types of allocation (those corresponding to memory-mapped files and managed and unmanaged assemblies loaded by the process), and I wanted to be able to understand for myself what was going on 'under the hood'. So I wrote my own tool.
Using the tool Simply run the executable. It requires the .Net framework 4 Client profile, but otherwise needs no installation.Select a running process from the dropdown list. Alternatively, type the name of a process (e.g. "Excel"), and wait for it to start; Mnemonic will automatically scan the process for as long as it runs. You'll see a screen such as this:

Read more: Codeproject
QR:
#436 – Using a Drop Shadow with a Border
Posted by
jasper22
at
11:36
|
If you specify a DropShadowEffect for a Border, all elements within the border will get a drop shadow.<Border Margin="10" BorderBrush="Black" BorderThickness="1">
<Border.Effect>
<DropShadowEffect/>
</Border.Effect>
<StackPanel Orientation="Vertical" Margin="5">
<Label Content="Staying within borders"/>
<Button Content="Do It"/>
</StackPanel>
</Border>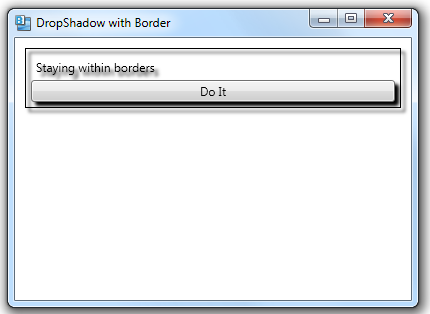
Read more: 2,000 Things You Should Know About WPF
QR:
<Border.Effect>
<DropShadowEffect/>
</Border.Effect>
<StackPanel Orientation="Vertical" Margin="5">
<Label Content="Staying within borders"/>
<Button Content="Do It"/>
</StackPanel>
</Border>

QR:
Building and Using Expression Blend Behaviors
Posted by
jasper22
at
11:34
|
Behaviors are a cool way of adding functionality to XAML design elements in Expression Blend. The idea is that some rich functionality that would be hard for a designer to do can be wrapped in a way that can then be used as a drag-and-drop feature to add that functionality to a XAML element in Expression Blend. A Behavior then is an ‘object’ that implements a certain base class and member(s) so that it can be easily consumed in Expression Blend as a drag-and-drop ‘behavior’ on the design surface. To build a new behavior you need to start in Visual Studio. Implementing BehaviorsImplementing a Behavior is straightforward and can be as complicated or as simple as you like. To start with, you will need Expression Blend installed so you can test your behavior in Expression Blend. If you are already in Expression Blend, right-click the project and click "Open in Visual Studio," which this implies correctly that you need both Expression Blend AND Visual Studio installed to create and test a Behavior. Once the project is opened in Visual Studio, right-click and select "Add New." Then in the "Add New" dialog, select Class. Give the class a name, and then you need to get the Expression Blend Library into your project. To get the base class (and the associated name space), you must add a reference to the System.Windows.Interactivity name space that comes with the Silverlight 4 framework. Right click on references and select "Add Reference.” Once the namespace is included, you are ready to build out the class you created into a Behavior. You need to start by adding the namespace at the top like this: using System.Windows.Interactivity;This gets the base library (namespace) you need so you can inherit from the behavior base class. Next, of course, you need to set up your class to inherit from TargetedTriggerAction and make your class look in effect like this: public class SomeBehavior : TargetedTriggerAction
{
}Read more: Windows Phone 7
QR:
{
}Read more: Windows Phone 7
QR:
Updated Documentation Site
Posted by
jasper22
at
11:32
|
Jeremie Laval has upgraded our Web-based documentation engine over at docs.go-mono.com. This upgrade brings a few features:New Look: Base on Jonathan Pobst's redesign, this is what our documentation looks like now: 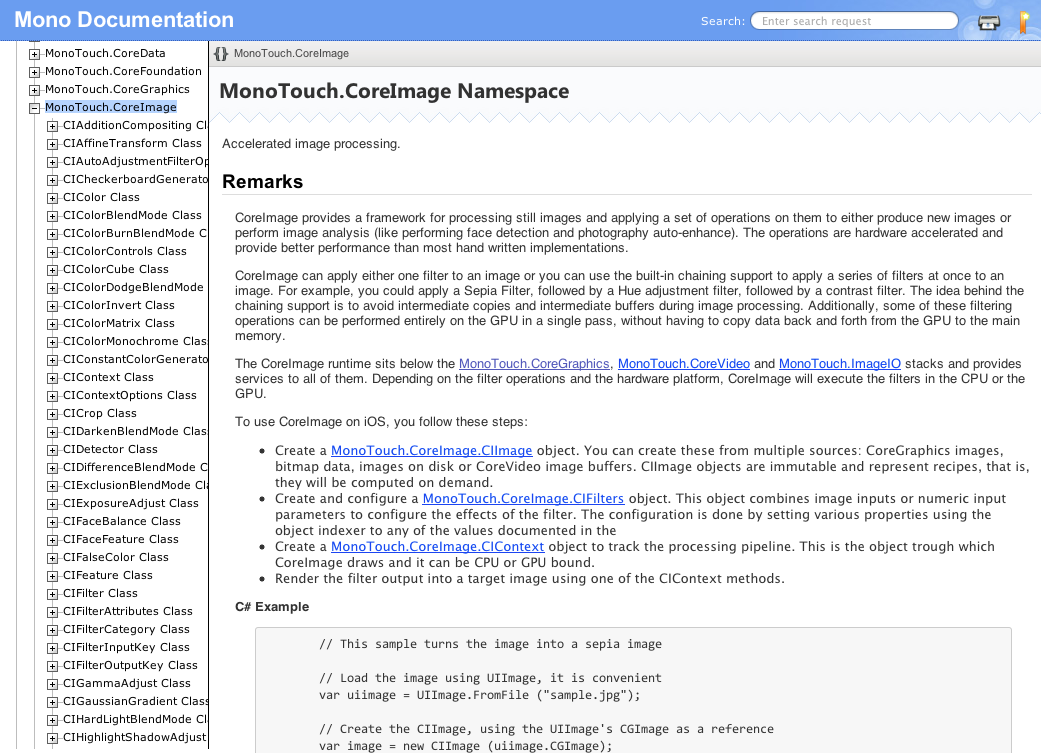
Read more: Personal blog of Miguel de Icaza
QR:

QR:
Visual Studio 2010 Walkthroughs
Posted by
jasper22
at
11:31
|

Visual Studio 2010 and .NET Framework 4 walkthroughs that include technical information and other learning resources. Read more: Visual Studio
QR:
Subscribe to:
Comments (Atom)



