ssdeep
Introduction
ssdeep is a program for computing context triggered piecewise hashes (CTPH). Also called fuzzy hashes, CTPH can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length.
A complete explanation of CTPH can be found in Identifying almost identical files using context triggered piecewise hashing from the journal Digital Investigation. There is a free version of this paper available through the Digital Forensic Research Workshop conference, free version of Identifying almost identical files using context triggered piecewise hashing.
There are some usage scenarios in the Quickstart guide and the Forensics Wiki entry on ssdeep.
The package also includes a fuzzy hashing API. The API is documented in the file API.TXT in the Windows distribution and README in the source code package.
See Also
The math behind fuzzy hashing was originally developed by Dr. Andrew Trigdell in a spam dectector he called spamsum.
Supported Platforms
Microsoft Windows
The program runs on Microsoft Windows 2000, XP, 2003, and Vista. It is not supported on Windows 95, 98, Me, 3.1, 3.11, or 3.11 for Workgroups.
*nix
The program has been tested on Open Solaris, FreeBSD, Linux, and Mac OS X. It should compile and run on any other platform that is supported by the GNU Build Tools.
Read more: Sourceforge
QR: 
Task.Run vs Task.Factory.StartNew
Posted by
jasper22
at
10:52
|
In .NET 4, Task.Factory.StartNew was the primary method for scheduling a new task. Many overloads provided for a highly configurable mechanism, enabling setting options, passing in arbitrary state, enabling cancellation, and even controlling scheduling behaviors. The flip side of all of this power is complexity. You need to know when to use which overload, what scheduler to provide, and the like. And “Task.Factory.StartNew” doesn’t exactly roll off the tongue, at least not quickly enough for something that’s used in such primary scenarios as easily offloading work to background processing threads.
So, in the .NET Framework 4.5 Developer Preview, we’ve introduced the new Task.Run method. This in no way obsoletes Task.Factory.StartNew, but rather should simply be thought of as a quick way to use Task.Factory.StartNew without needing to specify a bunch of parameters. It’s a shortcut. In fact, Task.Run is actually implemented in terms of the same logic used for Task.Factory.StartNew, just passing in some default parameters. When you pass an Action to Task.Run:
Task.Run(someAction);
that’s exactly equivalent to:
Task.Factory.StartNew(someAction,
CancellationToken.None, TaskCreationOptions.DenyChildAttach, TaskScheduler.Default);
In this way, Task.Run can and should be used for the most common cases of simply offloading some work to be processed on the ThreadPool (what TaskScheduler.Default targets). That doesn’t mean Task.Factory.StartNew will never again be used; far from it. Task.Factory.StartNew still has many important (albeit more advanced) uses. You get to control TaskCreationOptions for how the task behaves. You get to control the scheduler for where the task should be queued to and run. You get to use overloads that accept object state, which for performance-sensitive code paths can be used to avoid closures and the corresponding allocations. For the simple cases, though, Task.Run is your friend.
Task.Run provides eight overloads, to support all combinations of the following:
- Task vs Task<TResult>
- Cancelable vs non-cancelable
- Synchronous vs asynchronous delegate
The first two bullets should be self-explanatory. For the first bullet, there are overloads that return Task (for operations that don’t have a result) and there are overloads that return Task<TResult> (for operations that have a result of type TResult). There are also overloads that accept a CancellationToken, which enables the Task Parallel Library (TPL) to transition the task to a Canceled state if cancellation is requested prior to the task beginning its execution.
Read more: Parallel Programming with .NET
QR: 
Psychic Debugging of Async Methods
Posted by
jasper22
at
10:31
|
These days it’s not uncommon for me to receive an email or read a forum post from someone concerned about a problem they’re experiencing with an async method they’ve written, and they’re seeking help debugging the issue. Sometimes plenty of information about the bug is conveyed, but other times the communication is void of anything more than a root problem statement. That’s when I engage my powers of psychic debugging to suggest what the root cause might be, without actually knowing more about the developer’s codebase.
Here are four of the more common issues I’ve heard raised, along with their likely culprits. If you experience one of these problems, look at one of these causes first, as there’s a very good chance it’s to blame.
1. “I converted my synchronous method to be asynchronous using ‘async’, but it still runs synchronously.”
As explained in the Async/Await FAQ, marking a method as ‘async’ does not force the method to run asynchronously, e.g. it doesn’t queue a work item to run the method, it doesn’t spawn a new thread to run the method, etc. Marking a method as ‘async’ really just tells the compiler to allow usage of ‘await’ inside the body of the method, and to handle completion/results/exceptions from the method in a special way (i.e. putting them into a task that’s returned from the method call). When you invoke a method that’s marked as ‘async’, the method is still invoked synchronously, and it continues to run synchronously until either a) the method completes, or b) the method awaits an awaitable (e.g. a task) that’s not yet complete. If the method doesn’t contain any awaits (which will generate a compiler warning) or if it only ever awaits awaitables that are already completed, the method will run to completion synchronously, and the task returned to the caller will be completed by the time it’s handed back. This is by design.
If your goal in using ‘async’ isjust to offload some synchronous work to another thread, you can instead use Task.Run to do this rather than using the async/await language features, e.g. if you have the synchronous method:
int DoWork()
{
…
}
instead of converting that to the following (which isn’t doing what you wanted, as the method will run entirely synchronously due to a lack of awaits):
async Task<int> DoWorkAsync()
{
… // same code as in the synchronous method
}
Read more: Parallel Programming with .NET
QR: 
Turning to the past to power Windows' future: An in-depth look at WinRT
Posted by
jasper22
at
09:59
|
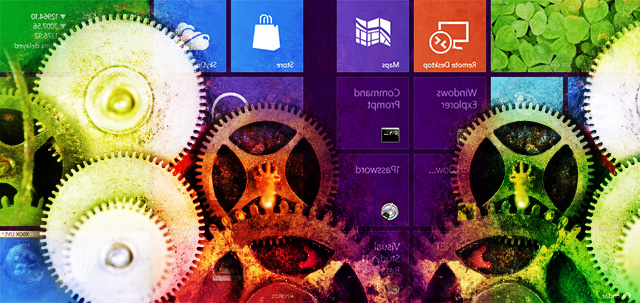
With its new tablet-friendly user interface, Windows 8 is going to be a revolution for both desktop users and tablet users alike. These substantial user interface changes are paired with extensive changes beneath the operating system's surface. For both developers and users, Windows 8 will be the biggest change the Windows platform has ever undergone.
In the wake of the first demonstrations of Windows 8 in mid-2011, some unfortunate word choices left many developers concerned that Windows 8 would force them to use Web technologies—HTML and JavaScript—if they wanted to write tablet-style applications using the new Windows user interface. We thought something altogether more exciting was in the cards: we felt Windows 8 would be a platform as ambitious in its scale as the (abandoned) Windows "Longhorn" project once was. At its BUILD conference in September 2011, Microsoft unveiled Windows 8 for real and talked about application development on the new operating system. The company proclaimed it to be an entirely new, entirely different way of developing applications. Our predictions were apparently confirmed and then some.
Closer inspection reveals a more complex picture. Windows 8 is a major release, and it is very different from the Windows before it. And yet it's strangely familiar: when you peek under the covers of the new user interface and look at how it all works, it's not quite the revolution that Microsoft is claiming it to be.
Read more: ArsTechnica
QR: 
Unity3d, в помощь начинающим
Posted by
jasper22
at
09:30
|

Эта статья предназначена для тех пользователей unity3d, что уже хорошо знакомы с самим движком, но ещё не обладают достаточной собственной базой знаний для того, чтобы писать без дополнительного сёрфинга по интернету, с целью поиска возникающих иногда фундаментальных вопросов. Чтобы сократить некоторым время на ресёч, расскажу несколько важных фишек, которые необходимо знать каждому unity программисту. Если у Вас возникают вопросы: как сделать чтобы у Вас не тормозило на чём-то послабее iPad 3, или Вы не знаете как удобно работать со спрайтами, как заставить музыку не прерываться при загрузке, или как обойти максимальный допустимый размер под android (50 мегабайт) и так далее, возможно Вы найдёте ответ в этой статье.
Статья затрагивает лишь проблемы мобильной разработки (IOS, Android). Все примеры только на C#.
Автор статьи не претендует на абсолютную категоричность и правильность предложенных решений.
Основы основ
1) Обязательно почитайте рекомендации от разработчиков Unity, как писать оптимальные с точки зрения производительности скрипты.
2) Лучше всего создать класс, прямой наследник от MonoBehaviour, который реализует кеширование transform и остальных подобных свойств MonoBehavior, все основные скрипты наследовать от него:
Код с примером кэширования
3) Используйте для хранения глобальных параметров своей игры статический класс со статическими методами и полями (если конечно данные не должны быть сохранены при закрытии игры, тогда пользуйте PlayerPrefs) но такой объект должен быть всего один, не увлекайтесь. Храните в нем только такие глобальные вещи, как текущее состояние игры (игра на паузе; мы в меню; cписок доступных пёрхейзов с их ценами, полученный с сервера и т.п.)
Read more: Habrahabr.ru
QR: 
Делаем простую игру с кнопками, ящиками и дверями на Unity
Posted by
jasper22
at
09:29
|
Read more: Habrahabr.ru
QR: 
Mono Improves Aync Support and MonoDevelop Adds NuGet
NuGet on MonoDevelop
MonoDevelop recently received support to use the NuGet package manager. MonoDevelop, the open source IDE, supports .NET development on Windows, Mac OS X, and various Linux distributions. NuGet provides developer's with a way to obtain extensions to their development environment from within their IDE.
With over 69,000 packages, NuGet is already popular with Visual Studio users. Thanks to Matt Ward's work, MonoDevelop users can now access this library. Developers who solely use MonoDevelop for their work can more easily access NuGet's offerings while those who MonoDevelop to manage cross-platform products that originated on Visual Studio can more easily keep their environment in sync.
Ward notes that while functional, this is a beta release and not all features of the original NuGet are yet supported. For example, as PowerShell is not supported by Mono, any PowerShell scripts included with NuGet packages will not be run.
Mono 3.0.3 Released
Read more: InfoQ
QR: 
Sorting C# collections that have no collating sequence
Posted by
jasper22
at
14:02
|
This Tip/Trick is an alternative to the original tip Sorting using C# Lists[^].
You often face the issue that a given class has not one Collating Sequence[^] but many various ways to order the class objects. This alternative tip shows how to choose the ordering without depending on the class implementing IComparable[^].
Sorting alternatives to "hard coded" IComparable dependency
A class that has no natural Collating Sequence[^] should not implement IComparable<T>. Instead, one should use a per case defined ordering. Some concise solutions are shown below. They do not need any definition of any additional IComparer class nor do they require the element class to implement IComparable.
By LINQ means
Sorting by LINQ is as follows:
var querySortedByProperty = from element in collection
orderby element.property
select element;
foreach(var item in querySortedByProperty) { ... }
By Enumerable extension methods
Sorting equivalent to LINQ by Enumerable[^] extension method calls:
var querySortedByProperty = collection.OrderBy(e=>e.property);
foreach(var item in querySortedByProperty) { ... }
By Sorting overload
Sorting a colleciton is also possible by a Sort overload that takes a delegate for ordering the elements of the collection:
collection.Sort((a,b)=>a.property.CompareTo(b.property));
foreach(var item in colleciton) { ... }
Using the code
Assuming the following class analogous to the one from the original tip without implementing IComparable<T>.
Read more: Codeproject
QR: 
SSIS Checking File/Folder Permissions
Posted by
jasper22
at
09:30
|
Recently I've been working on optimizing some SSIS packages. Part of this optimization was to delete files once they have been processed. I already knew the Proxy account had access to read the files from a directory but wasn't quite sure if the account had permissions to delete files. So Script Task to the rescue...
Below you will find the code that I've used to check if the user does have the required permissions (ReadData and Delete) to perform the tasks it's required to do. The script task is the first item in the control flow as I don't want all the other workflows to be executed if the permission isn't there to remove the files.
25: public void Main()
26: {
27: string path = Dts.Variables["inpSourceDirectory"].Value.ToString();
28: // Use WindowsIdentity as ssis packages run under a credential so will pick up the user executing the package
29: string NTUser = System.Security.Principal.WindowsIdentity.GetCurrent().Name;
30:
31: Boolean HasReadData = false, HasDelete = false;
32:
33: try
34: {
35: DirectoryInfo di = new DirectoryInfo(path);
36:
37: // Check the folder actually exists
38: if (!di.Exists)
39: throw new System.IO.DirectoryNotFoundException("The folder " + path + "does not exist. Check the folder path variable is correct");
40:
41: // Directory Security throws a PrivilegeNotHeldException if AccessControlSections is All so use Access
42: DirectorySecurity ds = di.GetAccessControl(AccessControlSections.Access);
43: AuthorizationRuleCollection rules = ds.GetAccessRules(true, true, typeof(System.Security.Principal.NTAccount));
44:
45: // Go through the rules returned from the directory security
46: #region Authorization Rules
47:
48: foreach (AuthorizationRule authorizationRule in rules)
49: {
50: // We're only interested in the current NTUser
51: if (authorizationRule.IdentityReference.Value.Equals(NTUser, StringComparison.CurrentCultureIgnoreCase))
52: {
53: // Assign Rules
54: FileSystemAccessRule CheckRules = (FileSystemAccessRule)authorizationRule;
55:
56: foreach (string right in Enum.GetNames(typeof(FileSystemRights)))
57: {
58: #region ReadData Right
59: // Check if NTuser has ReadData File System Right
60: if (right == "ReadData")
61: {
62: int val = Convert.ToInt32(Enum.Parse(typeof(FileSystemRights), right));
63: // remove combined values
64: if ((val != 0x1f01ff) && (val != 0x301bf) && (val != 0x20089) && (val != 0x200a9) && (val != 0x116))
65: {
66: if (((int)CheckRules.FileSystemRights & val) > 0)
67: HasReadData = true;
68: }
QR: 
Life changing XAML tip for Visual Studio
Posted by
jasper22
at
08:52
|
If you've worked with XAML in Visual Studio 2008 (SP1), either for WPF or Silverlight work, you know how painful it is.
Of course, the first thing to do is to get rid of the design view. It's slow as a snail and it's pretty useless anyway.
Make yourself a favor, and check "Always open documents in full XAML view" in "Tools | Options | Text Editor | XAML | Miscellaneous".
Even if this a great improvement, you'll soon realize that Visual Studio still sucks up a lot of your time and energy when you switch to a XAML file in the text editor. The same happens when you switch back to Visual Studio from another application. Now, try to open two XAML files side-by-side and the time to display them doubles. Same thing when you switch between two XAML files.
What the heck, there's gotta be a solution to this damnation! How could we develop good WPF or Silverlight applications if this XAML editor keeps getting on our nerves?
I've been enduring this for a long time. I had tried to edit the XAML file as an XML file, but this disabled IntelliSense, for some reason. So the XML editor was not an option.
Read more: Fabrice's weblog
QR: 
Accessing an API through a closed source C++ DLL
Introduction
This article describes a useful technique for using a closed source C++ DLL, loaded at run-time, to access an API for a popular consumer peripheral. It’s assumed the developer does not have access to import libraries or source code.
Background
This is a technical follow-up to my Continuum blog post describing how I automated a simple software task to enable an automatic pan-and-zoom feature of a consumer webcam that didn't provide an API. We needed to do this without disturbing the user experience, so standard program automation tools like AutoIt were off the table.
Throughout the process, I realized some of the pitfalls in making calls on C++ DLLs and identified workarounds. The inspiration for this article was a blog post from Recx Ltd, Working with C++ DLL Exports without Source or Headers. An example project is provided, but our specific case relied on a proprietary DLL that could not be included due to licensing.
API Monitor is an invaluable tool for monitoring the activity of API calls. It has more comprehensive features for Windows API calls, but it can also be used to view calls to external DLLs. You can spawn processes
from within the tool or attach to a running process. The state of the call stack can be seen before and after API calls are made, return values are visible, and it even provides breakpoint functionality.
With API Monitor, I spawned an instance of the web cam controller application, which allowed me to see which DLLs were being loaded. Monitoring from process execution (as opposed to attaching to running process) can be important when trying to see initialization behavior.
The module dependency view revealed a large list of DLLs. Most of them were Windows system DLLs or related to the Qt framework. One in particular stood out for what we needed: CameraControls_Core.dll. I set up the API Monitor to log all calls to this DLL and this was the relevant output:
LWS::CameraControls::CameraControls_Core::Init ( ... )
LWS::CameraControls::CameraControls_Core::GetCurrentVideoDevice ( ... )
LWS::CameraControls::CameraControls_Core::SetCurrentVideoDevice ( ... )
LWS::CameraControls::CameraControls_Core::GetFaceTracking ( ... )
Monitoring the API activity live, I checked and unchecked the facial recognition box. I noticed calls to SetFaceTracking () were being made. A quick look at the call stack revealed Boolean values being sent as parameters to the method. I used the Microsoft dumpbin utility on CameraControls_Core.dll to view the exported method list. It was quickly evident that I was dealing with a C++ DLL (due to the use of name decoration).
The method names were like so:
1 0 00001366 ??0CameraControls_Core@CameraControls@LWS@@QAE@XZ
2 1 000015C3 ??1CameraControls_Core@CameraControls@LWS@@UAE@XZ
3 2 00038740 ??_7CameraControls_Core@CameraControls@LWS@@6B@
I ran the output of the dumpbin tool into Microsoft’s undname utility to undecorate the names.
Read more: Codeproject
QR: 
C++ bindings for monotouch using SWIG
Posted by
jasper22
at
14:01
|
I love bindings. I've always loved them. Back in the days, I was binding gtk+ and other gobject libs to C# for fun and f-spot usage. Then I bound some obj-C libs to monotouch for a client and some for pleasure.
But last week I faced something new. I wanted to bind (for monotouch) a C++ iPhone lib for which I only received the binaries and the headers files. The component was too large to even think about doing a manual C glue code. I googled about the possible solutions and the only valuable advice was to use SWIG, without any rationale or tutorial. This is then probably a first. An explanation on why SWIG can help you for this, the problem I ran into and the solutions I found.
Mono.Cxxi is sexy, but not all-purpose
I'm not the kind of guy who blindly follows recommendations, so my first try was to use anything but SWIG. I opted for Mono.Cxxi and created a full binding in a few hours. It was really easy after I figured out the gcc-xml installation steps and caveats with clang. But when I first tried to use inside my monotouch project, it was to no avail. A quick reality-check confirmed my fears:

That being said, Mono.Cxxi is great stuff, check it out. But don't count on it for static AOT.
Go SWIG
Miguel was, once again right. SWIG was the only sensible option. I've used SWIG in the 90's for python (iirc), and it looks like the website hasn't left this era. But that's for the surface only. The tool is quite capable, is well suited for .NET and you can customise it to your liking. There's even a tutorial so I won't cover the basics.
Read more: Stephane's log
QR: 
Scrum — реальный опыт работы по методологии
Posted by
jasper22
at
13:05
|
В данной статье я привожу обзор организации процесса создания программного обеспечения в команде, в которой работаю. Моя цель – это поделиться опытом разработки и управления командой разработчиков.
Для организации процесса работ над проектом мы решили выбрать популярную методологию Scrum. Отчасти это дань моде, отчасти большое количество публикаций в сети Интернет на тему «Scrum сделал за нас все!».
Какие роли есть в Scrum
С чего обычно начинается разработка программного обеспечения? С идеи: «Как было бы замечательно, если бы у меня было некое ПО, которое делало бы примерно вот это. Было бы просто супер!» Человека, который в команде будет представлять эту идею, называют Product Owner (PO) или Владелец продукта. Product Owner – это тот, кто видит цель продукта или кому кажется, что он видит цель продукта, но важно то, что он может ее сформулировать и начать процесс движения к ее достижению. Цель он формирует в виде списка своих пожеланий (хотелок). Этот список называется Product Backlog Items (PBI). Он постоянно модифицируется в зависимости ситуации на рынке или от разрастающегося аппетита Product Owner'a.
Команда. По Scrum считается, что наибольшая эффективность разработки достигается в том случае, если команда сама будет самостоятельно принимать решения в отношении того, как она будет двигаться к цели. Поэтому основное требование к команде – она должна быть самоорганизующейся и самоуправляемой. Обеспечьте одно это требование, и этого будет достаточно для успеха проекта. Так как требование серьезное, то в команду вводится роль ScrumMaster’a, который следит за тем, чтобы соблюдались правила Scrum.
Что такое спринт и зачем он нужен
ProductOwner сформулировал свою цель в виде некого пункта B, который нужно достичь, начав движение с пункта A. Но пункт B – это не точка, в которую можно попасть, просто нарисовав прямую линию между ней и пунктом А. На самом деле пункт B это окрестность точки, и радиус ее может варьироваться.

Read more: Habrahabr.ru
QR: 
The Exceptional Beauty of Doom 3’s Source Code
Posted by
jasper22
at
11:05
|
This is a story about Doom 3's source code and how beautiful it is. Yes, beautiful. Allow me to explain.
After releasing my video game Dyad I took a little break. I read some books and watched some movies I'd put off for too long. I was working on the European version of Dyad, but that time was mostly waiting for feedback from Sony quality assurance, so I had a lot of free time. After loafing around for a month or so I started to seriously consider what I was going to do next. I wanted to extract the reusable/engine-y parts of Dyad for a new project.
When I originally started working on Dyad there was a very clean, pretty functional game engine I created from an accumulation of years of working on other projects. By the end of Dyad I had a hideous mess.
In the final six weeks of Dyad development I added over 13k lines of code. MainMenu.cc ballooned to 24,501 lines. The once-beautiful source code was a mess riddled with #ifdefs, gratuitous function pointers, ugly inline SIMD and asm code—I learned a new term: "code entropy." I searched the internet for other projects that I could use to learn how to organize hundreds of thousands of lines of code. After looking through several large game engines I was pretty discouraged; the Dyad source code wasn't actually that bad compared to everything else out there!
Unsatisfied, I continued looking, and found a very nice analysis of id Software's Doom 3 source code by the computer expert Fabien Sanglard.
Read more: Kotaku
QR: 
NTLM 100% Broken Using Hashes Derived From Captures
Posted by
jasper22
at
11:02
|
Security researcher Mark Gamache has used Moxie Marlinspike's Cloudcracker to derive hashes from captured NTLM handshakes, resulting in successful pass-the-hash attacks. It's been going on for a long time, probably, but this is the first time a 'white hat' has researched and exposed the how-to details for us all to enjoy. 'You might think that with all the papers and presentations, no one would be using NTLM...or, God forbid, LM. NTLMv2 has been around for quite some time. Surely, everyone is using it. Right? Wrong! According to the last data from the W3 Schools, 21% of computers are running XP, while NetMarketShare claims it is 39%. Unless someone has hardened these machines (no MS patches do this), these machines are sending LM and NTLM responses!' Microsoft has posted a little guidance for those who need to turn off NTLM. Have fun explaining your new security project to your management, server admins!
Read more: Slashdot
QR: 
Storage made easy (SME)
Posted by
jasper22
at
10:54
|
Cloud File Server
The Cloud File Server is a multi-tenant user system that features access control permissions, file locking, event auditing and can be used natively as a Cloud drive on any desktop and from any mobile device.
Read more: Storage made easy
QR: 
Alan Cox Calls Fedora 18 "The Worst Red Hat Distro"
Posted by
jasper22
at
10:38
|
Alan Cox, the venerable Linux kernel developer presently employed by Intel and an avid open-source enthusiast, has lashed out against the recent release of Fedora 18. Cox calls the new Fedora release, "the worst Red Hat distro I've ever seen." Alan ended up switching to Ubuntu as a result of his disastrous experience with Fedora 18.
On his Google+ page yesterday, Alan Cox wrote:
So Fedora 18 seems to be the worst Red Hat distro I've ever seen.The new installer is unusable, the updater is buggy. When you get it running the default desktop has been eviscerated to the point of being slightly less useful than a chocolate teapot, and instead of fixing the bugs in it they've added more.It can't even manage to write valid initrds for itself instead on one machine of simply bombing into a near undebuggable systemd error (same kernel with F17 and F17 dracut works so its the dracut stuff)systemd-cryptosetup-generator: Failed to create unit file .... : File existsYeah wonderful. Time to re-install that box, and not with Fedora.
In another post later in the day, Cox wrote:
Ok so problem box switched to UbuntuMost stuff seems to have gone fine so far. The cunning plan to do some jitsu with the VM I decided against in the end - its doable but the VM thinks its on /dev/vda1 and /dev/vda1 is in fact an encrypted volume across a two disk md on the real host so fiddly.It's mostly behaving but the monitor configuration tools suck and are so buggy I took joe to monitors.xml instead. The biggest problem though was the orange.. that had to go. It's now blue - something Fedora gets right ;-)OpenSCAD is out of date (ok thats mean the new one is only a week or so old)Gnome3 on Ubuntu sucks too so I stuck Cinammon on it.Now to poke at the snag list
The past week I have been carrying out many Fedora 18 installations as I run various benchmarks on the much-delayed distribution: Fedora 18 Systemd Boot Performance Is Mixed, AMD R600 Gallium3D Is Mixed On Fedora 18, Intel Graphics See Some Gains On Fedora 18, and Fedora 18 Fails At ARM Wrestling Arch, Ubuntu, Linaro. (Many more performance benchmarks of Fedora 18 and compared to other Linux distributions are also on the way.)
Read more: Phoronix
QR: 
Barracuda Appliances Have Exploitable Holes, Fixed By Firmware Updates
Posted by
jasper22
at
10:33
|
Barracuda Networks has released firmware updates that remove SSH backdoors in a number of their products and resolve a vulnerability in Barracuda SSL VPN that allows attackers to bypass access restrictions to download potentially insecure files, set new admins passwords, or even shut down the device. The backdoor accounts are present on in all available versions of Barracuda Spam and Virus Firewall, Web Filter, Message Archiver, Web Application Firewall, Link Balancer, Load Balancer, and SSL VPN appliances.
Read more: Slashdot
QR: 
Attacking the Windows 7/8 Address Space Randomization
Posted by
jasper22
at
09:09
|
Microsoft upped its security ante with Address Space Layout Randomization (ASLR) in Windows 7 and Windows 8, but it seems this mechanism to prevent hackers from jumping to a known memory location can be bypassed. A hacker has released a brilliant, yet simple trick to circumvent this protection. KingCope, a hacker who released several exploits targeting MySQL in December, has detailed a mechanism through which the ASLR of Windows 7, Windows 8 and probably other operating systems can be bypassed to load a DLL file with malicious instructions to a known address space.
Read more: Slashdot
Read more: kingcopes´ blag
QR: 
Subscribe to:
Comments (Atom)


