I had an interesting question pop up on my “SSL is not about encryption” blog post this weekend:
I have a question about logging to site like StackOverflow which doesn't use SSL at all.
If I am login to SO via Google. Is this secure in this case?
This is actually a very good question for a number of reasons so I thought it deserved a little more attention than just the short response I gave on the blog. The question implies there is some sort of absolute state to security (probably unintentionally) where a site such as Stack Overflow is deemed to be either “secure” or “insecure” (hence the quotes in the title).
The reality is that there are a few more twists to it than that and Stack Overflow in particular is an interesting case study due to their use of a third party authentication provider. What this blog post will show you is that in this particular case, we’re really looking at two different security domains with different levels of protection and in the case of Stack Overflow, yes, it’s kind of secure – but then it’s also kind of insecure too…
Stack Overflow and the role of OpenID
I’ve followed the evolution of Stack Overflow from the very early days and one thing that Jeff Atwood was always adamant about was the role of OpenID. Jeff has many, many good points and probably the most significant one from a security perspective is that it makes the job of keeping credentials safe the responsibility of someone else. This is a good thing, particularly when you consider the work organisations like Google they’ve done around two factor authentication. Now of course there are other OpenID providers who are not quite as well equipped, but certainly they still do a very good job of implementing secure authentication mechanisms.
There are opponents of OpenID, but the arguments are more about the logistics of implementing it and dealing with customers having accounts with all sorts of different providers. These are perfectly valid concerns, but they’re not about security; all the OpenID implementations I’ve seen adhere to all the sorts of good account management practices I regularly talk about such as no restrictions on password length or structure, well implemented password reset processes and of course everything is done over HTTPS.
But what we need to remember is that OpenID is being used by Stack Overflow solely for the purpose of authenticating the users. What happens after this is a whole new ballgame.
Stack Overflow and HTTPS
Here’s what you currently see on Stack Overflow today:
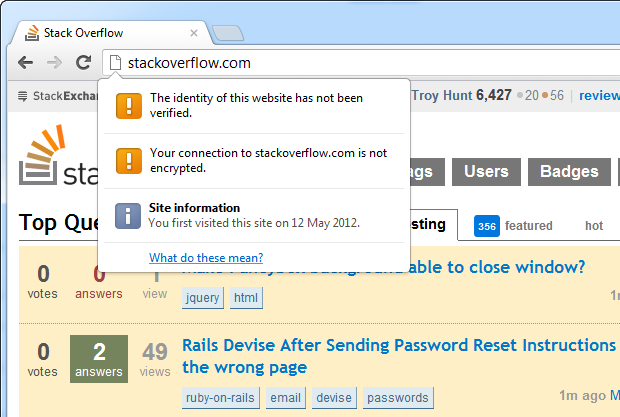
This is really what Marek was referring to in the initial question which sparked this blog post and as he has rightly observed, there is no use of HTTPS. But is this a problem? I mean I’ve already logged on via OpenID so my credentials have been sent securely already, what’s the risk?
To answer that question, let’s start by taking a look at the cookies set by the site. Why? Because cookies are how our logged in state is persisted across multiple requests over HTTP which is a stateless protocol, that is each request is made over a new connection totally independent to the other requests. In other words, HTTP itself doesn’t know we’re logged in, it needs help from cookies.
Read more: Troy Hunt's Blog
QR: