Official site: HaveYourFriendsBeenThere
HaveYourFriendsBeenThere: Remotely check any browser history for naughty sites
Do you want to know which of your friends have been looking at naughty websites? Or perhaps you want to know who among your coworkers have been visiting NSFW websites while at work? Then you should check out HaveYourFriendsBeenThere? It is a web tool that enables you remotely snoop into someones browser history and check for naughty websites. Read more: Make use of
Official site: HaveYourFriendsBeenThere
Official site: HaveYourFriendsBeenThere
Top Ten One-Liners from CommandLineFu Explained
I love working in the shell. Mastery of shell lets you get things done in seconds, rather than minutes or hours, if you chose to write a program instead. In this article I’d like to explain the top one-liners from the commandlinefu.com. It’s a user-driven website where people get to choose the best and most useful shell one-liners. #1. Run the last command as root$ sudo !!We all know what the sudo command does - it runs the command as another user, in this case, it runs the command as superuser because no other user was specified. But what’s really interesting is the bang-bang !! part of the command. It’s called the event designator. An event designator references a command in shell’s history. In this case the event designator references the previous command. Writing !! is the same as writing !-1. The -1 refers to the last command. You can generalize it, and write !-n to refer to the n-th previous command. To view all your previous commands, type history. This one-liner is actually really bash-specific, as event designators are a feature of bash.I wrote about event designators in much more detail in my article “The Definitive Guide to Bash Command Line History.” The article also comes with a printable cheat sheet for working with the history. #2. Serve the current directory at http://localhost:8000/$ python -m SimpleHTTPServerThis one-liner starts a web server on port 8000 with the contents of current directory on all the interfaces (address 0.0.0.0), not just localhost. If you have “index.html” or “index.htm” files, it will serve those, otherwise it will list the contents of the currently working directory. It works because python comes with a standard module called SimpleHTTPServer. The -m argument makes python to search for a module named SimpleHTTPServer.py in all the possible system locations (listed in sys.path and $PYTHONPATH shell variable). Once found, it executes it as a script. If you look at the source code of this module, you’ll find that this module tests if it’s run as a script if __name__ == '__main__', and if it is, it runs the test() method that makes it run a web server in the current directory. To use a different port, specify it as the next argument:$ python -m SimpleHTTPServer 8080This command runs a HTTP server on all local interfaces on port 8080.#3. Save a file you edited in vim without the needed permissions :w !sudo tee %This happens to me way too often. I open a system config file in vim and edit it just to find out that I don’t have permissions to save it. This one-liner saves the day. Instead of writing the while to a temporary file :w /tmp/foobar and then moving the temporary file to the right destination mv /tmp/foobar /etc/service.conf, you now just type the one-liner above in vim and it will save the file. Here is how it works, if you look at the vim documentation (by typing :he :w in vim), you’ll find the reference to the command :w !{cmd} that says that vim runs {cmd} and passes it the contents of the file as standard input. In this one-liner the {cmd} part is the sudo tee % command. It runs tee % as superuser. But wait, what is %? Well, it’s a read-only register in vim that contains the filename of the current file! Therefore the command that vim executes becomes tee current_filename, with the current directory being whatever the current_file is in. Now what does tee do? The tee command takes standard input and write it to a file! Rephrasing, it takes the contents of the file edited in vim, and writes it to the file (while being root)! All done! #4. Change to the previous working directory$ cd -Everyone knows this, right? The dash “-” is short for “previous working directory.” The previous working directory is defined by $OLDPWD shell variable. After you use the cd command, it sets the $OLDPWD environment variable, and then, if you type the short version cd -, it effectively becomes cd $OLDPWD and changes to the previous directory. To change to a directory named “-“, you have to either cd to the parent directory and then do cd ./- or do cd /full/path/to/-.#5. Run the previous shell command but replace string “foo” with “bar”Read more: catonmat.net
How to Add Google Analytics to Your Facebook Fan Page
Posted by
jasper22
at
14:16
|
You’ve created a Facebook fan page and people are frequenting your page. But do you really know how many people visit your page, what areas are popular and what parts of the world your visitors come from? Facebook Insights shows some demographic information on your page, but is limited to information about interactions with your fans. The free Google Analytics tool offers more sophisticated and comprehensive data. Adding Google Analytics to your fan page can be done easily but requires some special steps. One of the limitations of Facebook fan pages is they can only run limited JavaScript. Google Analytics needs JavaScript code included on a page to correctly track visitors in the traditional way. And running JavaScript won’t work on your fan page… However, there is a new solution. Using free and opensource FBGAT (Facebook Google Analytics Tracker), you can get Google Analytics working on your Facebook fan page. Now you can track visitor statistics, traffic sources, visitor countries, and keyword searches with all the other powerful reporting of Google Analytics. Read more: SocialMedia examiner
Free anti-virus scanner hits the cloud
Posted by
jasper22
at
14:15
|
Avira has added cloud technology to the latest version of its popular freebie anti-virus scanner.Version 10 of Avira AntiVir, released on Tuesday, adds cloud-based detection to a free-of-charge security scanner that competes with similar products offered by (Czech-firm ALWIL's) Avast and AVG. All three firms aim to move consumers to fuller featured paid-for security suites as well as selling security software pitched at the SME end of the business market. Each of the three has had to step up its game following the release of Microsoft's Security Essentials freebie scanner last September. The incorporation of cloud-based technologies is an industry trend across paid-for and now freebie scanners designed to respond to the growing volume of malware variants (50,000 a day, according to industry estimates) produced by the bad guys. Traditional techniques, like pushing revised signature detection files from central servers, are struggling to cope, hence the need to switch architectures to add crowd-sourced malware detection to the mix.Read more: The Register
Google releases free tool to migrate from Microsoft Exchange to Google Apps
Posted by
jasper22
at
13:01
|
Rejoice, small-, medium- and enterprise-size users of Microsoft Exchange! You can now migrate your company's entire database of contacts, emails and calendars to Google Apps. The tool takes the form of a small app that you can download from Google -- all you have to do is install it, run it... and that's it! It works with both Exchange 2003 and 2007, and you need to be a Google Apps Premier or Education Edition customer, but other than that... it's free, quick and seemingly painless -- employees can even use Exchange during the migration. Incidentally, if you're thinking about 'Going Google', it'll cost you $50/year per user (details here)... 'and it's never been easier!' Read more: DownloadSquad
Etacts Adds Contact Info, Social Networking, and Handy Statistics to Your Gmail Sidebar
Posted by
jasper22
at
12:59
|

If you ever thought previously mentioned Xobni looked cool, but you prefer Gmail to Outlook, free Gmail plug-in Etacts adds many of the same features. You get social information, conversation history, and advanced sending preferences right in your Gmail sidebars. The Etacts plug-in automatically adds detailed contact information to the sidebar of messages, as shown above, similar to previously mentioned Rapportive, but Etacts takes it one step further. Not only do you get links to any social networks that contact is a part of, and some of the information contained therein (such as their occupation and location), but you also get a detailed summary of your mailing history with them, complete with nice little graphs and charts. All this information is also available in compose mode as well, so you know exactly who you're sending it to. Read more: Lifehacker
Clever desktop wallpaper ?
Posted by
jasper22
at
11:31
|
 www.i-am-bored.com/media/16571_bestscreensaverever.jpg" alt="16571_bestscreensaverever.jpg" />Read more: I-am-bored
www.i-am-bored.com/media/16571_bestscreensaverever.jpg" alt="16571_bestscreensaverever.jpg" />Read more: I-am-bored Gmail Detects and Warns You If Someone Else Is Using Your Account
Posted by
jasper22
at
11:29
|

Gmail launched a new feature this morning designed to detect suspicious activity in your account and notify you when a suspicious login has occurred in your account. Read more: Lifehacker
Law Enforcement Appliance Subverts SSL
Posted by
jasper22
at
10:59
|
That little lock on your browser window indicating you are communicating securely with your bank or e-mail account may not always mean what you think its means.Normally when a user visits a secure website, such as Bank of America, Gmail, PayPal or eBay, the browser examines the website’s certificate to verify its authenticity. At a recent wiretapping convention, however, security researcher Chris Soghoian discovered that a small company was marketing internet spying boxes to the feds. The boxes were designed to intercept those communications — without breaking the encryption — by using forged security certificates, instead of the real ones that websites use to verify secure connections. To use the appliance, the government would need to acquire a forged certificate from any one of more than 100 trusted Certificate Authorities. The attack is a classic man-in-the-middle attack, where Alice thinks she is talking directly to Bob, but instead Mallory found a way to get in the middle and pass the messages back and forth without Alice or Bob knowing she was there. The existence of a marketed product indicates the vulnerability is likely being exploited by more than just information-hungry governments, according to leading encryption expert Matt Blaze, a computer science professor at University of Pennsylvania. “If the company is selling this to law enforcement and the intelligence community, it is not that large a leap to conclude that other, more malicious people have worked out the details of how to exploit this,” Blaze said. The company in question is known as Packet Forensics, which advertised its new man-in-the-middle capabilities in a brochure handed out at the Intelligent Support Systems (ISS) conference, a Washington, D.C., wiretapping convention that typically bans the press. Soghoian attended the convention, notoriously capturing a Sprint manager bragging about the huge volumes of surveillance requests it processes for the government. Read More: Wired
First Anti-Cancer Nanoparticle Trial on Humans a Success
Posted by
jasper22
at
10:56
|
Nanoparticles have been able to disable cancerous cells in living human bodies for the first time. The results are perfect so far, killing tumors with no side effects whatsoever. Mark Davis, project leader at CalTech, says that 'it sneaks in, evades the immune system, delivers the siRNA, and the disassembled components exit out.' Truly amazing. Read more: Slashdot
Creating a Simple ASP.NET MVC 2.0 Application
Posted by
jasper22
at
10:48
|
In this walkthrough I will show the major changes and add-ins we can find in ASP.NET MVC 2.0. Creating A simple ASP.NET MVC 2.0 Application. Open Visual Studio 2010 and create a new project from the ASP.NET MVC 2.0 web application template. A Wizard screen will pop up to ask whether we want to create a Unit-Test project with our MVC Application.Choose No. (I will show TDD with MVC 2.0 on a future Post)To make this walkthrough a little more interesting and easy to follow i will use the Microsoft Sample Database called Northwind : To provide and explain the MVC (Model – View – Controller) Approach will start with the part that handles the data : The Model.Right-Click on the Models folder and choose to add a new Item :Read more: Ignorance is bliss
Перенос ASP.NET приложения на Mono. Поддержка русского языка
Posted by
jasper22
at
10:47
|
Недавно перенёс небольшое ASP-приложение c .NET на Mono. Столкнулся с практически полным отсутствием поддержки русского языка при настройках по умолчанию. Использовалась связка Debian lenny (netinst) + Apache2 + mono-apache-server2. Решение проблем:Первая проблема: не отображается русский текст в теле ASPX-файловНа первом же тесте возникла проблема потери русских букв в теле ASPX.
Например такой файл:
<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Test.aspx.cs" Inherits="Test" %>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" >
<head runat="server">
<title>Test</title>
</head>
<body>
Тест русский.
</body>
</html>Read more: habrahabr.ru
Например такой файл:
<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Test.aspx.cs" Inherits="Test" %>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" >
<head runat="server">
<title>Test</title>
</head>
<body>
Тест русский.
</body>
</html>Read more: habrahabr.ru
How to store ViewState on the server - the *RIGHT* way!
Posted by
jasper22
at
10:42
|
Many have tried to implement serialization of ViewState on the server, and many have failed, which is quite easy to understand considering even Microsoft's reference documentation on this subject is in fact *WRONG*...! Of all the samples you find when you search for "storing ViewState on server in ASP.NET", virtually all the top ones are *WRONG*. Even Microsoft's reference documentation on this is wrong! Take a look at Microsoft's documentation for PageStatePersister for instance and try to find the bug. No wonder people are having a hard time implementing this feature. In fact if you do it the way described at Microsoft, and your solution depends upon upon ControlState, you will fail miserably...! I have historically argued against storing ViewState on the server, mostly because I've seen so many wrong solutions, like for instance some developers are storing their ViewState in the Session object. This is a *terrible* thing to do and should be never be done! And yes, I know Microsoft even have a "shortcut" for doing it, but you can't justify terrible code just because Microsoft gave you the tools to do it! Bad code is bad code, even when it's Microsoft code! When you store your ViewState in your Session object on the server, you're basically turning the most scalable and beautiful platform ever created [the web] and turning it into an Outlook client. Needless to say, scalability goes out the window, and a system that would normally be able to handle thousands of concurrent users, will break down if more than 5 people are using it simultaneously! So whenever people have asked me how to store the ViewState on the server, I've basically answered; *DON'T*...! Read more: ra-ajax.org
The platform-independent code with Mono: Client-server application sample
Posted by
jasper22
at
10:40
|
* Introduction
* 1. Requirements
* 2. Design
o 2.1 Architecture
o 2.2 Database schema
* 3. Implementation
o 3.1 TDD methodology and NUnit tool
o 3.2 Server
+ 3.2.1 Persistence layer
# Object-relation mapping and NHibernate
# Implementation
# Test cases
+ 3.2.2 Bussiness layer
+ 3.2.3 Presentation layer
o 3.3 Client
+ 3.3.1 Service or daemon
+ 3.3.2 Get system information
+ 3.3.3 Compress data
+ 3.3.4 Call web service
+ 3.3.5 Logging
* 4 Deployment
o 4.1 Database
+ 4.1.1 Ms Sql Server config
+ 4.1.2 MySql config
o 4.2 Client
+ 4.2.1 Windows
+ 4.2.2 Run ASP.NET site on Linux and Apache
* Conclusion
* HistoryIntroductionIn this article I want to show how we can develop the platform-independent software with Mono usage . I don’t consider what is Mono. If Mono is unfamiliar to you, look through my previous article – "How we can write on C# in Linux: Implementing PanelApplet to Gnome Desktop". The first three parts describe the developed software. The last part describes how we can deploy this software in different operating system and I think it is the most important part of the article. Read more: Codeproject
* 1. Requirements
* 2. Design
o 2.1 Architecture
o 2.2 Database schema
* 3. Implementation
o 3.1 TDD methodology and NUnit tool
o 3.2 Server
+ 3.2.1 Persistence layer
# Object-relation mapping and NHibernate
# Implementation
# Test cases
+ 3.2.2 Bussiness layer
+ 3.2.3 Presentation layer
o 3.3 Client
+ 3.3.1 Service or daemon
+ 3.3.2 Get system information
+ 3.3.3 Compress data
+ 3.3.4 Call web service
+ 3.3.5 Logging
* 4 Deployment
o 4.1 Database
+ 4.1.1 Ms Sql Server config
+ 4.1.2 MySql config
o 4.2 Client
+ 4.2.1 Windows
+ 4.2.2 Run ASP.NET site on Linux and Apache
* Conclusion
* HistoryIntroductionIn this article I want to show how we can develop the platform-independent software with Mono usage . I don’t consider what is Mono. If Mono is unfamiliar to you, look through my previous article – "How we can write on C# in Linux: Implementing PanelApplet to Gnome Desktop". The first three parts describe the developed software. The last part describes how we can deploy this software in different operating system and I think it is the most important part of the article. Read more: Codeproject
C# Snippet Tutorial - The checked and unchecked keywords
Posted by
jasper22
at
10:39
|
Every once and a while I run across a new C# keyword that I've never used before. Today it's checked and unchecked. Basically, these keywords control whether or not an exception will be thrown when an operation causes a number to overflow. First, let's check out unchecked. The unchecked keyword will prevent exceptions from being thrown if a number overflows. By default, .NET does not throw exceptions for overflows, which means the following use of unchecked has no affect. What the unchecked keyword can do, however, is prevent compilation errors if the value can be calculated at compile-time. If you attempt to set an integer equal to 2147483647 + 1, the compiler will throw an error since it knows that value won't fit in an int. // With an unchecked block, which is the
// default behavior, numbers will roll-over.
unchecked
{
// default behavior, numbers will roll-over.
unchecked
{
int i = int.MaxValue;
Console.WriteLine(i); //2147483647
i++;
Console.WriteLine(i); //-2147483648
}As you can see, I initialize an integer to its max value, then increment it by one. The value then rolls over to a negative number and no exception is thrown. If we switch the block to a checked block, we'll now get an exception. Read more: Switch on code Console.WriteLine(i); //2147483647
i++;
Console.WriteLine(i); //-2147483648
NPipeline
Posted by
jasper22
at
10:38
|
NPipeline is a .NET port of the Apache Commons Pipeline components. It is a lightweight set of utilities that make it simple to implement parallelized data processing systems.Data objects flowing through the pipeline are processed by a series of independent user-defined components called Stages . A pipeline may have a number of different branches of execution, each of which is a fully qualified Pipeline in its own right.
Project Status
This project is in Pre-Alpha state and not ready for production use. I essentially needed a place to host the project :-) * Component design - Done
* Pipeline construction and Lifecycle events - Done
* Base class implementations for Interfaces - Done
* Synchronous StageDriver - Done
* Unit Tests for Framework - DoneRead more: Codeplex
Project Status
This project is in Pre-Alpha state and not ready for production use. I essentially needed a place to host the project :-) * Component design - Done
* Pipeline construction and Lifecycle events - Done
* Base class implementations for Interfaces - Done
* Synchronous StageDriver - Done
* Unit Tests for Framework - DoneRead more: Codeplex
Investigating .NET Memory Management and Garbage Collection
Posted by
jasper22
at
10:38
|
We will be looking into the world of managed memory In this article. It is a world in that part of the CLR where the garbage collector is king. We will consider what a memory leak is, how the garbage collector works and why it cannot always free memory; we will then, finally and most excitingly, reveal how to examine both memory and specific objects using Son of Strike (SOS).
What is a memory leak?At its most basic, a memory leak happens when memory has been allocated and, for whatever reason, that memory is not freed when the application has finished using it. In a .Net language, you allocate memory by creating an object and you free the memory by allowing the reference to that object to go out of scope. Simply put: void MethodName()
{
What is a memory leak?At its most basic, a memory leak happens when memory has been allocated and, for whatever reason, that memory is not freed when the application has finished using it. In a .Net language, you allocate memory by creating an object and you free the memory by allowing the reference to that object to go out of scope. Simply put: void MethodName()
{
Object o = new Object(); //Create a new Object and store a reference to it as o
DoSomethingWith(o); //Use the new Object by passing the reference to o
o = null; //Lose the reference to the new Object, it is now eligible for freeing
} //o is now out of scope so can be freedWhen “o” goes out of scope, the garbage collector can examine the object to see if it has any references; if nothing is referencing the object, it can be freed. If the “DoSomethingWith” method caused a reference to be kept to “o” then, when the garbage collector checked to see if it was being used, there would still be a reference and so it would not be able to free the memory. Read more: simple-talk DoSomethingWith(o); //Use the new Object by passing the reference to o
o = null; //Lose the reference to the new Object, it is now eligible for freeing
How To Drop All Indexes From A Database
Posted by
jasper22
at
10:36
|
I was doing some performance tweaking of a batch job that was hanging and i was suspecting the indexes in the database to have something to do with it shocking up so I used this script to clear all indexes. Ironically it was a missing index that caused the bottleneck. But here it is for anyone that might need it.DECLARE @indexName VARCHAR(128)
DECLARE @tableName VARCHAR(128)DECLARE [indexes] CURSOR FOR SELECT [sysindexes].[name] AS [Index],
[sysobjects].[name] AS [Table] FROM [sysindexes] INNER JOIN [sysobjects]
ON [sysindexes].[id] = [sysobjects].[id] WHERE [sysindexes].[name] IS NOT NULL
AND [sysobjects].[type] = 'U'OPEN [indexes]FETCH NEXT FROM [indexes] INTO @indexName, @tableNameWHILE @@FETCH_STATUS = 0
BEGIN
PRINT 'DROP INDEX [' + @indexName + '] ON [' + @tableName + ']' FETCH NEXT FROM [indexes] INTO @indexName, @tableName
ENDCLOSE [indexes]
DEALLOCATE [indexes] Read more: Hatim’s Development Blog
DECLARE @tableName VARCHAR(128)DECLARE [indexes] CURSOR FOR SELECT [sysindexes].[name] AS [Index],
[sysobjects].[name] AS [Table] FROM [sysindexes] INNER JOIN [sysobjects]
ON [sysindexes].[id] = [sysobjects].[id] WHERE [sysindexes].[name] IS NOT NULL
AND [sysobjects].[type] = 'U'OPEN [indexes]FETCH NEXT FROM [indexes] INTO @indexName, @tableNameWHILE @@FETCH_STATUS = 0
BEGIN
PRINT 'DROP INDEX [' + @indexName + '] ON [' + @tableName + ']' FETCH NEXT FROM [indexes] INTO @indexName, @tableName
ENDCLOSE [indexes]
DEALLOCATE [indexes] Read more: Hatim’s Development Blog
Microsoft Connectors Version 1.1 for Oracle and Teradata by Attunity
Posted by
jasper22
at
10:35
|
Microsoft Connector Version 1.1 for Oracle by Attunity - The Oracle source and destination components are written to achieve optimal performance when loading data into Oracle or unloading data from Oracle in the context of Microsoft SSIS. Microsoft Connector Version 1.1 for Teradata by Attunity - The components are written to achieve optimal performance when loading data into Teradata or unloading data from Teradata in the context of Microsoft SSIS. Microsoft SSIS Connectors by Attunity Version 1.1 is a minor release. It includes performance enhancements, bug fixes, and continued improvements for ease of use.The following enhancements were made: * Performance Improvements for Oracle and Teradata Components
o Optimize conversion functions in the Oracle and Teradata source and destination components.
o A major performance enhancement for the Oracle destination component when set to work in fast-load mode. This was achieved by code optimization and removal of unnecessary overhead in the Oracle connector. * Additional Property Support for the Teradata Components
o Added support for the following properties in the Teradata destination:
– Robust: TPT Stream only
– ArraySupport: TPT Stream only.
– Buffers: TPT Stream only.
– BufferSize: TPT Load only.
– QueryBandSessionInfo
– DetailedTracingLevel o Added support for the following properties in the Teradata Source:
– BufferSize
– QueryBandSessionInfo
- DetailedTracingLevel * Support for TPT API Version 13 in the Teradata Components
Support was added for TPT API version 13 Edition 2 (13.0.0.2). Version 12 APIs are still supported. * Enhanced Logging for the Teradata Components
The DetailedTraceLevel property was added to the Teradata source and destination. This allows setting the TPT API tracing to different levels. Additional Property Support for the Teradata Components. * Query Banding is Supported by the Teradata Components
The Teradata source and destination support query banding. This allows charge back, monitoring, and governance. This is set by the new QueryBandSessionInfo property. See Additional Property Support for the Teradata Components. Read more: MS Download
o Optimize conversion functions in the Oracle and Teradata source and destination components.
o A major performance enhancement for the Oracle destination component when set to work in fast-load mode. This was achieved by code optimization and removal of unnecessary overhead in the Oracle connector. * Additional Property Support for the Teradata Components
o Added support for the following properties in the Teradata destination:
– Robust: TPT Stream only
– ArraySupport: TPT Stream only.
– Buffers: TPT Stream only.
– BufferSize: TPT Load only.
– QueryBandSessionInfo
– DetailedTracingLevel o Added support for the following properties in the Teradata Source:
– BufferSize
– QueryBandSessionInfo
- DetailedTracingLevel * Support for TPT API Version 13 in the Teradata Components
Support was added for TPT API version 13 Edition 2 (13.0.0.2). Version 12 APIs are still supported. * Enhanced Logging for the Teradata Components
The DetailedTraceLevel property was added to the Teradata source and destination. This allows setting the TPT API tracing to different levels. Additional Property Support for the Teradata Components. * Query Banding is Supported by the Teradata Components
The Teradata source and destination support query banding. This allows charge back, monitoring, and governance. This is set by the new QueryBandSessionInfo property. See Additional Property Support for the Teradata Components. Read more: MS Download
Shazzam
Posted by
jasper22
at
10:04
|
The goal of Shazzam is to make it simple to edit and test WPF Pixel Shader Effects. Shazzam compiles HLSL code, atuo- generates C#/VB classes and creates a testing page for each effect. Plus it supports animations of the effect. Learn more at http://shazzam-tool.com This is the source code site for Shazzam.For more information about Shazzam go to the companion site
http://shazzam-tool.comThere you will find more information about Shazzam. Also on the site are many demonstration videos. Read more: Codeplex
http://shazzam-tool.comThere you will find more information about Shazzam. Also on the site are many demonstration videos. Read more: Codeplex
Why TCP Over TCP Is A Bad Idea
Posted by
jasper22
at
10:01
|
A frequently occurring idea for IP tunneling applications is to run a protocol like PPP, which encapsulates IP packets in a format suited for a stream transport (like a modem line), over a TCP-based connection. This would be an easy solution for encrypting tunnels by running PPP over SSH, for which several recommendations already exist (one in the Linux HOWTO base, one on my own website, and surely several others). It would also be an easy way to compress arbitrary IP traffic, while datagram based compression has hard to overcome efficiency limits. Unfortunately, it doesn't work well. Long delays and frequent connection aborts are to be expected. Here is why.
TCP's retransmission algorithmTCP divides the data stream into segments which are sent as individual IP datagrams. The segments carry a sequence number which numbers the bytes in the stream, and an acknowledge number which tells the other side the last received sequence number. [RFC793] Since IP datagrams may be lost, duplicated or reordered, the sequence numbers are used to reassemble the stream. The acknowledge number tells the sender, indirectly, if a segment was lost: when an acknowledge for a recently sent segment does not arrive in a certain amount of time, the sender assumes a lost packet and re-sends that segment. Many other protocols using a similar approach, designed mostly for use over lines with relatively fixed bandwidth, have the "certain amount of time" fixed or configurable. In the Internet however, parameters like bandwidth, delay and loss rate are vastly different from one connection to another and even changing over time on a single connection. A fixed timeout in the seconds range would be inappropriate on a fast LAN and likewise inappropriate on a congested international link. In fact, it would increase the congestion and lead to an effect known as "meltdown". For this reason, TCP uses adaptive timeouts for all timing-related parameters. They start at conservative estimates and change dynamically with every received segment. The actual algorithms used are described in [RFC2001]. The details are not important here but one critical property: when a segment timeouts, the following timeout is increased (exponentially, in fact, because that has been shown to avoid the meltdown effect).
Stacking TCPsThe TCP timeout policy works fine in the Internet over a vast range of different connection characteristics. Because TCP tries very hard not to break connections, the timeout can increase up to the range of several minutes. This is just what is sensible for unattended bulk data transfer. (For interactive applications, such slow connections are of course undesirable and likely the user will terminate them.) Read more: Why TCP Over TCP Is A Bad Idea
TCP's retransmission algorithmTCP divides the data stream into segments which are sent as individual IP datagrams. The segments carry a sequence number which numbers the bytes in the stream, and an acknowledge number which tells the other side the last received sequence number. [RFC793] Since IP datagrams may be lost, duplicated or reordered, the sequence numbers are used to reassemble the stream. The acknowledge number tells the sender, indirectly, if a segment was lost: when an acknowledge for a recently sent segment does not arrive in a certain amount of time, the sender assumes a lost packet and re-sends that segment. Many other protocols using a similar approach, designed mostly for use over lines with relatively fixed bandwidth, have the "certain amount of time" fixed or configurable. In the Internet however, parameters like bandwidth, delay and loss rate are vastly different from one connection to another and even changing over time on a single connection. A fixed timeout in the seconds range would be inappropriate on a fast LAN and likewise inappropriate on a congested international link. In fact, it would increase the congestion and lead to an effect known as "meltdown". For this reason, TCP uses adaptive timeouts for all timing-related parameters. They start at conservative estimates and change dynamically with every received segment. The actual algorithms used are described in [RFC2001]. The details are not important here but one critical property: when a segment timeouts, the following timeout is increased (exponentially, in fact, because that has been shown to avoid the meltdown effect).
Stacking TCPsThe TCP timeout policy works fine in the Internet over a vast range of different connection characteristics. Because TCP tries very hard not to break connections, the timeout can increase up to the range of several minutes. This is just what is sensible for unattended bulk data transfer. (For interactive applications, such slow connections are of course undesirable and likely the user will terminate them.) Read more: Why TCP Over TCP Is A Bad Idea
Mafia Boss Betrayed By Facebook
One of Italy's 100 most-wanted criminals, a vicious mafia boss who had been on the run for months, was betrayed by his passion for social networking and flushed out thanks to Facebook. Using the name 'Scarface' from the gangster movie starring Al Pacino, Pasquale Manfredi, 33, a boss of the the ferocious 'Ndrangheta mafia organization from the Calabria region in southern Italy, had logged on to his Facebook account so often that police were able to trace the signal from his Internet key and find his hideout.' Seems the Mafia Wars Facebook phenomenon goes deeper than it seemed! Read more: New York Post
Lock Files and Folders in Windows Without Extra Software
Posted by
jasper22
at
16:38
|
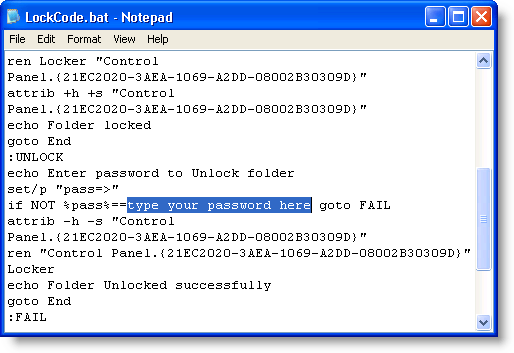
We have previously written about a utility used to lock files and folders in Windows, How to Protect and Lock Folders in Windows. Here is a method for locking files and folders without having to install a third-party software program. Download the following text file, which contains the code for the batch file:LockCode.txtOpen the file in Notepad. Replace “type your password here” in the LockCode.bat file with the password you want to use to lock and unlock the protected files and folders. DO NOT forget this password. Save the file as LockCode.bat. NOTE: We realize this seems unsecure to enter your password in plain text into a text file, but this will be discussed later.Read more: Help desk geek
Optical illusions - the brain just sees what it expects to see
Posted by
jasper22
at
16:25
|
Another example of how the brain just fills in the missing blanks . Unless you are one of the 0.7% of people who suffer from schizophrenia, you are unable to instruct your brain to see the hollow side of the rotating mask.
Remember the lazy visual brain when designing slides. The brain tends to follow lines in the reading direction, and sometimes finds it hard to spot the word "not" in a sentence, just to name a few examples. Read more: sticky slides
View video: Charlie Chaplin optical illusion (Youtube)
Remember the lazy visual brain when designing slides. The brain tends to follow lines in the reading direction, and sometimes finds it hard to spot the word "not" in a sentence, just to name a few examples. Read more: sticky slides
View video: Charlie Chaplin optical illusion (Youtube)
Conficker Eye Chart
Posted by
jasper22
at
16:05
|
How to know if you infected with Conficker virus by imagesRead more: Conficker Eye Chart
Use Advanced Font Ligatures in Office 2010
Posted by
jasper22
at
16:01
|
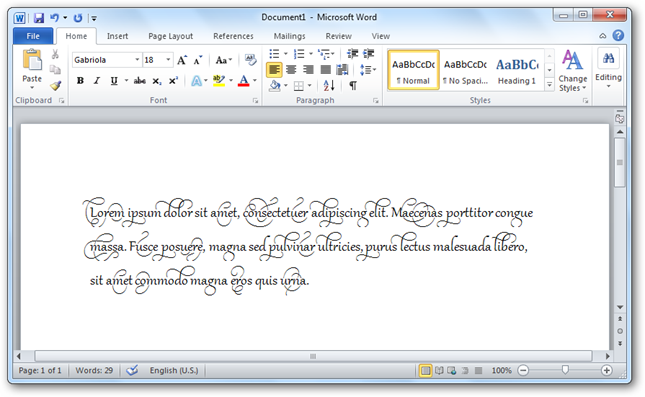
Fonts can help your documents stand out and be easier to read, and Office 2010 helps you take your fonts even further with support for OpenType ligatures, stylistic sets, and more. Here’s a quick look at these new font features in Office 2010. IntroductionStarting with Windows 7, Microsoft has made an effort to support more advanced font features across their products. Windows 7 includes support for advanced OpenType font features and laid the groundwork for advanced font support in programs with the new DirectWrite subsystem. It also includes the new font Gabriola, which includes an incredible number of beautiful stylistic sets and ligatures. Now, with the upcoming release of Office 2010, Microsoft is bringing advanced typographical features to the Office programs we love. This includes support for OpenType ligatures, stylistic sets, number forms, contextual alternative characters, and more. These new features are available in Word, Outlook, and Publisher 2010, and work the same on Windows XP, Vista and Windows 7. Please note that Windows does include several OpenType fonts that include these advanced features. Calibri, Cambria, Constantia, and Corbel all include multiple number forms, while Consolas, Palatino Linotype, and Gabriola (Windows 7 only) include all the OpenType features. And, of course, these new features will work great with any other OpenType fonts you have that contain advanced ligatures, stylistic sets, and number forms. Using advanced typography in WordTo use the new font features, open a new document, select an OpenType font, and enter some text. Here we have Word 2010 in Windows 7 with some random text in the Gabriola font. Click the arrow on the bottom of the Font section of the ribbon to open the font properties. Read more: How-to-geek
Windows 64-bit PCs Unable to Boot After Installing BitDefender Update
Posted by
jasper22
at
15:41
|
On the morning of Saturday, March 20th, a flawed BitDefender update was automatically pushed out to all 2008, 2009 & 2010 users. Following this event, it was discovered that BitDefender was falsely detecting several Windows and BitDefender files as infected with the Trojan.Fakealert.5 virus. As a result, there were reports of BitDefender and/or Windows and/or certain programs becoming inoperable, as well as PCs failing to boot.BitDefender promptly released a new automatic update which fixes these issues. Read more: WinMatrix
Read more: BitDeffender
Read more: BitDeffender
Turritopsis nutricula jellyfish
Posted by
jasper22
at
14:34
|

This species of jellyfish might be the only animal in the world to have truly discovered the fountain of youth. Since it is capable of cycling from a mature adult stage to an immature polyp stage and back again, there may be no natural limit to its life span. Because they are able to bypass death, the number of individuals is spiking. "We are looking at a worldwide silent invasion," says Dr. Maria Miglietta of the Smithsonian Tropical Marine Institute. Read more: 10 animals with the longest life spans
How To Evade URL Filters With (Not-So) Fancy Math
Posted by
jasper22
at
14:19
|
In their constant quest to find new and interesting ways to abuse the Internet, attackers recently have begun using an old technique to obfuscate URLs and IP addresses to bypass URL filters and direct users to malicious sites. The technique takes advantage of the fact that modern browsers will allow users to specify IP addresses in formats other than base 10. So a typical IP address that looks something like this — 192.10.10.1 — can also be written in base 8, hexadecimal or a handful of other formats, and the browser will recognize it and take the user to the specified site. What is interesting though is that due to the relative obscurity of using such methods to denote an IP or URL, it is quite feasible that existing security products do not correctly identify the URLs as valid or flag them as malicious when they point to existing known bad websites. Read more: Slashdot
IOGraph
Posted by
jasper22
at
13:31
|

Formerly known as MousePath it was made by Moscow designer Anatoly Zenkov to brighten up the routine work. Posting it at Flickr caused informal interest and afterward Anatoly Zenkov and his colleague Andrey Shipilov decided to evolve the app. IOGraph — is an application that turns mouse movements into a modern art. The idea is that you just run it and do your usual day stuff at the computer. Go back to IOGraph after a while and grab a nice picture of what you’ve done! Read more: IOGraph
Kleo Bare Metal Backup for Servers
Posted by
jasper22
at
13:30
|
With Kleo, you can now create all inclusive backups of your customers servers. Saves 100s of hours tracking down original CD’s or obsolete device drives. Kleo enables you to recover from server failure without the need of any other software. Comes with the Carroll-Net Server Recovery Kit. It includes hundreds of specialized server recovery tools. With it you can rescue failed servers, recover lost passwords and troubleshoot boot up problems.And best of all – it’s completely free! It makes the perfect addition to any computer technicians tool bag. Make as many copies as you like, even leave copies with your customers, or share with friends or colleagues. Reliable & Complete Bare Metal Backups for your customer’s servers (include's 100 free tools)Read more: Kleo Bare Metal Backup for Servers
New Legislation Would Crack Down On Online Criminal Havens
Posted by
jasper22
at
13:23
|
The Hill reports that Senators Orrin Hatch (R-Utah) and Kirsten Gillibrand (D-NY) have introduced a bill that would penalize foreign countries that fail to crack down on cyber criminals operating within their borders. Under the bill the White House would have the responsibility of identifying countries that pose cyber threats and the president would have to present to Congress in an annual report. Countries identified as 'hacker havens' would then have to develop plans of action to combat cybercrimes or risk cuts to their US export dollars, foreign-direct investment funds and trade assistance grants. Numerous American employers, including Cisco, HP, Microsoft, Symantec, PayPal, eBay, McAfee, American Express, Mastercard and Visa, as well as Facebook, are supporting the Senators' legislation. Read more: Slashdot
Comparison of Architecture presentation patterns MVP(SC),MVP(PV),PM,MVVM and MVC
Posted by
jasper22
at
13:03
|
This article will compare four important architecture presentation patterns i.e. MVP(SC),MVP(PV),PM,MVVM and MVC. Many developers are confused around what is the difference between these patterns and when should we use what. This article will first kick start with a background and explain different types of presentation patterns. We will then move ahead discussing about the state , logic and synchronization issues. Finally we will go in detail of each pattern and conclude how they differ from each other. Here’s my small gift for all my .NET friends , a complete 400 pages FAQ Ebook which covers various .NET technologies like Azure , WCF , WWF , Silverlight , WPF , SharePoint and lot more from here.
Special thanks This whole article is abstract from http://martinfowler.com/eaaDev/uiArchs.html GUI architectures. Great work by Mr. Martin flower.
Josh Smith and team http://msdn.microsoft.com/en-us/magazine/dd419663.aspx , great work on MVVM.
Mr. Nikhil kothari's blog http://www.nikhilk.net/Silverlight-ViewModel-Pattern.aspx , awesome source for MVVM.
Mr. Oleg Zhukov explains how to build a MVP Framework for .NET http://www.codeproject.com/KB/architecture/DotNetMVPFramework_Part1.aspx Background - Presentation patterns One of the biggest problems associated with user interface is lot of cluttered code. This cluttered code is due to two primary reasons , first the UI has complicated logic to manipulate the user interface objects and second it also maintains state of the application. Presentation patterns revolve around how to remove the UI complication and make the UI more clean and manageable. Below are different variety and classifications of presentation patterns as shown in the below figure. Read more: Codeproject
Special thanks This whole article is abstract from http://martinfowler.com/eaaDev/uiArchs.html GUI architectures. Great work by Mr. Martin flower.
Josh Smith and team http://msdn.microsoft.com/en-us/magazine/dd419663.aspx , great work on MVVM.
Mr. Nikhil kothari's blog http://www.nikhilk.net/Silverlight-ViewModel-Pattern.aspx , awesome source for MVVM.
Mr. Oleg Zhukov explains how to build a MVP Framework for .NET http://www.codeproject.com/KB/architecture/DotNetMVPFramework_Part1.aspx Background - Presentation patterns One of the biggest problems associated with user interface is lot of cluttered code. This cluttered code is due to two primary reasons , first the UI has complicated logic to manipulate the user interface objects and second it also maintains state of the application. Presentation patterns revolve around how to remove the UI complication and make the UI more clean and manageable. Below are different variety and classifications of presentation patterns as shown in the below figure. Read more: Codeproject
Use TortoiseHg (Mercurial) with SVN repository
Posted by
jasper22
at
13:01
|
It is trivial to use Mercurial client (TortoiseHg) to access Subversion repositories. Once you have the latest TortoiseHg, the process works easily. First you need to grab the hgsubversion extension: mkdir C:\repos
hg clone http://bitbucket.org/durin42/hgsubversion/ C:\repos\hgsubversionInfo about the hgsubversion extension. Then, you enable the extension: Right-click context menu - TortoiseHg - Global Settings - Edit File - add the lines below to your Mercurial.ini file:[extensions]
hgsubversion = C:\repos\hgsubversionNow you can, for example, grab the Autofac repository, using the usual check-out path prefixed with SVN: svn+https://autofac.googlecode.com/svn/trunkRead more: Rinat Abdullin
hg clone http://bitbucket.org/durin42/hgsubversion/ C:\repos\hgsubversionInfo about the hgsubversion extension. Then, you enable the extension: Right-click context menu - TortoiseHg - Global Settings - Edit File - add the lines below to your Mercurial.ini file:[extensions]
hgsubversion = C:\repos\hgsubversionNow you can, for example, grab the Autofac repository, using the usual check-out path prefixed with SVN: svn+https://autofac.googlecode.com/svn/trunkRead more: Rinat Abdullin
Windows 7 Start Button Changer v 2.0
Posted by
jasper22
at
13:00
|
Windows 7 Start Button Changer is a free tiny portable tool that allows you to change your Windows 7 start orb/button with just one click.Just follow the 1-2-3 simple steps to change your start orb: 1. Run the tool as administrator and click on "Select & Change Start Button".2. When it asks for the new start orb bitmap, either choose from any of the sample start orb bitmaps provided or choose the one you have.
If you have changed the start orb bitmap for the first time using this tool then it will create a backup of the unmodified explorer.exe.3. The Windows Explorer will now restart automatically and you will get the new start orb/button which you choosed. If you want to revert to the original start orb then click on "Restore Original Explorer Backup".Read more: DevianArt
If you have changed the start orb bitmap for the first time using this tool then it will create a backup of the unmodified explorer.exe.3. The Windows Explorer will now restart automatically and you will get the new start orb/button which you choosed. If you want to revert to the original start orb then click on "Restore Original Explorer Backup".Read more: DevianArt
Remove page flicker in IE8
Posted by
jasper22
at
12:59
|
In this pet project of mine I have two large background images. Unfortunately this means that IE will display a nasty page flicker on each request. I used to get rid of this with the a metatag that looks like this: <!--[if IE]>
<meta http-equiv="Page-Exit" content="blendTrans(Duration=0.0)" />
<![endif]-->For some reason however, this doesn't work in IE8 with cached pages. Use this tag instead and it all works fine again. <!--[if IE]>
<meta http-equiv="Page-Exit" content="Alpha(opacity=100)" />
<![endif]--> Read more: Wesley Bakker
<meta http-equiv="Page-Exit" content="blendTrans(Duration=0.0)" />
<![endif]-->For some reason however, this doesn't work in IE8 with cached pages. Use this tag instead and it all works fine again. <!--[if IE]>
<meta http-equiv="Page-Exit" content="Alpha(opacity=100)" />
<![endif]--> Read more: Wesley Bakker
36 Best Business Books that Influenced Microsoft Leaders
Posted by
jasper22
at
12:58
|
There are more books coming out every year than I can read in a lifetime. One of the ways I filter for great books is, I ask the most effective people I know, which books had a significant impact on how they think, feel, or act. I like to find the books that really made a difference, not just in theory, but in practice. Recently, I reached out to several Microsoft leaders, past and present, and up and down the ranks. The beauty of Microsoft is the extremely high concentration of smart people and I like to leverage the collective brain. In this case, I posed a simple question to find out which business books actually made a difference: “What are the top 3 books that changed your life in terms of business effectiveness?”I ended up with a really eclectic set ranging from parenting guides to changing the world. The top 3 business books that showed up multiple times were: Blue Ocean, Good to Great, and The Five Dysfunctions of a Team. This actually didn’t surprise me. I’ve been using Blue Ocean at work on a regular basis and Good to Great was a core part of the culture of the Microsoft patterns & practices team (the team I’m on.) Here are 36 best business books that influenced the Microsoft leaders that I reached out to: 1. All I Really Need to Know I Learned in Kindergarten
2. Authentic Leadership: Rediscovering the Secrets to Creating Lasting Value (J-B Warren Bennis Series)
3. Blue Ocean Strategy: How to Create Uncontested Market Space and Make Competition Irrelevant
4. Built to Last: Successful Habits of Visionary Companies
5. Execution: The Discipline of Getting Things Done
6. Fierce Conversations: Achieving Success at Work and in Life One Conversation at a Time
7. First, Break All the Rules: What the World’s Greatest Managers Do Differently
8. Fortune’s Formula: The Untold Story of the Scientific Betting System That Beat the Casinos and Wall Street
(more...)
Read more: Source of Insight
2. Authentic Leadership: Rediscovering the Secrets to Creating Lasting Value (J-B Warren Bennis Series)
3. Blue Ocean Strategy: How to Create Uncontested Market Space and Make Competition Irrelevant
4. Built to Last: Successful Habits of Visionary Companies
5. Execution: The Discipline of Getting Things Done
6. Fierce Conversations: Achieving Success at Work and in Life One Conversation at a Time
7. First, Break All the Rules: What the World’s Greatest Managers Do Differently
8. Fortune’s Formula: The Untold Story of the Scientific Betting System That Beat the Casinos and Wall Street
(more...)
Read more: Source of Insight
SQL SERVER – Difference Between ROLLBACK IMMEDIATE and WITH NO_WAIT during ALTER DATABASE
Posted by
jasper22
at
12:57
|
Today, we are going to discuss about something very simple, but quite commonly confused two options of ALTER DATABASE. The first one is ALTER DATABASE …ROLLBACK IMMEDIATE and the second one is WITH NO_WAIT. Many people think they are the same or are not sure of the difference between these two options. Before we continue our explaination, let us go through the explanation given by Book On Line. ROLLBACK AFTER integer [SECONDS] | ROLLBACK IMMEDIATESpecifies whether to roll back after a specified number of seconds or immediately.NO_WAITSpecifies that if the requested database state or option change cannot complete immediately without waiting for transactions to commit or roll back on their own, then the request will fail. If you have understood the difference by now, there is no need to proceed further. If you are still confused, continue with the rest of the post. Read more: Journey to SQL Authority with Pinal Dave
Windows Phone 7 OS can't run native code
Posted by
jasper22
at
12:56
|
Microsoft confirmed Monday at the company's Mix 10 developers event that native applications will not be allowed on Windows Phone 7 devices. Only applications running in the Silverlight runtime environment, or games in the XNA Game Studio runtime, will be allowed. That was the answer by Todd Brix, senior director for Mobile Platform Services Product Management, to a question from U.K.-based technology journalist Tim Anderson.Brix confirmed that Windows Phone 7, the user interface overlay atop the Windows Embedded CE 6.0 Release 3 kernel, runs only interpreted or managed code through the two runtime environments provided by Silverlight and XNA. Read more: InfoWorld
A C# wrapper for nearby Bluetooth devices Discovery under Windows Mobile
Posted by
jasper22
at
12:55
|
This code sample is named WMBluetoothWrapper. It demonstrates simple Bluetooth device discovery via the WinSock 2 API and provides a C# wrapper class for running the discovery. Both the names of the mobile devices and their addresses are retrieved and marshaled to C# data types. I provide both the Visual Studio 2010 DLL project WMBluetoothWrapper which present the WinSock 2 based discovery function as well as the C# file including the BluetoothConnection wrapper class. Using the retrieved addresses, the current wrapper can be extended to include further functions, such as, Bluetooth based connection and data exchanging functions. BackgroundAs part of my plan to write a mobile social network application (coming soon) using Windows Mobile Bluetooth capable devices, I need a way to know what Bluetooth devices are near me. I'm developing a mobile social network application in C# using the .NET compact framework 3.5 and thus, I was confronted with the need of writing the whole low level Bluetooth based functionalities in C++, compiling them into a DLL and finally writing a C# wrapper class and using P/Invoke(s) in order to run the Bluetooth functions. Before going ahead in the development of the wrapper, I've tried to find third-party libraries in C# exposing Bluetooth discovery functionalities, and I found 32feet.NET which seems to be popular from what I've read, however it seems to present some license limitations and after all it is better to have the control on a simpler and customizable wrapper. ArchitectureThe BluetoothConnection class is written in C# and it uses P/Invoke to gain access to exported functions within the WMBluetoothWrapper DLL file. The later is written in C++ and makes use of the Bluetooth functionalities provided by the Winsock 2 API in order to build the devices discovery function. Read more: Codeproject
Beginning Mac Programming
Posted by
jasper22
at
12:55
|
It’s time for another stop on the Books That I Have Known tour. This time I’d like to highlight a recently released Pragmatic title, Beginning Mac Programming, by Tim Isted.I am a fan of introductory texts, mainly because I’m often a newcomer to a particular subject myself. There’s a huge need for introductions: it’s important to hone and advance your skills, but it can be daunting to find a place to begin if you’re just starting out. And beginner books are not easy to write: the author has to really consider what it was like to learn the topic, and find a balance between giving the reader what they need and inundating them in useful but overwhelming details. Everyone’s a beginner sometime. There can be a certain degree of embarrassment about it: you sort of feel like you’re on your own, and it’s hard to ask questions of people who clearly know what they’re doing and don’t seem like they want to be bothered. I had a karate teacher (yes, I know, I’m a dork) who used to say when he visited other schools he would always wear a white belt, although he’d been teaching various martial arts for years. I like to think that his purpose was not to fool people into underestimating him so he could kick them in the head. The point is that no matter how skilled you are, it’s important to remember what it’s like to be new, to be a beginner. Read more: Editor's Field Journal
Image Insertion – Extension #2
Posted by
jasper22
at
12:52
|

The image insertion tool allows you to drag and drop images directly into your code, as shown below with an image of a UML diagram. Or, you could include your UI mockups to live literally alongside your code.
But the real reason I am including this extension is to prove to you this is an entirely new editor. In the image below, I’ve inserted a stick figure karate fighter (written in Silverlight) doing a side snap kick directly above the “Throw Kick” button click event handler. Read more: Sara Ford weblog
SQL Injection and the “Flintstones/Jetsons” Way to Deal with Licence Plate Cameras
Posted by
jasper22
at
12:31
|

“Flintstones/Jetsons” is a term that Mark Mothersbaugh from Devo uses to describe technology solutions that are a combination of low- and high-tech. It’s probably an apt term for what the driver of the Renault in the photo above is doing to foil licence plate cameras. If the “Jetsons” part – the SQL injection attack comprising the text on the banner on the bumper – doesn’t work, the “Flintstones” approach of physically covering up the licence plate will. Read more: Developer connection
Forcing an executable to run in 32bit mode
Posted by
jasper22
at
12:29
|
Since i am not a OS expert I would normally not write about this, but i was trying to run the BizTalk Documenter tool and always got startup errors.The customer environment is: * BizTalk 2006 R2 SP1 64 bits
* Windows 2003 server R2 64Bits
* SQL Server 2005 SP3 64 BitsIn my case the error was due that it seems Documenter Tool it is not able to run on 64bits on the detailed environment. So how literally force the tool to run on 32 bit mode? Just running a tool called CorFlags.exe Syntaxcorflags.exe Microsoft.Services.Tools.BiztalkDocumenter.exe /force /32BIT+
Great… but I do not see the tool, where is it?As far as i know it is installed by: * Microsoft Windows 200X SDK (C:\Program Files\Microsoft SDKs\Windows\v7.0\Bin\x64>) (note: this path is from a Windows 7 SDK)
* Visual Studio 2005 and above (C:\Program Files\Microsoft Visual Studio\SDK\v 2.0\Bin)Read more: BizTalk Tips & Things
* Windows 2003 server R2 64Bits
* SQL Server 2005 SP3 64 BitsIn my case the error was due that it seems Documenter Tool it is not able to run on 64bits on the detailed environment. So how literally force the tool to run on 32 bit mode? Just running a tool called CorFlags.exe Syntaxcorflags.exe Microsoft.Services.Tools.BiztalkDocumenter.exe /force /32BIT+
Great… but I do not see the tool, where is it?As far as i know it is installed by: * Microsoft Windows 200X SDK (C:\Program Files\Microsoft SDKs\Windows\v7.0\Bin\x64>) (note: this path is from a Windows 7 SDK)
* Visual Studio 2005 and above (C:\Program Files\Microsoft Visual Studio\SDK\v 2.0\Bin)Read more: BizTalk Tips & Things
מציאת קובץ שבה מוגדר מחלקה
Posted by
jasper22
at
12:28
|
עד היום (עד המעבר ל - Visual Studio 2010) כשהיינו בוחרים ב - Go To Definition על מחלקה מסויימת - היינו רואים באיזה Namespace המחלקה מוגדרת, אבל לא היה דרך הגיונית למצוא באיזה dll זה יושב (כדי לדעת למה לעשות AddReference) ב - VS2010 כשמגיעים ל - Go To Definition בחלק העליון מופיע הקוד הבא:
#region Assembly mscorlib.dll, v4.0.30128
// C:\Program Files (x86)\Reference Assemblies\Microsoft\Framework\.NETFramework\v4.0\mscorlib.dll
Server.Transfer Vs. Response.Redirect
Posted by
jasper22
at
12:26
|
לאחרונה שאלו אותי כמה אנשים על ההבדל בין Server.Transfer לבין Response.Redirect? מתי משתמשים בכל אחד מהם? ומדוע כדאי להשתמש ב Server.Transfer?
אז הגיע זמן לענות על השאלות :)
Response.Redirectהפקודה הזאת אומרת לדפדפן לעבור לעמוד המבקש:Response.Redirect("http://one-v.co.il/");Server.Transferגם הפקודה אומרת לדפדפן לעבור לעמוד המבוקש: Server.Transfer(http://one-v.co.il);אז מה ההבדל?Server.Transfer שומרת על הנתיב הנוכחי של העמוד ומעבירה רק את בקשה. אחד היתרונות של הפעולה היא חיסכון בבקשות של HTTP. החסרון בזה הוא שניתן להשתמש Server.Transfer רק כשרוצים להעביר באותו דומיין, Server.Transfer לא יעבוד במידה ונרצה להעביר לדומיין אחר.Server.Transfer ("http://one-v.org"); //won't work Server.Transfer מאפשר לנו גם לשמור את הנתונים של העמוד הקודם:Server.Transfer("send.aspx", true");
אז הגיע זמן לענות על השאלות :)
Response.Redirectהפקודה הזאת אומרת לדפדפן לעבור לעמוד המבקש:Response.Redirect("http://one-v.co.il/");Server.Transferגם הפקודה אומרת לדפדפן לעבור לעמוד המבוקש: Server.Transfer(http://one-v.co.il);אז מה ההבדל?Server.Transfer שומרת על הנתיב הנוכחי של העמוד ומעבירה רק את בקשה. אחד היתרונות של הפעולה היא חיסכון בבקשות של HTTP. החסרון בזה הוא שניתן להשתמש Server.Transfer רק כשרוצים להעביר באותו דומיין, Server.Transfer לא יעבוד במידה ונרצה להעביר לדומיין אחר.Server.Transfer ("http://one-v.org"); //won't work Server.Transfer מאפשר לנו גם לשמור את הנתונים של העמוד הקודם:Server.Transfer("send.aspx", true");
Read more: Arnold Simha
Is your MySQL Server Loaded ?
Posted by
jasper22
at
12:24
|
So you're running the benchmark/stress test - how do you tell if MySQL server is really loaded ? This looks like the trivial question but in fact, especially when workload consists of simple queries I see the load generation and network really putting a lot less load on MySQL than expected. For example you may have 32 threads (or processes) running queries as fast as they can... does it really mean there is an 32 concurrent queries ran all the time ? It may be the case or it may be not... Read more: DZone
Web Test Authoring and Debugging Techniques for Visual Studio 2010
Posted by
jasper22
at
11:01
|
A New Name, But Under the Covers Still the SameIn this release we renamed "Web Test” to “Web Performance Test” to highlight the primary scenario for Web tests, which is using them as scripts in a load test to model user actions. Load tests are used to drive load against a server, and then measure server response times and server response errors. Because we want to generate high loads with a relatively low amount of hardware, we chose to drive Web performance tests at the protocol layer rather than instantiating a browser. While Web performance tests can be used as functional tests, this is not their primary focus (see my post Are Web Tests Functional Tests?). You will see that I still refer to “Web Performance Tests” as “Web Tests” for short. If you really want to test the user experience from the browser, use a Coded UI test to drive the browser.In order to be successful working with Web Performance Tests, it is important you understand the fundamentals about how they work.
Web Performance Tests Work at the HTTP LayerThe most common source of confusion is that users do not realize Web Performance Tests work at the HTTP layer. The tool adds to that misconception. After all, you record in IE, and when running a Web test you can select which browser to use, and then the result viewer shows the results in a browser window. So that means the tests run through the browser, right? NO! The Web test engine works at the HTTP layer, and does not instantiate a browser. What does that mean? In the diagram below, you can see there are no browsers running when the engine is sending and receiving requests Read more: Ed Glas's blog on VSTS load testing
Read more: VS 2005: Web Test Authoring and Debugging Techniques
Read more: VS 2008: Web Test Authoring and Debugging Techniques for VS 2008
Web Performance Tests Work at the HTTP LayerThe most common source of confusion is that users do not realize Web Performance Tests work at the HTTP layer. The tool adds to that misconception. After all, you record in IE, and when running a Web test you can select which browser to use, and then the result viewer shows the results in a browser window. So that means the tests run through the browser, right? NO! The Web test engine works at the HTTP layer, and does not instantiate a browser. What does that mean? In the diagram below, you can see there are no browsers running when the engine is sending and receiving requests Read more: Ed Glas's blog on VSTS load testing
Read more: VS 2005: Web Test Authoring and Debugging Techniques
Read more: VS 2008: Web Test Authoring and Debugging Techniques for VS 2008
SQL SERVER – Fix : Error : 8501 MSDTC on server is unavailable. Changed database context to publisherdatabase
Posted by
jasper22
at
10:59
|
During configuring replication on one of the server, I received following error. This is very common error and the solution of the same is even simpler.MSDTC on server is unavailable. Changed database context to publisherdatabase. (Microsoft SQL Server, Error: 8501) Solution:Enable “Distributed Transaction Coordinator” in SQL Server.Method 1: 1. Click on Start–>Control Panel->Administrative Tools->Services
2. Select the service “Distributed Transaction Coordinator”
3. Right on the service and choose “Start”Method 2:Read more: Journey to SQL Authority with Pinal Dave
2. Select the service “Distributed Transaction Coordinator”
3. Right on the service and choose “Start”Method 2:Read more: Journey to SQL Authority with Pinal Dave
Visual Dumpbin - A C# Visual GUI for Dumpbin
Posted by
jasper22
at
10:58
|
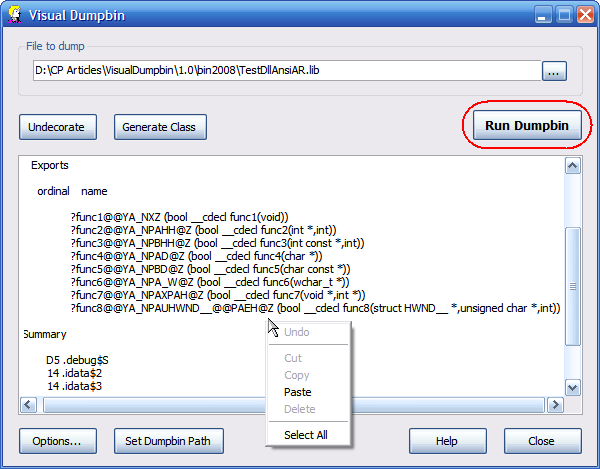
Since I started working with .NET, I use dumpbin frequently, since some of my work involves integrating unmanaged C++ DLLs, most of which I do not have source code for. It is very tedious to find the file I want to dump, open a command prompt, run dumpbin, open the output file, and finally copy the information I want. For .lib files this is bad enough, but for .dll files it is even worse; .lib files contain undecorated function prototypes, but .dll files do not. I put together Visual Dumpbin to help with this. After you select the file you want to dump, you see the exported functions with just one clickRead more: Codeproject
Implementing the IAsyncResult interface and calling functions asynchronously
Posted by
jasper22
at
10:56
|
One of the interesting features in .NET framework programming is the ability to easily use asynchronous programming and multi threading. .NET offers a wide variety of methods for asynchronous programming and for working with threads, but this was made very much easier with .NET 2.0. Building multithreaded applications in .NET 1.0 and .NET 1.1 has been made very convenient with classes like Thread and ThreadStart delegates. The ThreadPool class is useful in managing threads in multithreaded applications. In a quick glance, we can see that the addition of the BackgroundWorker class has added to the Windows application tool set.We can do an asynchronous callback for ASP.NET pages by adding the attribute: <%@ Page Async="true" ... %>This has made it very easy for users (even beginners) to use these facilities.I will not talk about how to use multithreading in .NET, this is out of the scope of this article and the internet is full of such articles. I will be talking about how to make your methods callable asynchronously by creating begin/end pair stems, in a similar way that the WSDL.exe tool generates the contract files for a Web Service. You will need this when you make a service or something like that and you want others to use it in an asynchronous way, to make it easy for them to implement it and enhance the performance without the need for them to create more threads and manage them etc. BackgroundI got really interested in the subject when I was developing a Smart Client application from scratch. In the beginning, I made a Web Service and coded all its functionality. Then, I built up a Windows client application which consumed the functionality of the service, and in order to enhance performance, I consumed the service in its Begin/End pair of methods, asynchronously. Read more: Codeproject
Creating a Performance Baseline
Posted by
jasper22
at
10:55
|
You'll often hear that you should monitor the performance of SQL Server. You may read a little about performance monitoring, and you may turn on a few counters or perform a query against a dynamic management view that you know about. But, you may still wonder "Are these numbers good or bad?" To determine if something is bad, you need to know what it looks like when it is good. Sounds obvious doesn't it? By creating a performance baseline, you can learn what your numbers are when your system is performing well. A performance baseline includes a single performance chart that is accompanied by an interpretation of the results, based on your environment. To establish your performance baseline against Windchill, you'll need to find a time when the performance of your SQL Server environment is considered normal. For example, no users are complaining about slow responses, no backups or large jobs are running, and no "special" processing is taking place. Once you find that time, you'll need to collect a range of Windows Performance Monitor (perfmon) counters, information from dynamic management views, and maybe even a small SQL Server Profiler trace. Then, you can use the results of your collection as the starting point for subsequent performance collections. How do the new numbers compare to the baseline numbers, when everything was fine? Did one counter go up or down? Did several numbers change? Having something to compare the current numbers with can help you identify the source of new performance bottlenecks. What Should You Monitor?The actual counters, dynamic management views, or SQL Server Profiler trace events that you should collect are based on your system setup. But, the counters that we list below are a good place to start. If you capture these counters, you should have enough information to determine if you are having a performance issue—and if you are having an issue, which area is the source. Note: Many of the counters that we list below list a threshold. These threshold numbers are not written in stone, and your actual values may be different. It is important to note that a standard threshold number is a starting point—if your value is a little higher or a little lower, the values that you see during your performance baseline collection become your new thresholds. Monitoring the Disk SubsystemThere are several methods to monitor the disk subsystem. Since the disk subsystem is getting more and more complex each year, we recommend that database administrators monitor the following Performance Monitor counters to understand the latency of their disk I/O requests. Read more: PTC Windchill on SQL Server
NET StarCraft II Replay Parser
Posted by
jasper22
at
10:54
|
Project Description
A .NET 3.5 Library used to parse StarCraft II replays.Developed in C# 3.5.Read more: Codeplex
A .NET 3.5 Library used to parse StarCraft II replays.Developed in C# 3.5.Read more: Codeplex
Использование SQLCLR для увеличения производительности
Начиная c MS SQL Server 2005 в распоряжение разработчиков баз данных была добавлена очень мощная технология SQL CLR.Эта технология позволяет расширять функциональность SQL сервера с помощью .NET языков, например C# или VB.NET. Используя SQL CLR можно создавать написанные на высокопроизводительных языках свои хранимые процедуры, триггеры, пользовательские типы и функции, а также агрегаты. Это позволяет серьезно повысить производительность и расширить функциональность сервера до немыслимых границ. Рассмотрим простой пример: напишем пользовательскую функцию разрезания строки по разделителю используя SQL синтаксис и SQL CLR на базе C# и сравним результаты.Пользовательская функция, возвращающая таблицу CREATE FUNCTION SplitString (@text NVARCHAR(max), @delimiter nchar(1))
RETURNS @Tbl TABLE (part nvarchar(max), ID_ORDER integer) AS
BEGIN
declare @index integer
declare @part nvarchar(max)
declare @i integer
set @index = -1
set @i=1
while (LEN(@text) > 0) begin
set @index = CHARINDEX(@delimiter, @text)
if (@index = 0) AND (LEN(@text) > 0) BEGIN
set @part = @text
set @text = ''
end else if (@index > 1) begin
set @part = LEFT(@text, @index - 1)
set @text = RIGHT(@text, (LEN(@text) - @index))
end else begin
set @text = RIGHT(@text, (LEN(@text) - @index))
end
insert into @Tbl(part, ID_ORDER) values(@part, @i)
set @i=@i+1
end
RETURN
END
go
Эта функция разрезает входную строку используя разделитель и возвращает таблицу. Применять такую функцию очень удобно, например, для быстрого заполнения временной таблицы записями. select part into #tmpIDs from SplitString('11,22,33,44', ',') Read more: habrahabr.ru
RETURNS @Tbl TABLE (part nvarchar(max), ID_ORDER integer) AS
BEGIN
declare @index integer
declare @part nvarchar(max)
declare @i integer
set @index = -1
set @i=1
while (LEN(@text) > 0) begin
set @index = CHARINDEX(@delimiter, @text)
if (@index = 0) AND (LEN(@text) > 0) BEGIN
set @part = @text
set @text = ''
end else if (@index > 1) begin
set @part = LEFT(@text, @index - 1)
set @text = RIGHT(@text, (LEN(@text) - @index))
end else begin
set @text = RIGHT(@text, (LEN(@text) - @index))
end
insert into @Tbl(part, ID_ORDER) values(@part, @i)
set @i=@i+1
end
RETURN
END
go
Эта функция разрезает входную строку используя разделитель и возвращает таблицу. Применять такую функцию очень удобно, например, для быстрого заполнения временной таблицы записями. select part into #tmpIDs from SplitString('11,22,33,44', ',') Read more: habrahabr.ru
Running Groovy on the Nokia N900
Posted by
jasper22
at
15:57
|
My favorite gadget for the last few months is definitely the Nokia N900. It’s a geeky device with a real Linux OS aboard. In opposite to it’s locked down competitors, the N900 runs Maemo, a platform consisting (mostly) of open source software. So I wonder if it’s possible to use Groovy on that. And yes, it is possible!Unfortunately the Maemo platform doesn’t contain a JVM by itself. Some days ago, I saw a tweet that there a OpenJDK port for ARM. All you have to do, is downloading the JDK and JRE from this page, bunzip it and move the directory to the N900. The next step is downloading Groovy and setting the envionment variables Read more: Armbruster IT Blog
Contributing to open source projects
Posted by
jasper22
at
15:47
|
Amit has written from India asking how to start participating in open source projects. I am a software developer from India and recently came through your article on "How improved hardware changed programming". It was good reading it. I wanted to know more about open source projects & how to get involved in it. I read that you contribute to a couple of them so thought of asking you about your experience and how did it help from a developer's perspective. My experience with code contributions to open source projects is mainly in the field of Php libraries and frameworks. This is not a coincidence as I am more stimulated to make contributions to projects I personally use: if I had to give one advice to choosing an open source project to participate in, I would recommend selecting a project you actually use at the Api level (interfacing with their source code or with their binary interface with your own code).
It's not an egoistic choice, although you would clearly benefit from your improved knowledge of the project internals, bugs that have been fixed and new features that have been introduced thanks to your work. It's more a synergistic approach.
Employing an open source project at the user level (in the case of standard applications) gives you a picture of its overall features and maybe an involvement with the supporting community, which is not a deep vision of the project goals and inner workings. But your contribution will be by far more valuable and simple if you start with contributions to codebases you already know "intimately". I would never try to contribute to Pidgin with code, because even if I run it all the time for instant messagging, the time I would spend in a field not related to my work it's probably not worth very much, as there is a steep learning curve and the learning process is limited to a field I'm not interested into (and thus am likely not to enjoy.) Read more: Invisible to the eye
It's not an egoistic choice, although you would clearly benefit from your improved knowledge of the project internals, bugs that have been fixed and new features that have been introduced thanks to your work. It's more a synergistic approach.
Employing an open source project at the user level (in the case of standard applications) gives you a picture of its overall features and maybe an involvement with the supporting community, which is not a deep vision of the project goals and inner workings. But your contribution will be by far more valuable and simple if you start with contributions to codebases you already know "intimately". I would never try to contribute to Pidgin with code, because even if I run it all the time for instant messagging, the time I would spend in a field not related to my work it's probably not worth very much, as there is a steep learning curve and the learning process is limited to a field I'm not interested into (and thus am likely not to enjoy.) Read more: Invisible to the eye
RIP Google.cn: Google Closes Its Search Operations in China
Posted by
jasper22
at
15:36
|
Google has announced a moment ago in their blogpost that they are closing down all of their search operations in China. From now onwards Google.cn will redirect to Google.com.hk. This is a black day for the open web and China. Google has stopped censoring their search services Google Search, News and Images on Google.cn and it will redirected to Google.com.hk where all the uncensored results will come in Chinese language. In simple words Google is just shifting their servers from China to Hong Kong. Google’s map and music search will remain live in China domain as of now. Google will continue to have their R&D center in China and also a sales team if and only if China doesn’t start blocking Google.com.hk. Read more: TechDust
Official blog: Google
Official blog: Google
Creating a rogue CA certificate
Posted by
jasper22
at
09:53
|
We have identified a vulnerability in the Internet Public Key Infrastructure (PKI) used to issue digital certificates for secure websites. As a proof of concept we executed a practical attack scenario and successfully created a rogue Certification Authority (CA) certificate trusted by all common web browsers. This certificate allows us to impersonate any website on the Internet, including banking and e-commerce sites secured using the HTTPS protocol. Our attack takes advantage of a weakness in the MD5 cryptographic hash function that allows the construction of different messages with the same MD5 hash. This is known as an MD5 "collision". Previous work on MD5 collisions between 2004 and 2007 showed that the use of this hash function in digital signatures can lead to theoretical attack scenarios. Our current work proves that at least one attack scenario can be exploited in practice, thus exposing the security infrastructure of the web to realistic threats. This successful proof of concept shows that the certificate validation performed by browsers can be subverted and malicious attackers might be able to monitor or tamper with data sent to secure websites. Banking and e-commerce sites are particularly at risk because of the high value of the information secured with HTTPS on those sites. With a rogue CA certificate, attackers would be able to execute practically undetectable phishing attacks against such sites. Read more: Security Research
Windows Research Kernel
Posted by
jasper22
at
09:47
|
OverviewThe WRK packages core Windows XP x64 and Windows Server 2003 SP1 kernel source code with an environment for building and testing experimental versions of the Windows kernel for use in teaching and research. The WRK includes the source for: * Processes
* Threads
* LPC
* Virtual memory
* Scheduler
* Object manager
* I/O manager
* Synchronization
* Worker threads
* Kernel heap manager
* Other core Windows (NTOS) kernel functionalityThe WRK is useful in design projects that allow your students to explore operating system (OS) principles using the Windows kernel sources. It facilitates the building of experiments and projects based on modifying the Windows kernel, enabling advanced teaching and research that promote better understanding of the Windows architecture and implementation. WRK DetailsThe Windows Research Kernel contains the sources for the core Windows (NTOS) kernel.NTOS implements the basic OS functions for: * Processes
* Threads
* Virtual memory and cache managers
* I/O management
* The registry
* Executive functions, such as the kernel heap and synchronization
* Object manager
* Local procedure call mechanism
* Security reference monitor
* Low-level CPU management (thread scheduling, Asynchronous and Deferred Procedure calls, interrupt/trap handling, exceptions) The NT Hardware Abstraction Layer, file systems, network stacks, and device drivers are implemented separately from NTOS and loaded into kernel mode as dynamic libraries. Sources for these dynamic components are not included in the WRK. However, some are available in various development kits published by Microsoft, such as the Installable File System Kit and the Windows Driver Development Kit. Read more: MS Research
* Threads
* LPC
* Virtual memory
* Scheduler
* Object manager
* I/O manager
* Synchronization
* Worker threads
* Kernel heap manager
* Other core Windows (NTOS) kernel functionalityThe WRK is useful in design projects that allow your students to explore operating system (OS) principles using the Windows kernel sources. It facilitates the building of experiments and projects based on modifying the Windows kernel, enabling advanced teaching and research that promote better understanding of the Windows architecture and implementation. WRK DetailsThe Windows Research Kernel contains the sources for the core Windows (NTOS) kernel.NTOS implements the basic OS functions for: * Processes
* Threads
* Virtual memory and cache managers
* I/O management
* The registry
* Executive functions, such as the kernel heap and synchronization
* Object manager
* Local procedure call mechanism
* Security reference monitor
* Low-level CPU management (thread scheduling, Asynchronous and Deferred Procedure calls, interrupt/trap handling, exceptions) The NT Hardware Abstraction Layer, file systems, network stacks, and device drivers are implemented separately from NTOS and loaded into kernel mode as dynamic libraries. Sources for these dynamic components are not included in the WRK. However, some are available in various development kits published by Microsoft, such as the Installable File System Kit and the Windows Driver Development Kit. Read more: MS Research
Approaching Parallelism
Posted by
jasper22
at
09:35
|
Reed Copsey has written a series of blog postings on how to look at your application to make it run on multi-core processors. He approaches the issue by focusing on what you are trying to accomplish. This is an indepth series that shows code and details in how you can Here’s a list of his posts so far: * Parallelism in .NET – Introduction
* Parallelism in .NET – Part 1, Decomposition
* Parallelism in .NET – Part 2, Simple Imperative Data Parallelism
* Parallelism in .NET – Part 3, Imperative Data Parallelism: Early Termination
* Parallelism in .NET – Part 4, Imperative Data Parallelism: Aggregation
* Parallelism in .NET – Part 5, Partitioning of Work
* Parallelism in .NET – Part 6, Declarative Data Parallelism
* Parallelism in .NET – Part 7, Some Differences between PLINQ and LINQ to Objects
* Parallelism in .NET – Part 8, PLINQ’s ForAll Method
* Parallelism in .NET – Part 9, Configuration in PLINQ and TPL
* Parallelism in .NET – Part 10, Cancellation in PLINQ and the Parallel class
* Parallelism in .NET – Part 11, Divide and Conquer via Parallel.Invoke
* Parallelism in .NET – Part 12, More on Task DecompositionEach post is a short, concise, thought-provoking way to look at your application to run in parallel.
See AlsoSee also my screencast series on Channel 9 which serves as an introduction to Parallel Computing on Windows Read more: ISV Developer Community
* Parallelism in .NET – Part 1, Decomposition
* Parallelism in .NET – Part 2, Simple Imperative Data Parallelism
* Parallelism in .NET – Part 3, Imperative Data Parallelism: Early Termination
* Parallelism in .NET – Part 4, Imperative Data Parallelism: Aggregation
* Parallelism in .NET – Part 5, Partitioning of Work
* Parallelism in .NET – Part 6, Declarative Data Parallelism
* Parallelism in .NET – Part 7, Some Differences between PLINQ and LINQ to Objects
* Parallelism in .NET – Part 8, PLINQ’s ForAll Method
* Parallelism in .NET – Part 9, Configuration in PLINQ and TPL
* Parallelism in .NET – Part 10, Cancellation in PLINQ and the Parallel class
* Parallelism in .NET – Part 11, Divide and Conquer via Parallel.Invoke
* Parallelism in .NET – Part 12, More on Task DecompositionEach post is a short, concise, thought-provoking way to look at your application to run in parallel.
See AlsoSee also my screencast series on Channel 9 which serves as an introduction to Parallel Computing on Windows Read more: ISV Developer Community
Comparing Memcache and Ehcache Server Performance
Posted by
jasper22
at
09:33
|
Ehcache Server provides a RESTful API for cache operations. I am working on v0.9 and have been doing some performance benchmarks. I thought it would be interesting to compare it with the performance of that other over-the-network cache, Memcache. Now I already knew that Ehcache in-process was around 1,000 times faster than Memcache. But what would the over-the-network comparison be. Here are the results:Memcache and SpyMemcache Client10000 sets: 3396ms10000 gets: 3551ms10000 getMulti: 2132ms10000 deletes: 2065msEhcache 0.9 with Ehcache 2.0.0 10000 puts: 2961ms10000 gets: 3841ms10000 deletes: 2685msSo, the results are a wash. Memcache is slightly slower on put, maybe because the JVM does not have to malloc, it already has the memory in heap. And very slightly faster on get and delete. A few years ago there was a raging thread on the Memcache mailing list about Memcache versus MySQL with in-memory tables. They were also a wash. I think the point is that serialization and network time is more significant than the server time, provided the server is not that much different. Read more: Greg Luck's Blog
Using SystemParametersInfo to access user interface settings
The SystemParametersInfo function gives you access to a whole slew of user interface settings, and it is the only supported method for changing those settings.I'm not going to list every single setting; go read the list yourself. Here are some highlights: * SPI_GETICONTITLELOGFONT lets you query the font that is used for icon labels; SPI_SETICONTITLELOGFONT lets you change it.
* SPI_GETNONCLIENTMETRICS lets you query the fonts that are used for window captions, menus, status bars, and message boxes; SPI_SETNONCLIENTMETRICS lets you change them. Here are some control panel settings. * SPI_SETKEYBOARDDELAY and SPI_SETKEYBOARDSPEED let you set the keyboard autorepeat parameters.
* SPI_SETDOUBLECLICKTIME lets you set the mouse double-click speed.
* SPI_SETMENUFADE lets you enable or disable the menu fade animation. [Typo fixed, 4pm.]
* There is a whole series of SPI_SETxxxANIMATION settings that let you control which screen elements animate. Notice that when using the SPI_SET* commands, you also have to choose whether the setting changes are temporary (lost at logoff) or persistent. The historically-named SPIF_UPDATEINIFILE flag causes the changes to be saved to the user profile; if you leave it off, then the changes are not saved and are lost when the user logs off. You should also set the SPIF_SENDCHANGE flag so that programs which want to refresh themselves in response to changes in the settings can do so. The fact that there exist both temporary and persistent changes highlights the danger of accessing the registry directly to read or write the current settings. If the current settings are temporary, then they are not saved in the registry. The SystemParametersInfo function retrieves the actual current settings, including temporary ones. For example, if you want to query whether menus are being animated, and the user has temporarily disabled animation, reading the registry will tell you that they are being animated when in fact they are not. Also, changes written to the registry don't take effect untll the next logon, because that is the only time the values are consulted. To make a change take effect immediately, you must use SystemParametersInfo. It still puzzles me why people go to the undocumented registry keys to change these settings when there is a perfectly good documented function for doing it. Especially when the documented function works and the undocumented registry key is unreliable. Read more: The old new thing
* SPI_GETNONCLIENTMETRICS lets you query the fonts that are used for window captions, menus, status bars, and message boxes; SPI_SETNONCLIENTMETRICS lets you change them. Here are some control panel settings. * SPI_SETKEYBOARDDELAY and SPI_SETKEYBOARDSPEED let you set the keyboard autorepeat parameters.
* SPI_SETDOUBLECLICKTIME lets you set the mouse double-click speed.
* SPI_SETMENUFADE lets you enable or disable the menu fade animation. [Typo fixed, 4pm.]
* There is a whole series of SPI_SETxxxANIMATION settings that let you control which screen elements animate. Notice that when using the SPI_SET* commands, you also have to choose whether the setting changes are temporary (lost at logoff) or persistent. The historically-named SPIF_UPDATEINIFILE flag causes the changes to be saved to the user profile; if you leave it off, then the changes are not saved and are lost when the user logs off. You should also set the SPIF_SENDCHANGE flag so that programs which want to refresh themselves in response to changes in the settings can do so. The fact that there exist both temporary and persistent changes highlights the danger of accessing the registry directly to read or write the current settings. If the current settings are temporary, then they are not saved in the registry. The SystemParametersInfo function retrieves the actual current settings, including temporary ones. For example, if you want to query whether menus are being animated, and the user has temporarily disabled animation, reading the registry will tell you that they are being animated when in fact they are not. Also, changes written to the registry don't take effect untll the next logon, because that is the only time the values are consulted. To make a change take effect immediately, you must use SystemParametersInfo. It still puzzles me why people go to the undocumented registry keys to change these settings when there is a perfectly good documented function for doing it. Especially when the documented function works and the undocumented registry key is unreliable. Read more: The old new thing
Scaling writes in MySQL
Posted by
jasper22
at
14:14
|
We use MySQL on most of our projects. One of these projects has a an access pattern unlike any other I've worked on. Several million records a day need to be written to a table. These records are then read out once at the end of the day, summarised and then very rarely touched again. Each record is about 104 bytes long (thre's one VARCHAR column, everything else is fixed), and that's after squeezing out every byte possible. The average number of records that we write in a day is 40 million, but this could go up. A little bit about the set up. We have fairly powerful boxes with large disks using RAID1/0 and 16GB RAM, however at the time they only had 4GB. For BCP, we have a multi-master set up in two colos with statement level replication. We used MySQL 5.1. My initial tests with various parameters that affect writes showed that while MyISAM performed slightly better than InnoDB while the tables were small, it quickly deteriorated as the table size crossed a certain point. InnoDB performance deteriorated as well, but at a higher table size. The table size turned out to be related to the innodb_buffer_pool_size, and that in turn was capped by the amount of RAM we had on the system. I decided to go with InnoDB since we also needed transactions for the summary tables and I preferred not to divide my RAM between two different engines. I stripped out all indexes, and retained only the primary key. Since InnoDB stores the table in the primary key, I decided that rather than use an auto_increment column, I'd cover several columns with the primary key to guarantee uniqueness. This had the added advantage that if the same record was inserted more than once, it would not result in duplicates. This small point was crucial for BCP, because it meant that we did not have to keep track of which records had already been inserted. If something crashed, we could just reinsert the last 30 minutes worth of data, possibly into the secondary master, and not have any duplicates at the end of it. I used INSERT IGNORE to get this done automatically. Read more: The other side of the moon
Subscribe to:
Comments (Atom)

 Read more:
Read more: 


